Teach a Man to Phish
Give a man an 0day and he'll have access for a day, teach a man to phish and he'll have access for life."
Information Security
Is Hard
What is InfoSec?
"Information Security is the practice of preventing unauthorized access, use, disclosure, disruption, modification, inspection, recording or destruction of information."
The focus of InfoSec is balancing protection of the Confidentiality, Integrity and Availability of data. Data security should focus on effective policies that don't impede operational efficiency.
Threat Modeling
- Assets
- Threats
- Vulnerabilities
more info: https://www.owasp.org/index.php/Application_Threat_Modeling
Data!
Notes About PHI
PHI: health status, provision of health care, or payment for health care created or collected by a Covered Entity
- Difficult/impossible to change if compromised
- Can be used to commit health care fraud or other identity theft
- Can be held for ransom
What are the threats we
might be facing?

The Government?

Hackers?

Organized Crime?

Where are we vulnerable?
Some Areas of Vulnerability
- Servers
- People
- Login systems
- Connections to 3rd parties
Meltdown and Spectre


Meltdown
This exploit breaks application isolation and allows one program running on an OS to access memory used by other applications. We were vulnerable to this until Aptible rolled out a fix early this week!
Spectre
Spectre exploits a CPU's speculative execution of code and can be used to read data from the CPU's cache. This can allow attackers to access things like passwords typed into different browser tabs.
https://meltdownattack.com/
Phishing

Common Phishing Attacks
- Deceptive Phishing - pretending to be a legitimate site
- Spear Phishing - highly personalized
- CEO fraud - spear phishing directed at CEOs
- Pharming - redirecting http traffic
- Dropbox Phishing - harvesting credentials with dropbox links
- Google Docs Phishing
Login and 3rd Parties
- Http can leak credentials
- Sending unnecessary info risks leaks
- Giving access to 3rd parties exposes our system to 3rd party risk
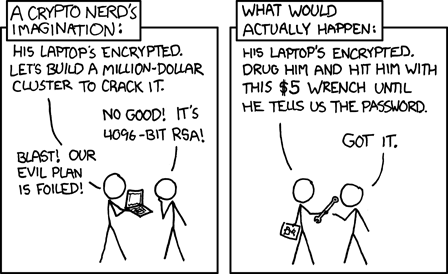
Sometimes you just fail.
What can we do?
- mitigate – build layers of defence to address our assessed threats and vulnerabilities
- transfer – outsource some risk where we don't have a core competency. (like Aptible)
- accept – weigh costs and benefits, no security is perfect and near perfect might be prohibitively expensive
Mitigation
- Defense in Depth
- Good Policies
- Training
- Cryptography
Cyber Security!

Further Reading
- https://krebsonsecurity.com/
- https://meltdownattack.com/
- https://medium.com/@thegrugq/
- https://www.owasp.org/index.php/Category:Vulnerability
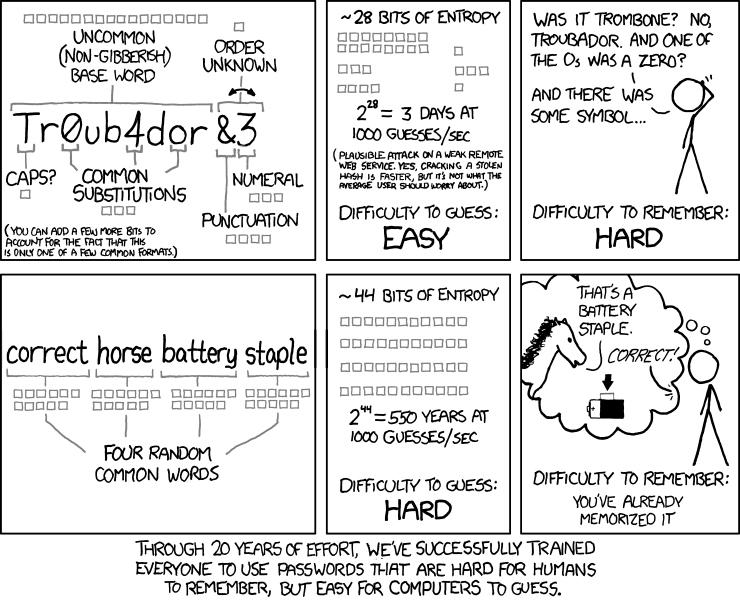
Thanks for listening,
please use a password manager.
phishing and phrends
By Chase Gilliam
phishing and phrends
- 265



