The Operational View
by Giorgio Garasto
Evolution of hacker attacks
- In the 2000s, hackers used to use worms
- Now, hackers use BotNet
-
To prevent attacks, you can't just
- Prevent attacks to singular hosts
- Have a good security policy on the hosts
- Have a well configured firewall
You need these things all together!
How Cisco reacts to attacks
-
CSIRT (Cisco Security Incident Response Team)
- Monitors all the activities from and to the Cisco servers
- Queries the log database if something happens
-
SIO (Cisco Security Intelligence Operations Team)
- Specialized branch of the CSIRT
-
It's devided into
- Analysis team (analyzes the NetFlow)
- Investigation team (investigates if an attack happens)
Tools to prevent and detect attacks
- IronPort: prevents spam and bad attachments on the emails
- Proxy (WSA/WCCP): silently checks all of the network traffic
- Firewall: blocks incoming and outgoing network traffic based on predefined rules
- NetFlow: logs everything that happens on the network
- IPS/IDS: checks inflow packets using predefined patterns
- FireEye: checks attachments using stored hashes
- Data Collection: allows to know exactly what happened before, during and after an attack
IronPort
IronPort Systems, Inc. was a company best known for its AntiSpam, SenderBase email reputation services and email security appliances. In 2007, IronPort was acquired by Cisco Systems.
Proxy (WSA/WCCP)
-
WSA (Web Security Appliance): combines advanced threat defense, advanced malware protection, application visibility and control, insightful reporting and secure mobility into a single solution
- WCCP (Web Cache Communication Protocol): it's a routing protocol that allows to redirect traffic flows in real-time
NetFlow
NetFlow is an hardware
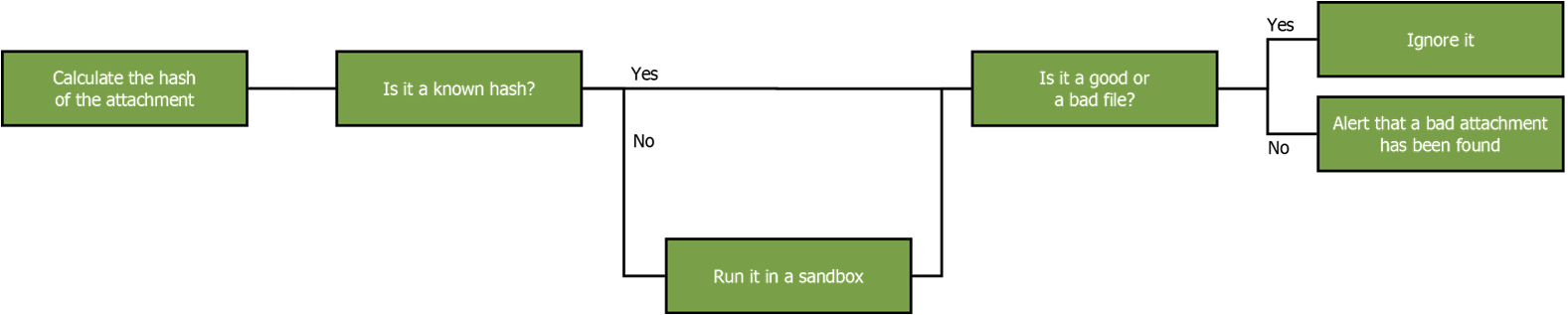
How does FireEye work
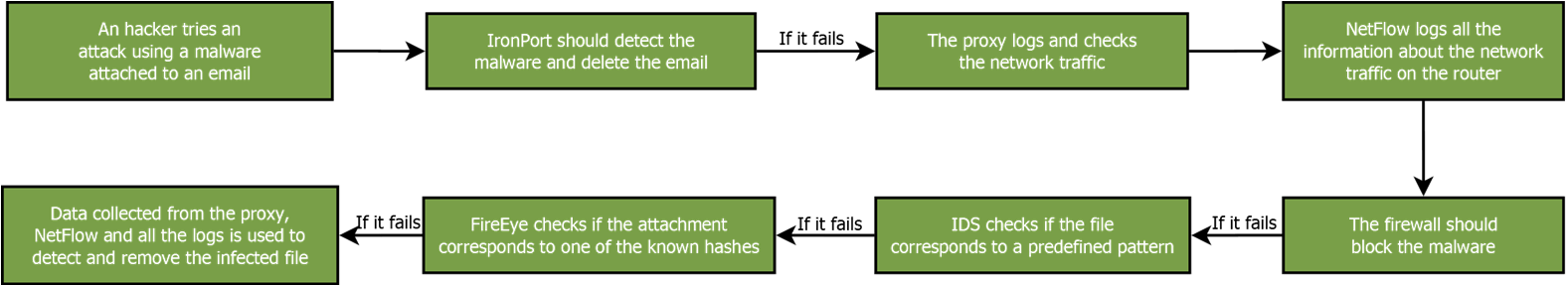
Malware attack example
The End
Source:
Cyber Security: The Operational View by Gavin Reid
The Operational View
By Giorgio Garasto
The Operational View
Summary of The Operational View explanation by Gavin Reid
- 215

