Cryptography
Garasto Giorgio
Guerra Francesco
5°C IA I.T.S.T. J.F. Kennedy
A.S. 2015-2016
History
- From Greek kryptós, graphein,logia
- Secure communication in the presence of third parties called adversaries
- Modern cryptography is heavily based on mathematical theory and computer science
- Legal issues in the information age: many governments classified cryptography as a weapon
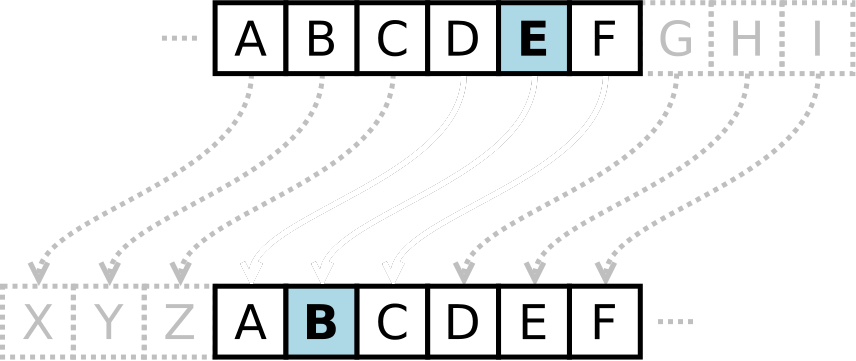
Caesar cipher
- Simplest but most widely known encryption technique
- Named after Julius Caesar who used it to protect messages of military significance
- Substitution of the cipher where the plaintext is replaced by another letter in the alphabet
ENIGMA
- Used during World War II
- Its decryption allowed the allies to win the war
- It started the computer era

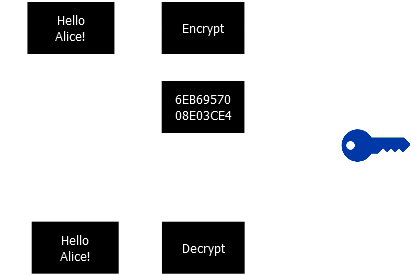
Symmetric key cryptography
- Sender and receiver share the same key
- DES (Data Encryption Standard) and AES (Advanced Encryption Standard) have been designated as Cryptography standards by the U.S. government
- Although it is deprecated it is widely used on ATM, e-mail privacy
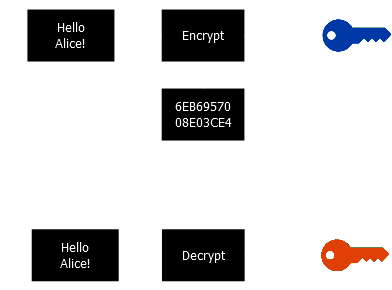
Asymmetric cryptography
- Sender and receiver have both a public and a private key
- The sender uses the receiver's public key to encrypt data
- The receiver decrypts data using its private key
- RSA is one of the most used asymmetric algorithm
Examples of cryptography
- Uses MTProto Mobile Protocol
- Developed by the same team that created Telegram
- Combination of symmetric and asymmetric encryption
- Offers US$300,000 to who discovers a security breach
- A vulnerability has theorically been found, but can't be practically applied
Telegram

Examples of cryptography
- Security is an essential part of any transaction that takes place over the internet.
-
there are 3 requirements for safe e-payments
- Confidentiality
- Integrity
-
Availabilty
-
HTTPS (HTTP over Secure Socket Layer)
-
Extend HTTP internet protocol with
public key encryption, authentication
and digital signature.
-
E-commerce

The End
Sources:
https://en.wikipedia.org/
https://core.telegram.org/
http://www.cisco.com/
Cryptography
By Giorgio Garasto
Cryptography
- 271

