AWS Config
Hands-On
Demo

In this Demo, we will:
- Verify AWS Config rules are set up (encrypted-volumes, s3-bucket-versioning-enabled, restricted-ssh)
- Create unencrypted EBS volume and attach to EC2 instance
- Create S3 bucket without versioning
- Create security group with open SSH
- Trigger rule evaluations
- Review non-compliant resources in AWS Config dashboard
- Clean up all resources
Agenda


Settings



Data governance


Delivery method

s3-bucket-versioning-enabled
restricted-ssh
encrypted-volumes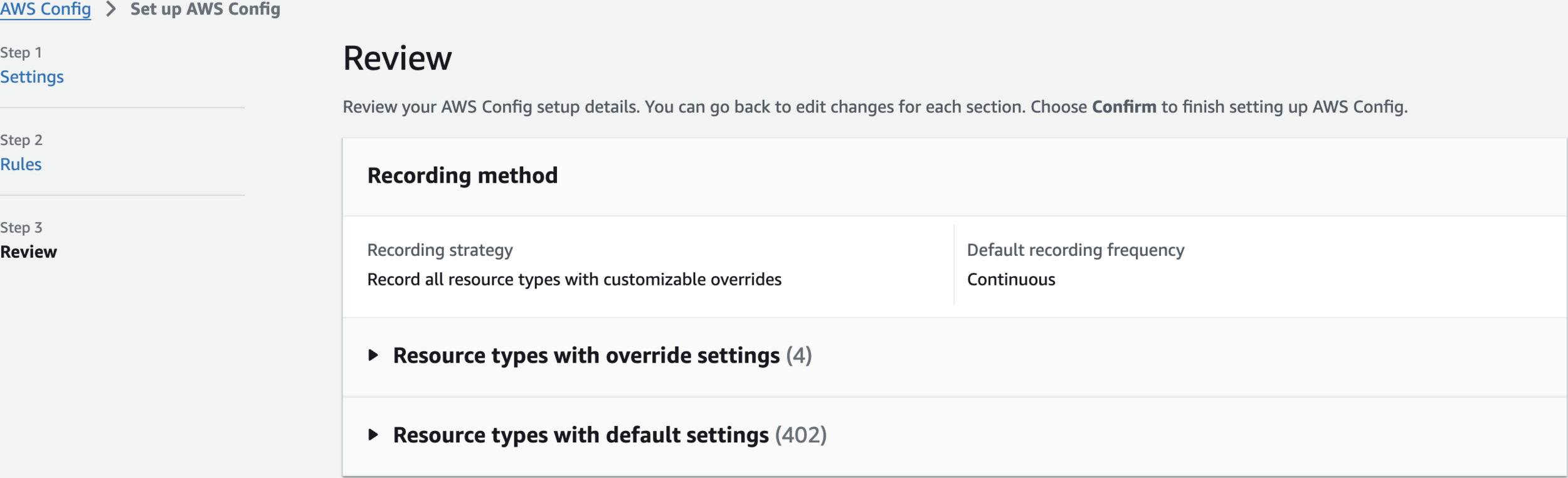
Review

Review and Confirm





Create Non Compliance Objects/Scenarios

Launch AWS CloudShell
# For EBS Volume Demo
# Create volume
echo "Creating EBS volume..."
VOLUME_ID=$(aws ec2 create-volume \
--volume-type gp3 \
--size 1 \
--availability-zone us-east-1a \
--query 'VolumeId' \
--output text)
echo "Created Volume ID: $VOLUME_ID"Scenario 1 : Unencrypted EBS Volume
# Get AMI ID
echo "Getting latest Amazon Linux 2 AMI..."
AMI_ID=$(aws ec2 describe-images \
--owners amazon \
--filters "Name=name,Values=amzn2-ami-hvm-*-x86_64-gp2" \
"Name=state,Values=available" \
--query 'sort_by(Images, &CreationDate)[-1].ImageId' \
--output text)
echo "Using AMI ID: $AMI_ID"# Get Subnet ID
echo "Getting subnet in us-east-1a..."
SUBNET_ID=$(aws ec2 describe-subnets \
--filters "Name=availabilityZone,Values=us-east-1a" \
--query 'Subnets[0].SubnetId' \
--output text)
echo "Using Subnet ID: $SUBNET_ID"Scenario 1 : Unencrypted EBS Volume
# Launch EC2 instance
echo "Launching EC2 instance..."
INSTANCE_ID=$(aws ec2 run-instances \
--image-id $AMI_ID \
--instance-type t2.micro \
--subnet-id $SUBNET_ID \
--count 1 \
--query 'Instances[0].InstanceId' \
--output text)
echo "Created Instance ID: $INSTANCE_ID"# Wait for instance
echo "Waiting for instance to be running..."
aws ec2 wait instance-running --instance-ids $INSTANCE_IDScenario 1 : Unencrypted EBS Volume
# Attach volume
echo "Attaching volume to instance..."
aws ec2 attach-volume \
--volume-id $VOLUME_ID \
--instance-id $INSTANCE_ID \
--device /dev/sdfecho "Triggering encrypted-volumes rule evaluation..."
aws configservice start-config-rules-evaluation \
--config-rule-names encrypted-volumesScenario 1 : Unencrypted EBS Volume
# For S3 Bucket Demo
echo -e "\nStarting S3 bucket versioning demo..."
BUCKET_NAME="test-config-bucket-$(date +%s)"
echo "Creating bucket: $BUCKET_NAME"
aws s3api create-bucket \
--bucket $BUCKET_NAME \
--region us-east-1echo "Triggering s3-bucket-versioning-enabled rule evaluation..."
aws configservice start-config-rules-evaluation \
--config-rule-names s3-bucket-versioning-enabledScenario 2 : Unversioned S3 Bucket
# For Security Group Demo (Automated version)
echo -e "\nStarting security group demo..."
echo "Creating security group..."
SG_ID=$(aws ec2 create-security-group \
--group-name test-ssh-open \
--description "Test security group for SSH rule" \
--query 'GroupId' \
--output text)echo "Adding SSH rule to security group..."
aws ec2 authorize-security-group-ingress \
--group-id $SG_ID \
--protocol tcp \
--port 22 \
--cidr 0.0.0.0/0echo "Triggering restricted-ssh rule evaluation..."
aws configservice start-config-rules-evaluation \
--config-rule-names restricted-sshScenario 3 : Open Security Group

Wait and Check in AWS Config
Clean Up

Terminate (delete) instance

Delete S3 Bucket

Delete volume

Delete security group

Wait and Check for Compliance after fixing

Some Rules can take time - upto 1 day
🙏
Thanks
for
Watching
AWS Config - Hands-On Demo
By Deepak Dubey
AWS Config - Hands-On Demo
AWS Config - Hands-On Demo
- 613



