Don't Be SecureLess
Best practices for keeping your Lambdas secure
bene@theodo.co.uk
Ben Ellerby


@EllerbyBen



Ben Ellerby


@EllerbyBen

serverless-transformation


@EllerbyBen
Serverless


What is this Serverless thing?
-
Architectural movement
- Developers send application code which is run by the cloud provider in isolated containers abstracted from the developer.
- Use 3rd party services used to manage backend logic and state (e.g. Firebase, Cognito)
- Cost nothing when not used
- A framework with the same name

@EllerbyBen

Why Serverless?
💰 Cost reduction
👷♂️ #NoOps
💻 Developers focus on delivering business value
📈 More scalable
🌳 Greener

@EllerbyBen

Not just Lambda (FaaS)



Lambda
S3
Dynamo

API Gateway
Compute
Storage
Data
API Proxy

Cognito
Auth
SQS
Queue

EventBridge
Event Bus

Power and Flexibility








@EllerbyBen

FaaS: AWS Lambda








@EllerbyBen


@EllerbyBen

Cleanup /tmp
When the temporary is persistent

@EllerbyBen

-
/tmp is the only place to write to disk on Lambda
-
Useful for performance and file manipulation (e.g. PDFs)
-
But, removes the sandboxing isolation from src (and injected) code.
- EFS has changed some aspects of this, but tmp is the main concern for most users.
Cleanup after yourself

@EllerbyBen

Always remove any file written to the /tmp directory unless you are explicitly doing it to optimize performance and have considered all potential security risks.
Cleanup after yourself

@EllerbyBen

const removeFolderContentsRecursively = (directory) => {
fs.readdir(directory, (err, files) => {
if (err) throw err;
for (const file of files) {
console.log(`--- Deleting ${file} ---`);
const curPath = `${directory}/${file}`;
if (fs.lstatSync(curPath).isDirectory()) {
removeFolderContentsRecursively(curPath);
} else { // delete file
try {
fs.unlinkSync(file);
} catch (error) {
}
}
}
});
}
// Clean up if on Lambda (not local!)
if (context.awsRequestId && !process.env.IS_LOCAL) {
removeFolderContentsRecursively('/tmp');
}
@EllerbyBen

Separate Lambdas
Separation of Lambda Concerns

@EllerbyBen

-
IAM roles allow fine-grained permissions
-
Large cross-functional monolithic Lambdas don't benefit as much
-
"Micro-Lambdas" that do one thing can have fine-grained policies.

@EllerbyBen






@EllerbyBen







@EllerbyBen






Keep it fine-grained

@EllerbyBen

Keep your Lambdas fine-grained with a separation of concerns, using specific roles with specific policies for each.

Automate Checks

@EllerbyBen

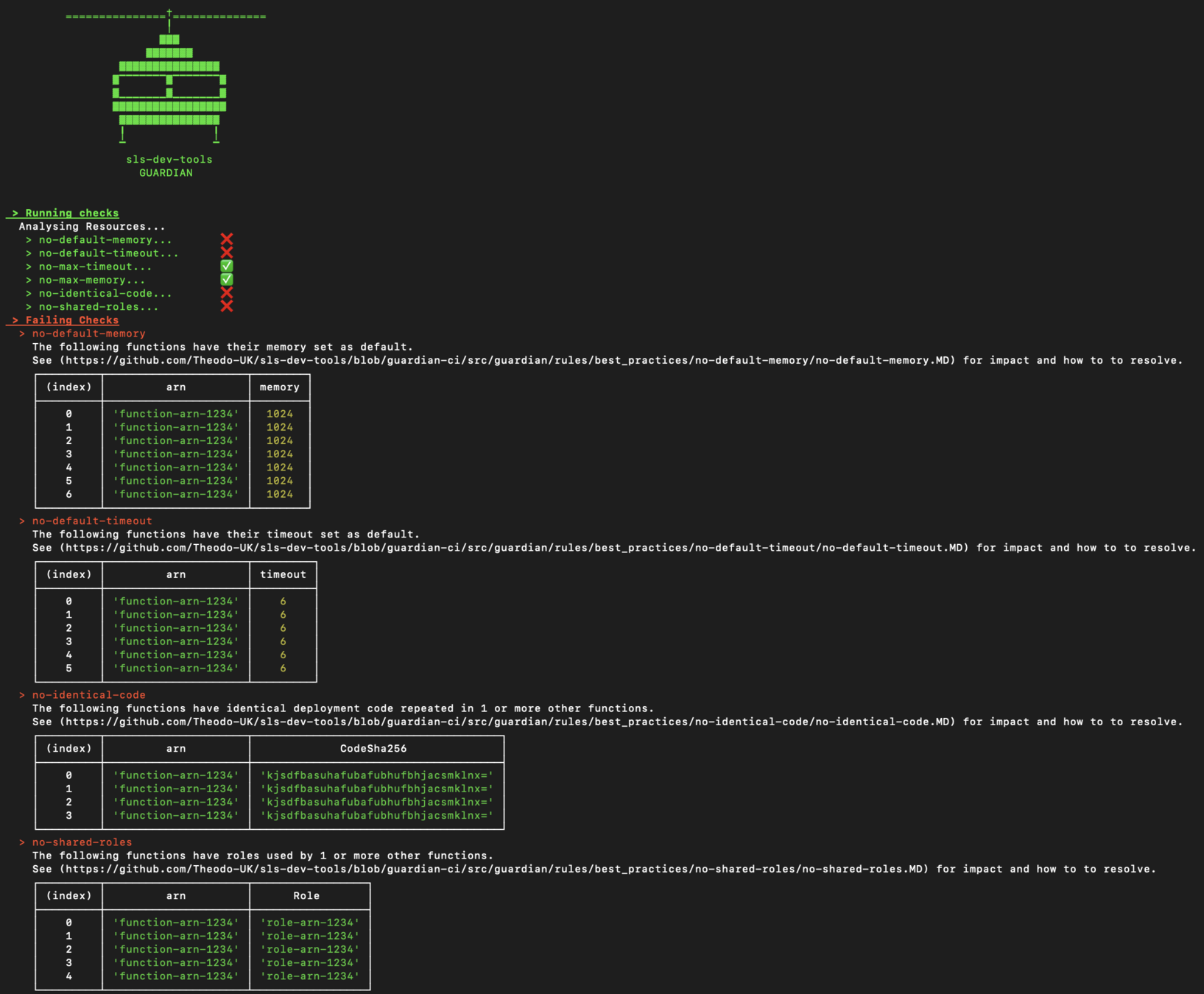

@EllerbyBen



@EllerbyBen

Least Privilege
Don't go wild with IAM

@EllerbyBen

-
IAM is a great tool to secure your application.
-
Developers have been massively empowered by Serverless, but at what cost?
-
Use policies that give least privilege possible to perform a specific task.
Audit your policies

@EllerbyBen



Train and Automate

@EllerbyBen

Ensure all IAM policies allow the least privileges needed to perform their task. Train your team on this principle and ensure basic checks are enforced on CI.


@EllerbyBen

API Gateway
Security Check

@EllerbyBen

-
Keep private lambdas private
-
Expose via well-configured API Gateway
-
DoS protection
-
Rate limiting
-
Integration with “Authentication as a Service” e.g. Cognito, Okta...
Add WAF

@EllerbyBen


AWS WAF is your first line of defence against web exploits
WAF & API Gateway?

@EllerbyBen


Check Requests

@EllerbyBen

Avoid exposing Lambda functions to the Internet and if exposed only allow invocation through API Gateway with WAF.


@EllerbyBen

Observability
Know what’s happening

@EllerbyBen

-
The flexibility, distribution and granularity of Serverless architectures make logging hard.
-
Cloudwatch & XRay are the minimum.



@EllerbyBen


CloudWatch Lambda Insights

@EllerbyBen

Dedicated Observability Service







Be All-Seeing

@EllerbyBen

Basic logging is a given. Add onto this, X-Ray Logging and specialised third-party Serverless logging providers (and Cloudwatch ServiceLens).
Build to make your logs recoverable.


@EllerbyBen

OWASP 10

Don’t forget the basics

@EllerbyBen

-
Serverless changes many things - but don't forget to secure code, access control, dependencies encryption...
-
Apply OWASP Top 10
-
Apply Serverless OWASP Top 10
Keep applying the basics

@EllerbyBen

Keep applying basic security principles and use the OWASP Top Ten as your reference.
Also, use automated tools like snyk and Protego


@EllerbyBen

Account Security

Environmental Impact

@EllerbyBen

-
1 AWS Account PER Environment (e.g. dev, staging, UAT, production)
-
Use AWS Organizations to share billing and policies. Aim for 1 account / service strategy.
-
MFA is NEVER optional.
AWS SSO can help too!
Secure Your Accounts

@EllerbyBen

Separate your dev, test and production environments to mitigate human error and attacks
MFA is not optional for your teams!

Conclusion
-
Serverless does take away some (not all) security concerns like patching
-
There new attack vectors and mitigating them is key
-
Developer speed and autonomy may threaten your security. Ops need to coach and automate

@EllerbyBen

serverless-transformation

@EllerbyBen
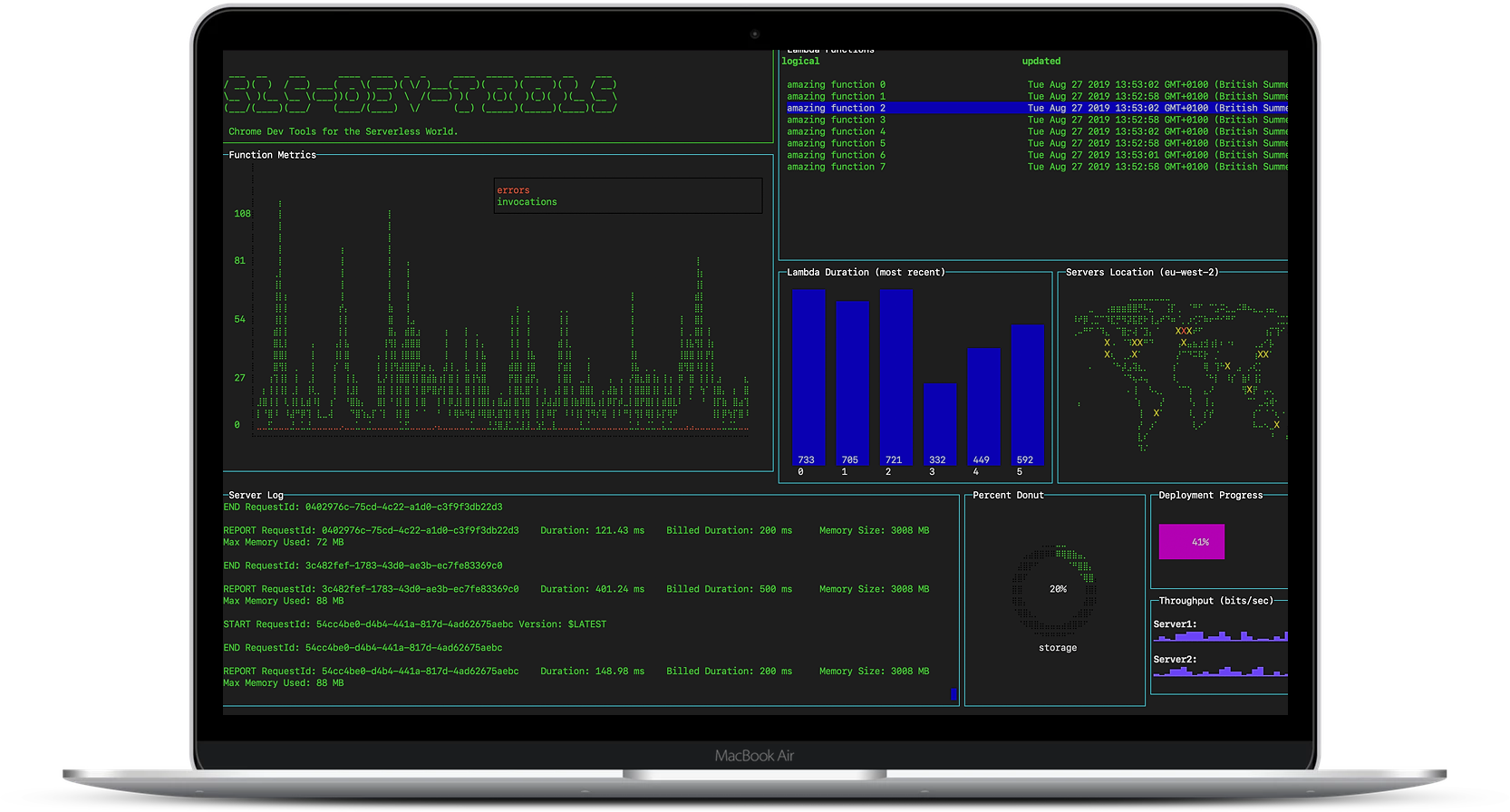
sls-dev-tools


@EllerbyBen
Don't be SecureLess: Best practices for keeping your Lambdas secure
By Ben Ellerby
Don't be SecureLess: Best practices for keeping your Lambdas secure
Talk given at the AWS Community Summit.
- 3,397



