Web Security - OWASP
Dyan Galih Nugroho Wicaksi
@DyanGalih
2016
dyan.galih@gmail.com
089672015135
https://id.linkedin.com/in/dyangalih
Who am i?
A Simple Person Who Love Code, Share Knowledge and Always Learning about Java, PHP, Linux sysadmin, Android, Javascript.
Specialties: OpenSource, PHP, JavaSE, Android, Javascript, Linux Sysadmin, Webservice, Socket Service.

Quotes Today!
There is nothing secure in cyberworld
This Is What We Are?

Are We?
HackingIssue
-
White Hat Hacker
- Penetration Testing
-
Black Hat Hacker
- Vandalisme
- Sabotage
- Protest Issue
Penetration Testing
-
Black-box Testing
- is a method of software testing that examines the functionality of an application without peering into its internal structures or workings
-
White-box Testing
- a method of testing software that tests internal structures or workings of an application, as opposed to its functionality
What is OWASP?
OWASP (Open Web Application Security Project) is an organization that provides unbiased and practical, cost-effective information about computer and Internet applications.
Web Security
- Communication Security
- Authentication
- Authorization
- Input Validation
- File and Resources
- Error Handling
- Data Protection
Communcation Security
-
Https + TLS
- Comodo / etc
- Let’s Encrypt
- Cloudflare
- Https Check
Let’s Encrypt
Let's Encrypt is a certificate authority that launched on April 12, 2016 that provides free X.509 certificates for Transport Layer Security (TLS) encryption via an automated process designed to eliminate the current complex process of manual creation, validation, signing, installation, and renewal of certificates for secure websites.(wikipedia)
Cloudflare
CloudFlare is designed to accelerate and secure any website. Our system works somewhat like a content delivery network (CDN), but is designed to be much easier to setup and configure.

Authentication
- Authentication Page
- Username & Password
- Login
- Logging Auth
Authentication Page
- Use authentication for protected page
- Use Capthca for public submit
-
Authentication in server side only
Username & Password
- Never display plain text for password
- Never use default user and password
- Change password include old password
-
Password length and Complexity
Login
- Transmit Passwords Only Over TLS or Other Strong Transport
- Authentication and Error Messages
- Prevent Brute-Force Attacks
- Use Correct Response For Failed Login
Logging Auth
- Logging for success login
- Logging for failed login
-
Logging for success logout
Authorization
-
Access Data
- Private page can access only for the user has Auth
- Data Level Access
- Log Access Data
Input Validation
- Validation Method
- Server Side, It Must
- Client Side Optional
- Injection
- Sql Injection
- XSS injection
- OS Command Injection
SQL Injection
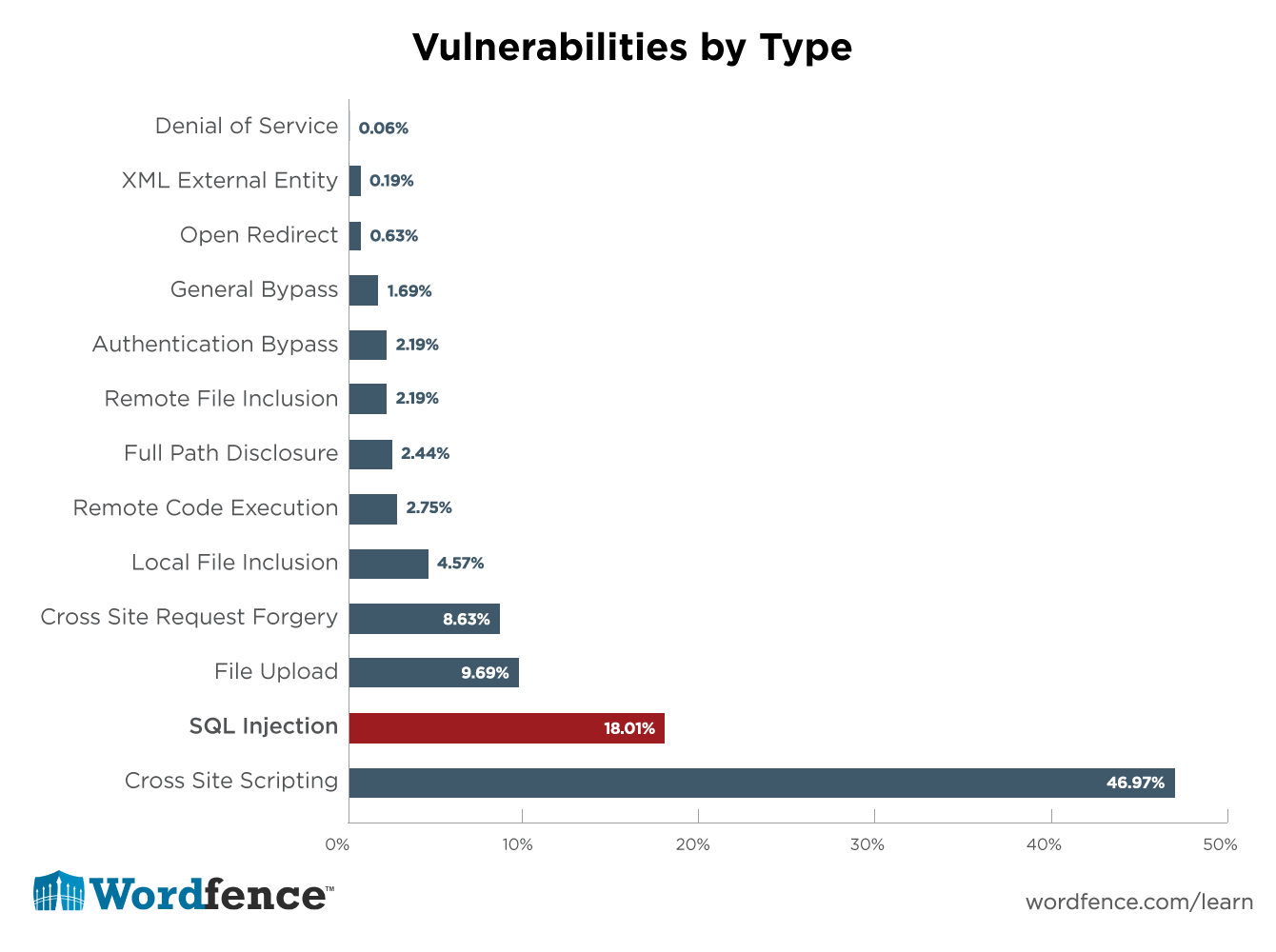

XSS Injection

OS Command Injection
File and Resources
-
File and Resources
- Whitelisted destination
-
Trusted Files
- Filtering Upload Files
- GIGO Method
Error Handling
- Debugging
- Debug display only in development mode
- Never put the debugging file in the public folder
- Put debug log in console.log browser
-
Logging
- Log files must secure, auth needed
- Never put sensitive data into log files
- Log rotation
- Grouping log data
Protection Data
- Debugging
- Never cache sensitive data
- Put sensitive data into body or head http message
- Add protecting data on cache method
Thank you
Web Security
By Dyan Galih
Web Security
- 3,607



