Hacking The BDP File for FUN AND PROFIT
(FROM A UI PERSPECTIVE)

Pre 2020

2020
Jim Cummins @jimthedev
Connected App Framework
What is the .bdp file?
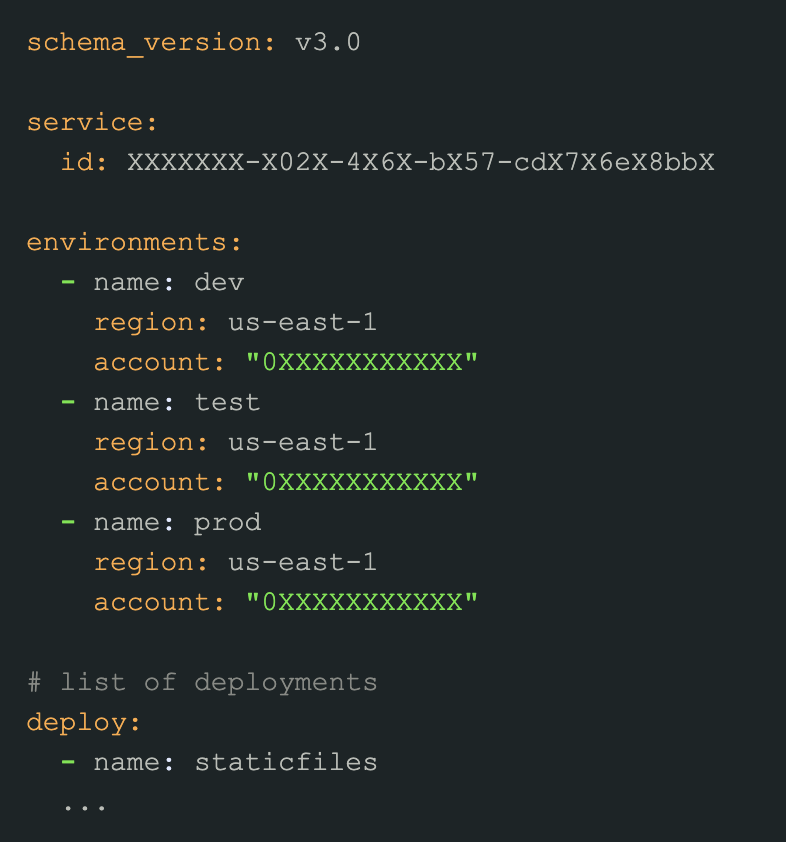
ENHANCE
DEPLOY
SECTION
DOCS
UI dev looks for static DEPLOY in the bdp schema
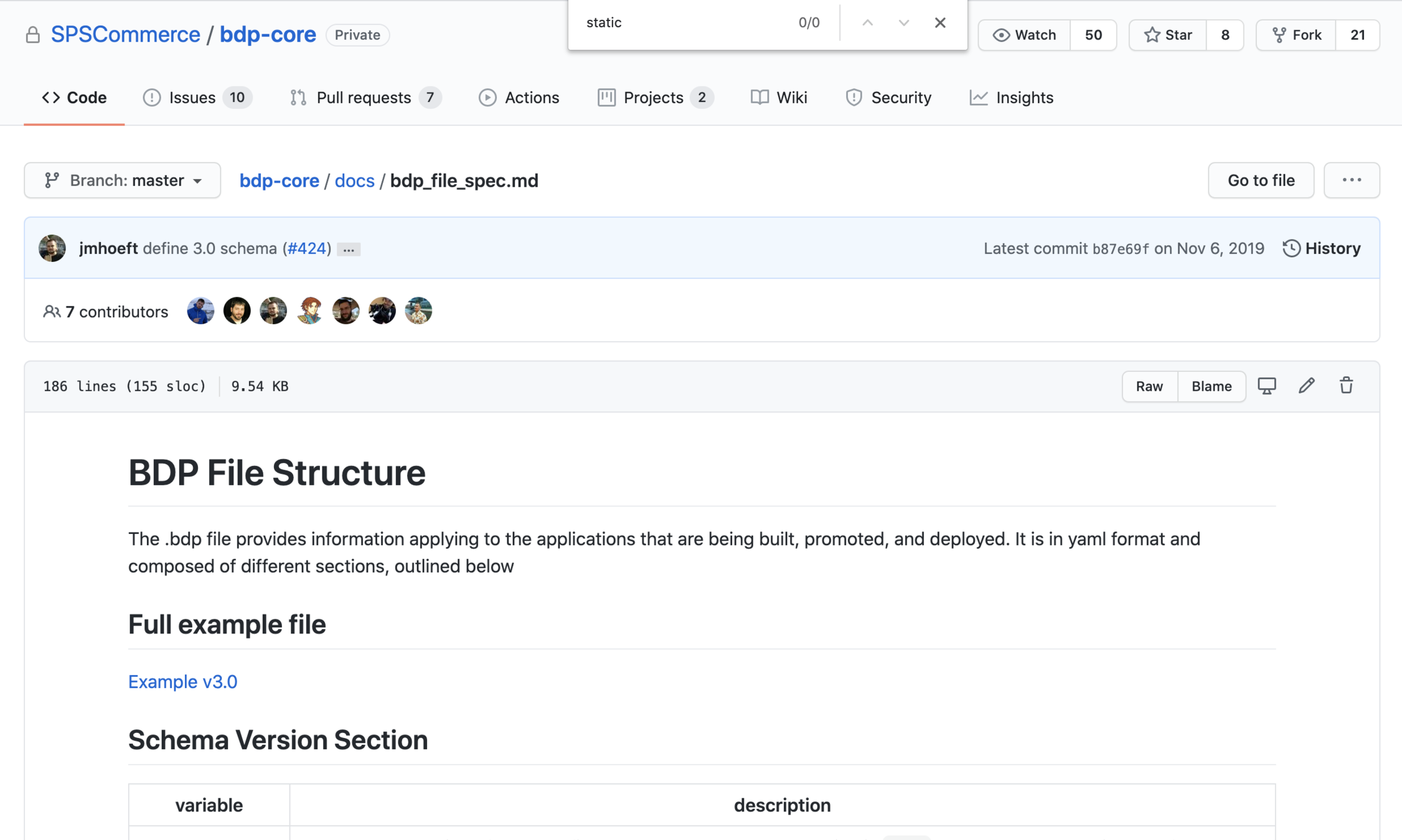
0 results for static assets. Does this mean I have to run...a server?

FEAR NOT UI DEV!
FOR THERE ARE MORE PLACES TO SEARCH
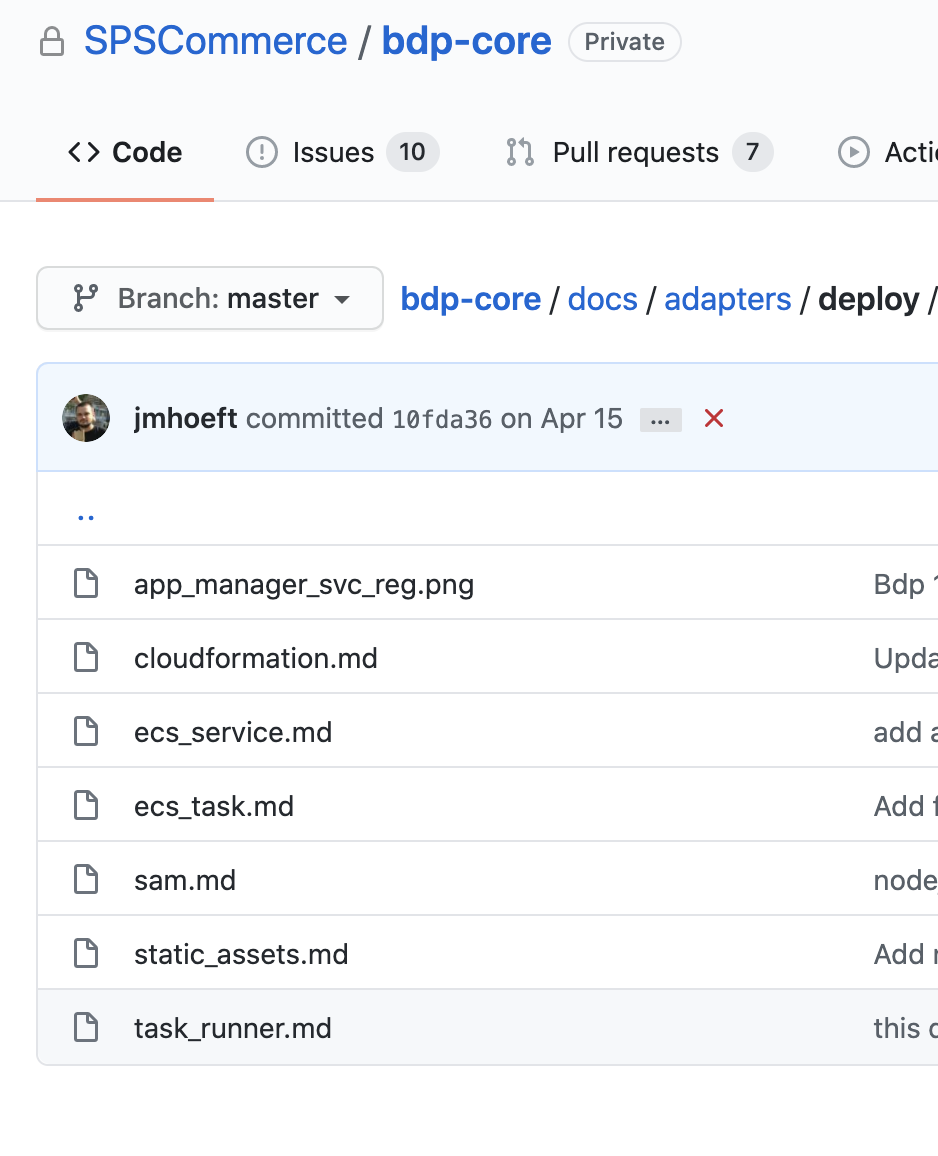
Text
Why use static assets?

tldr; we want to deploy our static UI assets
RIGHT BUT Why ARE WE talking about "hack the BDP File for Fun anD Profit" when there are docs outlining the INTENDED file STRUCTURE?
Umm, We have REST APIS...

WITH SWAGGER
Growth leads to increased data model complexity
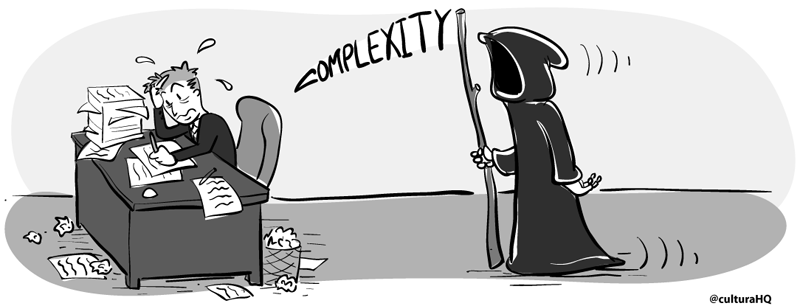
Which leads to REST APIS with Swagger calling rest APIs with Swagger

APIS!!!
Which leads to Complexity+Latency
FIRST OFF, MAYBE don't DO WHAT YOU ARE ABOUT TO SEE
(Unless you need to but even then maybe do a PR to bdp to improve this specific experience instead)
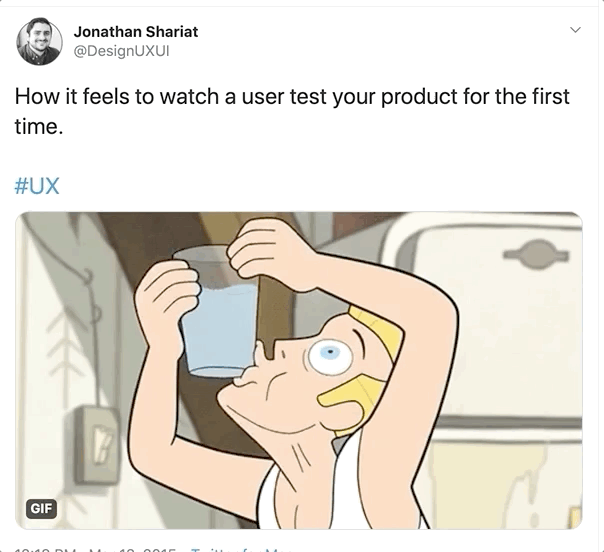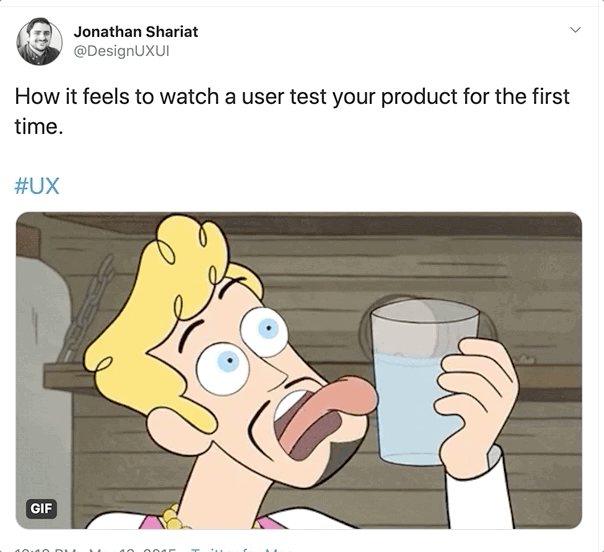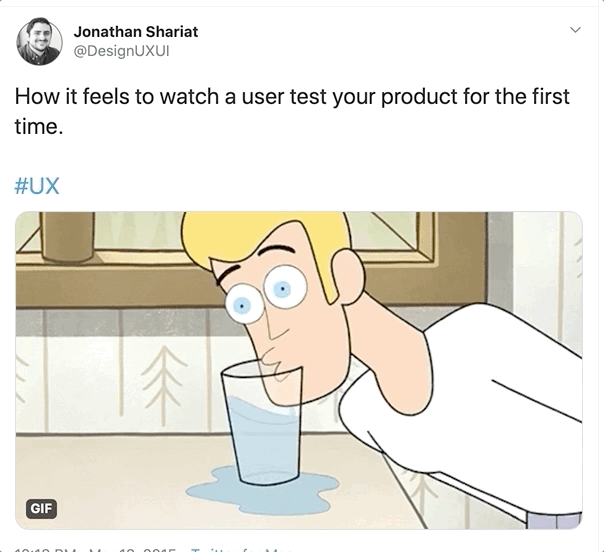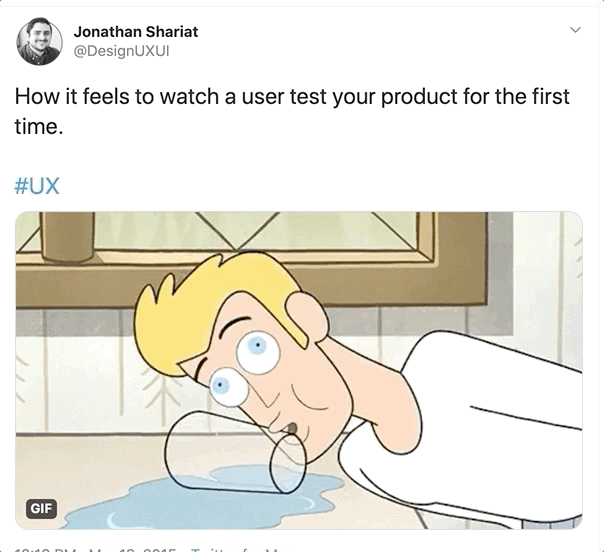
TWO UI DEVS
JUST Trying
to work
(via a really old iPhone without spell check apparently?)
What are some Goals we have?
- Enable non-technical and/or external reviews of the actual experience before release
- Increase likelihood of spotting regressions by reducing cost of each review
- Make pre-deployment QA easier
- Retain historical build artifacts at low cost
- For UI libraries, be able to see build examples and play with components pre- merge and release to deployment channel
EACH UI COMMIT (Which triggers OUR CI BUILD) GENERATED A UNIQUE Url?
What if...
URLS
- A basic building block of the web
- Very inexpensive if content hosted on s3
- Easy to share
each commit to a PR generated a new url and it AND A BOT posted THAT URL back to the PR
SO WHAT IF...
COOL story but I am basically lazy and I'd need to go into CI LOGS to get the url Every time
So we did this in Design System
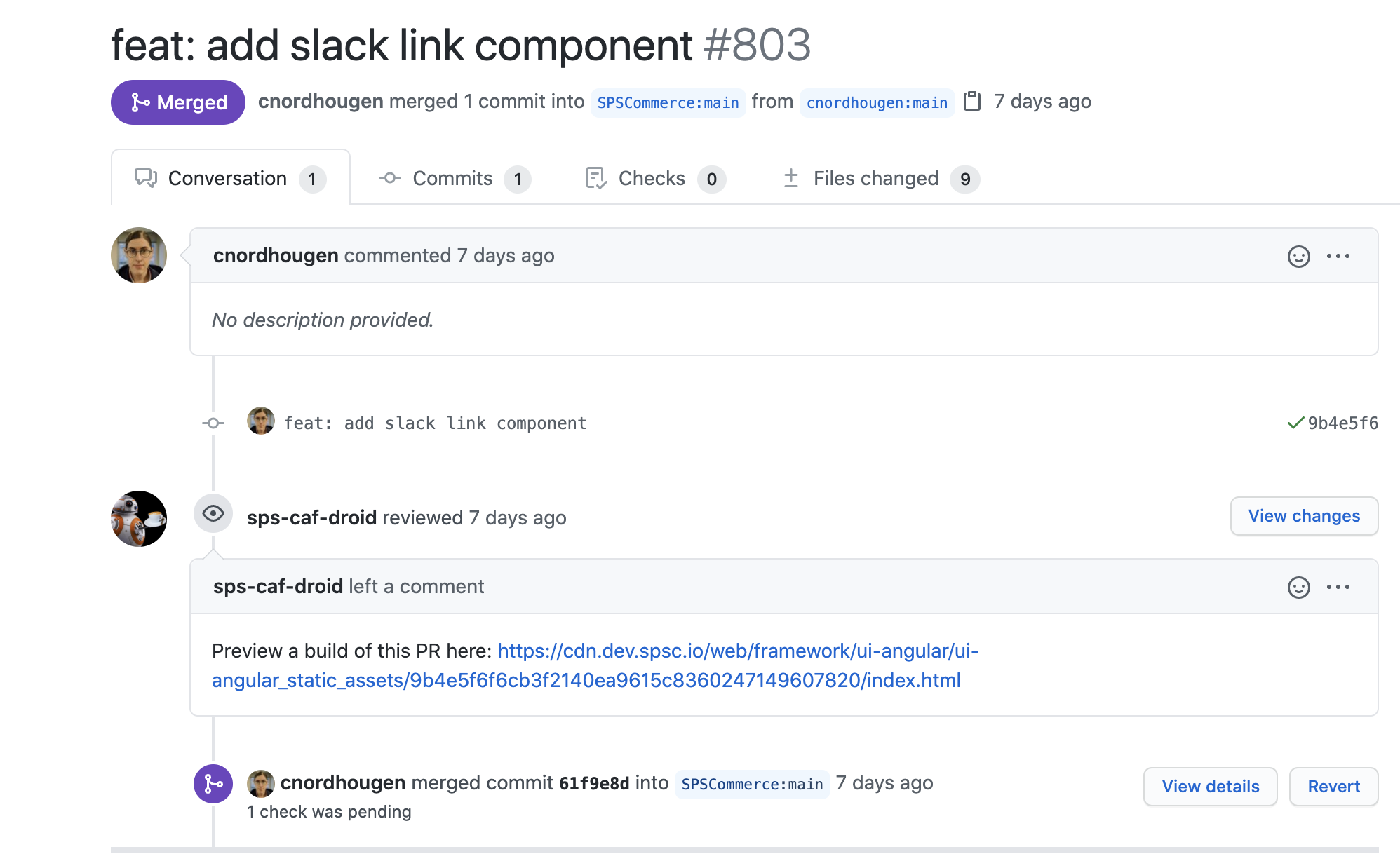
Product owners or DESIGNERs can see what things are going to look like before release
How we (DANGEROUSLY) did it?
CREATE A BOT GITHUB ACCOUNT THAT HAS ACCESS TO YOUR REPOS (SORRY SECURITY?)
CREATE A GITHUB TOKEN FOR THAT USER TO BE USED FROM HERE FORWARD AS YOUR GH_TOKEN
How we (DANGEROUSLY) did it?
MAKE SURE YOUR REPO IS PRIVATE
DRONE SECRETS WEB UI IS INSUFFICIENT FOR THIS TASK, USE CLI BUT BEWARE IT IS A PAIN!
PLACE GH_TOKEN SECRET INTO DRONE/CI IN YOUR PRIVATE REPO
FOR YOUR PRIVATE REPO TELL YOUR CI TO EXPOSE THE GH_TOKEN SECRET FOR PULL REQUESTS
(IF YOUR REPO LATER BECOMES PUBLIC, GH_TOKEN WILL BE LEAKED TO VILLAN BY YOUR CI SO BE CAREFUL OR BETTER YET DON'T DO ANY OF THIS)
Look at Code!
Hacking BDP
By jimthedev
Hacking BDP
- 1,126



