The rising sophistication
of
network scanning
Context
- Brad Hein, a network administrator and security researcher.
-
noticed a steady flow of unsolicited network scans
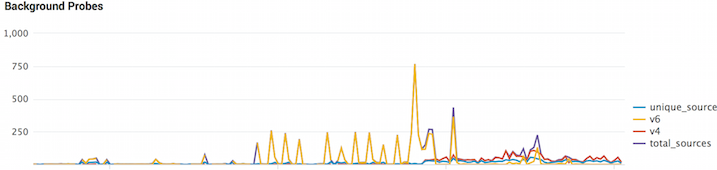
Context
Problem
- Targeted devices had randomized IPv6 addresses and were not published in DNS or any public record.
- IPv6 space is too big for systematic scans (2¹²⁸ possibilities).
- None of the scanned devices had ever made outbound connections to the scanner addresses.
- How did they know the unpublished addresses ?
Background
- Devices were Raspberry pi using Raspbian.
- Comes packaged with the “NTP time daemon”, preconfigured to query a specific set of time providers.
- scans take less than 5 seconds and scans over 100 common TCP and UDP ports.
- While not being registered and guessable, the device made a normal request to the public NTP pool to set its clock.
Network Time Protocol
- Pretty much every computer these days sets its time to the atomic standard.
-
Most often, a computer will use NTP to synchronize its clock to a public NTP server.
-
NTP uses a concept of pools or groups of servers.
-
Ntp.org aggregates the public pools and makes them available with names such as 0.Debian.pool.ntp.org
-
IPv6 and NTP Debian users have probably been scanned
Port scanning
- Like walking through a parking lot and pulling on door handles to see which doors are unlocked.
- Port scans can be used ethically, but they can also be used maliciously.
- Researchers use port scan data to compile reports about the internet as a whole.
- Evil hackers use port scan results to identify potential victims based on the software they detected during the port scan.
Shodan
lets the user find specific types of computers (routers, servers, etc.) connected to the internet using a variety of filters
IPv6
- the most recent version of the IP protocol.
- 128 bits address -> 2¹²⁸ (or about 3.4×10³⁸) theoretical addresses available.
- Every device can have its own public address.
- No need for Network Address Translation (NAT).
- Global Unique address : the network activity of each device can potentially be tracked
Privacy extension
-
Provides randomized addressing : an IP address that is half home/network prefix and half random bits.
-
Supposed to make a device address nearly unguessable.
-
privacy addresses are still exposed any time the device makes an outgoing connection (such as setting its clock to an NTP server).
Early findings
- Scans are being carried out by way of the Shodan’s scan API.
- NTP time sync against a harvester will result in a follow-up scan.
- IP harvesting operation is looking for targets at a packet level.
2604:a880:0800:0010:0000:0000:0970:a001 = thor.scan6.shodan.io.
2604:a880:0800:0010:0000:0000:00fe:d001 = gateway.scan6.shodan.io.
2604:a880:0800:0010:0000:0000:0092:2001 = bone.scan6.shodan.io.
2604:a880:0800:0010:0000:0000:00fd:7001 = burger.scan6.shodan.io.
2604:a880:0800:0010:0000:0000:0089:c001 = rock.scan6.shodan.io.Consequences
- Guess the ratio of IPv6 addresses which do and do not have a firewall.
- know which services are not protected by a firewall on the clients.
- Probe for vulnerabilities in the clients.
Test server setup
sysctl.conf
# BH - for testing. Turn off SLAAC.
net.ipv6.conf.all.autoconf=0
net.ipv6.conf.default.autoconf=0
# BH - privacy extensions - override the default 1-day long tempaddr validity time
# with something much smaller.
# This should help narrow down ipv6 address harvesting servers, among other things.
net.ipv6.conf.all.use_tempaddr=2
net.ipv6.conf.default.use_tempaddr=2
net.ipv6.conf.eth0.use_tempaddr=2
net.ipv6.conf.all.temp_prefered_lft=1200
net.ipv6.conf.all.temp_valid_lft=2400
net.ipv6.conf.default.temp_prefered_lft=1200
net.ipv6.conf.default.temp_valid_lft=2400
net.ipv6.conf.eth0.temp_prefered_lft=1200
net.ipv6.conf.eth0.temp_valid_lft=2400- Goal : have unique IP per harvester.
- make Addresses expire once every 20 minutes and tests once every 30 minutes.
- Unique source address for each time requests.
Harvesting servers
- Only a few IPv6 addresses are returned by a DNS lookup against the pool, but they all get returned eventually.
- There are literally hundreds, maybe thousands of IPs that can be returned.
$ host 2.debian.pool.ntp.org
<snip>
2.debian.pool.ntp.org has IPv6 address 2604:a880:400:d0::9:b002
2.debian.pool.ntp.org has IPv6 address 2604:a880:400:d0::9:b00e
2.debian.pool.ntp.org has IPv6 address 2001:470:e949:a::1
2.debian.pool.ntp.org has IPv6 address 2604:a880:1:20::a7:f004Harvesting servers
- NTP: Visits a handful of different servers before making its final adjustment to the clock.
- In a given synchronization period, it may visit half a dozen different time servers.
- More difficult to identify which NTP server was harvesting and triggering the scans.
- Using short temporary address and detective script.
Detective Script
- Performs firewall log analysis to uncover scan operations.
- Execute second query to uncover outbound packet responsible for scan.
SCAN DETECTED: startTime=2016-01-13T19:33:10.000+00:00 numPortsScanned=117
SRC=2604:a880:0800:0010:0000:0000:0970:a001 DST=my:prefix:my:prefix:7c0d:e6cb:8719:7d94
durationSeconds=0.0 startTimeEpoch=1452713590.0
One or more of these packets may have triggered the scan...
lag=47.0s @2016-01-13T19:32:25.000+00:00 epoch=1452713545
my:prefix:my:prefix:7c0d:e6cb:8719:7d94:42539 -> 2604:a880:0001:0020:0000:0000:00a7:f007:123
lag=7.0s @2016-01-13T19:33:05.000+00:00 epoch=1452713585
my:prefix:my:prefix:7c0d:e6cb:8719:7d94:59081 -> 2604:a880:0001:0020:0000:0000:00a7:f009:123Confirming harverster
- Individually by using ntpdate.
- Checking for an immediate follow-up scan.
- Using a bash script to surgically probe each suspect while not letting ntp make other connections.
2604:a880:0400:00d0:0000:0000:0009:b001 (DNS: robot.data.shodan.io)
2604:a880:0400:00d0:0000:0000:0009:b002
...
2604:a880:0400:00d0:0000:0000:0009:b00f
2604:a880:0001:0020:0000:0000:00a7:f001 (DNS: abend.data.shodan.io)
2604:a880:0001:0020:0000:0000:00a7:f002
...
2604:a880:0001:0020:0000:0000:00a7:f00fAnalysis
- 3 Blocks of 15 IPs belonging to Shodan.
- Each of the blocks of 15 is probably a single server.
- The scan results are probably being saved to a massive database (Shodan).
After publication
- The whole NTP IPv6 pool was affected.
- The incriminated servers were removed from the NTP pool.
- The harvesting wasn't disclosed and went well beyond the service advertised by NTP Time Project.
- Potential solution : using a secondary IPv6 address to make NTP queries or even for all outgoing connections.
Conclusion
- People are wrongly assuming IPv6 good obscurity properties provides a lot of security.
- An efficient approach to finding hosts in, by design, sparsely populated IPv6 subnets.
- Something we should come to expect.
- The proposed fix would also do little to prevent abuse by other services.
The rising sophistication of network scanning
By Baptiste Desbiolles
The rising sophistication of network scanning
Based on Brad Hein's article: http://netpatterns.blogspot.com/2016/01/the-rising-sophistication-of-network.html
- 831


