Curiosity is not a crime
Duarte Monteiro - AET
-=[101 to infosec world]=-
~$Chantam_house_rule
TLP:Amber
My personal two rules: > Everything is Broken > POC||GTFO
"><svg/onload=The Infosec World
Defensive
Offensive
"><svg/onload=The Infosec World
"><svg/onload=The Infosec World
"><svg/onload=The Infosec World
"><svg/onload=The Infosec World
"><svg/onload=The Infosec World
This talk...
Understanding the players

We seek after knowledge... and you call us criminals. We exist without skin color, without nationality, without religious bias... and you call us criminals.
You build atomic bombs, you wage wars, you murder, cheat, and lie to us and try to make us believe it's for our own good, yet we're the criminals.
Yes, I am a criminal. My crime is that of curiosity. My crime is that of judging people by what they say and think, not what they look like. My crime is that of outsmarting you, something that you will never forgive me
for.
I am a hacker, and this is my manifesto. You may stop this individual,
but you can't stop us all... after all, we're all alike.
+++The Mentor+++
http://phrack.org/issues/7/3.html
~$ ./HACKER_101
- Curious by default,
- Self-taught,
- feed on cafeine and moral ambiguity (?)
- Love for the virtual world.

Kevin Mitnick Wanted Poster
Blackhat
Greyhat
Whitehat
Mindset:

GID=0x31337
Threat Actors
Script Kiddies
Hackivist


Gary McKinnon - Hacked NASA and the US military
Threat Groups
Organised Crime
Nation States


GID=0x31337

GID=0xcafecafe
Grey/White hat world
Conferences


Certifications


Job Offers :)

...
...
...
() { :; }; /Pentesting

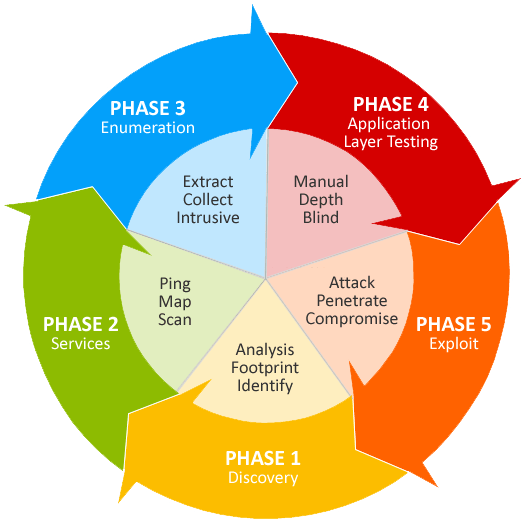
DISCLOSURE' OR 1=1/*


https://googleprojectzero.blogspot.pt/
https://hackerone.com/pornhub

Lei n.º 109/2009, de 15 de Setembro
Artigo 4.º (Dano relativo a programas ou outros dados informáticos)
Artigo 5.º (Sabotagem informática)
Artigo 6.º (Acesso ilegítimo)
Artigo 7.º (Intercepção ilegítima)
Artigo 8.º (Reprodução ilegítima de programa protegido)
Artigo 9.º (Responsabilidade penal das pessoas colectivas e entidades equiparadas)
DISCLOSURE' OR 1=1/*
MEDIA


Accurate
4phun
Just bad.




MEDIA
We are all sitting ducks.
Known/Unknown Old vulnerabilities in applications
Unknown in new vulnerabilities in applications
Some of them don't reach the world (...)

Vault 7
https://wikileaks.org/ciav7p1/cms/index.html
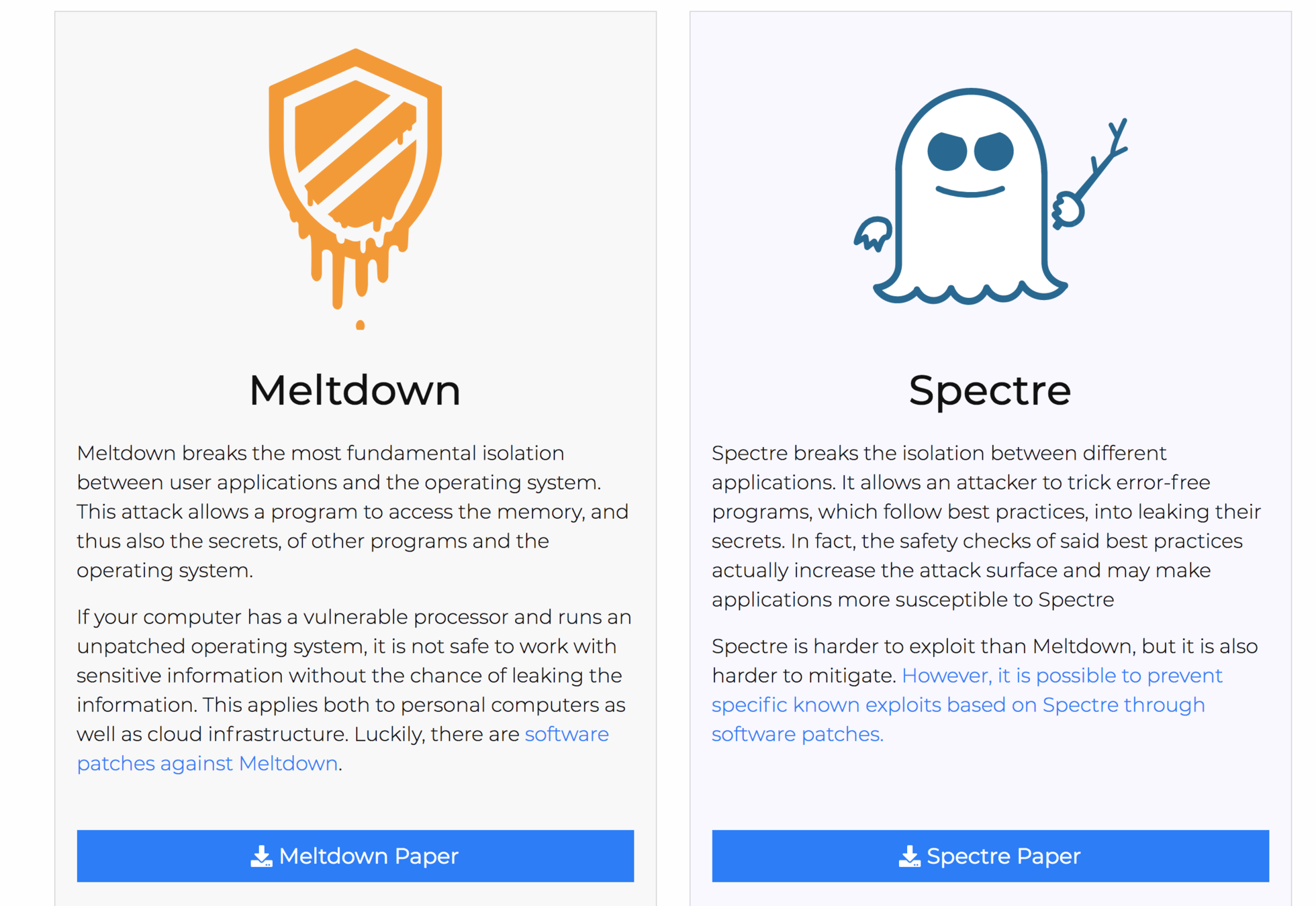
Meltdown / Spectre
Outch: http://www.securityweek.com/intel-halts-spectre-meltdown-cpu-patches-over-unstable-code

Meltdown / Spectre

Exploits Database

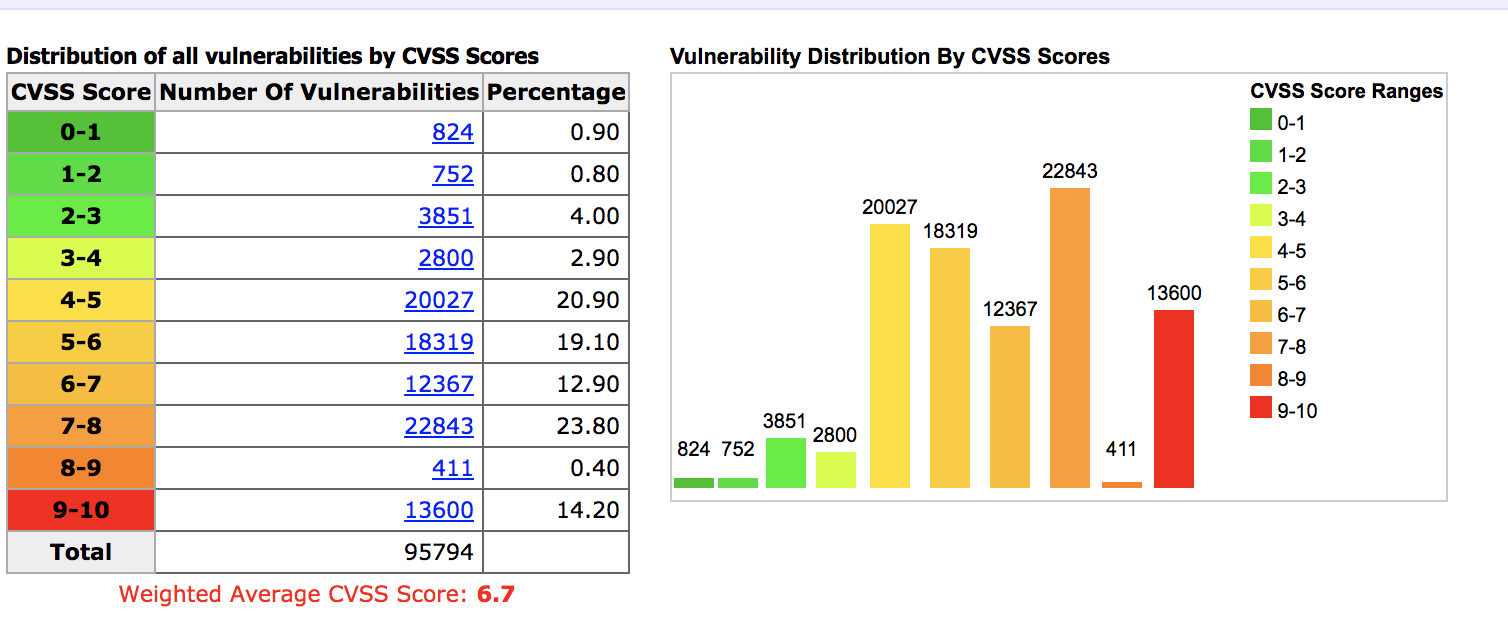
0DAYS
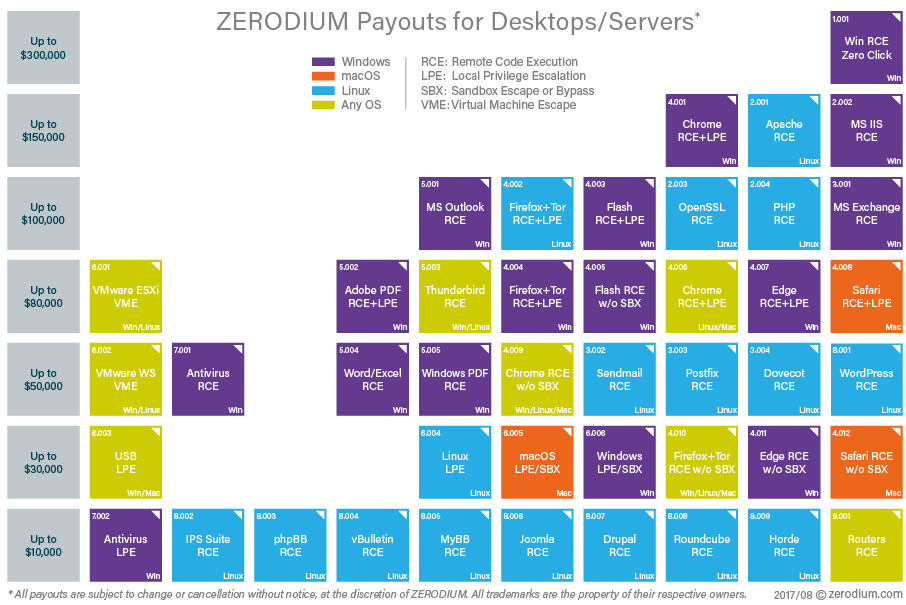
pwn2own
Security Threats
/../../../../../../threats
Social Engineering
Malware
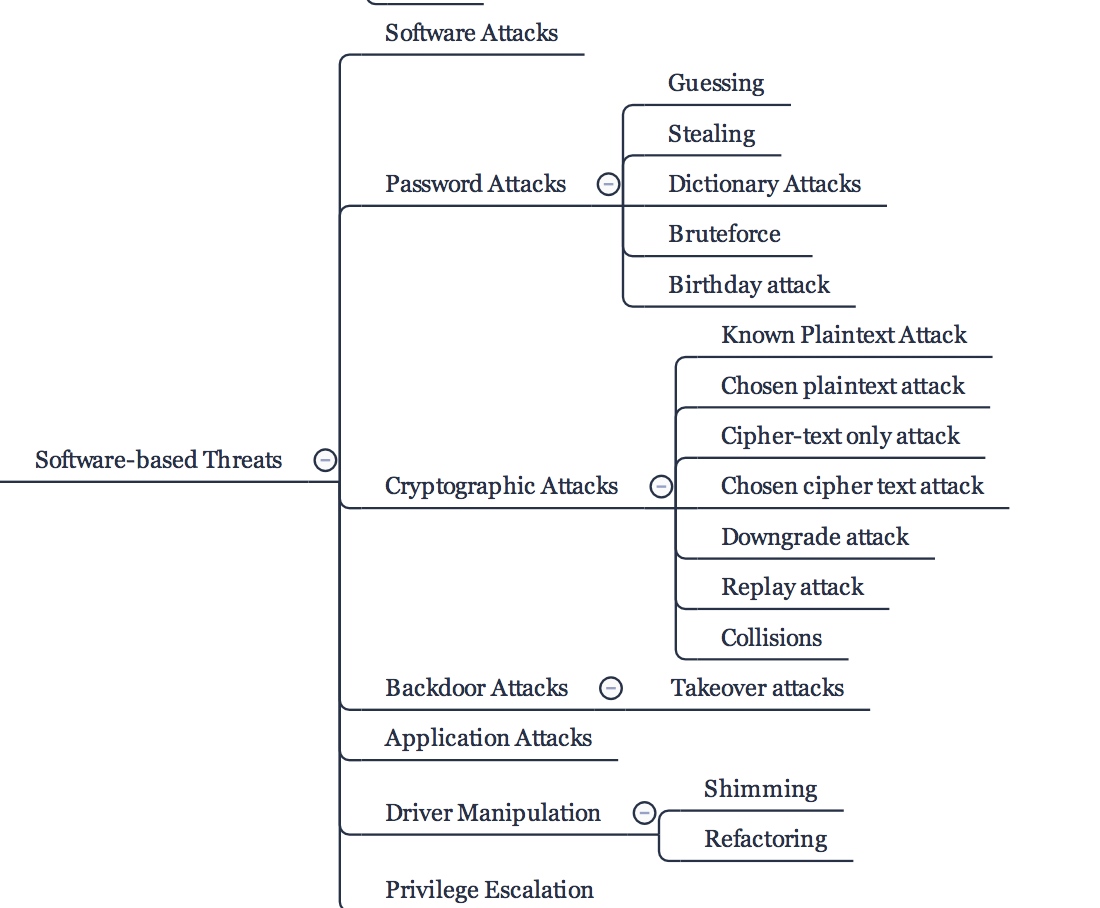
Software-based
Network-based
Wireless
Physical
Humans are always the weakest link.

Spear phshing
- Victims profile (What he wants? Needs?)
- Targeted information (Spoofing real pages)
- Attack vector (E-email, SMS, Social Networks)
- Patience is a virtue ....
- Collect and proceed.
/../../../../../../threats
Social Engineering
Malware
Software-based
Network-based
Wireless
Physical
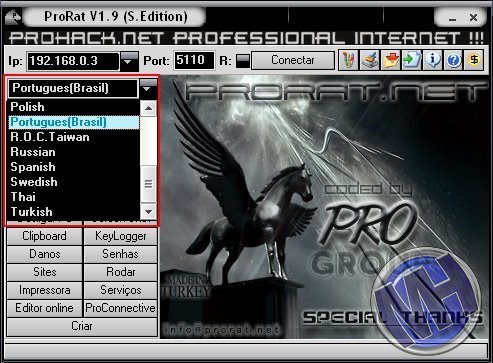
Goldies
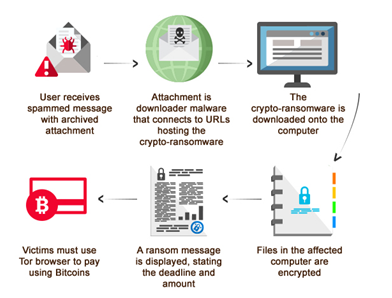
Ransomware
AV Evasion Artware by Кириакос Экономоу
/../../../../../../threats
Social Engineering
Malware
Software-based
Network-based
Wireless
Physical
Goldies
/../../../../../../threats
Social Engineering
Malware
Software-based
Network-based
Wireless
Physical
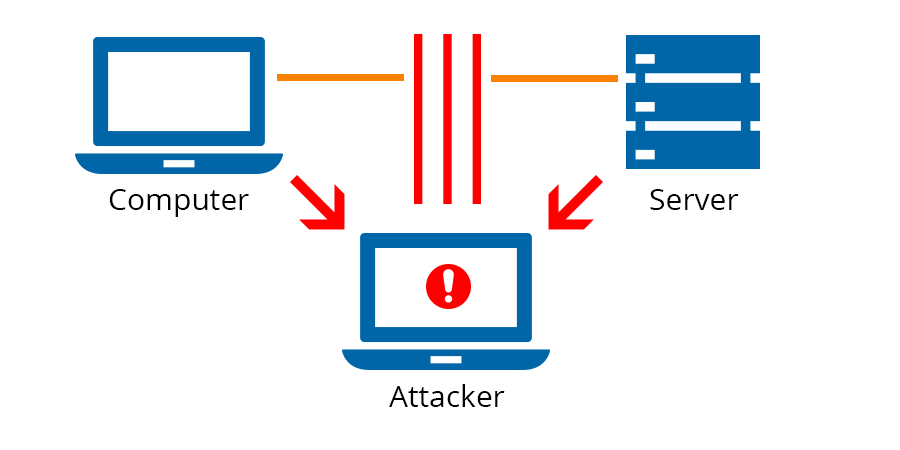
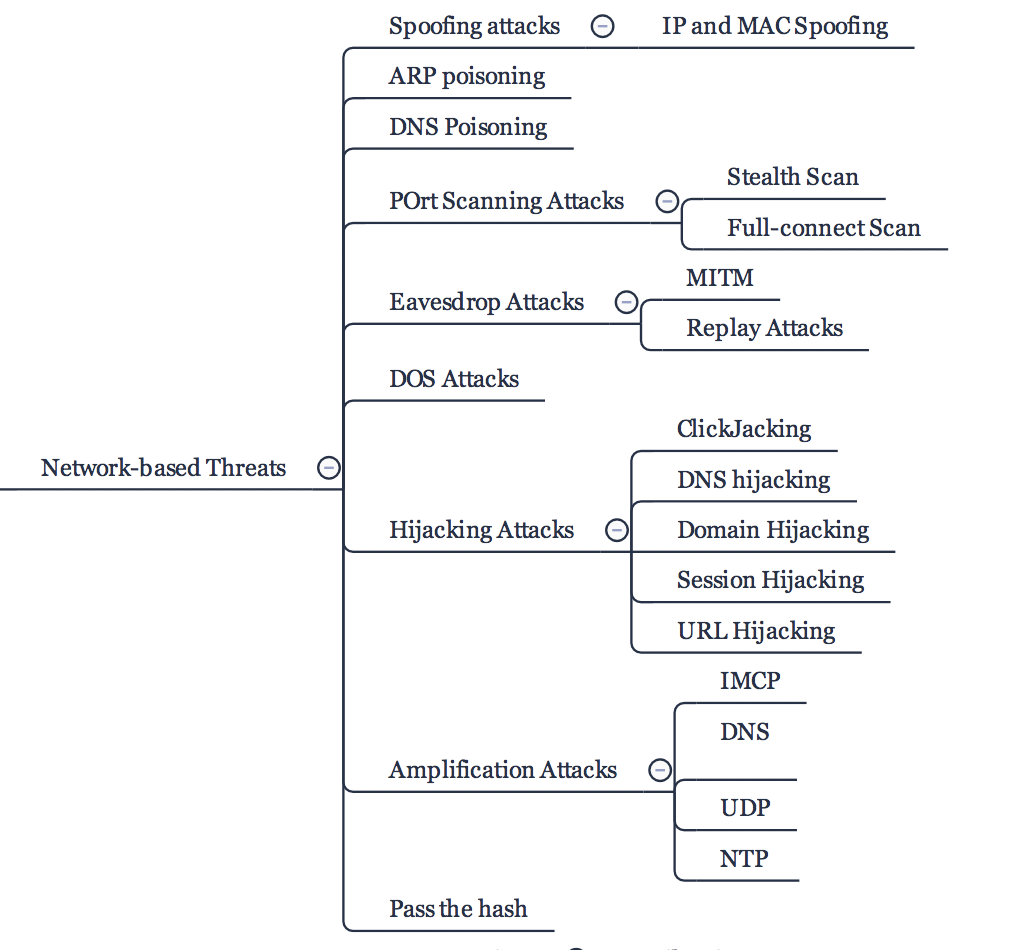
/../../../../../../threats
Social Engineering
Malware
Software-based
Network-based
Wireless
Physical

/../../../../../../threats
Social Engineering
Malware
Software-based
Network-based
Wireless
Physical
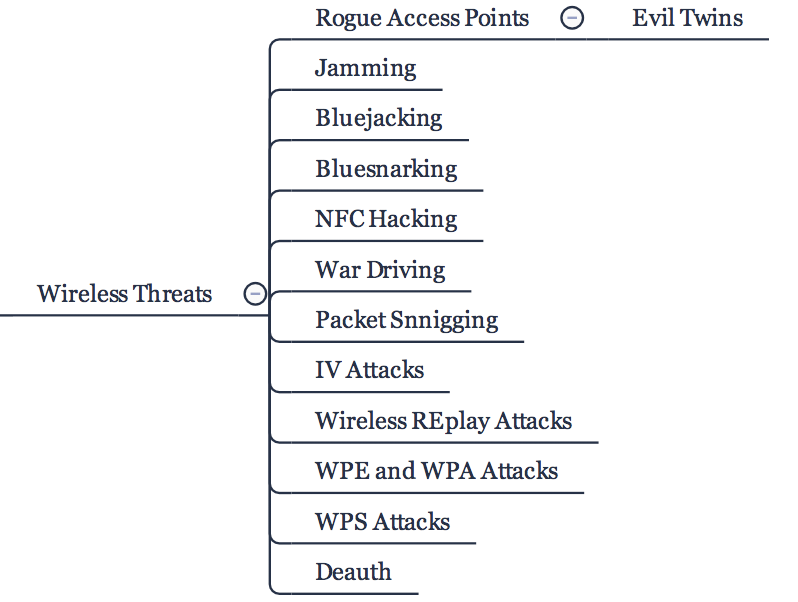
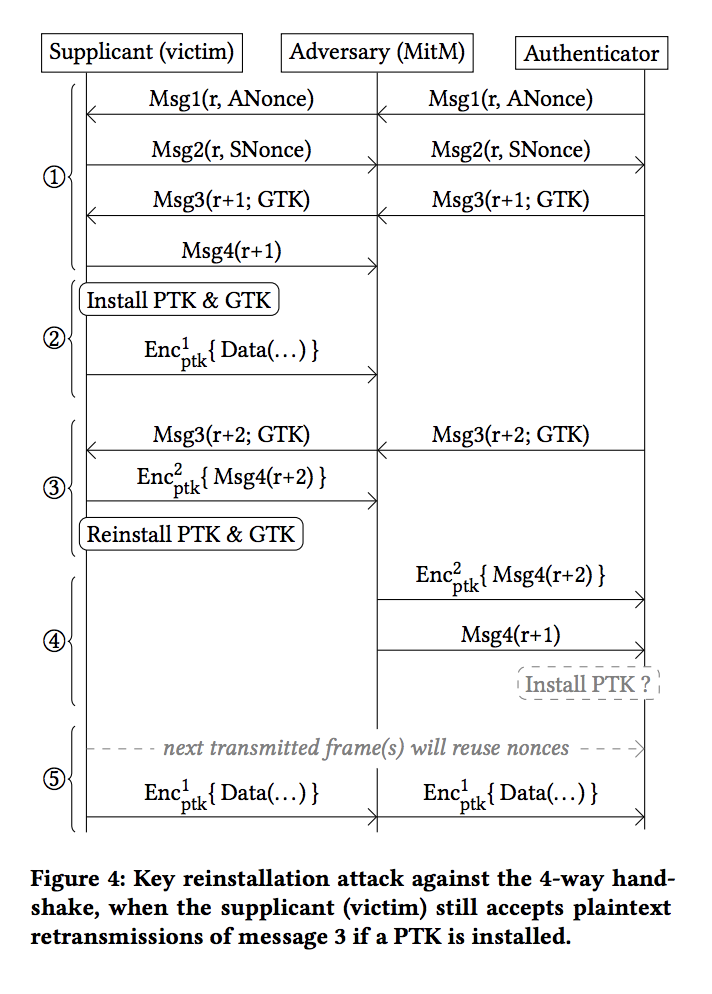
KRAKS - https://papers.mathyvanhoef.com/ccs2017.pdf
/../../../../../../threats
Social Engineering
Malware
Software-based
Network-based
Wireless
Physical



Recommended:
https://www.youtube.com/watch?v=4skSBwBBI-s
/../../../../../../threats
Social Engineering
Malware
Software-based
Network-based
Wireless
Physical

Tricks & Tips <<defensive>>
Tricks &' | echo 'tips'
1. Dont' click sh1t. Rule of thumb: if you are not expecting it, it is suspicious.
Risky file types:
- Any executable files: EXE, COM, CMD, BAT, PS1, SWF, JAR etc.
- MS Office documents, especially with macros: DOC/DOCX/DOCM, XLS/XSLX/XLSM etc.
- PDF documents: PDF.
- Vector graphics with embedded code: SVG.
- Archives of these files, especially password-protected.
Not sure? https://virustotal.com
=> Also, don't plug and play, unexpected USB or CD/DVD.




Tricks &' | echo 'tips'
Tricks &' | echo 'tips'
2. Set-up the basis.
Default FW ?

Freeware ?

Common Sense

File Write

Network Access
Also... FDE

3. Harden your browser.
Tricks &' | echo 'tips'

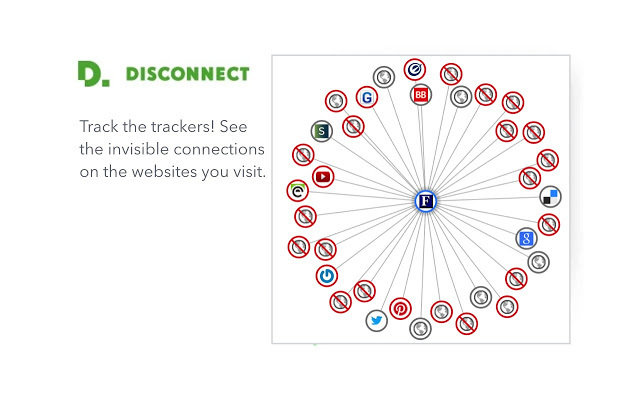

4. Authentication procedures hardened
Tricks &' | echo 'tips'
Always 2FA

Strong Passwords
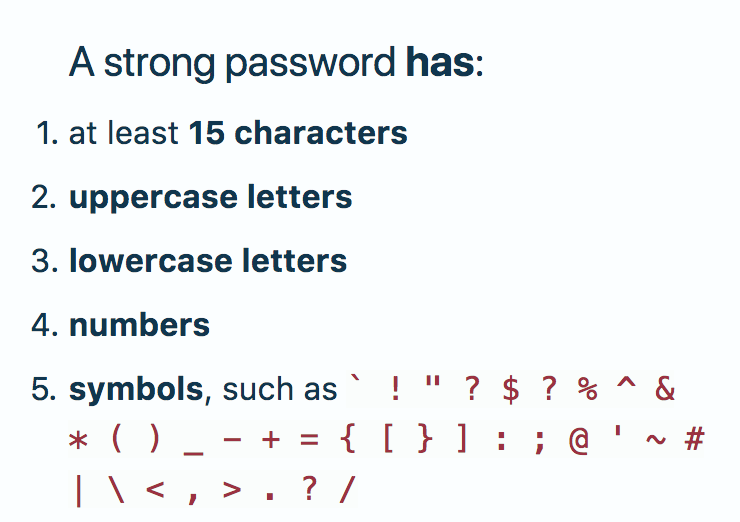
Memory Problem?

4. Authentication procedures hardened
Tricks &' | echo 'tips'
5. 'use tor use signal'
Tricks &' | echo 'tips'

VPN
Sharing private info ?
1. Always HTTPS
2. Use CryptoBin
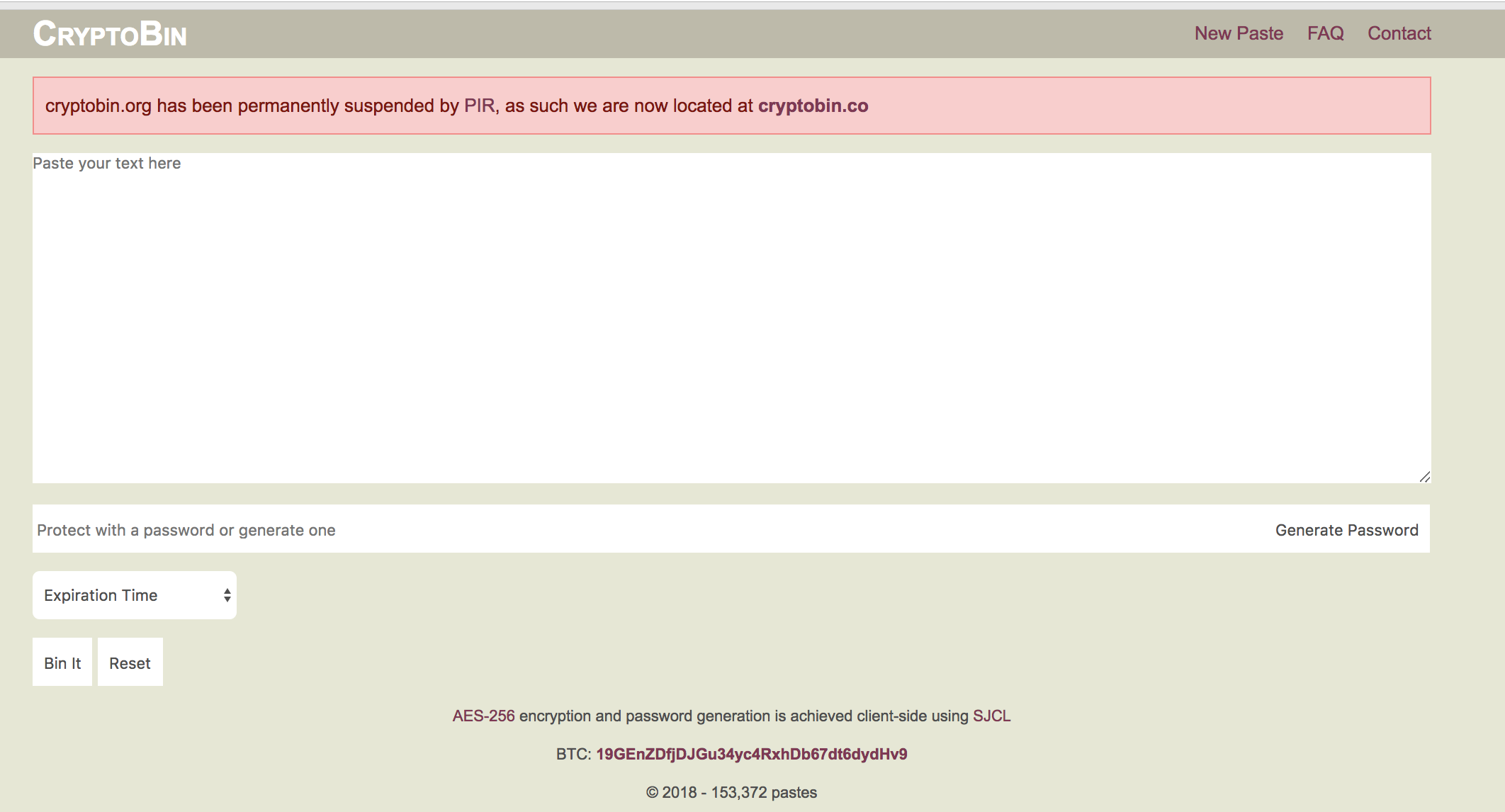
6. on the go
Tricks &' | echo 'tips'
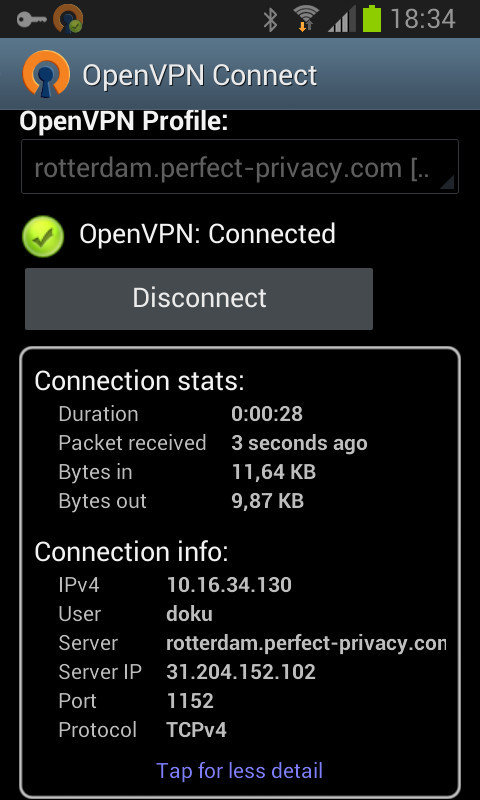
1. FDE
2. PIN (fingerprints are not hashable)
3. Guest mode
4. Minimize the attack surface
5. Minimize data exposure (GPS Sharing apps, Social Networks,....)

7. Update sh1t.
Tricks &' | echo 'tips'
My personal two rules:
> Everything is Broken
> POC||GTFO
Hope you enjoyed,
stay safe & stay legal.
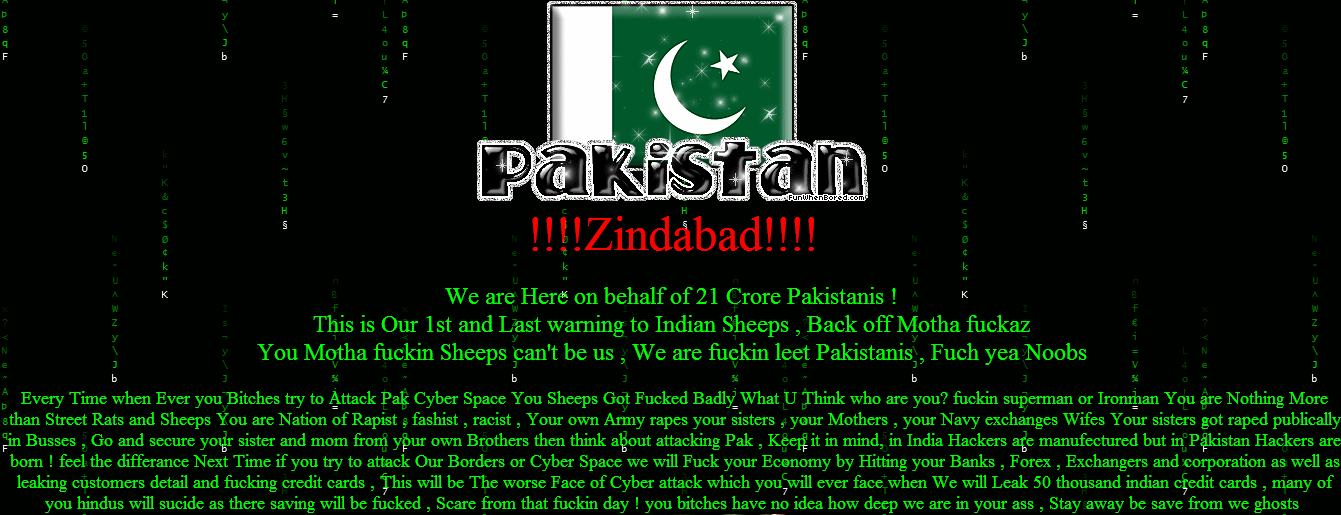
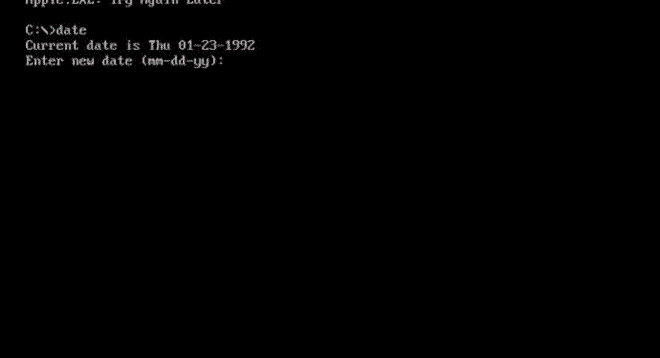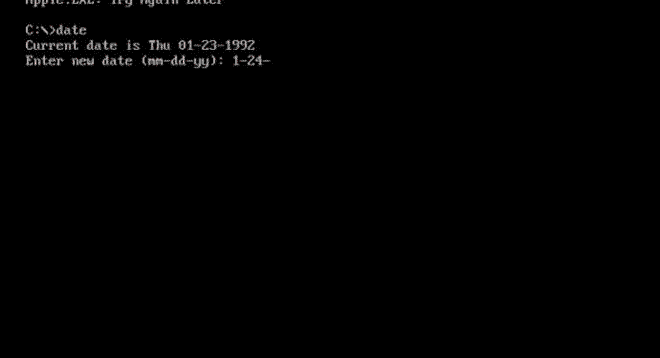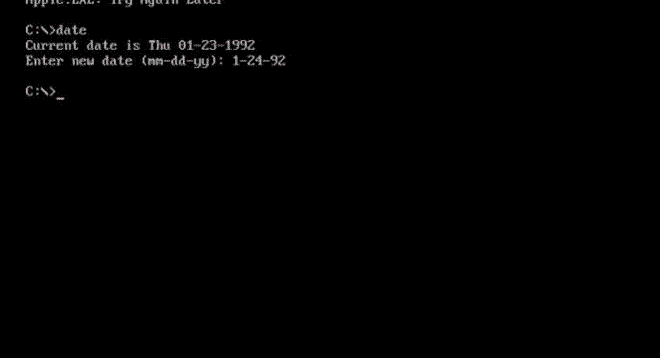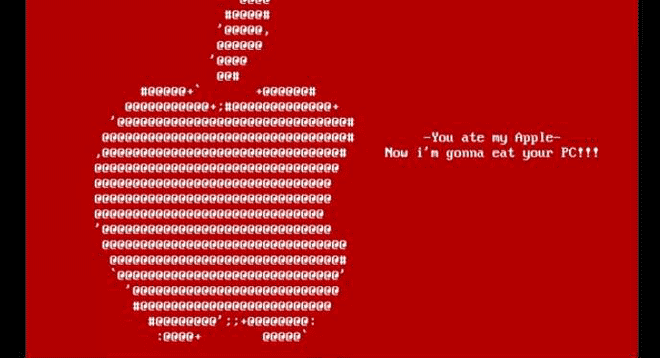
Don't let this happen to you or your site!
google > hacked site:.pt
Bonus!
Curiosity is not a crime
By Duarte Monteiro
Curiosity is not a crime
- 1,100


