GNAP: The future of OAuth
By Robin Chalas
GNAP: The future of OAuth
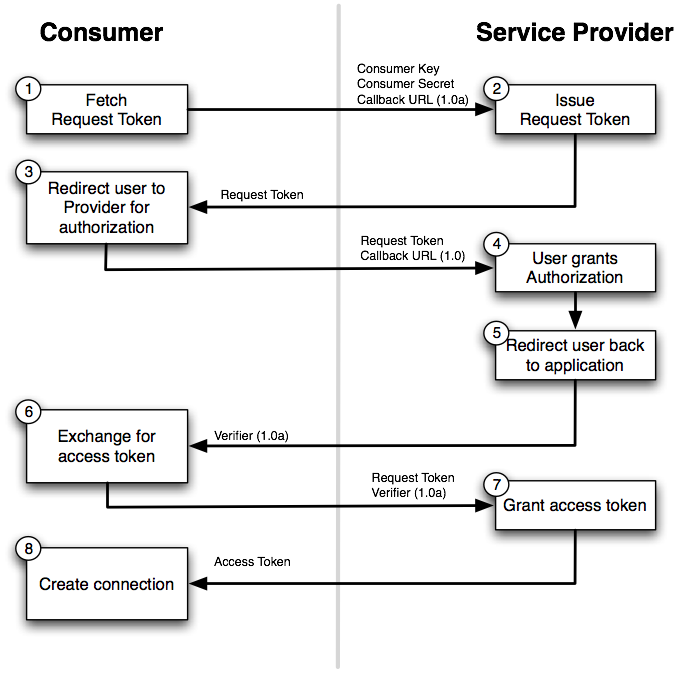
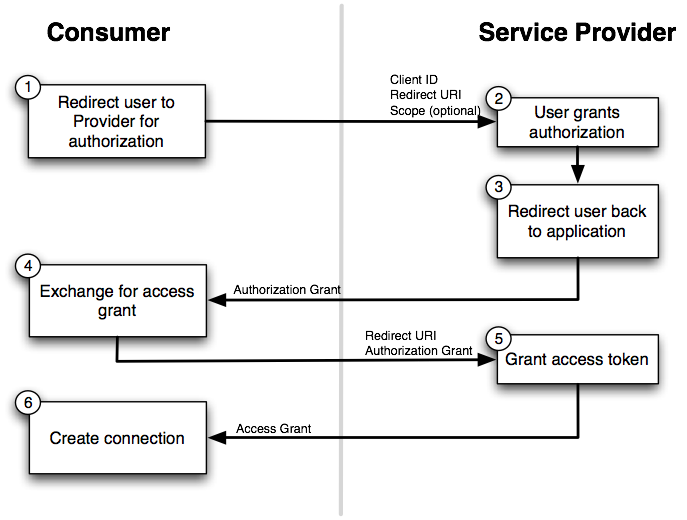
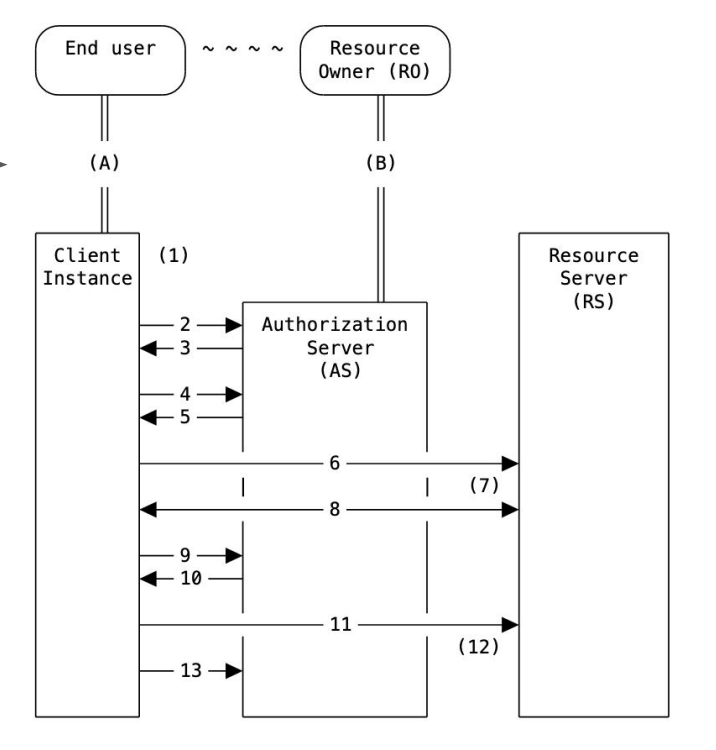
OAuth 2 is an industry-standard for authorization that every developer probably heard about. As hinted by its name, it is the evolution of OAuth 1 and as such; it aims to address most of its known issues. But, just like OAuth 1, OAuth 2 now has a lot of known issues. Fortunately, a lot of these issues have been already fixed by extending the specification. The drawback of this is that today, in order to get OAuth2 right, one needs to read a dozen of RFCs and make sure they are relevant to the use case. This hurts developer experience as it increases the complexity of the protocol, which goes against its main focus: simplicity for client developers. Here comes GNAP (Grant Negotiation and Authorization Protocol): an in-progress effort to develop the next-generation authorization protocol by learning from the past. In this talk, we'll have a deep look into the GNAP protocol, passing by a review of the known OAuth2 flaws that it aims to fix, how it plays with authentication protocols such as Open ID Connect or WebAuthN, what is its current state and more. Delivered in English Room: The Symfony room Thursday, December 8, 2022 at 10:05 AM – 10:40 AM