ThunderBolt

-
Developed by Intel with collaboration of Apple
Why ThunderBolt?
-
Large data loads on set and in post production-
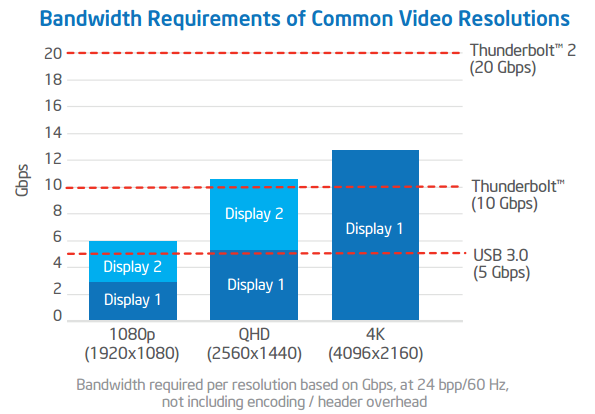
4K Display
-
-
Massive data movement requirements-
Data transfers for backup, sharing, and editing
-

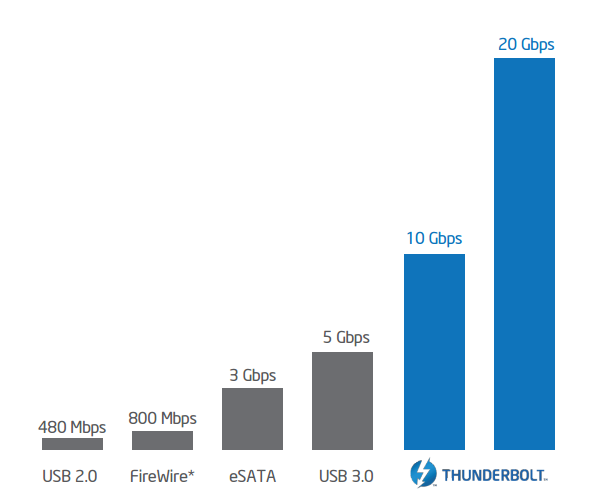
How fast is ThunderBolt?
Working

one simple port and a cable that carries
DisplayPort
PCI Express data

Working

Protocol Architecture
Protocol Architecture
-
Based on switched fabric architecture with full duplex link
Protocol Architecture
-
Full bandwidth of the link in both direction
-
Cables
-
Uses an active cable
-
boost the power of the signal
-
error checking of the incoming transmissions
-
-
Electrical
-
Connections upto 3 meters
-
Up to 10W of power deliverable to a bus-powered device
-
-
Optical
-
Longer Range
-
-
Electrical/ Optical Layer
Controller Architecture

Frame Format

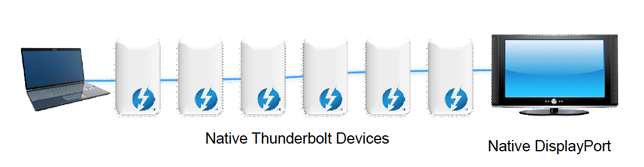
Works in Daisy Chain
-
Supports up to seven chained devices
-
Five devices and two Thunderbolt-based displays
-
Six devices and one Thunderbolt-based display
-
Six devices and one display via mini-DisplayPort adapter
-
Five devices, one Thunderbolt-based display, and one display via mini-DisplayPort adapter
Features Summary
-
10Gbps bi-directional, dual channel data transfer
-
Data & Video on single cable with Dual-protocol (PCI Express and DisplayPort)
-
Daisy chain up to six devices
-
Compatible with existing DisplayPort devices
-
Low latency with highly accurate time synchronization
-
Uses native PCIe and DisplayPort protocol software drivers
-
Power over cable for bus-powered devices (electrical cables only)
What Next?
ThunderBolt 2

Vulnerability
DMA attacks
-
If users extend the PCI Express bus
-
Allows very low-level access to a computer system
-
-
System-bus devices usually have unlimited access to memory
-
Could be used to compromise security by performing DMA attacks
Option ROM attacks
-
When a system with Thunderbolt boots,
-
It loads and executes Option ROMs from attached devices.
-
Malware can begin execution before OS.
-
-
Unless The BIOS or UEFI firmware has some sort of Trusted Boot protection.
-
Such as
-
Enforcing signatures on Option ROMs
-
Whitelisted hashes for known good ROMs
-
What is ThunderBolt
By Bhushan Sonawane
What is ThunderBolt
- 1,074



