AWS Organizations
Hands-On
Demo

In this Demo, we will:
- Create AWS Organization.
- Create Production and Development OUs.
- Create Development SCP (t2/t3 instances, region limits).
- Create Production SCP (encryption, deletion protection).
- Setup Development tags (Environment, Project).
- Setup Production tags (Environment, CostCenter, BusinessUnit).
- Enable tag policy reporting.
- Attach and test policies.
Agenda

Create an organization


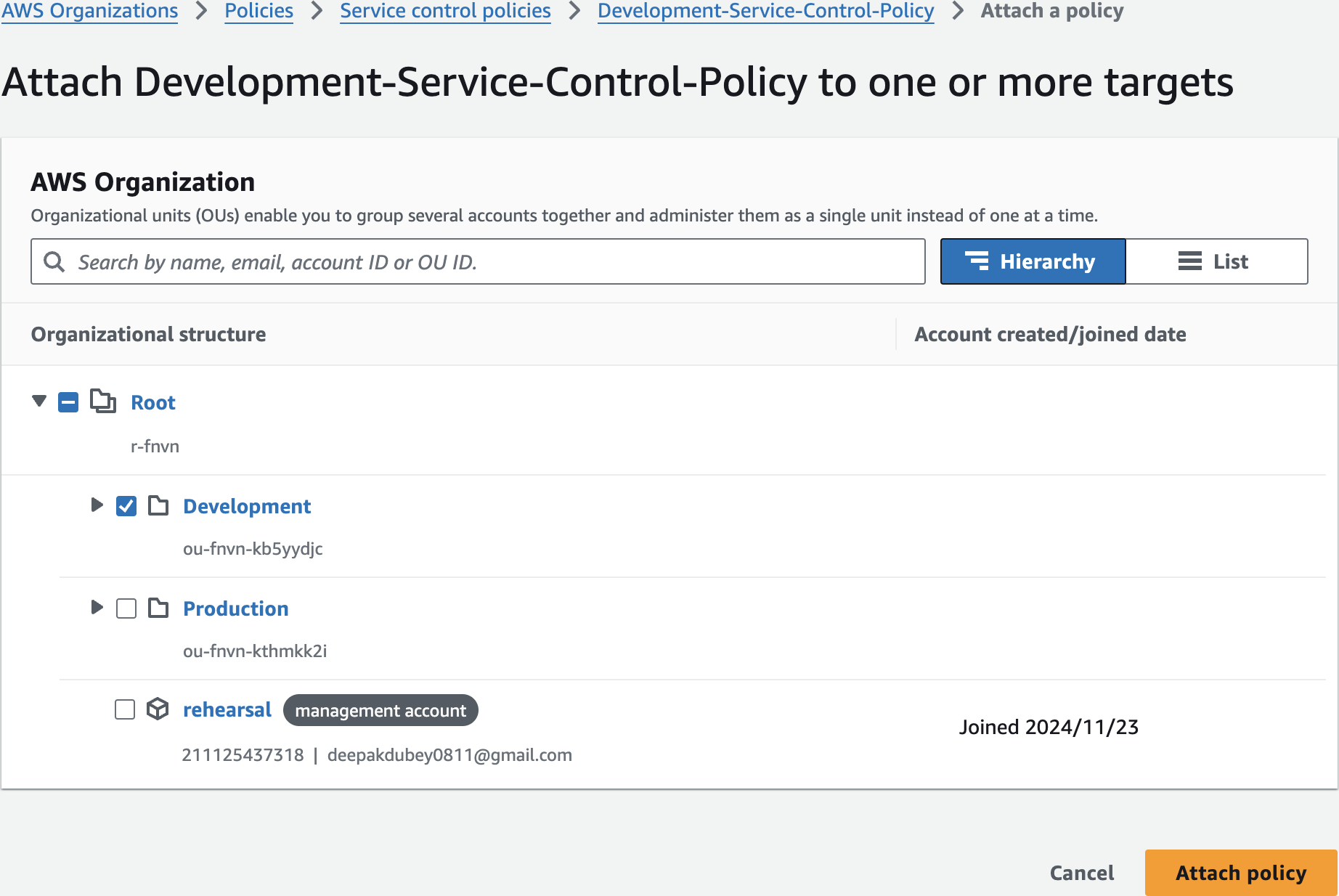
Create 1st Organizational Unit (OU)

Production
Create 2nd OU - Development

Add 1st AWS account

prod-accountlearnpde+prod@gmail.com
Create AWS account

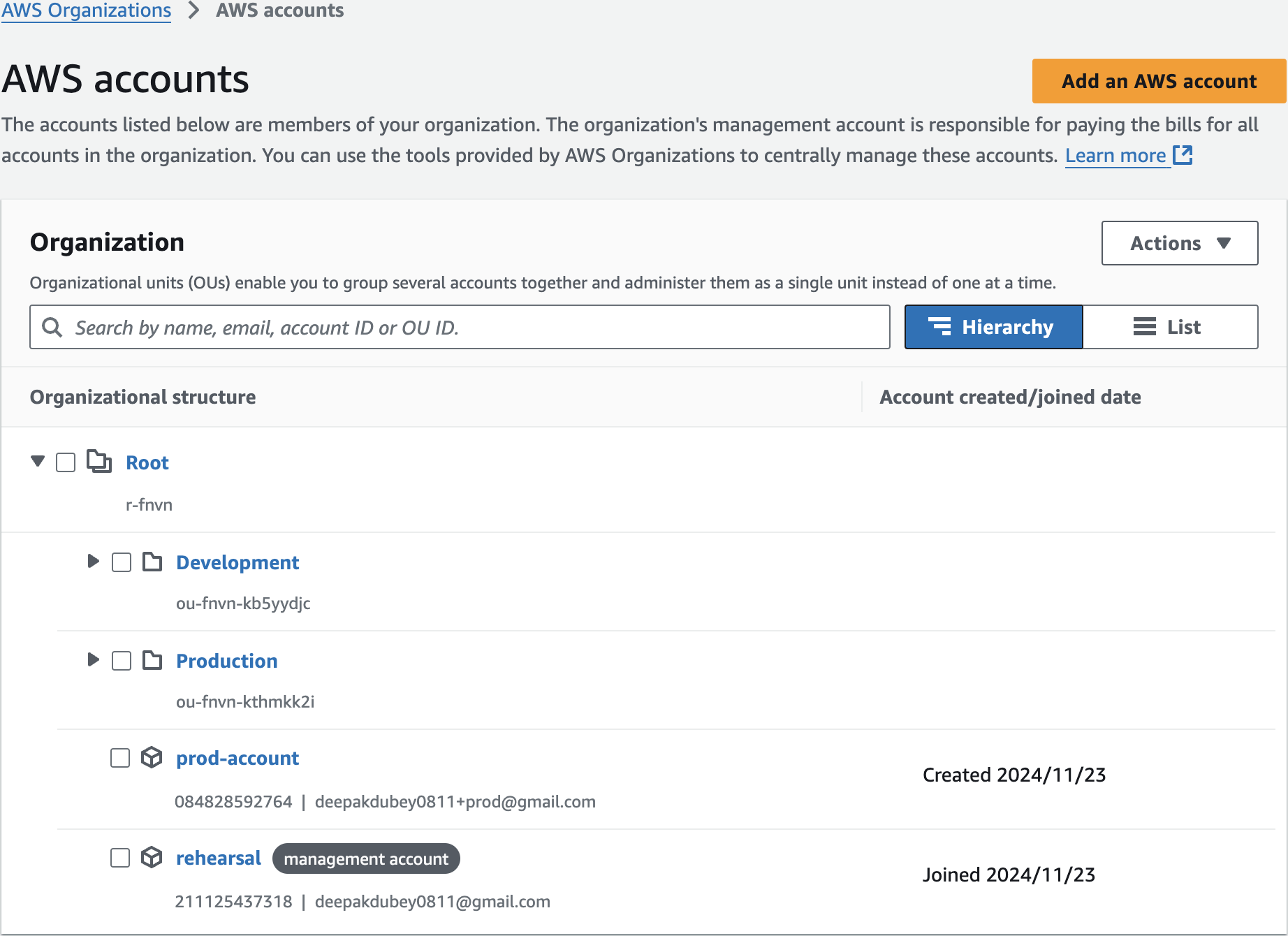
Create 2nd Account

learnpde+dev@gmail.comdev-account


Move Prod


Move Dev Account



Policies


Enable Service control policies

Create new service control policy
Development-Service-Control-Policy{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "LimitEC2InstanceTypes",
"Effect": "Deny",
"Action": "ec2:RunInstances",
"Resource": "arn:aws:ec2:*:*:instance/*",
"Condition": {
"StringNotLike": {
"ec2:InstanceType": [
"t2.*",
"t3.*"
]
}
}
},
{
"Sid": "DenyNonApprovedRegions",
"Effect": "Deny",
"Action": "*",
"Resource": "*",
"Condition": {
"StringNotEquals": {
"aws:RequestedRegion": [
"us-east-1",
"us-west-2"
]
}
}
}
]
}Development-Service-Control-Policy


Attach policy to Development OU
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "EnforceProductionRegions",
"Effect": "Deny",
"Action": "*",
"Resource": "*",
"Condition": {
"StringNotEquals": {
"aws:RequestedRegion": [
"us-east-1",
"us-west-2"
]
}
}
},
{
"Sid": "RequireEncryptedEBSVolumes",
"Effect": "Deny",
"Action": [
"ec2:RunInstances",
"ec2:CreateVolume"
],
"Resource": [
"arn:aws:ec2:*:*:volume/*",
"arn:aws:ec2:*:*:instance/*"
],
"Condition": {
"Bool": {
"ec2:Encrypted": "false"
}
}
},Production-Service-Control-Policy
{
"Sid": "DenyDeleteProductionTags",
"Effect": "Deny",
"Action": [
"ec2:DeleteTags",
"s3:DeleteObjectTagging",
"rds:RemoveTagsFromResource"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:ResourceTag/Environment": "Production"
}
}
},
{
"Sid": "RequireResourceTags",
"Effect": "Deny",
"Action": [
"ec2:RunInstances",
"rds:CreateDBInstance",
"s3:CreateBucket"
],
"Resource": "*",
"Condition": {
"Null": {
"aws:RequestTag/Environment": "true",
"aws:RequestTag/CostCenter": "true",
"aws:RequestTag/Project": "true"
}
}
}
]
}Production-Service-Control-Policy

Attach Production Service Control Policy


Enable tag policies

Create Dev Tag Policy
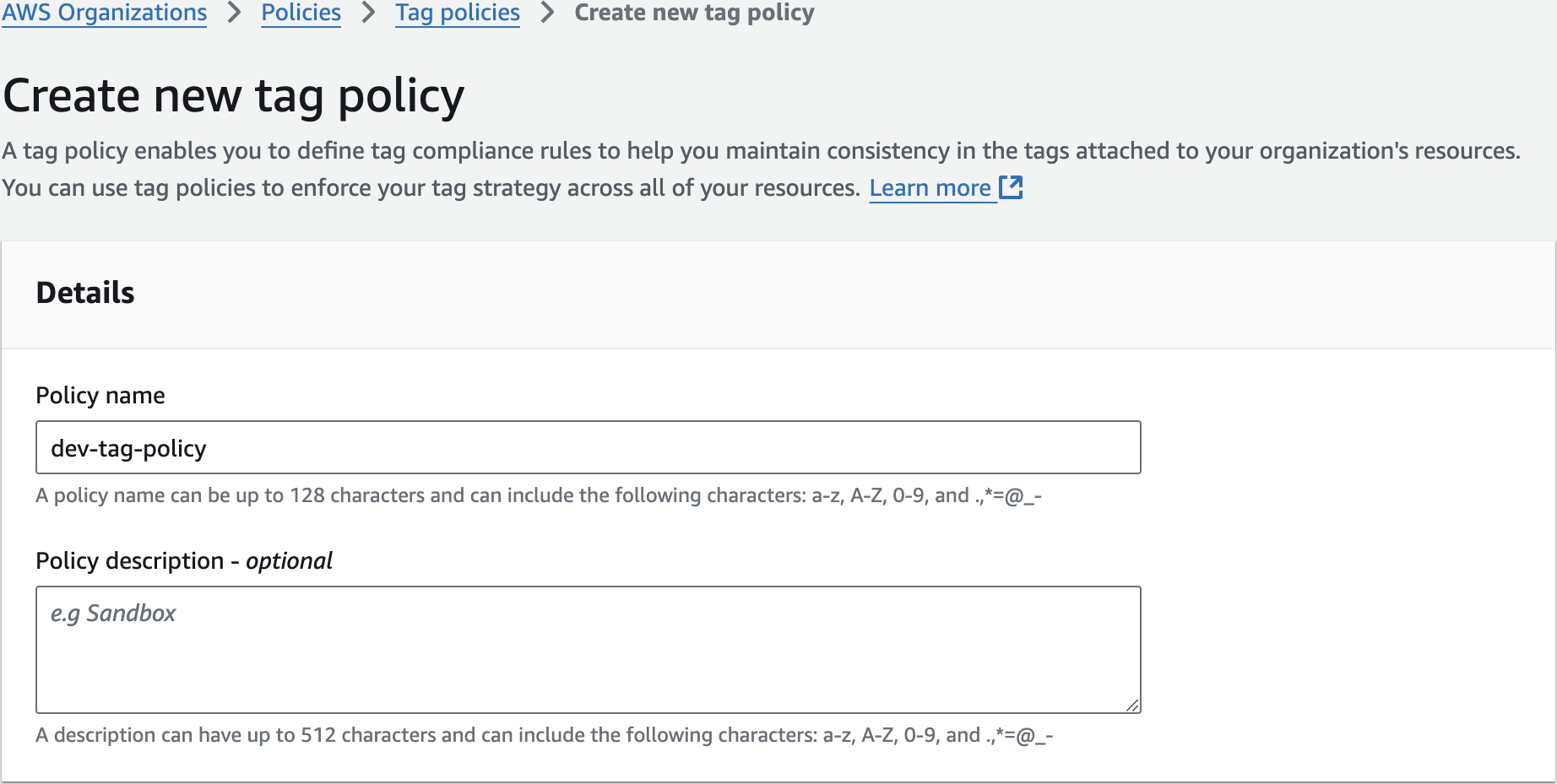
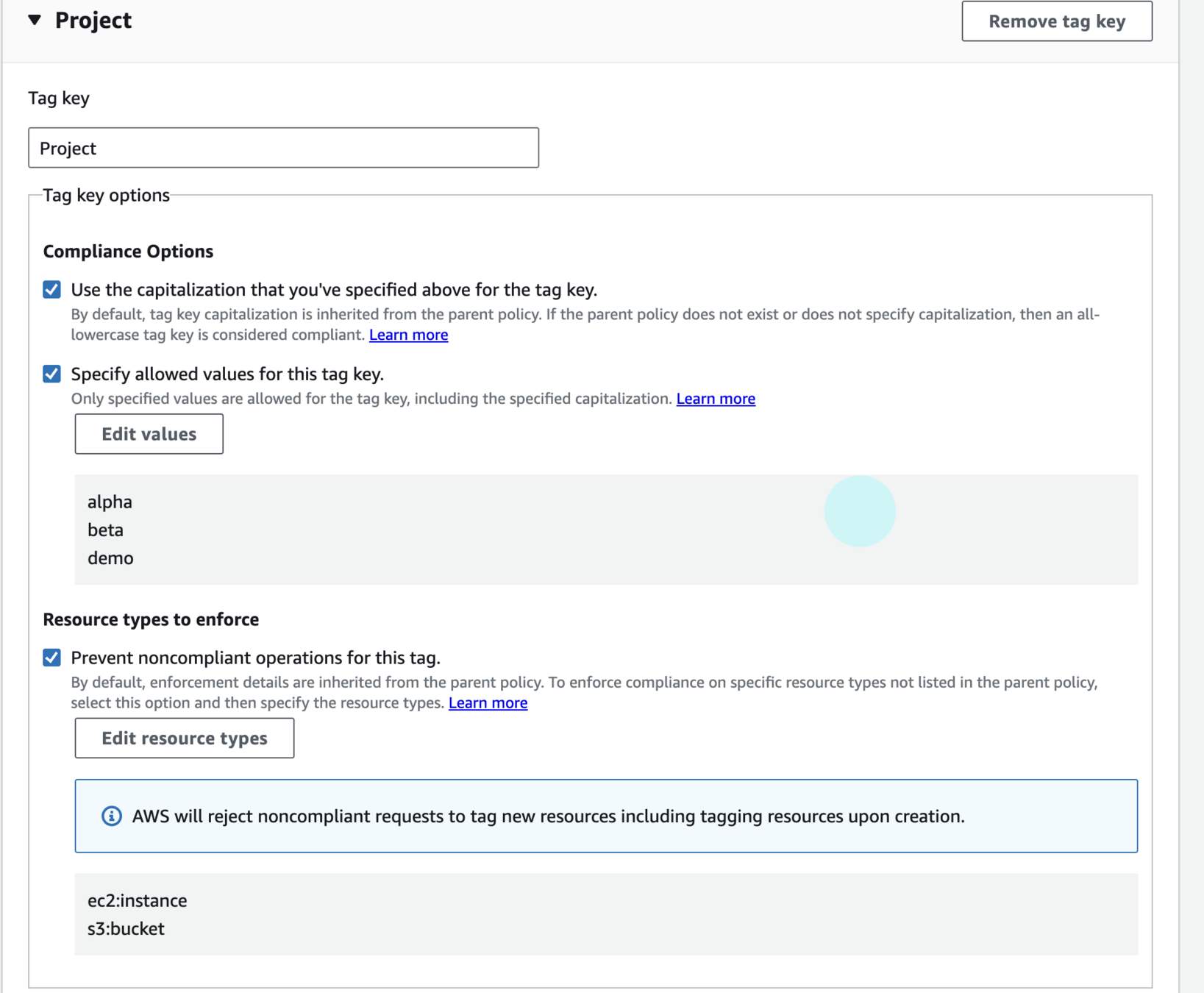
dev-tag-policy{
"tags": {
"Environment": {
"tag_key": {
"@@assign": "Environment"
},
"tag_value": {
"@@assign": [
"dev"
]
},
"enforced_for": {
"@@assign": [
"ec2:instance",
"s3:bucket"
]
}
},
"Project": {
"tag_key": {
"@@assign": "Project"
},
"tag_value": {
"@@assign": [
"alpha",
"beta",
"demo"
]
},
"enforced_for": {
"@@assign": [
"ec2:instance",
"s3:bucket"
]
}
}
}
}


prod-tag-policyCreate prod tag policy
{
"tags": {
"environment": {
"tag_key": {
"@@assign": "Environment"
},
"tag_value": {
"@@assign": [
"prod"
]
},
"enforced_for": {
"@@assign": [
"ec2:instance",
"s3:bucket"
]
}
},
"costcenter": {
"tag_key": {
"@@assign": "CostCenter"
},
"tag_value": {
"@@assign": [
"101",
"102",
"103"
]
},
"enforced_for": {
"@@assign": [
"ec2:instance",
"s3:bucket"
]
}
}
}
}


Attach Dev tag policy to Dev OU


Attach Prod tag policy to Prod OU

Login to Dev AWS Account
https://796973489092.signin.aws.amazon.com/console
Sign in and select Forgot Password

Launch T2 Large
T2-Large

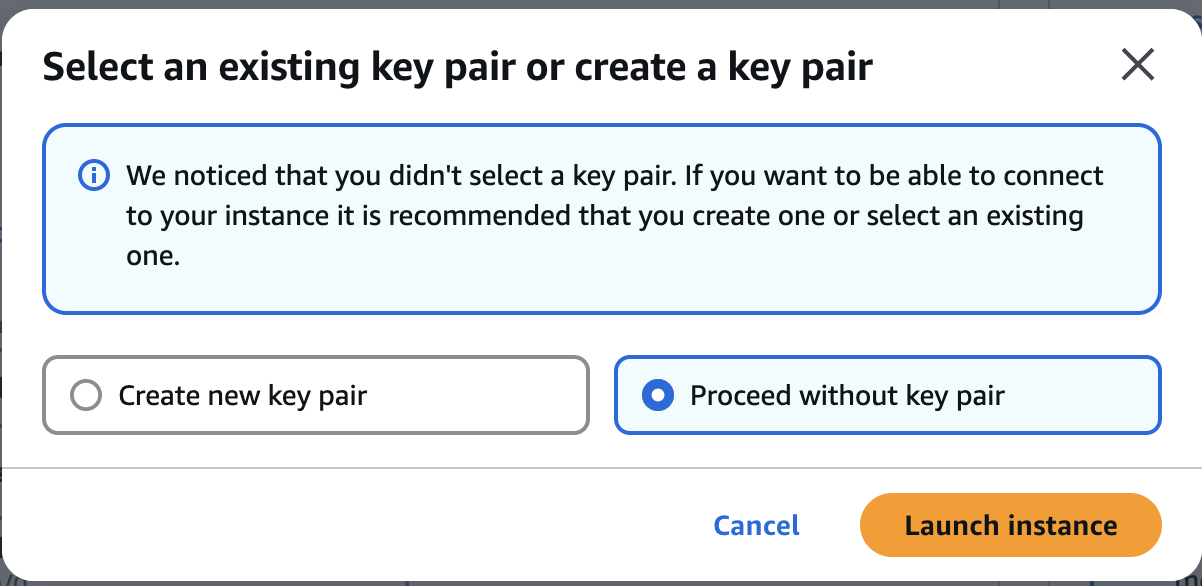
Proceed without key pair

No Problem

Launch M5 Large Instance
M5-Large


Proceed without key pair

Launch Failed because of SCP

Run this command only if it shows as Not Enabled
aws organizations enable-aws-service-access --service-principal tagpolicies.tag.amazonaws.com
AWS Resource Groups

AWS Resource Groups View

Environment tag key must match tag values
wrongtagpurposeexperimentEnvironmentnotinlist
Environment must match Tag Values
dev
Other tag Keys are fine
myownkeymyownvalueEnforce Tag Policy at Creation
Preventive Control - SCP
{
"Sid": "RequireMandatoryTags",
"Effect": "Deny",
"Action": [
"ec2:RunInstances"
],
"Resource": "arn:aws:ec2:*:*:instance/*",
"Condition": {
"Null": {
"aws:RequestTag/Environment": "true",
"aws:RequestTag/Project": "true"
}
}
},
{
"Sid": "EnforceTagValues",
"Effect": "Deny",
"Action": [
"ec2:RunInstances"
],
"Resource": "arn:aws:ec2:*:*:instance/*",
"Condition": {
"ForAnyValue:StringNotLike": {
"aws:RequestTag/Environment": [
"dev"
],
"aws:RequestTag/Project": [
"alpha",
"beta",
"demo"
]
}
}
}Add this to Dev SCP

Launch EC2 with no Tags

Launch EC2 with all required tags
EnvironmentdevprojectalphaTest-Tags


🙏
Thanks
for
Watching
AWS Organizations - Hands-On Demo
By Deepak Dubey
AWS Organizations - Hands-On Demo
AWS Organizations - Hands-On Demo
- 610



