Proposal Defense
PDRM Visit Log System
Muhammad Fadzil Bin Mohd Jusri
19055
Information Communication Technology (ICT)
Presentation Outline
- Introduction
- Literature Review
- Methodology
- Findings
- Prototype
- Conclusion
Introduction
Background Study
PDRM mission is to provide professional services and quality services in protecting the country to ensure public safety, security and prosperity
One of alternatives: Patrol Duty
Provides a log book and book tours at the potential crime areas

Problem Statement
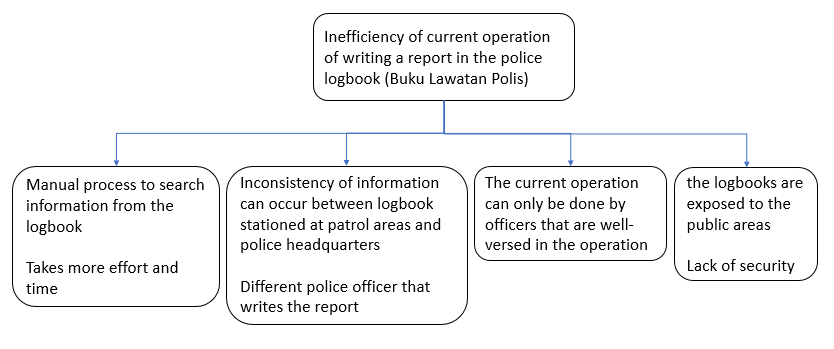
- Takes more effort and time to keep track of the logs
- Inconsistency of information with current process of writing reports
- Can only done by several officers that are well versed of the visit log process
- logbooks are exposed to the public areas which still lack of security
Objectives
- Develop an online system that allows the PDRM to keep track of the logs of their patrolling activities
- Provide a real-time applications platform that are accessible to PDRM at all times regardless their locations
- Program a system that is easily understandable to all PDRM officers
- Create a system that able to encrypt all the information transferred in within the system safely and securely
Scope of Study
Develop and design a Visit Log system for PDRM
User groups:
- Police Officers
- Officers from administration
Literature Review
Patrolling Duties by PDRM
Crime affects all Malaysians, regardless of race, religion, gender, or occupation and asking Malaysians to corporates in fighting crime at all levels so that we all can live in a safer country

PDRM has applied several initiatives to create a peaceful and united communities.
Police omnipresence
Current Method

‘Peti Lawatan Polis Asrama Sekolah’
25 Feb 2017
Click image for details
Potential Usage of Technology
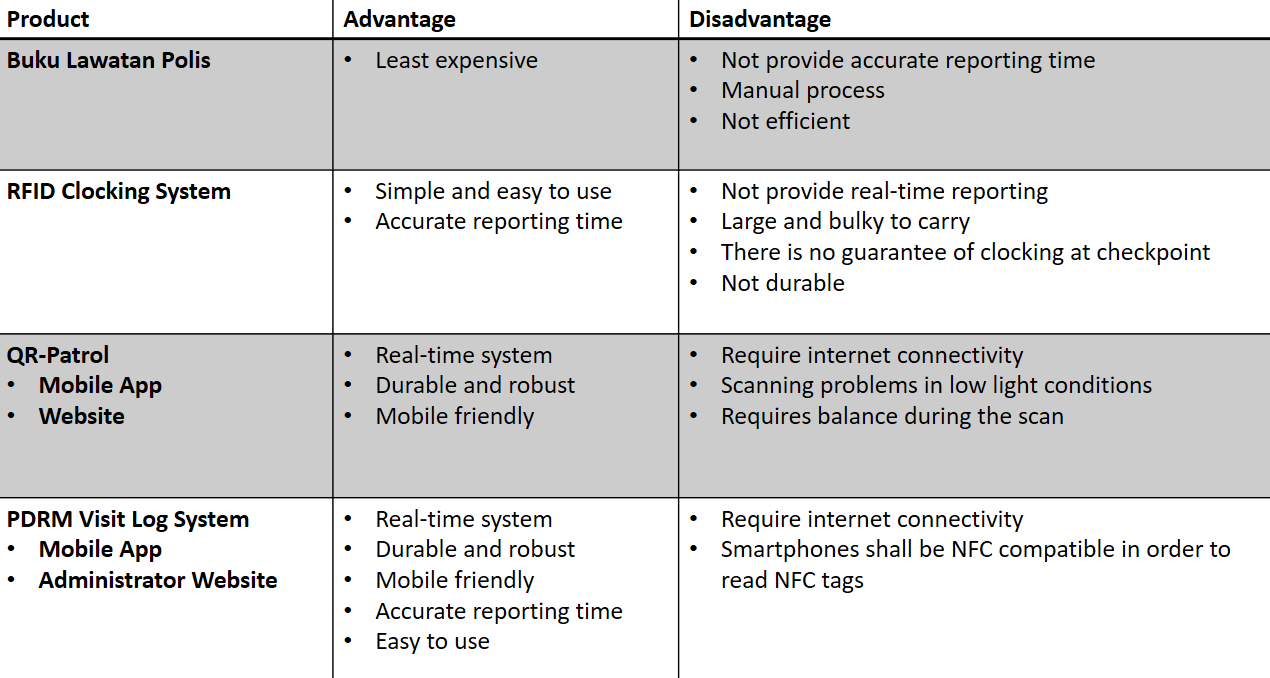
QR-Patrol System (Guard Tour System)
- QR Code / NFC
- Beacon technologies
RFID Clocking System


NFC Technology
Close range wireless proximity communication, normally 10 centimeters

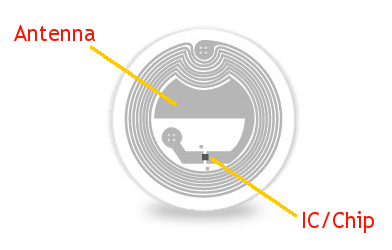
NFC Reader
NFC Tag
Methodology
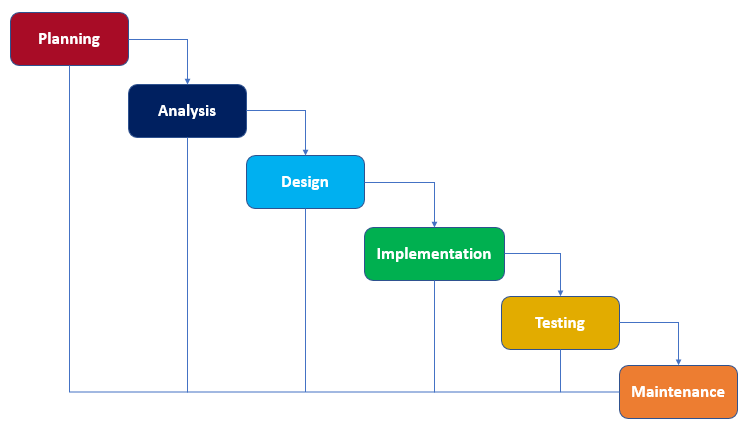
Development Methodology
Structured Design
- formal step by step approach
Waterfall Model
Research Methodology
Qualitative Method
- Interview
- Questionnare
Interview
To gain knowledge and opinions on a specific subject matter regarding patrol activities


Questionnaire
To receive additional feedback from PDRM to support requirement gatherings on the research project.
Types of Q:
Paper-pencil questionnaires
Dichotomous (Yes/No)
Findings
- Understanding the objective of the implementation of Police Logbook
- Understanding of current process involved in writing report in the Police Logbook
- Obtain data written in the logbook
- Know the frequency of the operation
Root Cause Analysis
Requirements
Functional
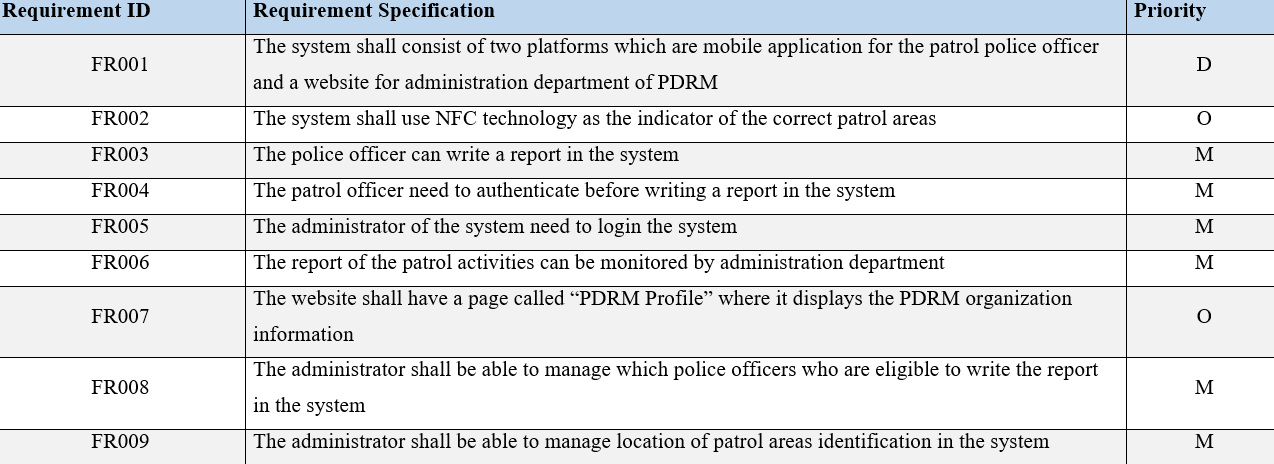
Requirements
Non-Functional

Requirement Analysis
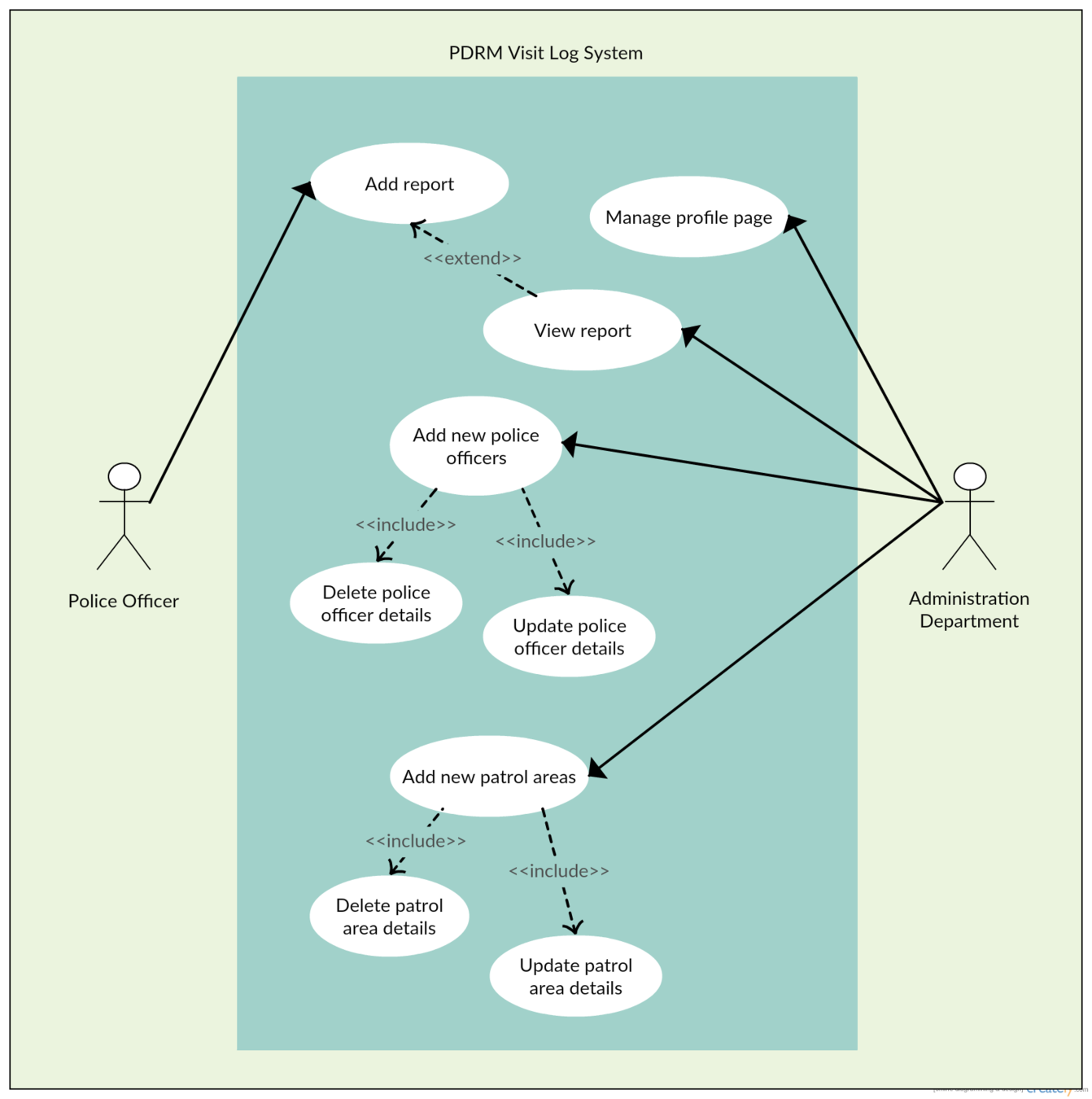
Use Case
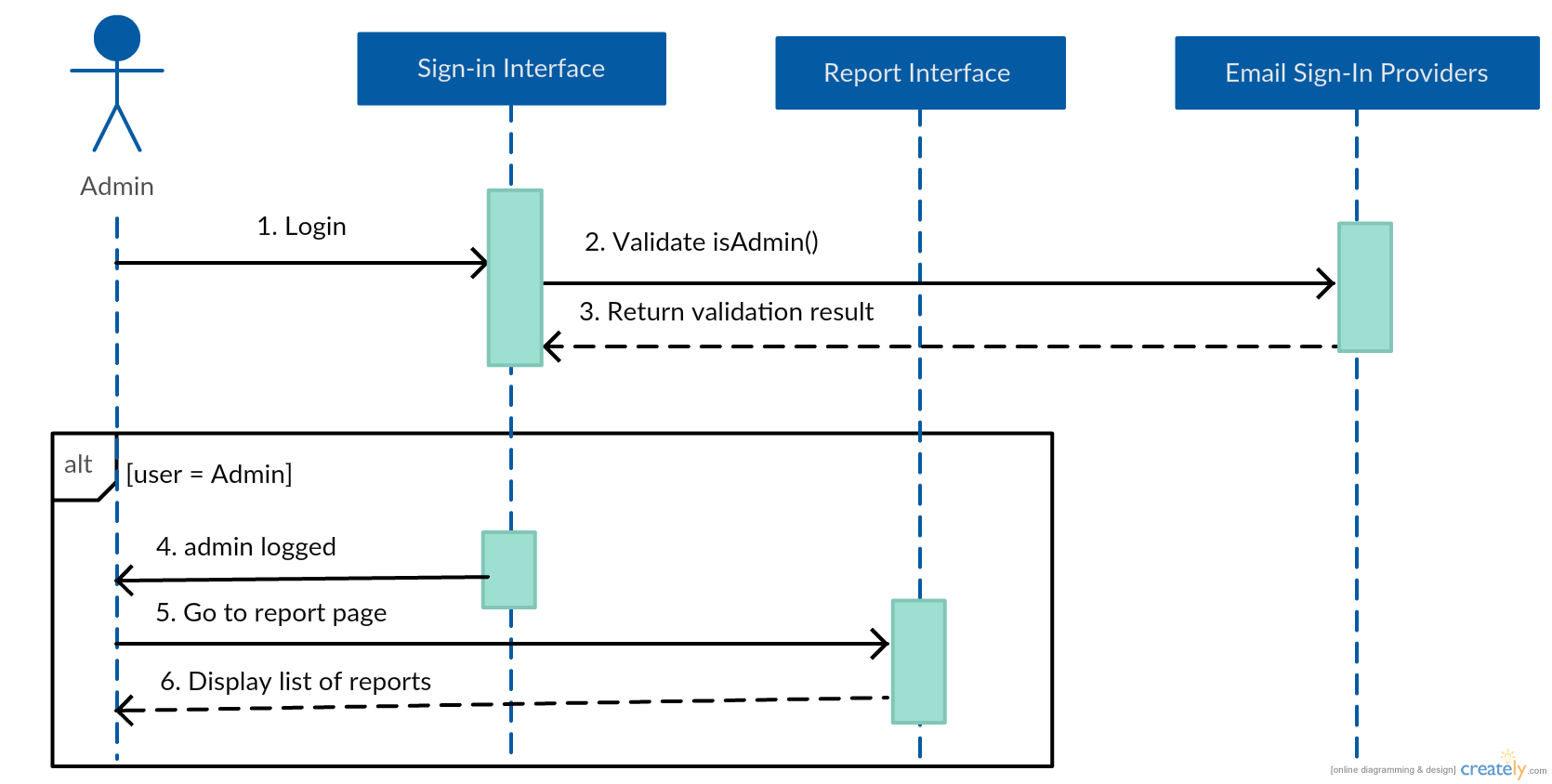
Sequence Diagram
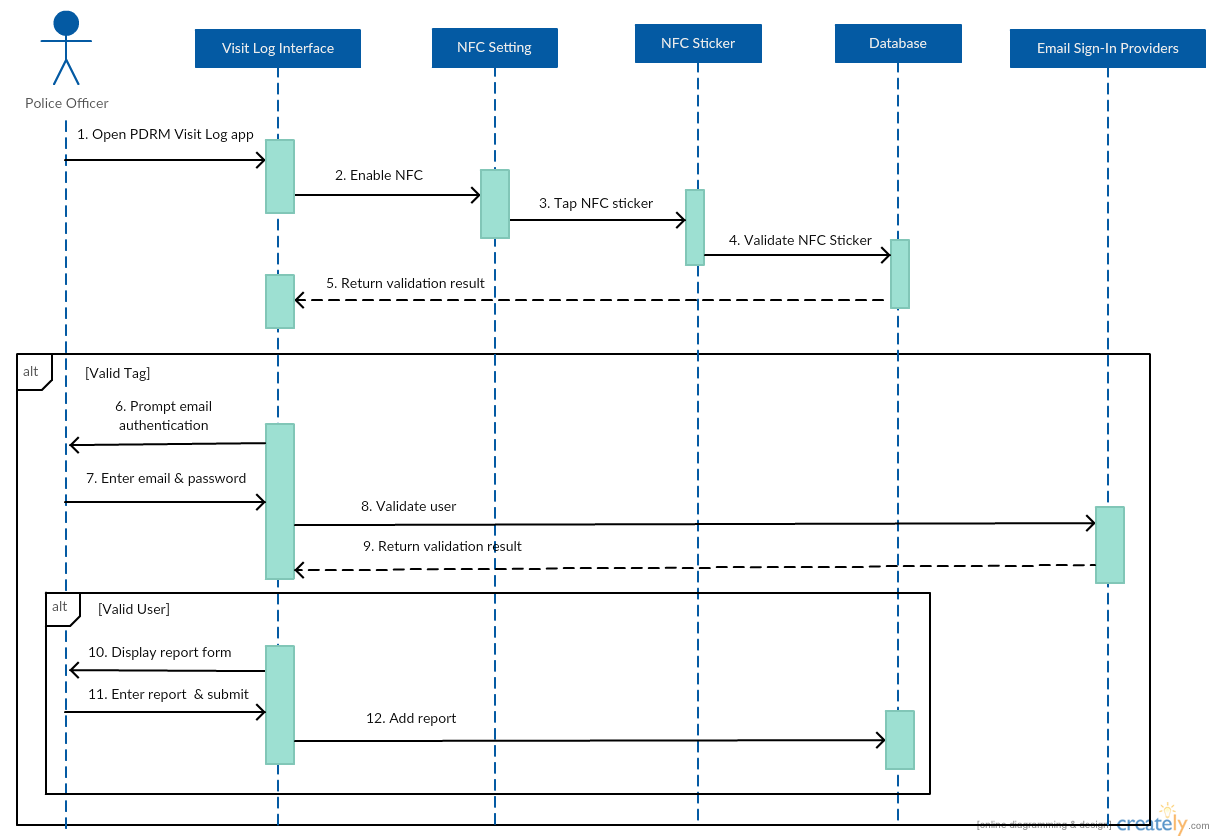
Add report
View report
Manage organization profile
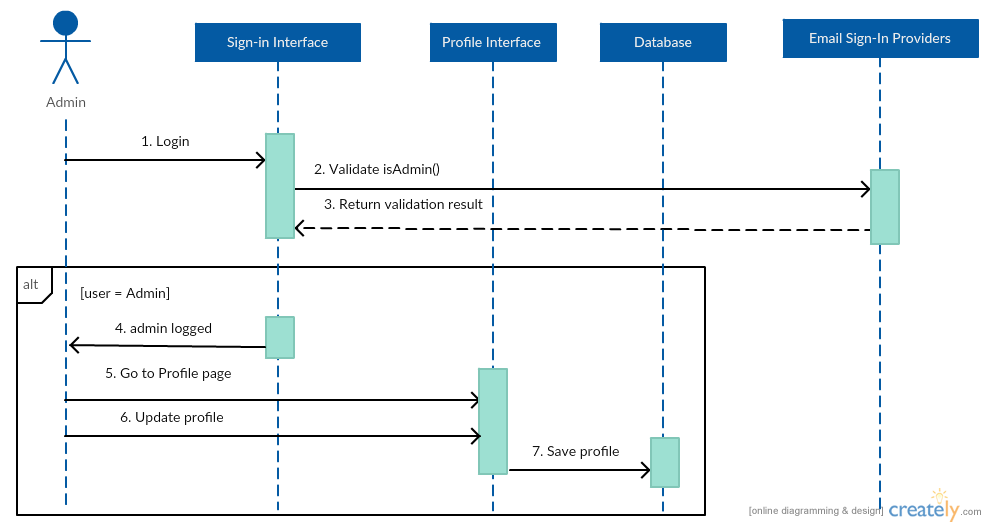
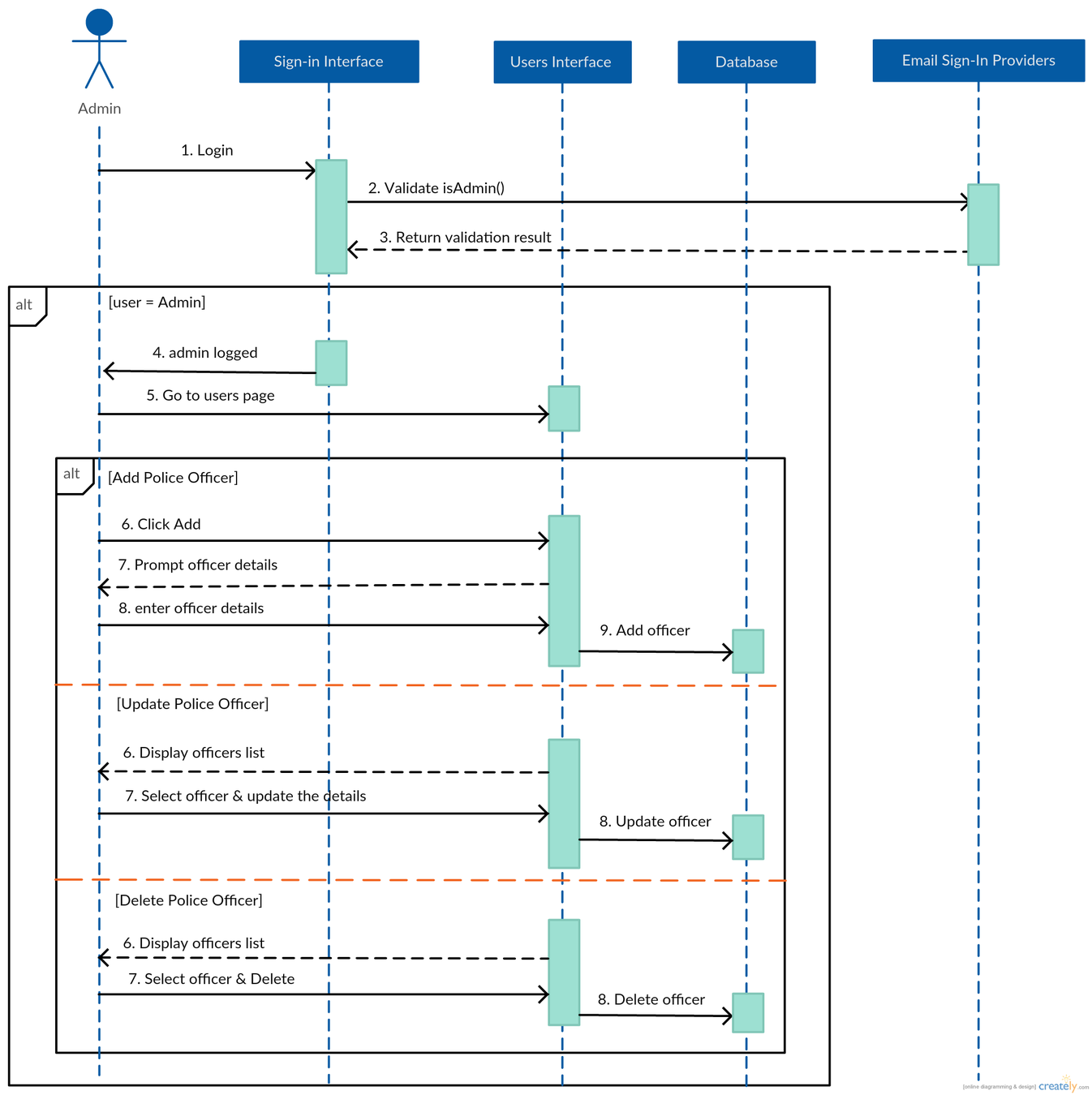
Manage users
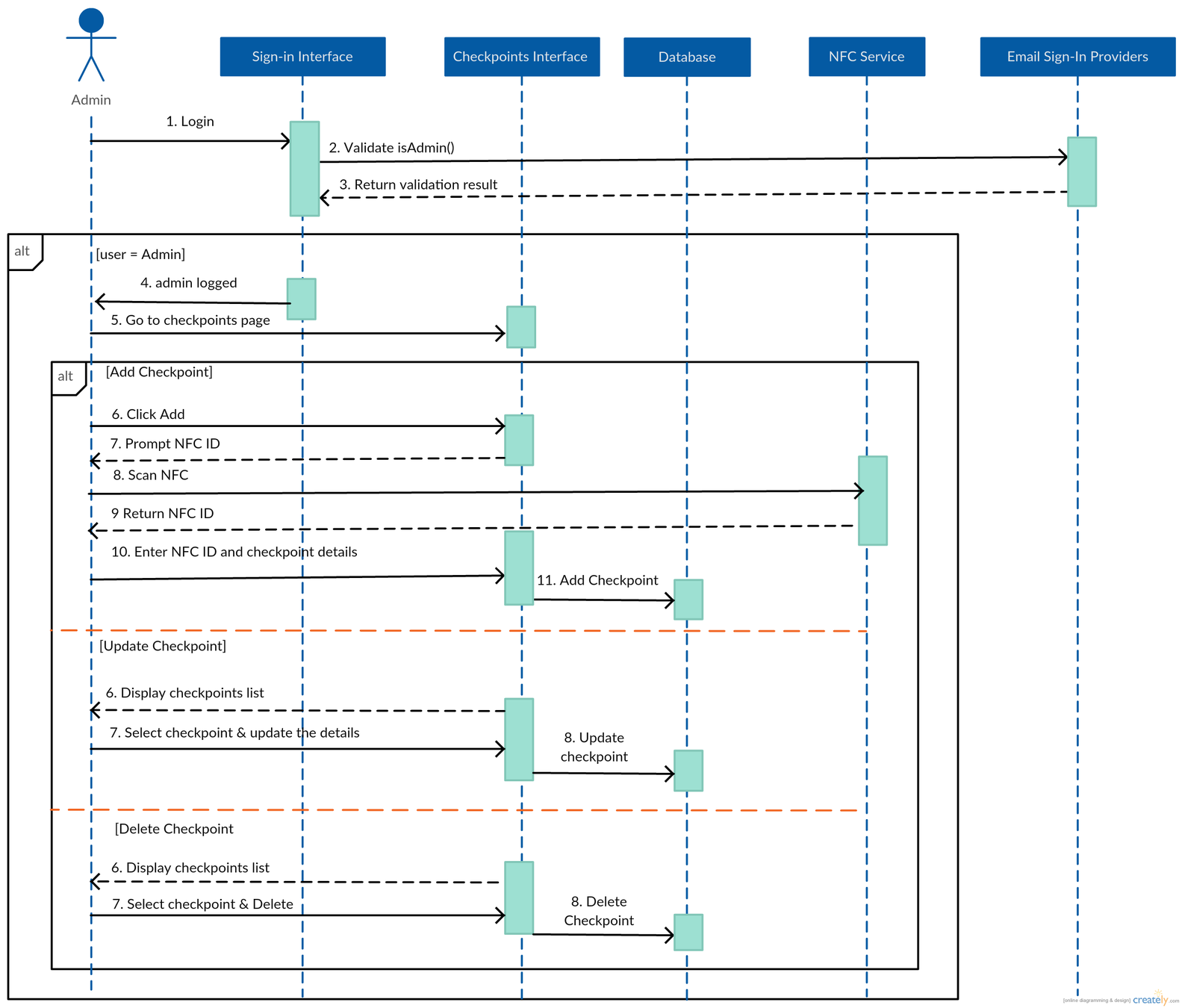
Manage checkpoints
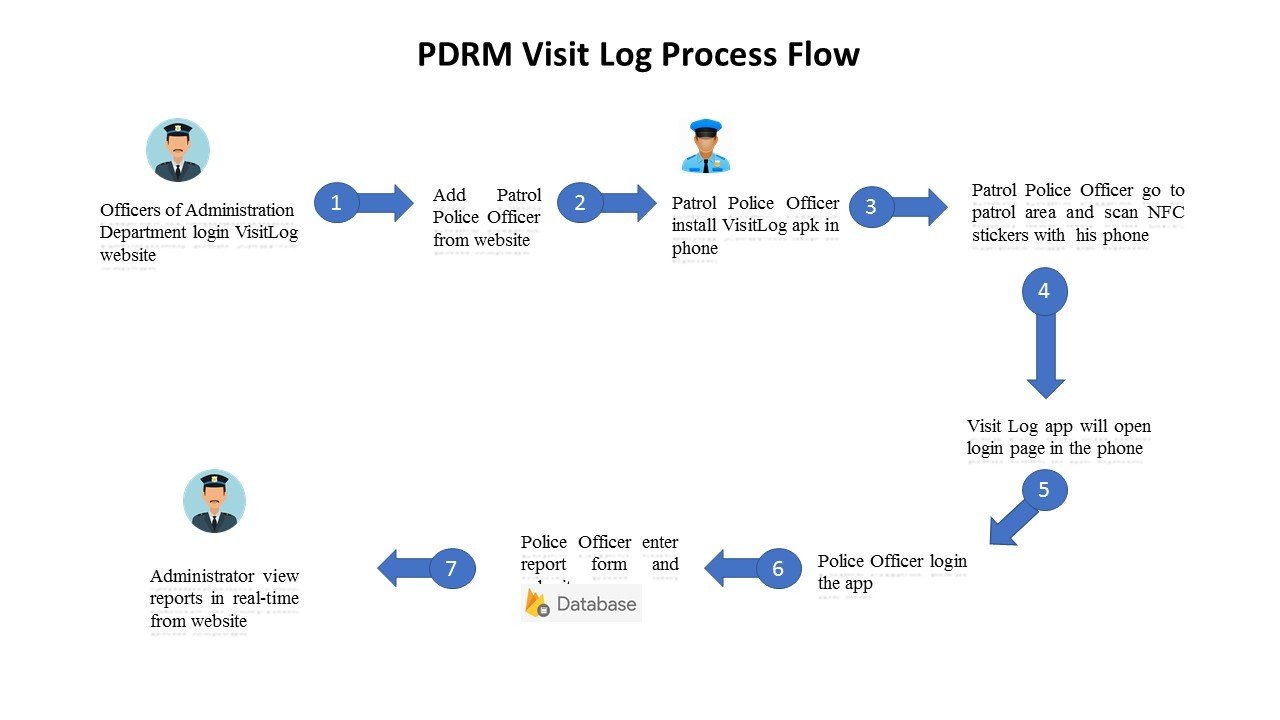
After conducting several studies through literature reviews, interview, and questionnaires analysis, a system has been proposed to solve the inefficiency of patrol activities which involve police logbook (Buku Lawatan Polis).
This research project is committed in developing the innovation as an IT Solution in a real scenario for the implementation of Police Logbook (Buku Lawatan Polis) activities
Conclusion
Proposal Defense
By fadziljusri
Proposal Defense
FYP1 Proposal Defense, Universiti Teknologi PETRONAS
- 232




