Cryptography
Victor OSTERTAG
Monday 26th of March 2018

Presentation for HP Labs
Cryptography

Plan

INTRODUCTION
A BRIEF HISTORY
MODERN CIPHERS
CONCLUSION
Presentation for HP Labs
Cryptography

Who am I?

Victor Ostertag



Software Engineering background
Presentation for HP Labs
Cryptography

The presentation
Present Spectre and Meltdown to people with no CS background
Present cryptography in a way that everyone can understand
A brief history

Cryptography

Presentation for HP Labs
Presentation for HP Labs
Cryptography

What is cryptography?
A
B
E
lice
ob
ve

It's all about solving the following problem:
Presentation for HP Labs
Cryptography

The idea





Share a key to a lock
ENCRYPTION

DECRYPTION
Presentation for HP Labs
Cryptography

Cryptography
Secret
Message
"Hello, I am doing a presentation for HP Labs"
"Khoor, L dp grlqj d suhvhqwdwlrq iru KS Odev"
"Hello, I am doing a presentation for HP Labs"
CIPHER

Some information

Presentation for HP Labs
Cryptography

Caesar Cipher

Shift each letter by a certain amount
With a shift of 3:
| A | D |
|---|---|
| B | E |
| C | F |
| D | G |
| E | H |
Presentation for HP Labs
Cryptography

Example
"Hello, I am doing a presentation for HP Labs"
"Khoor, L dp grlqj d suhvhqwdwlrq iru KS Odev"Presentation for HP Labs
Cryptography

Brute Force
Trying all the possibles keys
"Jgnnq, K co fqkpi c rtgugpvcvkqp hqt JR Ncdu"
Shift of 1
"Ifmmp, J bn epjoh b qsftfoubujpo gps IQ Mbct"
Shift of 2
"Hello, I am doing a presentation for HP Labs"
Shift of 3
Presentation for HP Labs
Cryptography

Another approach
"Hello, I am doing a presentation for HP Labs"
Some letters are more frequent than others...
3 E
4 A
1 G
Frequency Analysis
Presentation for HP Labs
Cryptography

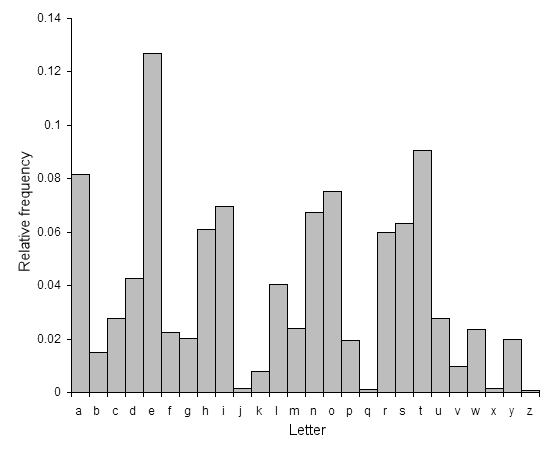

Normal
New
3
Presentation for HP Labs
Cryptography


Easy to break using brute force
Frequency analysis
gives us the key
Conclusion
HOW TO AVOID THAT?
Presentation for HP Labs
Cryptography

Polyalphabetic ciphers

FLATTEN THE FINGERPRINT
MORE KEYS (KEY SPACE)
Presentation for HP Labs
Cryptography

The idea
Use a word as a key

HPL
Convert it to numbers
8 16 12
Presentation for HP Labs
Cryptography

"Hello, I am doing a presentation for HP Labs"
8 16 12
8

16
12
8
16
12
"Hello, I am doing a presentation for HP Labs"
Presentation for HP Labs
Cryptography

Example
"Otwsd, t hb ovxyn p aytdlcehitvc qvg sw alih"
But there still is a problem...
Presentation for HP Labs
Cryptography

Repetition
"Hello, I am doing a presentation for HP Labs"
We need to find the length of the key

Presentation for HP Labs
Cryptography

Breaking the cipher
Create frequency tables for different intervals
No result
No result

Clear pattern
Interval of 2
Interval of 3
Interval of X
Presentation for HP Labs
Cryptography

One time pad
How to avoid repetition?

Sequence of shifts as long as the text

Randomness
Presentation for HP Labs
Cryptography

How strong?
Unbreakable!

What about brute force?
3.3424674e+49 possibilities!
30000000000000000000000000000000000000000000000000

Modern ciphers
Cryptography

Presentation for HP Labs

Presentation for HP Labs
Cryptography

Symmetric Ciphers
What we have seen so far



Have to share a key beforehand
Presentation for HP Labs
Cryptography

Two types
Stream Cipher
Encrypts each letter one at a time
Block Cipher
Encrypts the text in blocks
Presentation for HP Labs
Cryptography

Problem with Internet

MEETING
IMPOSSIBLE





Alice
Bank
YouTube
IMPRACTICAL
Presentation for HP Labs
Cryptography

Assymetric Ciphers
A
B
E
lice
ob
ve






Public key
Private key
It is indeed Alice!
Presentation for HP Labs
Cryptography

Maths


Easy


Hard
TRAPDOOR ONE-WAY FUNCTION

The Trapdoor
Presentation for HP Labs
Cryptography

The Phi function
Counts the number of coprime of a given number
8
7
6
5
4
3
2
1
Phi(8) = 4
Presentation for HP Labs
Cryptography

The Phi function
Phi (prime) = prime - 1
Phi (m * n) = Phi (m) * Phi (n)
Two important properties:
Presentation for HP Labs
Cryptography

RSA: Creating keys
- Select two large prime numbers: p and q
- Calculate n = p * q
- Calculate Phi(n) = (p-1) * (q-1)
- Choose e between 1 and Phi(n) and coprime of Phi(n)
- (n, e) is the public key
- The private key d must solve: d * e = 1 (mod(Phi(n)))
Presentation for HP Labs
Cryptography

RSA
To convert a message M into a cipher C:
C = M ^ e (mod(n))
To decrypt:
M = C ^ d (mod(n))
Conclusion
Cryptography

Presentation for HP Labs
Presentation for HP Labs
Cryptography

We only scratched the surface!
Hash functions

Random numbers
Networks

Cryptography: An introduction
By isvoli
Cryptography: An introduction
- 1,177



