Cybersecurity 101
Silvia Puglisi: www.hiro7.eu - @nopressure
Hello World
My name is Silvia and I am a security/privacy researcher
I am a Ph.D. Candidate at UPC - Barcelona
I am currently working @ torproject.org
I am here to talk about cybersecurity in practical terms.
What is cybersecurity?
Cybersecurity is the protection of computer systems.
A computer system can be anything from your watch to your bank account.
Personal data protection is actually personal safety.
What does this mean?
- Part of our lives are lived online
-
In 2011, the amount of digital information created and replicated globally exceeded 1.8 zettabytes (1.8 trillion gigabytes) *.
- “meta-data” is collected and stored by public and private organisations about our actions, both online and offline.
* Library Briefing - Library of the European Parliament - 01/03/2012
Cybersecurity is as ordinary as the weather
Attacks are common
- Latest attacks exibihits massive scale
- Used CCTV cameras, digital video recorders, home routers, and other embedded computers interconnected as part of the IoTs.
What this attack demonstrates is that the economics of the IoT mean that it will remain insecure unless government steps in to fix the problem. This is a market failure that can't get fixed on its own.
Bruce Schneier
https://www.schneier.com/blog/archives/2016/10/security_econom_1.html
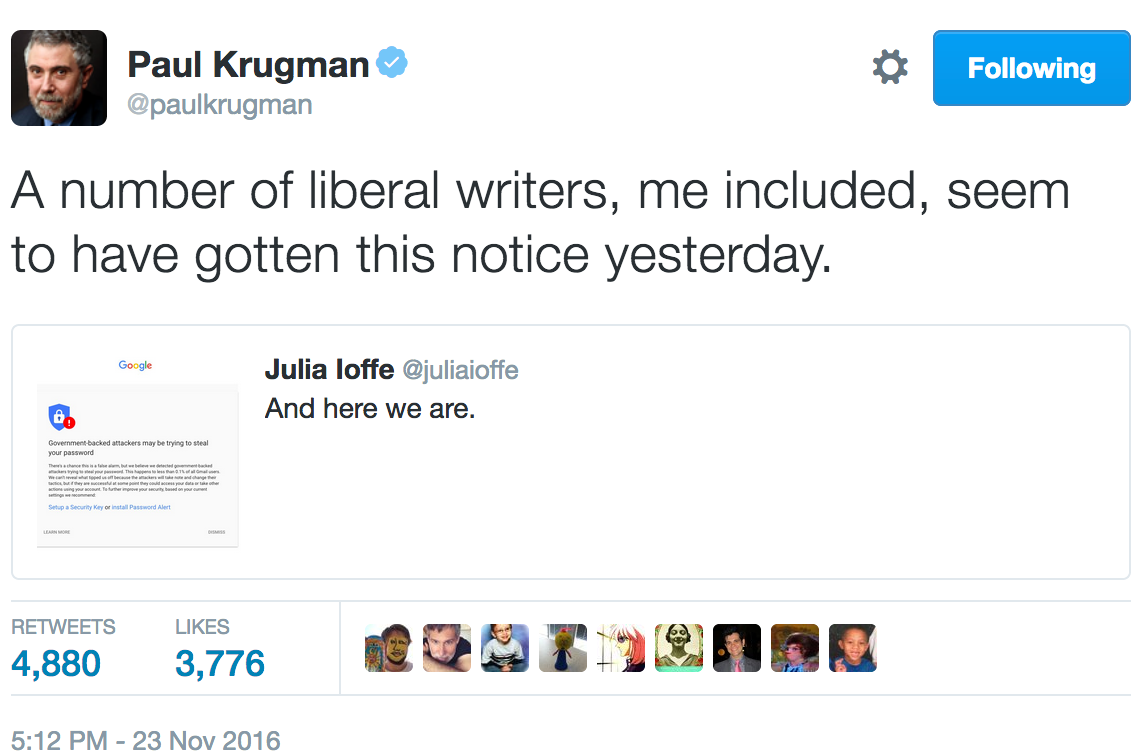
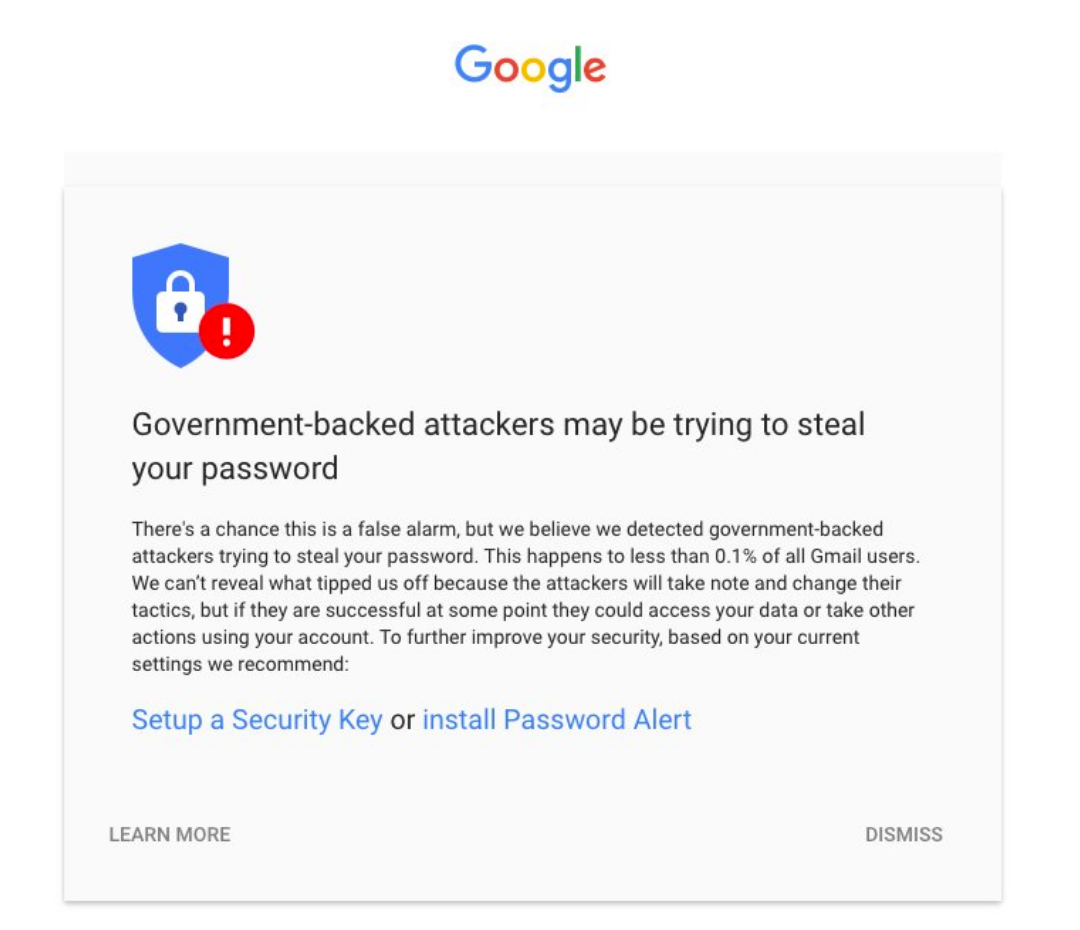
cybersecurity challenges
- Computer systems are complex.
- It is difficult to know which parties are trustworthy.
- What if things change?
Things can always change
The internet activity of everyone in Britain will have to be stored for a year by service providers, under new surveillance law plans.
State Simple Objectives
- I want to protect myself and the people I communicate with.
- I do not want third-parties to know where I am.
- I do not want third-parties to know what I do.
- I do not want third-parties to know what I am interested in.
I want to protect myself and the people I communicate with.
- Use unique passwords, use a password manager, use 2fa (or secure alternatives).
- Use encryption when you communicate. There are simple and free alternatives to common applications.
- If you are meeting with someone and you want to be extra safe do not bring a smartphone.
I do not want third-parties to know where I am.
- Disable location sharing on your phone.
- Disable or delete apps that share location.
- If possible do not bring a mobile phone.
I do not want third-parties to know what I do.
- Do not share public updates on social media.
- Do not enable location sharing.
- If possible do not bring a phone.
I do not want third-parties to know what I am interested in
- Avoid public updates on social media.
- Use Tor when surfing sensitive material.
- Use encrypted communication systems.
Practical Tips
- Use Signal for mobile messaging:
- Use encryption for email:
- Use encrypted storage solutions:
Practical Tips
- Use unique passphrases - change them frequently (use 2fa):
- Use Tor for safe browsing:
- Use a safe Operating System:
How can you learn more
- Books:
- Tips and more tips from The Guardian
- Tips from the NYTimes
- Passwords and Hacking: the jargon
- How much is privacy worth: research paper on location privacy
- Samantha Bee on the Surveilance state (comedy)
- Deeplinks blog from the EFF
- Cybersecurity meetup in Barcelona
Thank you

me @ hiro7.eu
Cybersecurity 101
By hiropaw
Cybersecurity 101
- 1,619


