Secure Web Application Development
Software Architecture and Design
Jmcshannon
Module Objectives
- Create a system architecture
- Use security viewpoints to assign security requirements to architectural elements
- Manage traceability of security requirements throughout the ssdlc
Part 0: Software Architectures
Vocabulary
Software Architectures - Analogous to a blueprint, a software architecture should communicate the connections between the elements of a system.
Components - A component is a functional grouping that handles some activity or certain logic.
Interface - An interface in this context is connection point between components
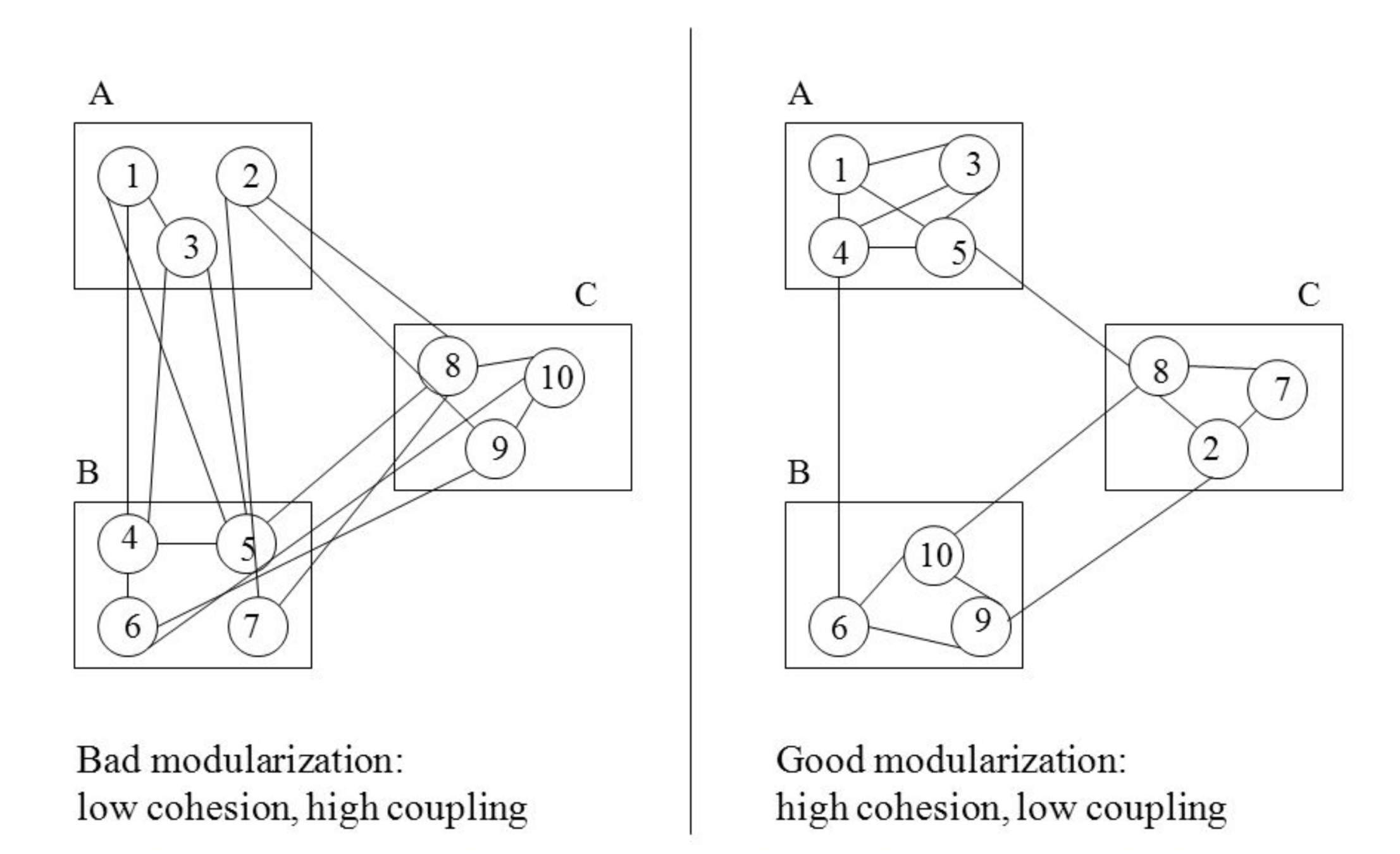
When designing software architectures a main point of focus is on cohesion and coupling.
https://vivadifferences.com/difference-between-coupling-and-cohesion-in-software-engineering-with-examples/
Part 1: Security Boundaries
What is a security boundary?
"The line of intersection between any two areas, subnets, or environments that have different security requirements or needs"
How are these boundaries expressed in software architecture?
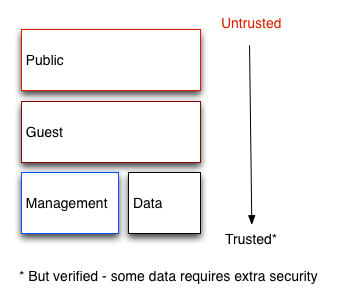
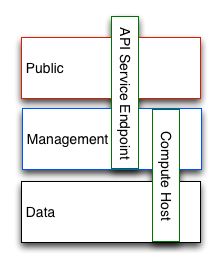
How are these boundaries expressed in software architecture?
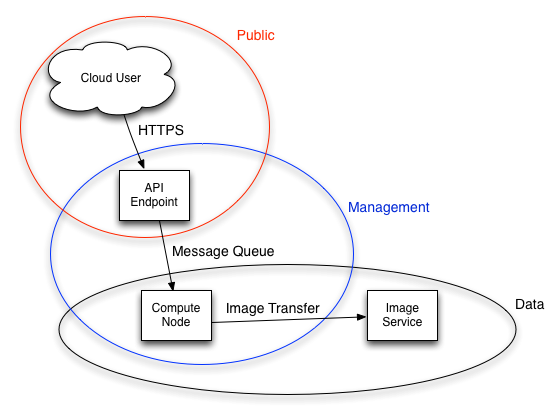
https://docs.openstack.org/security-guide/introduction/security-boundaries-and-threats.html
https://docs.openstack.org/security-guide/_images/bridging_domains_clouduser.png
C4 Modeling
- Context - The highest layer of abstraction depicts the software in its operating environment and shows how it interacts with users and external systems
- Container - Illustrates the high level technical building blocks that make up a system
- Component - Breaks down container views to show the individual components and their interactions with the container
- Code - Often optional, this describes the code classes/methods in the implementation
Why C4?
- Simplicity and Clarity
- Improved Comms
- Scalability
- Standardization
- Security Focus
How to make a C4 diagram?
- Identify the scope
- Select appropriate levels
- Maintain Consistency
- Iterative Refinement
Learn More https://c4model.com/
Part 2: Using MITRE Att&ck for Security Requirements
What is MITRE Att&ck?
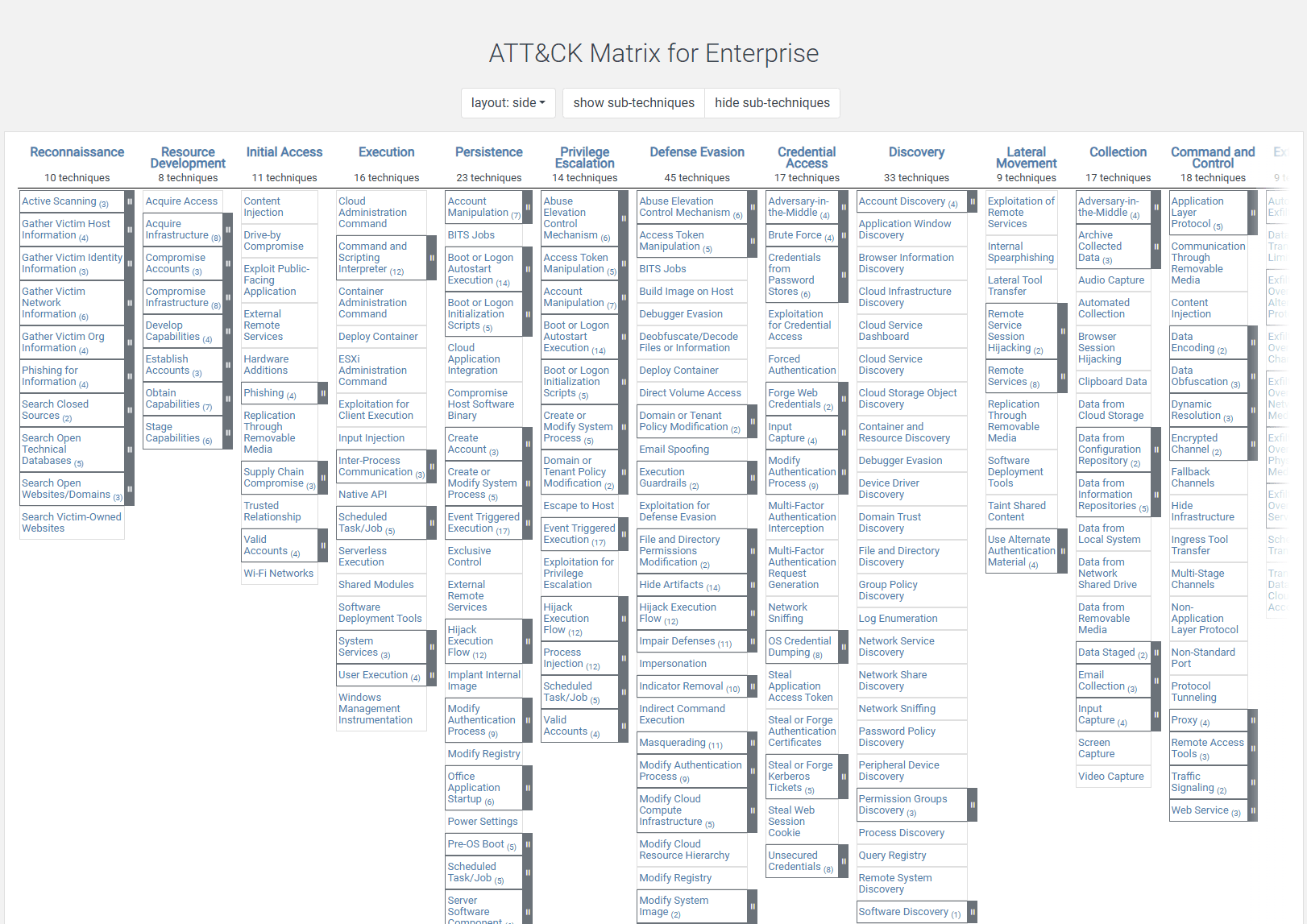
ATT&CK WITH C4
- Map Out the System Using C4 Diagrams
- Identify Critical Components
- Associate ATT&CK Techniques with Components
- Analyze Potential Attack Paths
- Use Mitigation Strategies
deck
By jmcshannon
deck
- 22



