Android Security
Activity Hijacking Vulnerability
Parag Dave

OWASP - M5
Poor Authorization and Authentication
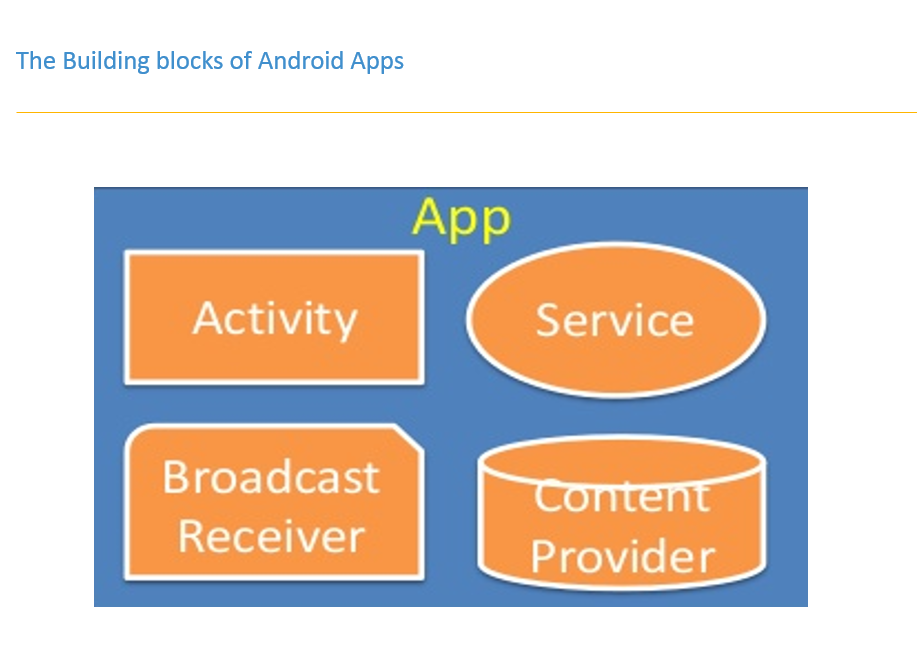
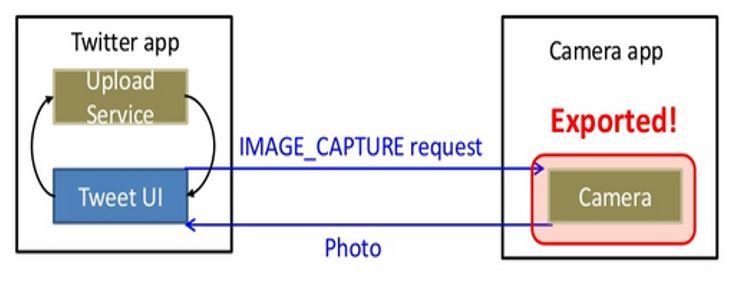
- App components can be exposed to other apps
- Manifest file to define the exposure of components
OWASP - M5
Poor Authorization and Authentication
Exploitability:
Once the adversary understands how the authentication scheme is vulnerable, they fake or bypass authentication by submitting service requests to the mobile app's backend server and bypass any direct interaction with the mobile app. This submission process is typically done via mobile malware within the device owned by the attacker.
OWASP - M5
Poor Authorization and Authentication
Technical Impacts
The technical impact of poor authentication is that the solution is unable to identify the user performing an action request. Immediately, the solution will be unable to log or audit user activity because the identity of the user cannot be established.
Business Impacts
The business impact of poor authentication will typically result in the following at a minimum:
- Reputational Damage
- Fraud
- Information Theft.
OWASP - M5
Set up Prerequisites
Android device
Genymotion + Virtualbox
Victim Apps
Insecure Bank
App type: Finance
Attacker type
Drozer framework client app
Android SDK + Java
Live Demo
Android Security
By Parag Dave
Android Security
Android Activity Hijacking
- 628



