OWASP SAMM
Thoughts & Experiences
d0kt0r @ 0xOPOSEC

~$ WHOAMI

0XOPOSEC - d0kt0r
Freelance Information Security Consultant
PhD Student @ FCUP
“We do what we must because we can.” – Aperture Science
Email: dm@dm-advisory.eu


Motivation
- Awareness mostly (something you can use as a guide)
- Proven it's value
- Less trendy dimension of Infosec
- Finding order in chaos
Disclaimer: This is not a Technical talk
Disclaimer2: Not reinventing the wheel here
Disclaimer3: not an OWASP pitch
Agenda
- The Problem
- The Model
- Implementation
- Experimentation
- Conclusions
The Problem
Information Security World
Information Security World
AppSec

Information Security World
AppSec

Security Architecture Teams
Security Assessments Teams
Development Teams
IR Teams
?
The Model
Objective
The Model

The Software Assurance Maturity Model (SAMM) is an open framework that provides an effective and measurable way for all types of organizations to analyze and improve their software security posture.
2.0 Version
"Your first step towards improvement, is to measure where you are now."
Features
The Model
Measurable
Defined maturity levels across business practices
Actionable
Clear pathways for improving maturity levels
Versatile
Technology, process, and organization agnostic
Structure
The Model
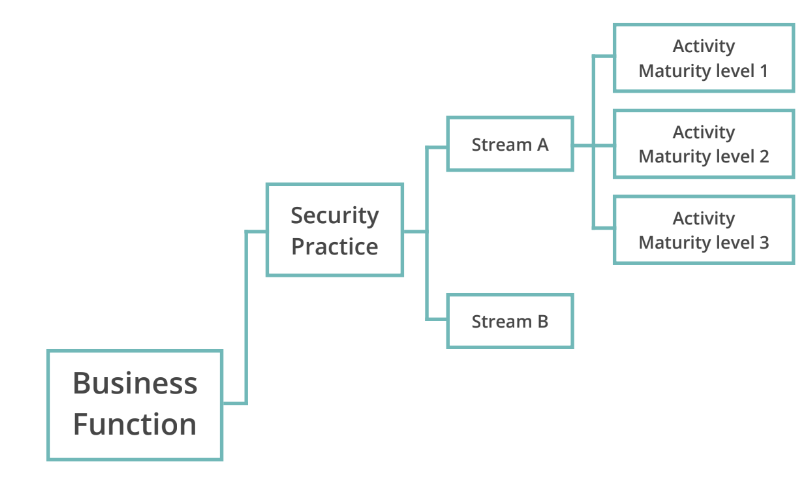
- 5 business functions
- 15 Security Practices
- Higher the maturity higher the cost/effort
- No order or priority on functions and practices (depends on risks or threats)

Business Functions
The Model

Core activities that any organization does to develop software.
Organizational Scope
Application Specific
Security Practices
The Model

Security Practices
The Model

Security Testing Practice
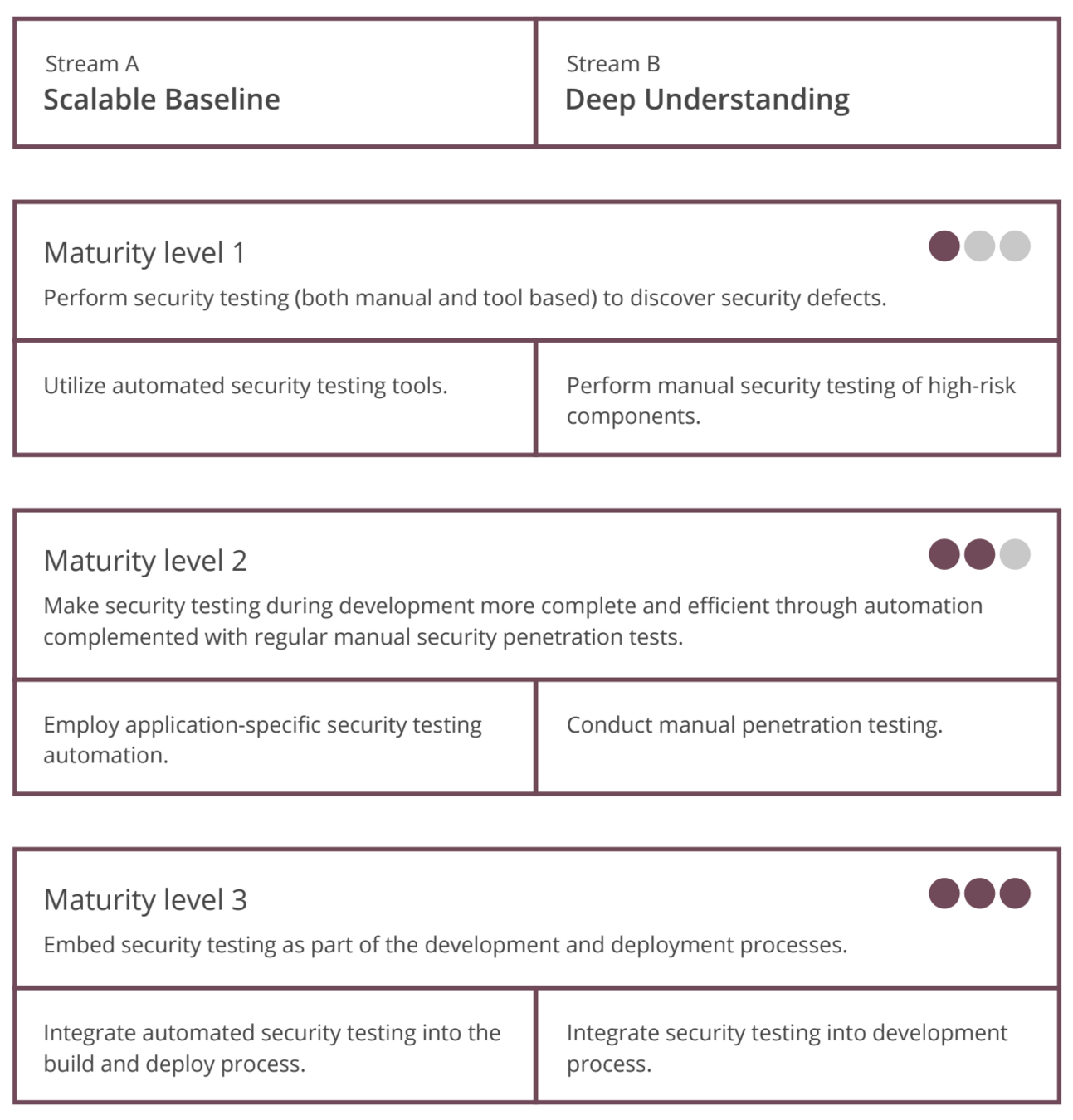

Assessment
The Model
One Question per Activity (total 90 questions)
Quality
Coverage
Assessment
The Model
OWASP SAMM Toolbox available online (SAMMY) or Excel:
Security Testing Maturity Score =
SUM(AVG(StreamALevel1,StreamBLevel1)+AVG(StreamALeve2,StreamBLevel2)+AVG(StreamALevel3,StreamBLevel3))


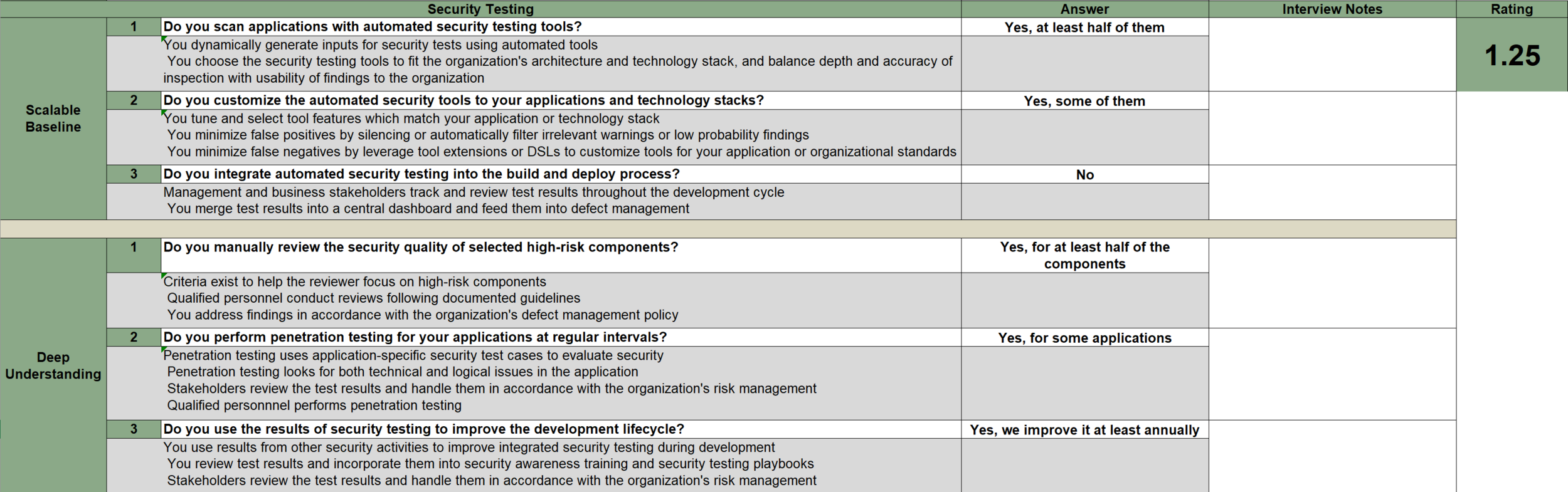
Assessment
The Model
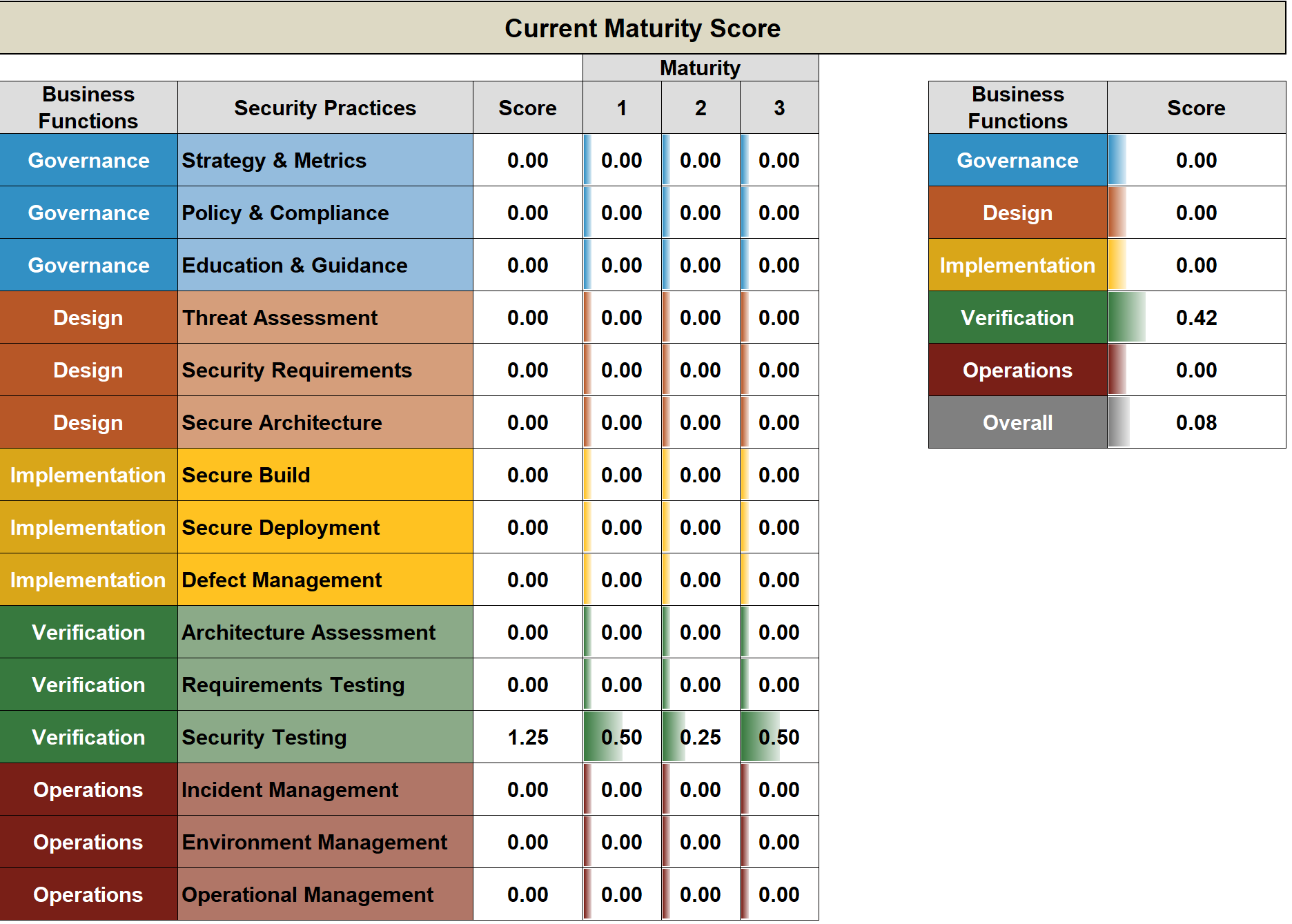
DEMO
Outputs
The Model
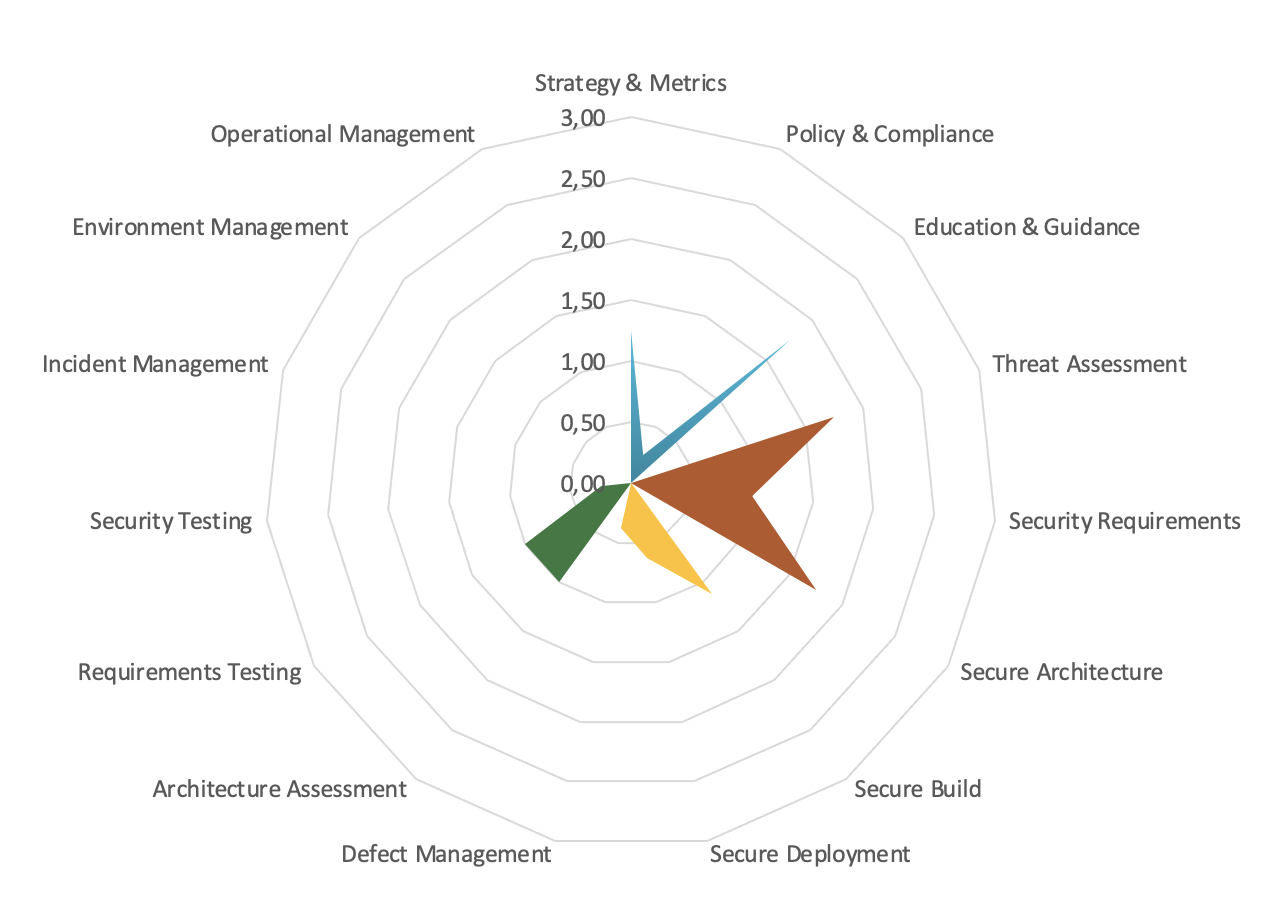
Helpful metrics to "sell" the investment for security programme and/or guide the next iteration of the programme
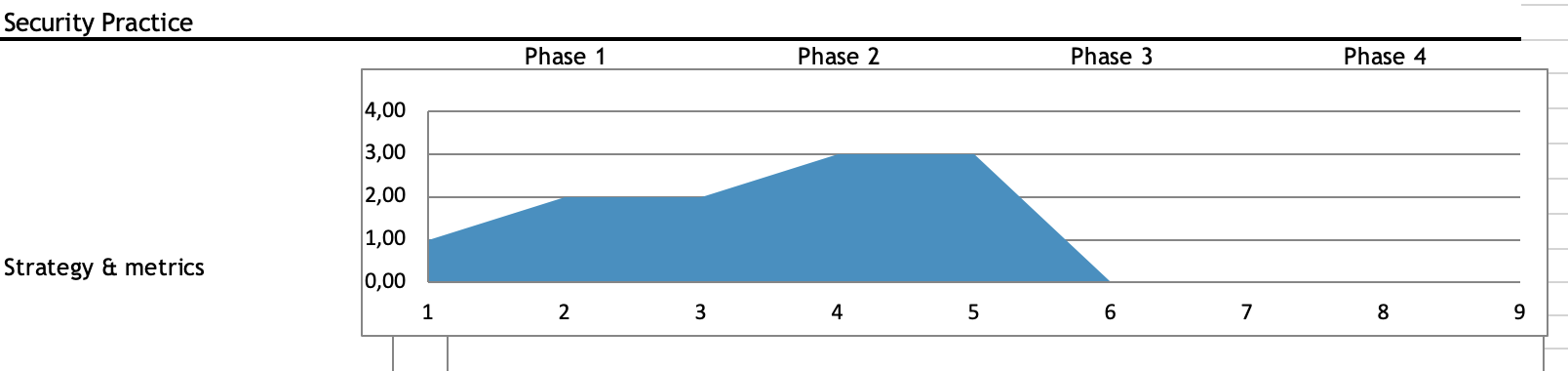
Implementation
6 Step Programe
Implementation
PREPARE
ASSESS
SET THE TARGET
DEFINE THE PLAN
IMPLEMENT
ROLL OUT
6 Step Programe
Implementation
PREPARE
- Ensure proper start of the project:
- Define the scope
- Define the stakeholders
- Spread the word.
*hint*: you may want to start gathering information about your environment and apps: typology, support model, status, location, criticality, data, etc.............
build a stakeholder maps and set comms channels (Steerco, newsletter,..)
6 Step Programe
Implementation
PREPARE
- Start where you are
- Identify and understand the maturity of your chosen scope in each of the 15 software security practices:
- Evaluate current practices
- Determine maturity level
ASSESS
6 Step Programe
Implementation
PREPARE
- Define what score you want to achieve
Software development process maturity will impact your approach
ASSESS
SET THE TARGET
*hint*: be realistic - important to respect dev/op team bandwidth; consider constraints: budget, timing, resources, organizational limitations, etc.
6 Step Programe
Implementation
PREPARE
- Develop a target roadmap that you use to guide the implementation.
ASSESS
SET THE TARGET
DEFINE THE PLAN
*hint*: OWASP has tons of open-source tools to support the implementation of all security practices with 0 cost
6 Step Programe
Implementation
PREPARE
...work
ASSESS
SET THE TARGET
DEFINE THE PLAN
IMPLEMENT
*hint*: really work;
you can measure progress!
6 Step Programe
Implementation
PREPARE
- Ensure that improvements are available and effectively used within the organization
- Reassess and check if objectives were accomplished
ASSESS
SET THE TARGET
DEFINE THE PLAN
IMPLEMENT
ROLL OUT
*hint*: build a service catalogue (AppSecaaService); do not scale if doesn't work; rethink and repeat
Experimentation
There is no magic framework, solution, recipe...
... customisation is always required.
(key advantage of SAMM)

Customizations
Experimentation
Problem #1: User Access is rarely mentioned in the model:
- Secrets Management - Access Production
- Education guidance - access before education
What about internal client user access?
Customizations
Experimentation
To be published soon on: https://github.com/DM-Advisory/
User Access Management
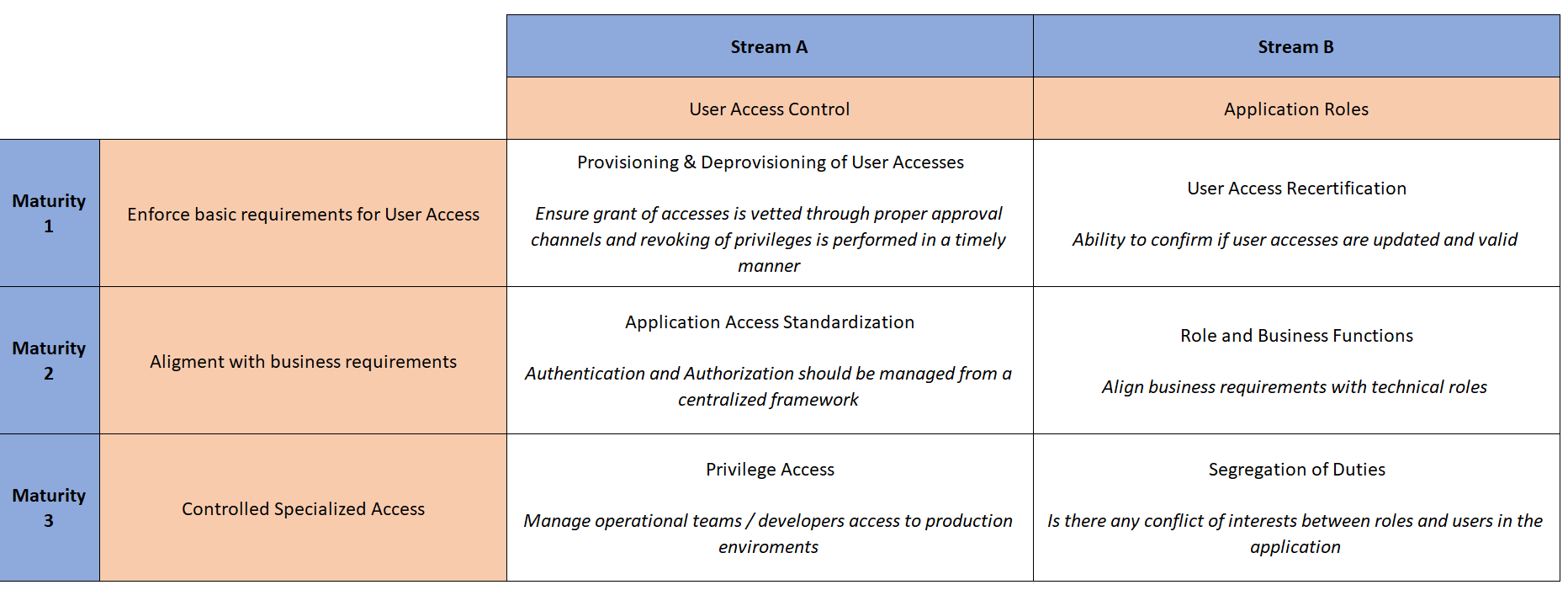
Customization
Experimentation
Problem #2: One of the main problem for Information Security teams is:
Bandwidth
Solution? Automate & Delegate
Model solution: Security Champions
but, in some realities SC does not solve all of our problems (outsourced, third parties,etc.)
Customization
Experimentation
Solution: Project Management Gamification
- Give Project Managers a tool to follow the S-SDLC Process
- Empowering PM over security requirements of their projects
- Make it point-based to leverage competition and compliance

- Are the technical teams aware of Security Policies? Is there a Point of contact for the project?
- Are the asset management rules being followed?
Customization
Experimentation
Solution: Project Management Gamification
- Give Project Managers a tool to follow the S-SDLC Process
- Empowering PM over security requirements of their projects
- Make it point-based to leverage competition and compliance

- Is the documentation being delivered and Security Requirement included?
- Is the vendor (if applicable) compliant with our policies?
Customization
Experimentation
Solution: Project Management Gamification
- Give Project Managers a tool to follow the S-SDLC Process
- Empowering PM over security requirements of their projects
- Make it point-based to leverage competition and compliance

- Internal Software Development practices are being followed?
- Are the security controls being enforced?
Customization
Experimentation
Solution: Project Management Gamification
- Give Project Managers a tool to follow the S-SDLC Process
- Empowering PM over security requirements of their projects
- Make it point-based to leverage competition and compliance

- Is the application eligible for a security test?
Customization
Experimentation
Solution: Project Management Gamification
- Give Project Managers a tool to follow the S-SDLC Process
- Empowering PM over security requirements of their projects
- Make it point-based to leverage competition and compliance


Customization
Experimentation
Solution: Project Management Gamification

Each control and activity from the model performed adds points -> If reaches a baseline the project is ready for go-live!
+20
+20
+20
+20
+20
Conclusions
Take aways
- OWASP SAMM is a open framework to support and guide the implementation of security activities
- Standards and models are a good way to make a valid business case
- Customization and prioritization is possible and required
- Have fun and be creative
Thank you!
Q&A
Credits to OWASP Foundation
Thanks to MG;FF;MT;CB for helping implementing the model
Copy of OWASP SAMM: Thoughts & Experiences
By Duarte Monteiro
Copy of OWASP SAMM: Thoughts & Experiences
- 266



