Meltdown & Spectre Summary
According to Mozilla, "Meltdown and Spectre are remotely exploitable by embedding attack code in mundane JavaScript files delivered via web pages".

Meltdown & Spectre Introduction
Meltdown Summary

What is it?
- The Meltdown vulnerability provides an attacker the possibility of utilizing an unprivileged user process to retrieve data from arbitrary physical memory addresses
How does it work?
- The Meltdown vulnerability is exploited by utilizing out of order execution (a technique used by modern processors to improve performance) to leak data
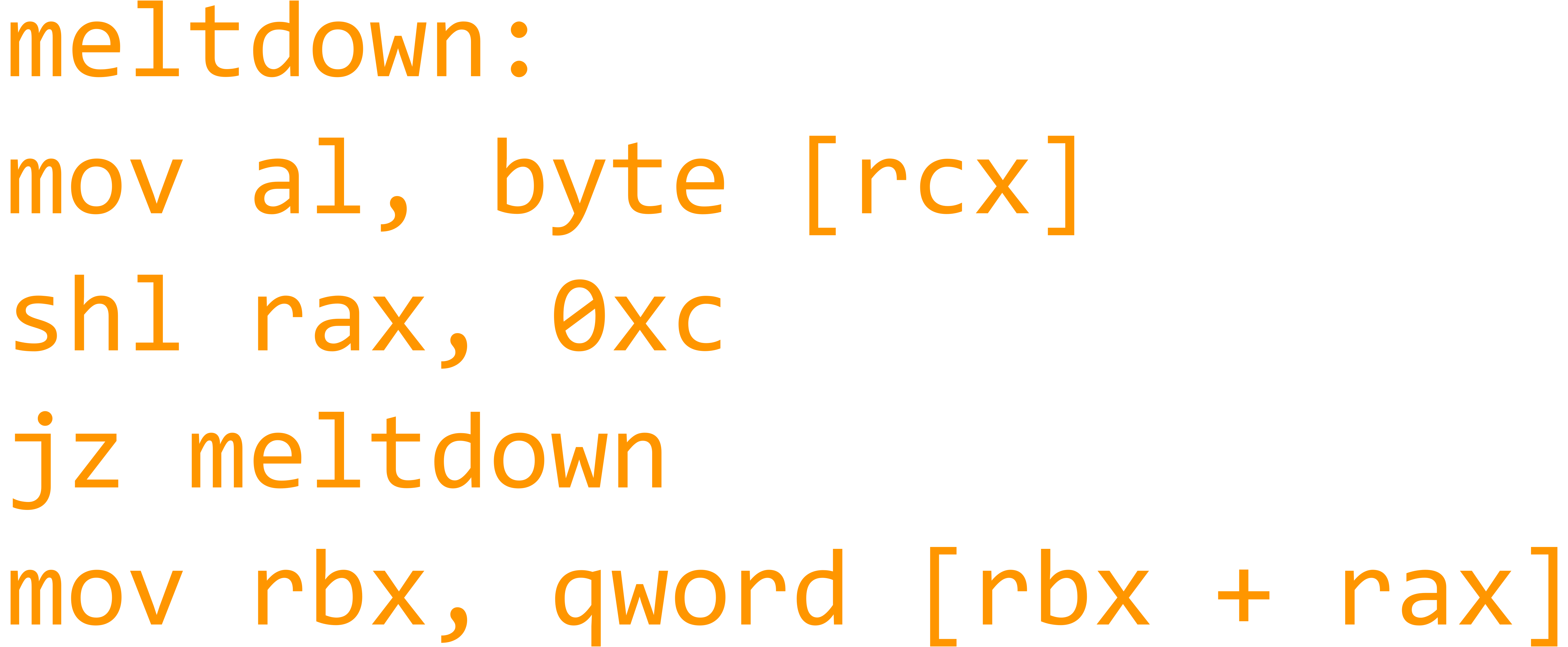
Who is affected?
- According to Google's Project Zero research, computer processors since 2011 were tested vulnerable, and computer processors since 1995 are theoretically vulnerable
- Virtually everyone is affected
- Intel CPUs have been tested to be vulnerable, while AMD CPUs and ARM CPUs are theoretically vulnerable; however, no practical exploit exists for both AMD and ARM CPUs
Google Project Zero Meltdown & Spectre Research: https://googleprojectzero.blogspot.my/2018/01/reading-privileged-memory-with-side.html
What are the possible exploit scenarios?

Possible Meltdown Attacks
- Privilege Escalation
- Container/Paravirtualization Hypervisor Escape
1. Privilege Escalation
Although Meltdown is a read-only threat which does not allow arbitrary execution of code, the impact of Meltdown and its risk comes from the ability to retrieve sensitive data from arbitrary memory addresses.
- Password hashes
- Private keys
- Other credentials
As a result, any attacker can execute a user process on any unpatched system and dump memory from nearly the entire physical memory, gaining credentials for privilege escalation
2. Container/Paravirtualization Hypervisor Escape
As a result of being able to retrieve data from arbitrary physical memory addresses, confidential data in hypervisor containers can be leaked. A major cause for concern are corporations that utilize cloud services running in virtual operating systems hosted within hypervisors.
Spectre Summary

What is it?
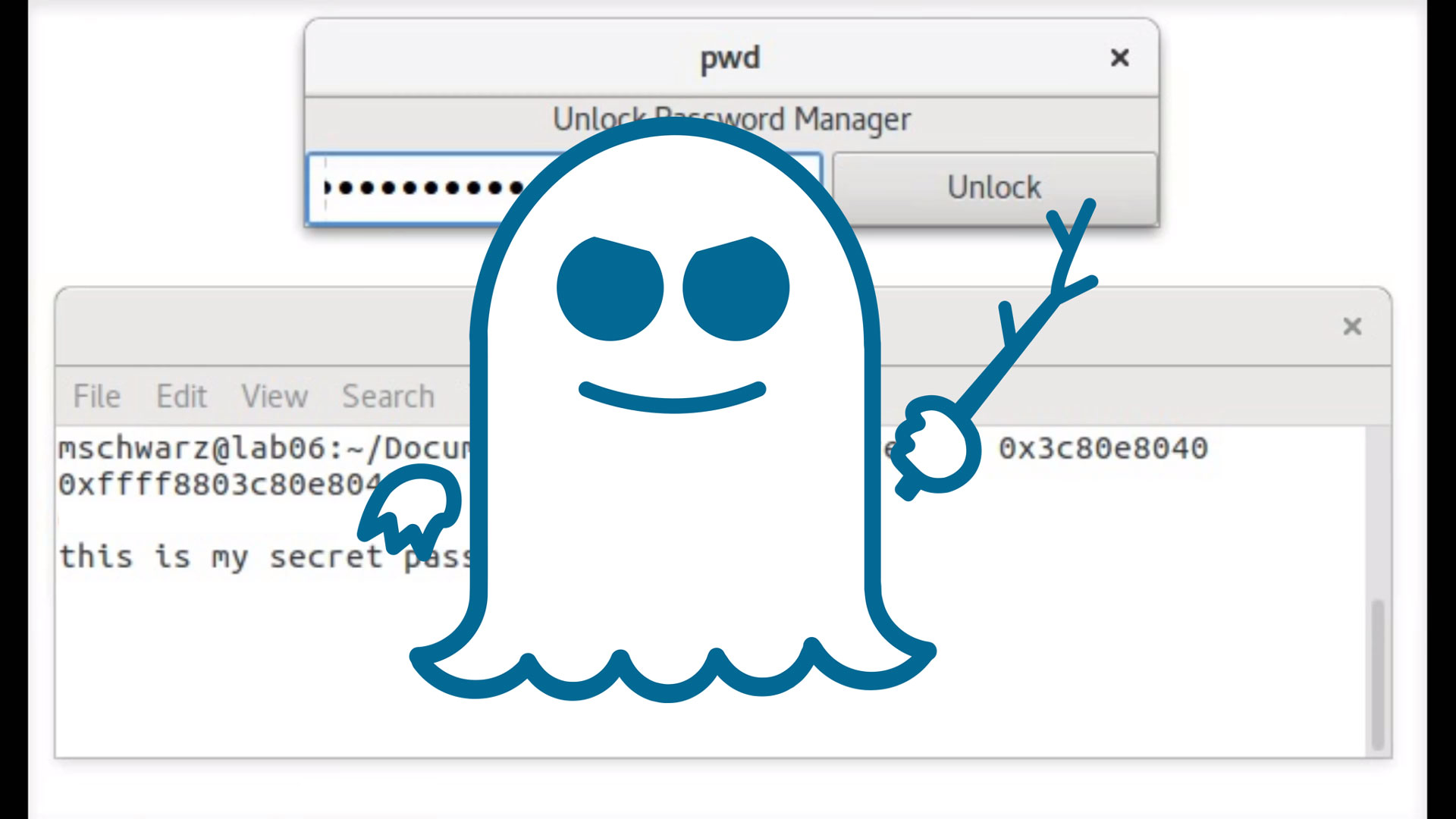
- The Spectre vulnerability provides an attacker the possibility of retrieving data from physical memory addresses but within the current process only
- Although this is a read-only threat which does not allow arbitrary execution of code, the impact of Meltdown and its risk comes from the ability to retrieve sensitive data in memory, such as plain text credentials
How does it work?
- The Spectre vulnerability is exploited by abusing branch prediction and speculative execution (a technique used by modern processors to improve performance) to leak data

Who is affected?
- According to Google's Project Zero research, computer processors since 2011 were tested vulnerable, and computer processors since 1995 are theoretically vulnerable
- Virtually everyone is affected
- Intel, AMD, and ARM CPUs have been tested to be vulnerable
Google Project Zero Meltdown & Spectre Research: https://googleprojectzero.blogspot.my/2018/01/reading-privileged-memory-with-side.html
What are the possible exploit scenarios?
Possible Spectre Attacks
- Leaking confidential data outside of JavaScript sandbox
- Leaking addresses of user space modules to bypass ASLR
- Leaking confidential data outside of JavaScript sandbox
Exploits can be written in JavaScript and deployed (perhaps in pop-ups or advertisements) to leak browser cache, which may contain confidential information from the victim's visited sites
2. Leaking addresses of user space modules to bypass ASLR
Spectre exploits allow attackers to determine the physical memory address of user modules stored in memory, allowing attackers to bypass ASLR, introducing more threats, because protection against threats that are mitigated by address space layout randomization is broken
Are there patches available for Meltdown and Spectre?
-
Patched in Linux (Kaiser/KPTI)
- How to patch: https://www.cyberciti.biz/faq/patch-meltdown-cpu-vulnerability-cve-2017-5754-linux/
- Patch does not directly mitigate the Meltdown threat; however, it prevents practical exploitation. This patch does not mitigate Spectre threat.
- Introduces a performance impact, though arguably non-negligible in certain circumstances
-
Patched in Windows
- How to patch: https://support.microsoft.com/en-us/help/4072699/january-3-2018-windows-security-updates-and-antivirus-software
- Supported antivirus software with Windows update: https://docs.google.com/spreadsheets/d/184wcDt9I9TUNFFbsAVLpzAtckQxYiuirADzf3cL42FQ/htmlview?usp=sharing&sle=true
-
Mozilla Browser
- Temporary mitigation by updating to Firefox 57.0.4 onwards. (Reducing precision of timers provided by performance.now())
-
Chrome Browser
- Temporary mitigation by updating to Google Chrome 64 onwards (available January 23rd, 2018 onwards)
- Temporary mitigation by enabling site isolation: bit.ly/ChromeSiteIsolation (Each website is loaded into a different process)
| Meltdown | Spectre | |
|---|---|---|
| Arbitrary Kernel Memory Read | Yes | No |
| Practical Exploits Against CPUs | Intel | Intel, ARM, AMD |
| Remote Execution | Depends on situation | Definitely |
| Arbitrary User Memory Read | Yes | Yes |
| Highest Area of Impact | Kernel Integrity | Browser Memory |
Meltdown vs Spectre
References
- https://spectreattack.com/spectre.pdf
- https://spectreattack.com/meltdown.pdf
- https://www.renditioninfosec.com/files/Rendition_Infosec_Meltdown_and_Spectre.pdf
- https://googleprojectzero.blogspot.my/
Meltdown & Spectre
By chananloh
Meltdown & Spectre
Brief Summary of Meltdown and Spectre
- 475


