AWS Identity and Access Management (IAM)
Hands-On
Demo


Create User 1
developer1



Review and create

Console sign-in details
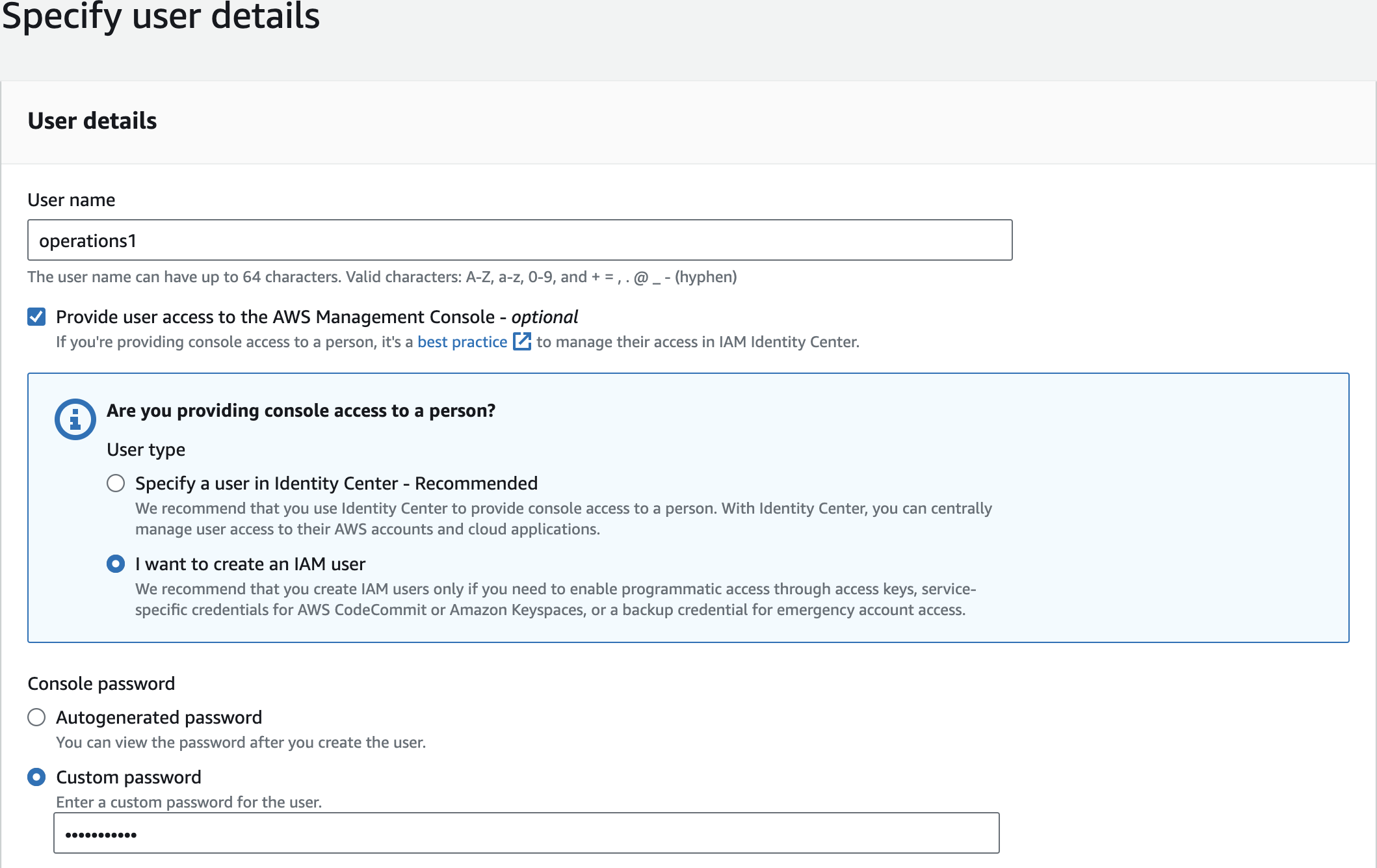
operations1Create User 2






Review and create

Console sign-in details


Create user group
Developers






Create user group 2
Operations






my-company-data-719246Create bucket for Test Policy

{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets",
"s3:GetBucketLocation"
],
"Resource": "arn:aws:s3:::*"
},
{
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetObject",
"s3:PutObject",
"s3:DeleteObject"
],
"Resource": [
"arn:aws:s3:::my-company-data-719246",
"arn:aws:s3:::my-company-data-719246/*"
]
}
]
}Create Policy 1

DeveloperS3AccessReview and create

Create policy

Attach Policy to Developers Group

DeveloperS3AccessAttach permission policies to Developers

Create Policy 2
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:*",
"cloudwatch:*",
"s3:*"
],
"Resource": "*"
}
]
}
OperationsAccessReview and create

Create policy

Attach Policy to Operations Group

OperationsAccess
Fresh AWS Account - Only 2 Roles

Create role


AmazonS3ReadOnlyAccessAdd permissions

EC2S3ReadOnlyRole details

Create role

Difference between User Group and Role
Test

Login as developer1 - S3 View

Login as developer1 - EC2 View

Login as operations1 - S3 View

Login as operations1 - EC2 View
Clean Up

Delete Policies
DeveloperS3Access
Delete Policies

Delete Policies
OperationsAccess
Delete Policies

Delete Role


Delete Users


Delete User Groups
🙏
Thanks
for
Watching
AWS IAM - Hands-On Demo
By Deepak Dubey
AWS IAM - Hands-On Demo
AWS IAM - Hands-On Demo
- 274



