Overview, WEb apps and Threats, HTTP and REST
Secure Web Application Development
Joshua Mcshannon
University of Nebraska at Omaha
CYBR 8470 - Introduction Module
CYBR8470
Introduction ModuLe
Intro Module
Part 0: Quick Introductions
Part 1: Class Content Overview
Part 2: Web Apps and Attack Vectors Intro
Part 3: HTTP Review and Intro to RESTful APIs
Part0: Quick Introductions
New Dad, Linux Lover, Dog Father, Security Engineer, Threat Modeler, Developer, Traveler, Student, Teacher, Musician
WHOAMI
jmcshannon@unomaha.edu

Part1: Class Content Overview
What is this class?
This class is all about making. It is practitioner oriented. There will be a fair amount of coding involved. It will make you stretch. It is "hard."
That said...
- Anyone can do it! (even if you have little or no programming experience)
- You will feel great when you create something new and expand your comfort zone.
- I'll do my best to help keep you out of the panic zone.

Img credit: https://www.developgoodhabits.com/comfort-zone/
Comfort Zone
Stretch Zone
Panic Zone
Learning
Risk
Challenge
Growth
"Hard"
"Easy"
Boring
Anxiety Free
"Impossible"
Fear
Stress
Overwhelming
Model originally described by psychologists Robert M. Yerkes and John Dillingham Dodson in 1908
This class
Ok, So what will we cover?
- Web Services, REST, and SOA
- Server-side Development: Creating RESTful APIs
- Client-side Application Development
- Application Penetration Testing and Test-Driven Development
- Software Engineering: Architecture and design
- Server hardening and deployment
Languages and Platforms/Libraries








A Note about LLMs




Part2: Web Apps and Attack Vectors Intro

(nearly) All companies have a web app
You probably use them, daily.
Web Page ≠ Web Service ≠ Web App
Terminology
web page: an HTML (HyperText Markup Language) document that contains certain content (images, videos, text, etc)
web app: a web application is a piece of software that presents its user interface in a web browser. A web app typically includes at least one web service and generates many web pages in response to different user actions. The key difference between an app and a service is that an app is user facing, while a service is system-facing.
web service: a piece of software that serves up data through a web interface. Typically web services are object-oriented, provide access to a database, and encode data in XML or JSON.
WEb APP Reference Architecture

user

Web Application server
frontend
What the user sees
HTML, CSS, JS
perform action
see result
backend

API
data request
response
Web Services

File system
database
Processes requests, performs application logic, and provides data to the frontend
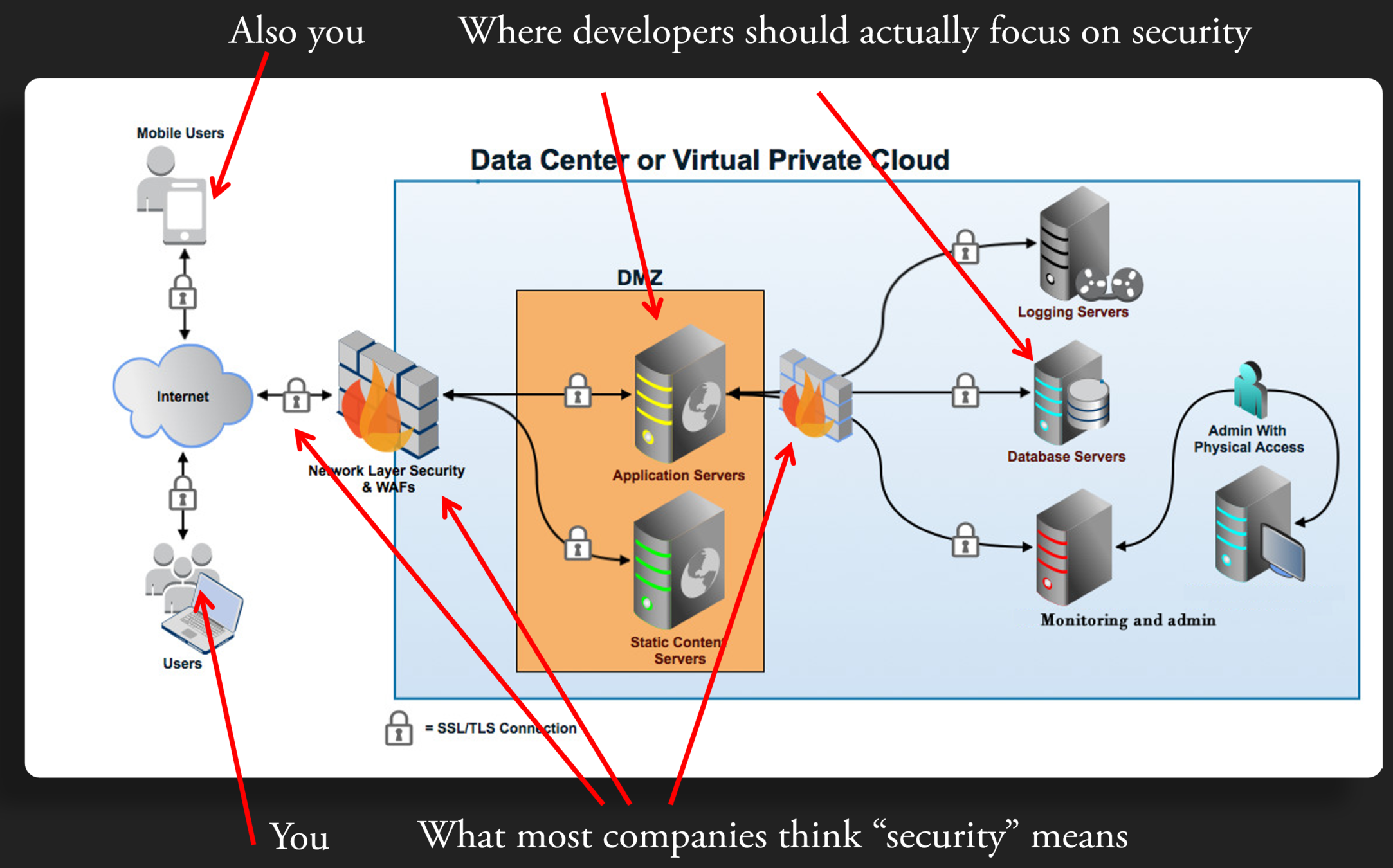
Expanded App Architecture
As a user, you expect web apps to be:
fast, responsive, always available, and secure
Despite your expectations:
80-95% of web apps have vulnerabilities*
The median number of known vulnerabilities found in these studies was 14
* according to Cenzic Application Vulnerability Trends report in 2013 and various research papers from 2015-2022
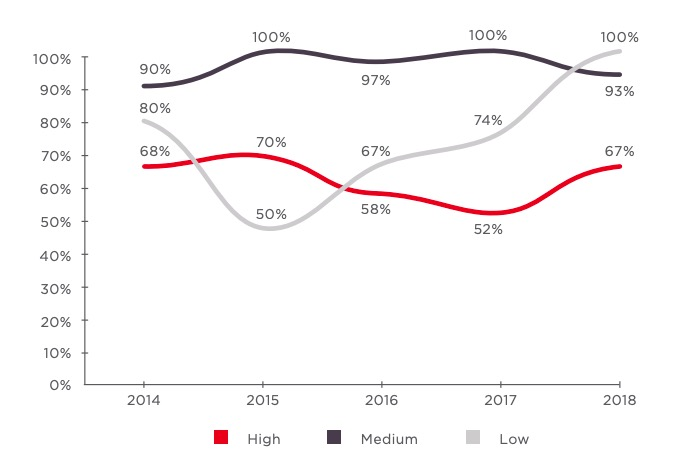
<-- How they breakdown
...at the application Level!
Edgescan, vulnerability statistics report, 2019 pg. 8.
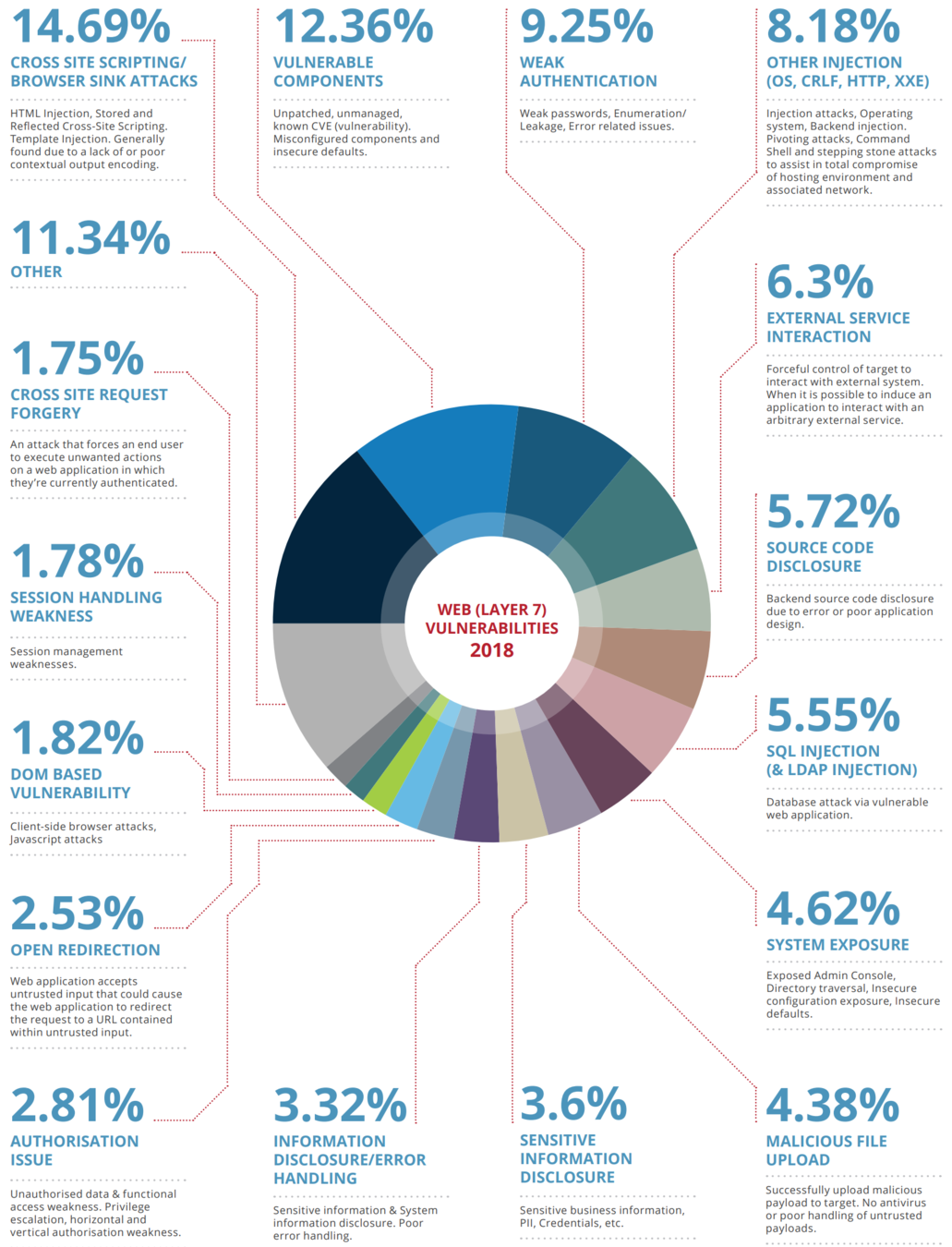
Specific example:
Study of 43 major Apps in 2019
% of websites falling within the vulnerability category
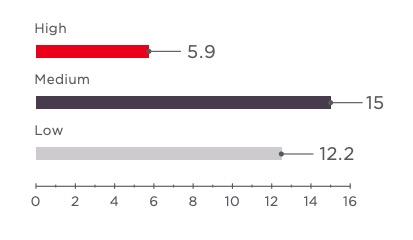
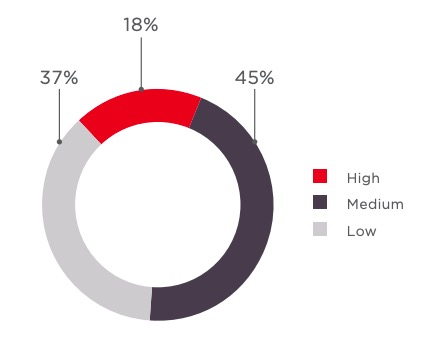
average number of vulnerabilities per application
vulnerabilities by severity
Clearly, this is problematic
Basic Web App attack Principle
...make the web application do something it was never intended to do.
aka...user input is evil.
EX: XSS
Allows attackers to inject malicious scripts into web pages and have it executed in another user’s browser. Usually to capture some user information.
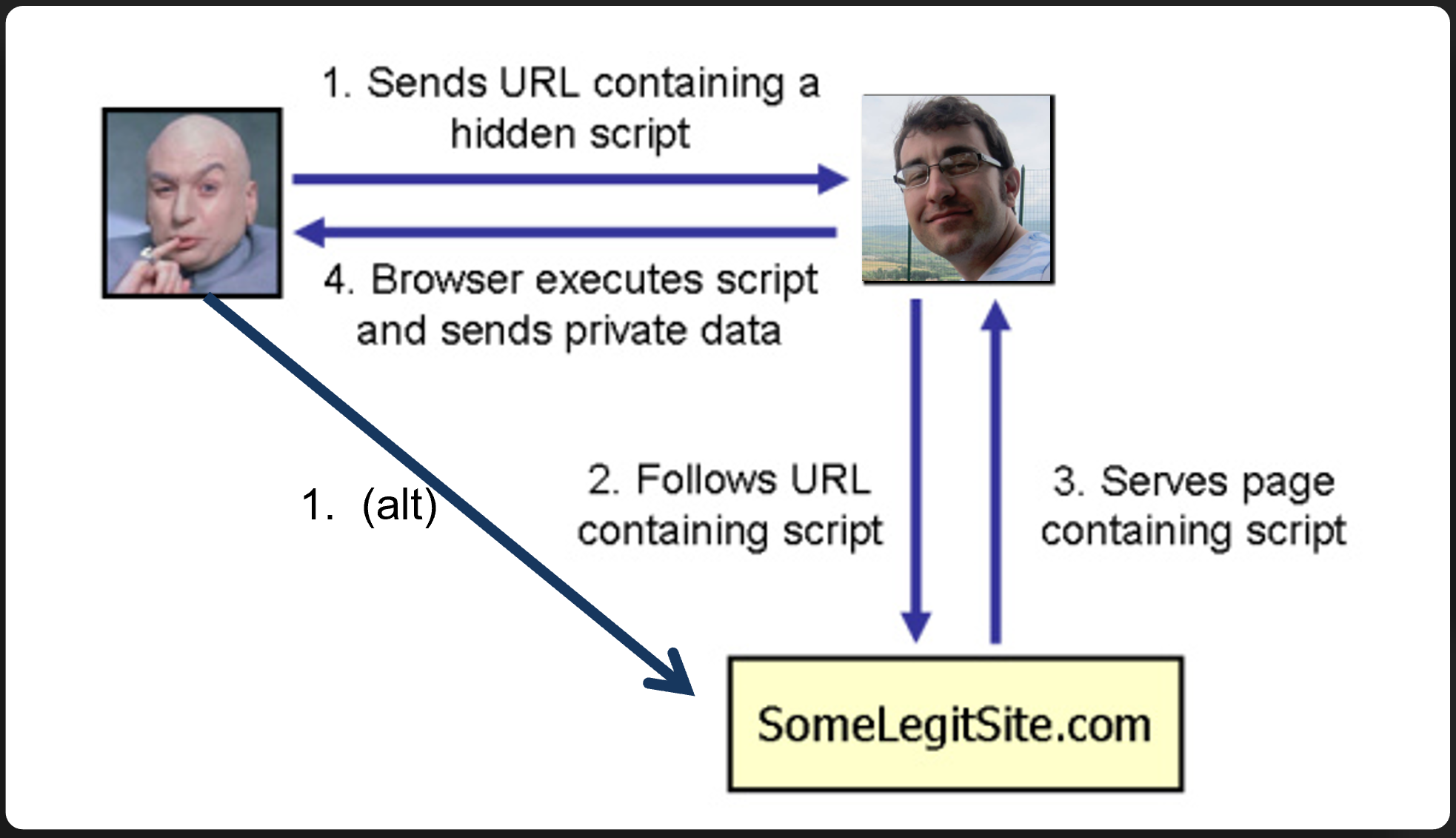
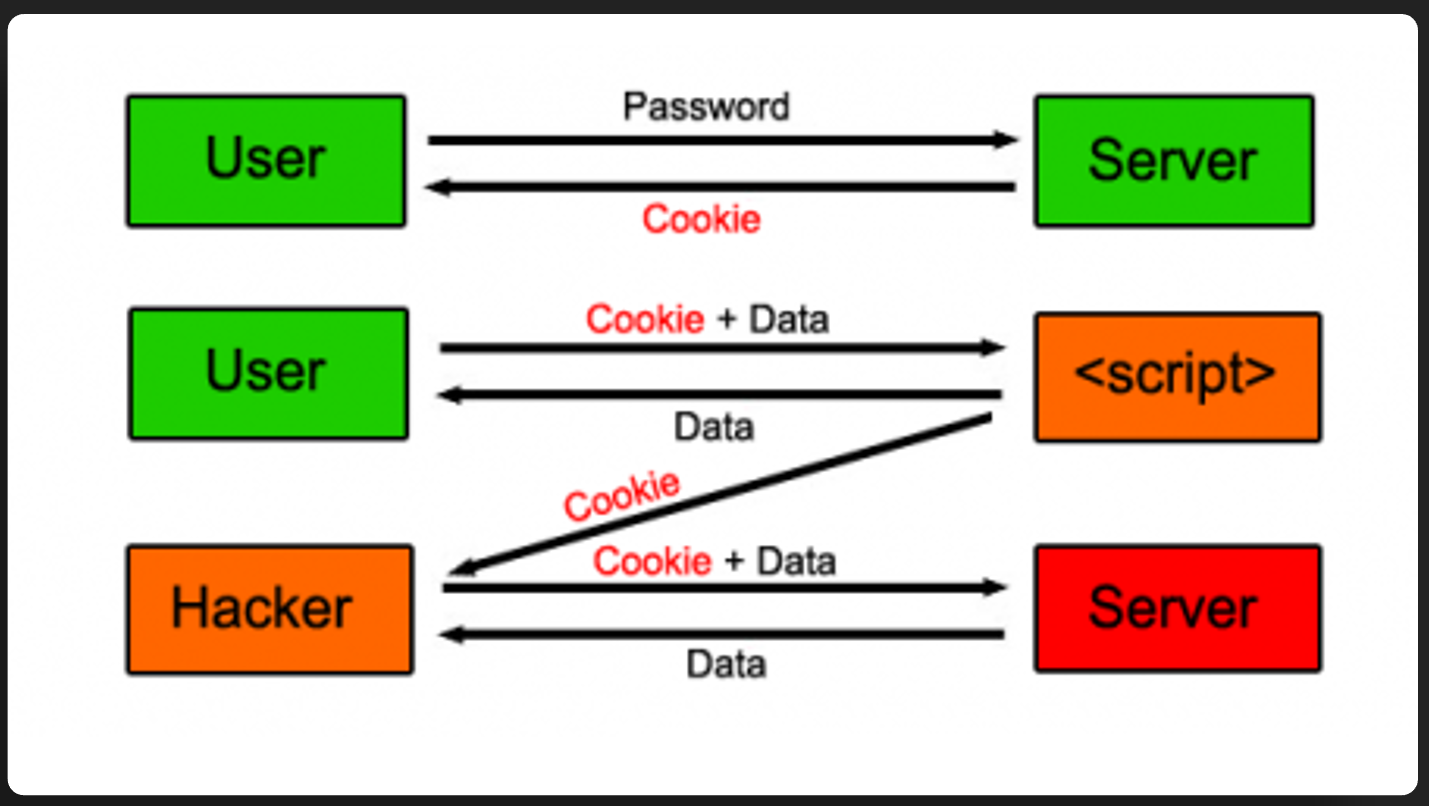
EX: XSS Defense
Filter and validate all user input before accepting it.
Encode and escape special characters as HTML.
Never trust user input or display raw submissions.
Problematic Characters
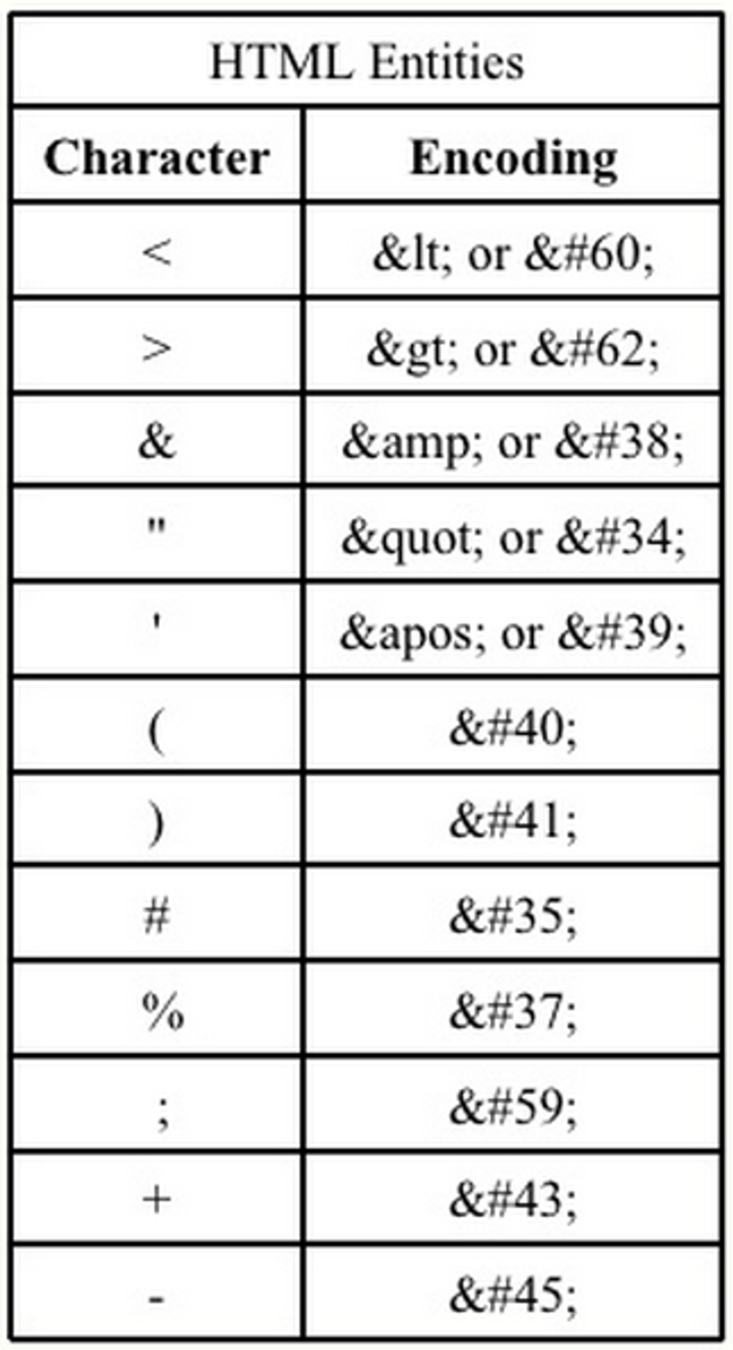
We will REturn to XSS and some of these other attack types
Part3: HTTP Review and INTRO TO RESTFUL APIS
We are doing it live
HAnds-ON Exercise
Take screenshots of successful GET and POST requests captured in POSTMAN
Submit screenshots to Canvas as Lab 1.
Questions?


Joshua Mcshannon
University of Nebraska at Omaha
Adjunct Professor, Cybersecurity
jmcshannon@unomaha.edu
slack: @jmcshannon
CYBR 8470 Introduction
By jmcshannon
CYBR 8470 Introduction
CYBR 8470 Introduction module
- 49



