
Safe
&
Sound
Threat Modeling and Holistic Security
Rory Mir
@_falsemirror
cypurr.nyc
slides.com/cypurr/safe-and-sound/
Outline:
- Intro
- Holistic Security Approach
- Threat Modeling/Analysis
- Security Planning
- Thank You/Resources
Who are we?
- We are…
- The Cypurr Collective
- In bk/nyc
- Cat enthusiasts
- Tech unenthusiasts
- Coming from a queer/feminist/anti-capitalist lens
- Members of the Electronic Frontier Alliance
- Here to learn from you as well

Who are you?
- You're welcome to pass on intros!
- Name
- Pronouns (he/him, she/her, they/them, etc)
- What brings you here today?
Ground Rules
-
Saf(er) Space
-
We DO NOT tolerate demeaning/harmful language or behavior
-
Don't pressure or question someone discussing their experience/threat model/situation
-
Consent: Ask before helping someone out! From unsolicited advice to grabbing someones phone.
-
-
Keep it constructive!
-
Share the space!
-
Stack! Raise your hand, we'll queue speakers
-
-
Photo/Video- Ask for approval!
-
Identify yourself if you are a...
-
reporter, researcher, or law enforcement
-

Warmup
What are some things you consider when you...
- Going home late at night
- Leaving your home/apt for an extended period of time
- Have visitors staying with you
- Traveling in an unfamiliar place

Today's Scenario
What's an example scenario?
This can be real, theoretical or even fantastical (e.g. Frodo Baggins)
- Who are we?
- Where/when are we?
- What are our goals?
- Who has conflicting goals?

Holistic Approach


https://myshadow.org/
Holistic Approach


Balance > Purity Growing > Finishing
Finding Balance


Sleeping less
Taking more breaks
Support with
workload
Balance Threats

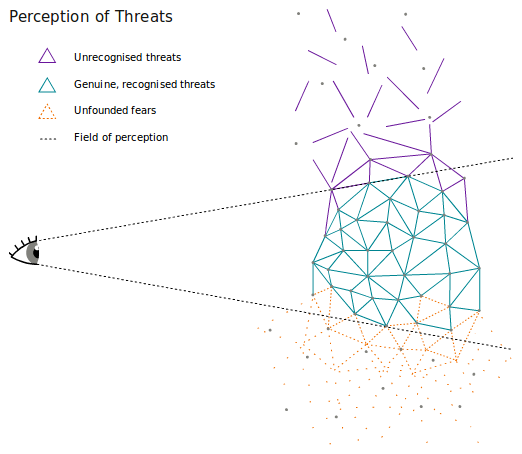

Threat Responses

- Groups
- Harder Group Boundaries
- Authoritarianism
- Fixed Patterns
- Individuals
- Freeze
- Fight
- Flight
- Comply
- Tend
- Befriend
- Posture

Threat Modeling
- What is being protected?
- Assets
- Who am I protecting it from?
- Adversaries
- How likely is this threat?
- Capabilities
- What are the consequences of failure?
- Threat
- How much trouble am I willing to go through to prevent the consequences?
- Risk

ssd.eff.org

Threat Analysis
Situation (PESTLE)
- Political
- Economic
- Scientific
- Technological
- Legal
- Environmental

Threat Analysis
Actor Mapping

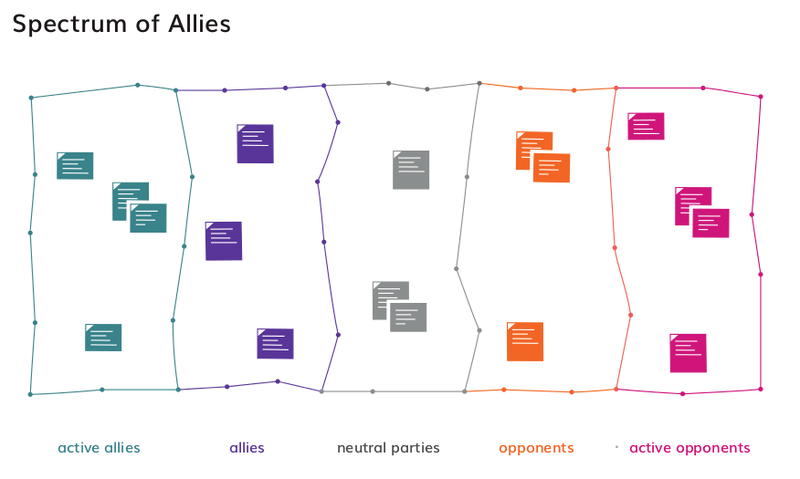
You
Me
Her


Them
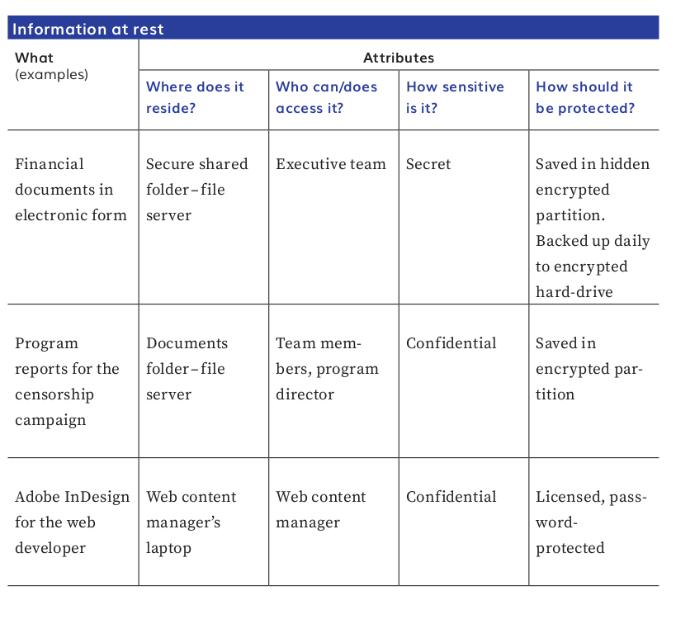
Info at Rest

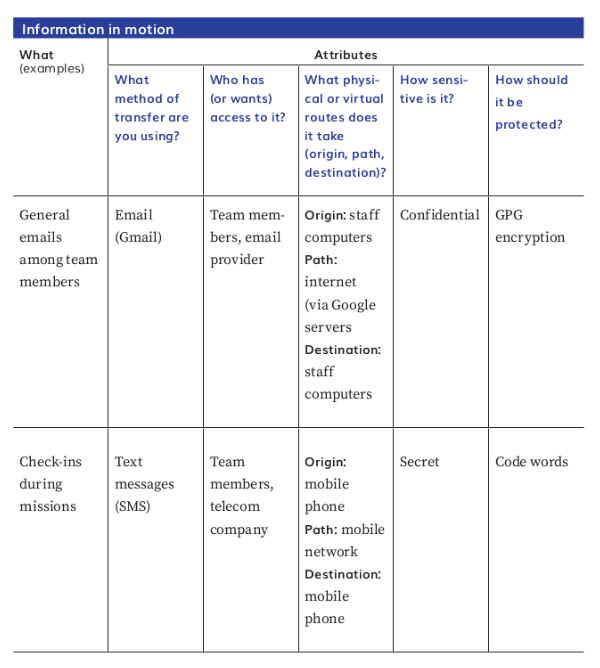
Data in Motion

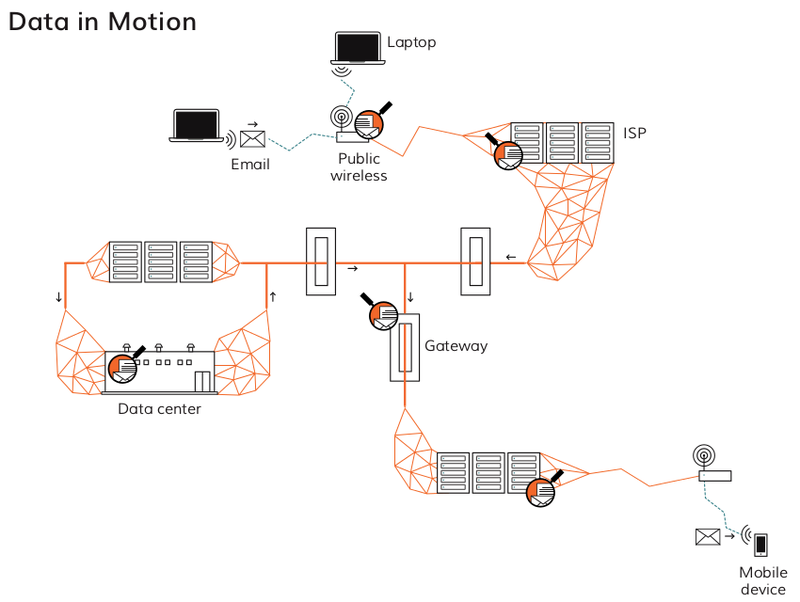



Info in Motion




Security Indicators
- Security indicator vs. Threat
- Indicator is the instance
- Threat is the feeling that an instance will bring harm, or that a series of instances will bring harm
- Something out-of-the-ordinary?
- Negative: I’m being followed by a van
- Positive: a strong ally just gave us some funds!!!!!!!!!
- Making space to share
- Keeping track
Security Debrief
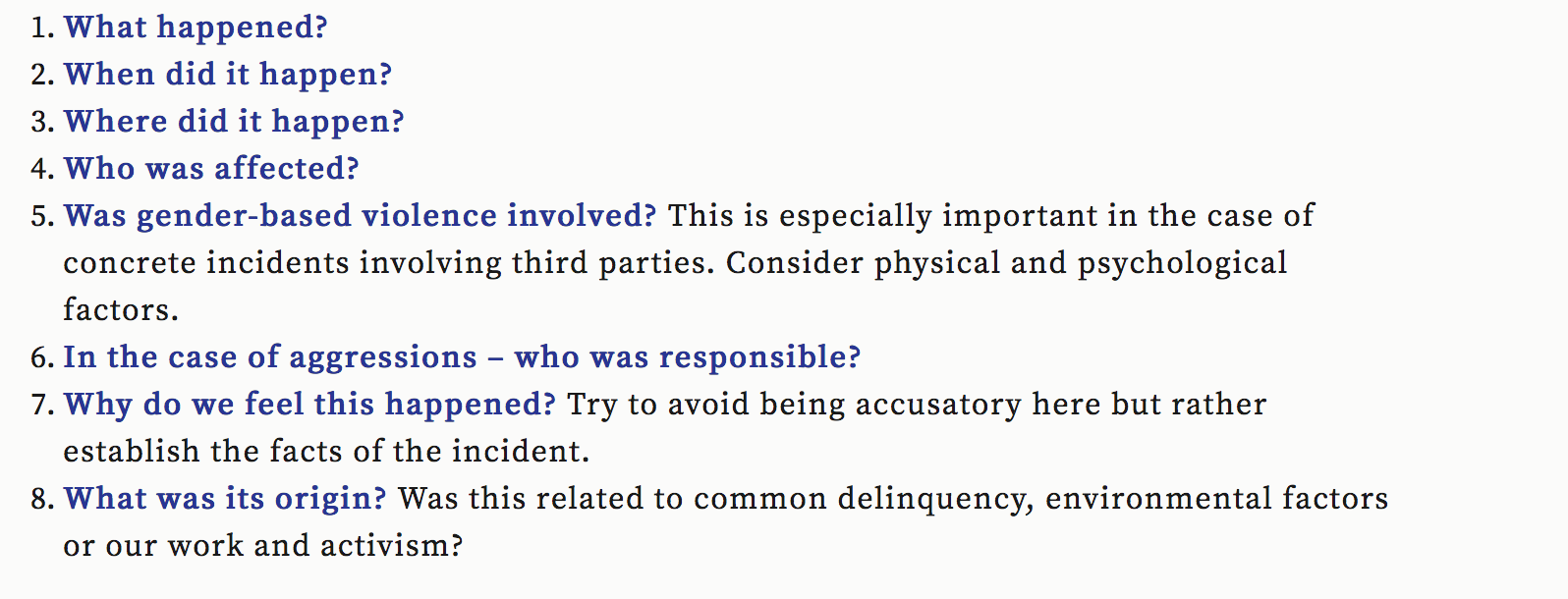
Security Debrief
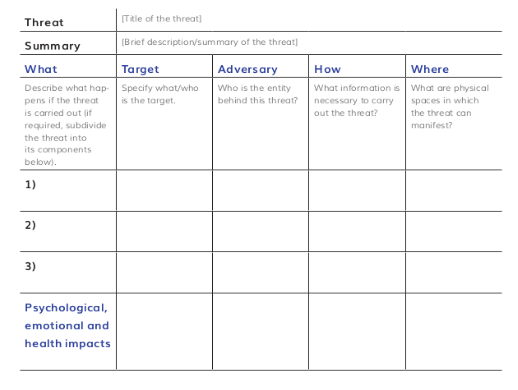

Security Planning
Include:
- Objective
- Threat(s) identified
- Preventative actions/resources
- Response to emergency situation
- (define an emergency)
- Communication practices and devices
- Self-care and well-being
Which strategies are already working?
Which need work?
Security Planning Strategies
- Acceptance
- Build support/allies
- Deterrence
- Make attacks more costly
- Protection
- building strength to make attack harder


Summary
- Prioritize Security in planning convos
- Not antithetical to action/progress/success
- Create Safe Space for these discussions
- Talk regularly!
- Schedule debriefs and refreshers
Resources
-
CyPurr Collective- cypurr.nyc and cypurr@protonmail.com
-
NYC CryptoParty and Meetup.com for other events
- Tactical Tech Collective- tacticaltech.org
- EFF- Surveillance Self Defense (ssd.eff.org) Security Edu Companion (sec.eff.org)
-
Freedom of the Press Foundation (Freedom.press)
- Tool Recommendations
- privacytools.io
- prism-break.org
- Self defense- Pop Gym (@popgymbk)
Upcoming
- Brooklyn Public Library- Central branch (1st Sundays)
- Babycastles Movie Night- Dec 5th
- Hacker Next Door- Dec 14th
- securiTEA (3rd Sundays)
- Monthly Open Meeting tbd
Thank You!

Safe and Sound: Threat Modeling & Holistic Security
By cypurr
Safe and Sound: Threat Modeling & Holistic Security
- 350



