password recovery
Gordon, Stanley 2016-07-28
Last week todo
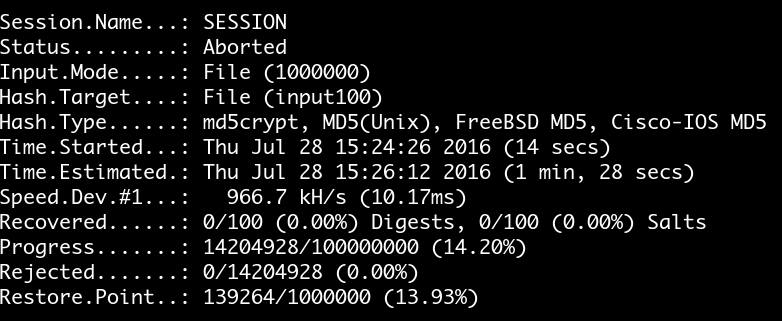
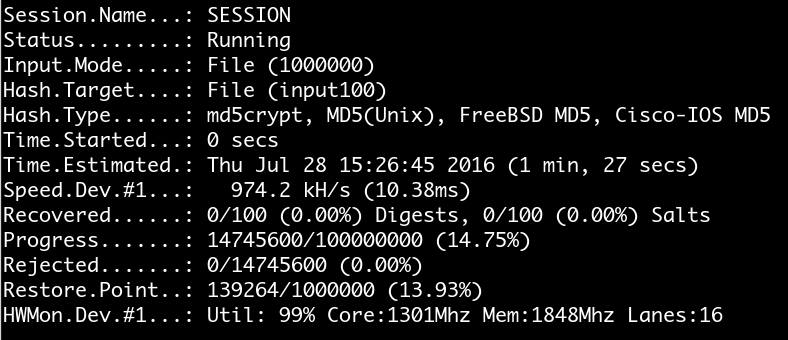
try restore
try different attack mode
Restore
$ hashcat --session <SESSION_NAME> ...
Run hashcat with a session name
hashcat will generate two files
- SESSION_NAME.log
- SESSION_NAME.restore
$ hashcat --restore --session <SESSION_NAME> ...
Restore hashcat with the session name
Attack Modes
- Wordlist
- Brute-force
- Combination
- Hybrid
Brute-force
Try all combinations for given charsets
ex:
rule: ?d?d
will generate
00, 01, 02, ..., 99
Brute-force charsets
?l = abcdefghijklmnopqrstuvwxyz
?u = ABCDEFGHIJKLMNOPQRSTUVWXYZ
?d = 0123456789
?s = !"#$%&'()*+,-./:;<=>?@[\]^-`{|}~
?a = ?l?u?d?s
?b = 0x00 - 0xff
Combinator
Each word of a dictionary is appended to each word in another dictionary
ex:
dictionary1: A, B, C
dictionary2: 0, 1, 2
will generate
A0, A1, A2, B0, B1, B2, C0, C1, C2
Hybrid
Similar to combinator attack,
One side is a dictionary
another side uses brute-force
ex:
dictionary: A, B, C
brute-force rule: ?d
will generate
A0, A1, ..., A9, B0, B1, ..., C9
Comparison
compares the following:
- pure wordlist
- wordlists, 2digits list combination
- wordlist, 3digits list combination
- wordlist + 2digit brute-force
- wordlist + 3digit brute-force
First Experiment
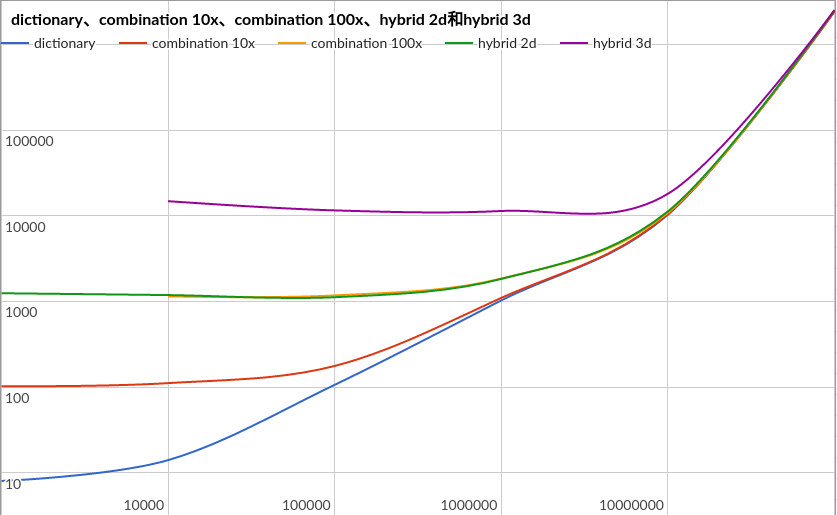
Result
Second Experiment
There are about 5000 names in English
Compare three attach modes using:
5000 names + 1~4 digits
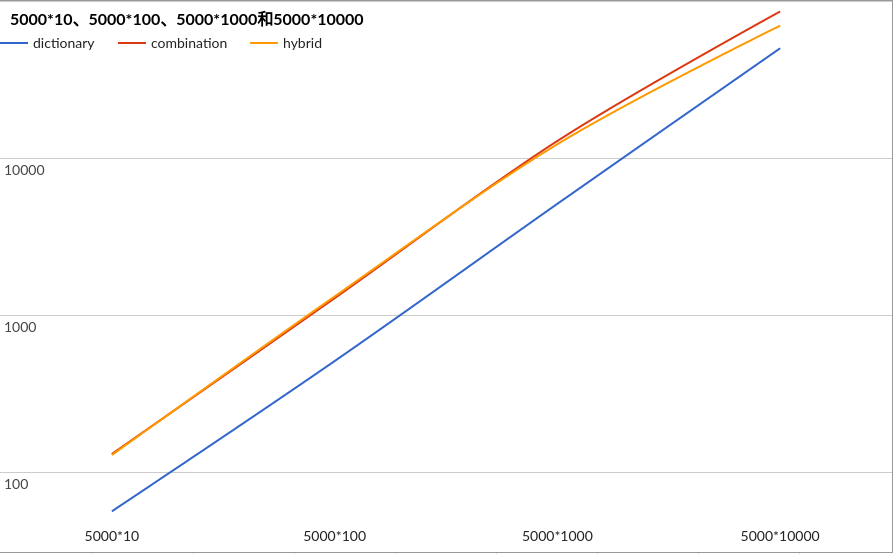
Result
Next week todo
try the remaining attack mode
collect password lists
trace hashcat
password recovery
By Gordon Ueng
password recovery
- 603



