SANS Institute’s Implementation of
Distributed Intrusion Detection System
(DIDS)
Arief Karfianto / 5296961
ISIT937 IT Security and Risk Management

Outline
Introduction
Research Method and Approach
Results
- Current prevalent types of attacks
- The origin of most of the attacks
- Current status of the Internet Storm Center
- FightBack Program
Conclusion
Introduction
National Computer Emergency Response Team of Australia's cyber security survey on major Australian industry in 2015*:
- 50% experienced
- 42% did not experience
- 8% were unsure
* Australian Cyber Security Center 2015, 2015 Cyber Security Survey: Major Australian Business,
Australian Cyber Security Center, Barton, viewed 26 March 2016,
<https://www.cert.gov.au/system/files/614/691/2015-ACSC-Cyber-Security-Survey-MajorAustralian-Businesses.pdf>.
Intrusion Detection System (IDS) is needed for detecting attacks before, during and after they occur.
Introduction (cont.)
Source: http://static.tenable.com/oldsite/blog/img/6a00d8345495f669e20163040fbac6970d
Intrusion detection is an activity of monitoring events in a computer system or network and then analyze the result (Whitman & Mattord 2013, p. 61).
Introduction (cont.)
Two approaches to IDS:
- Signature-based : recognizing specific known pattern
- Anomaly-based : define a baseline of normal behavior
Two basic IDS architecures:
- Host-based : e.g. buffer overflows and escalation of privilege
- Network-based : e.g. port scanning, denial of service, and request containing malformed packets
M Stamp, Information security. Wiley, Hoboken, N.J., 2011, pp. 294-296.
Introduction (cont.)
Distributed Intrusion Detection System (DIDS)
- Collect information from IDS in individual networks and intranets
-
Try to protect global information infrastructure
SANS Institute's DShield DIDS
- Started as a volunteer effort
- Provide an easy way to share attack information
- Focuses on people using a firewall as DIDS agent
- Upload raw logs from a firewall through a web form or client agent
- A report can be submitted by registered users or anonymously
Research Methods and Approach
- This report shows current trending cyber attacks globally.
- Literature review and secondary data collection are conducted.
- Literature and data source include government’s report, textbooks, white papers, and web articles.
- Data for the current prevalent types of attacks, the origin of most of the attacks and FightBack program are analyzed from DShield website (dshield.org).
- The status of current threat level is observed from SANS Institute’s Internet Storm Center (isc.sans.edu).
Results
Current Prevalent Types of Attacks
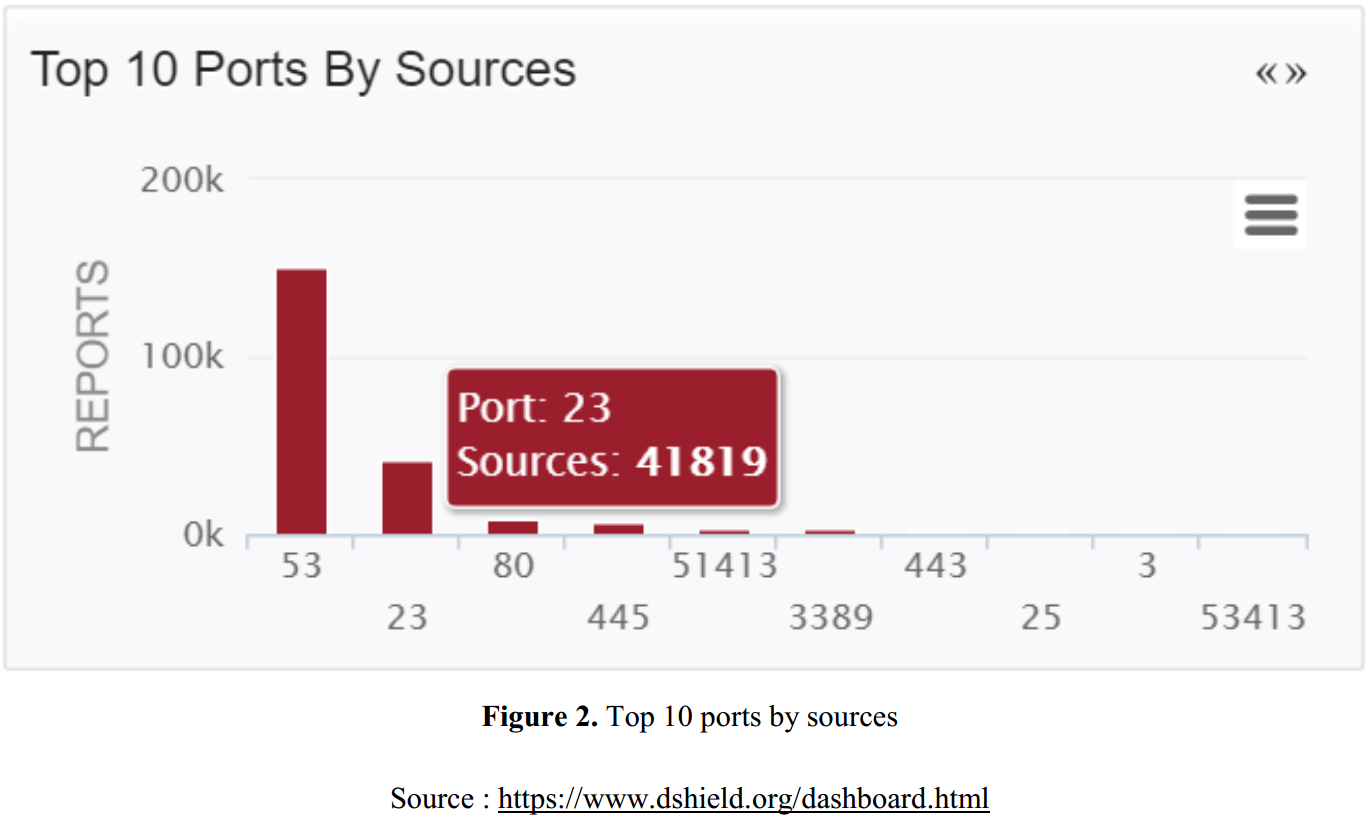
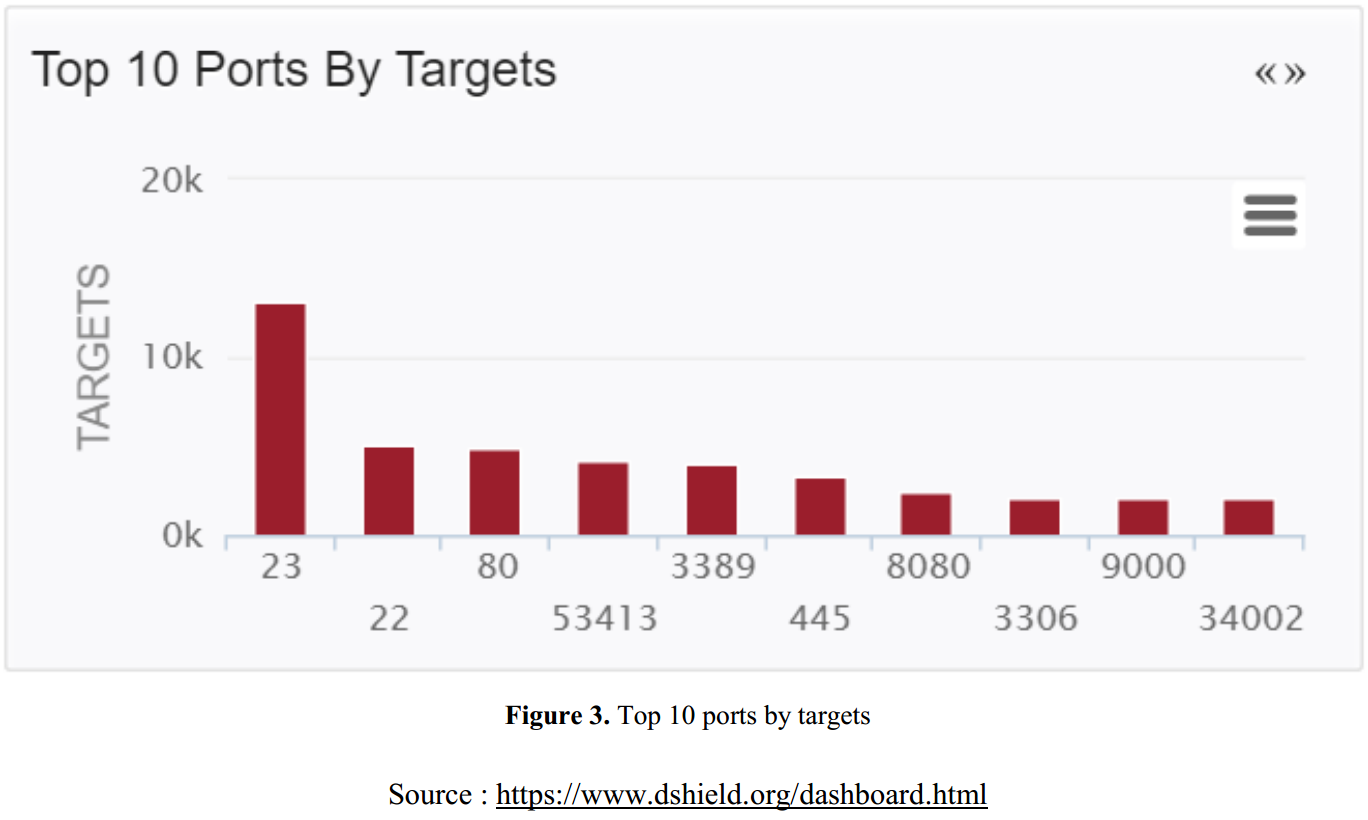
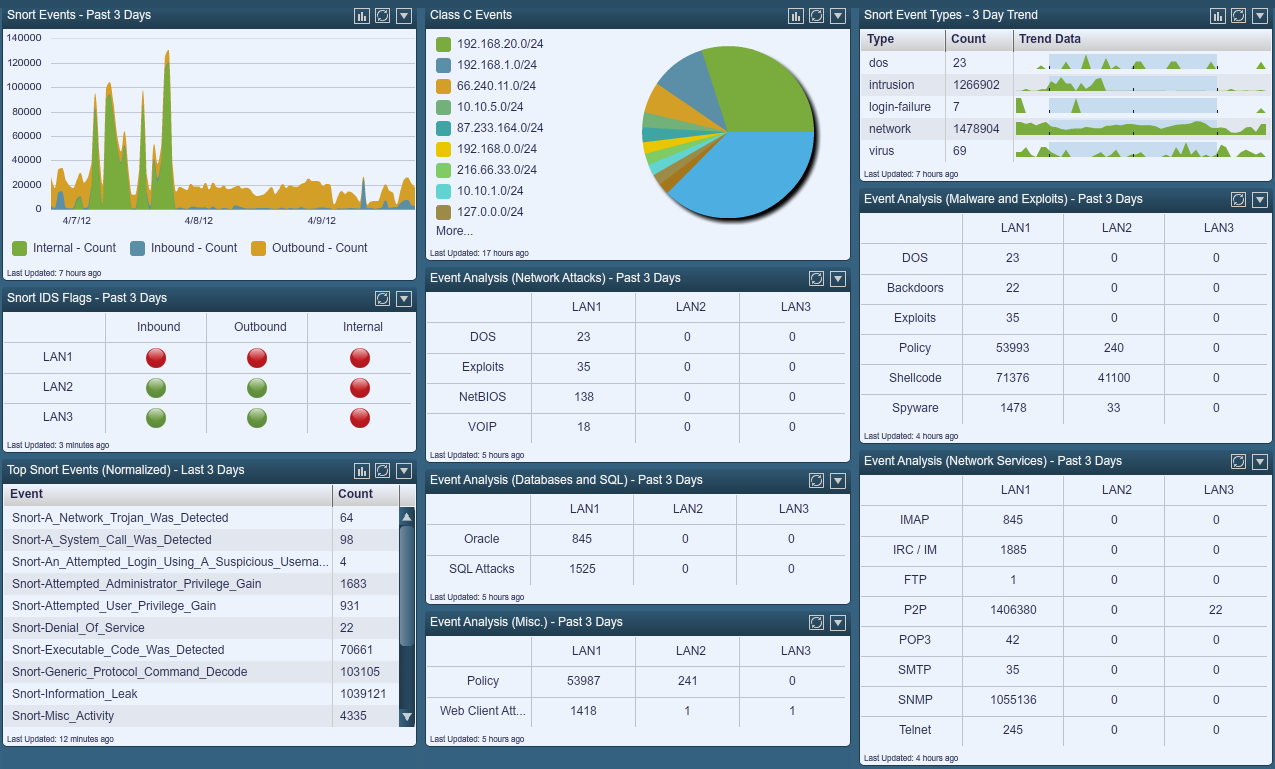
Current Prevalent Types of Attacks
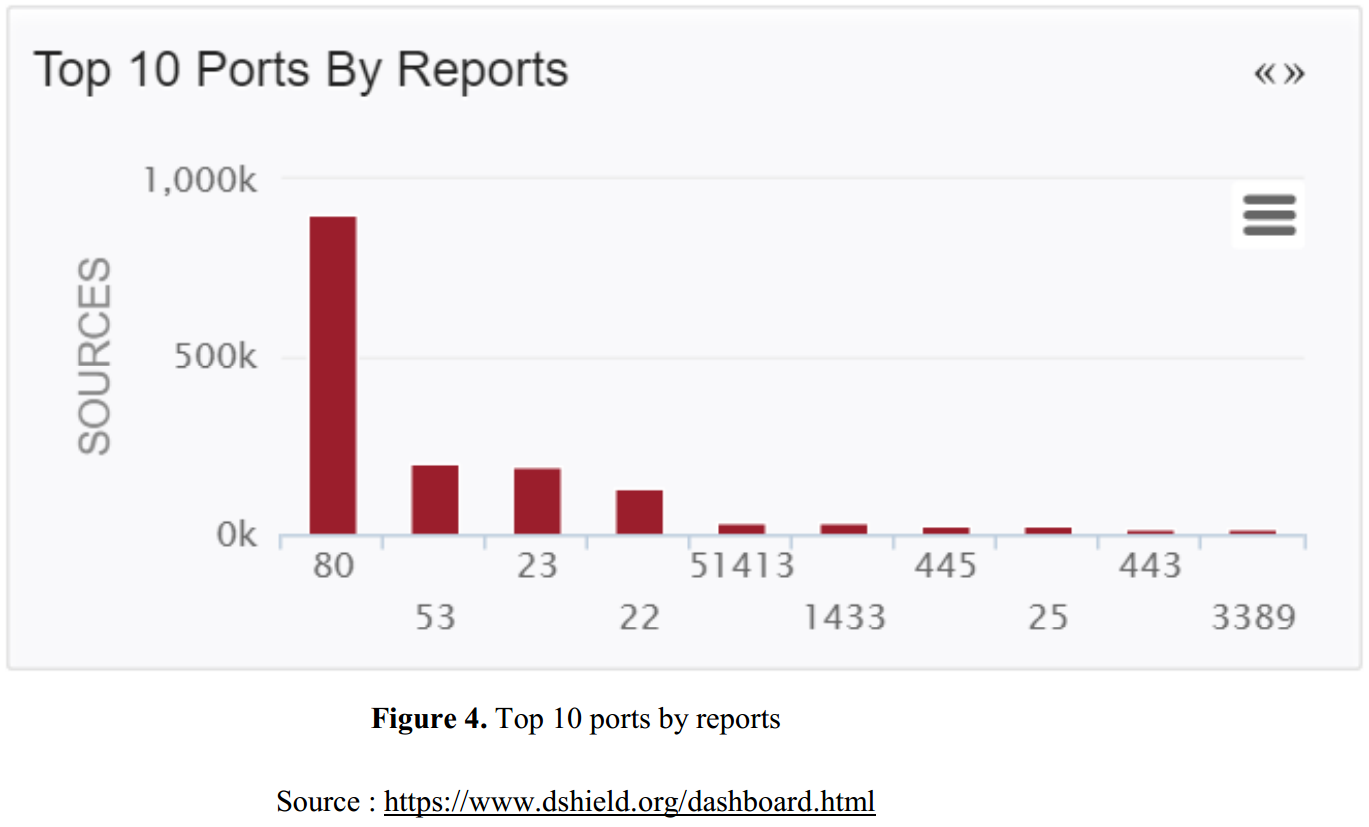
Current Prevalent Types of Attacks
The Origin of Most of the Attacks
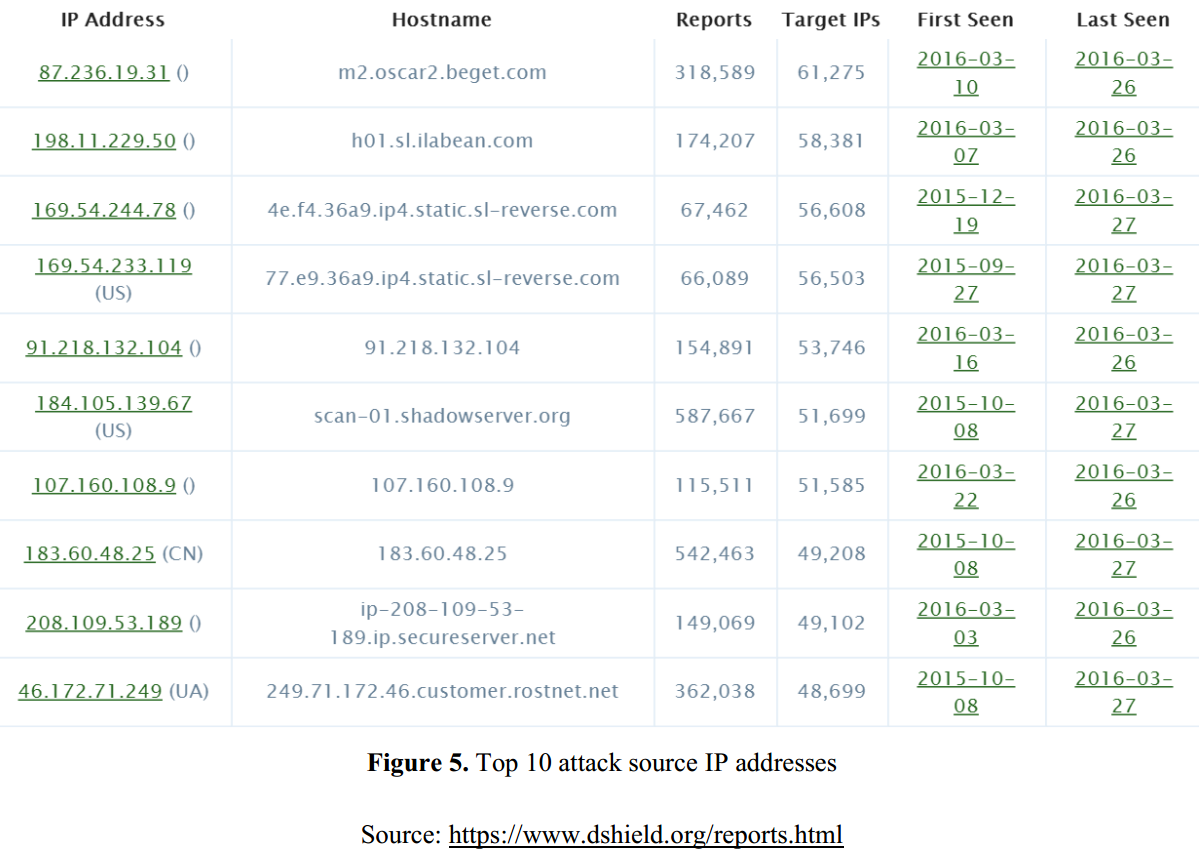
The Origin of Most of the Attacks
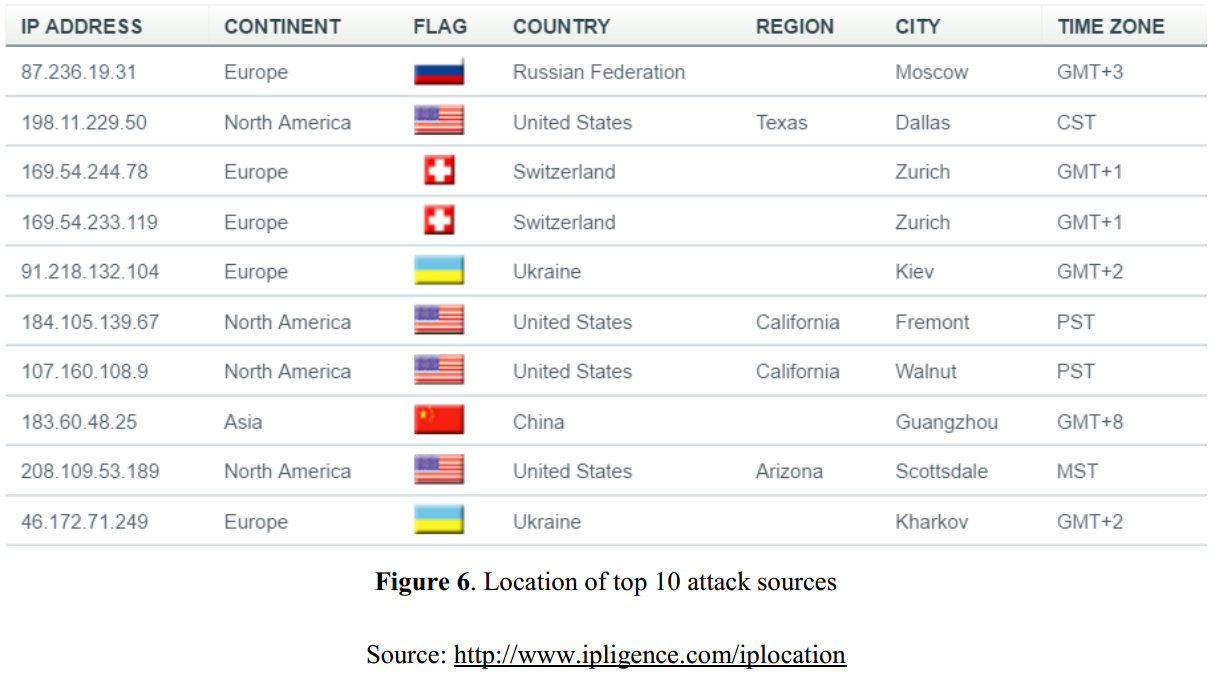
Current Status of the Internet Storm Center
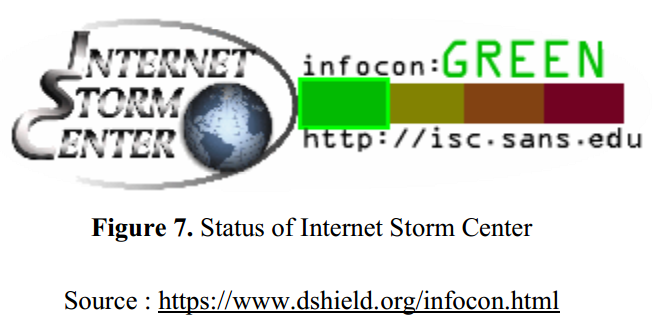
Everything is normal.
No significant new threat known.
FightBack Program
- Summarizes the analyses of attacks and sends them to the responsible ISP
- ISPs can perform immediate actions to help protecting client’s infrastructure from attacks
- The ISP only receive information submitted by registered users
- Users will receive any correspondence copy
- Notifications about attacking host are sent to ISPs automatically
- It does not have mechanism for users to track ISP response or escalation
Conclusions
- Detection of cyber attack is important to be able to take immediate action to response the incident.
- At the time, the most attacked ports by sources are 53, 23, and 80.
- The most attacked ports by targets are 23, 22, and 80.
- The most targeted services reported to DShield are port 80, 23, and 22.
- That most of recent attacks are originated from Russia, the US, Switzerland, Ukraine, and China.
- ISC shows that the current threat level is green.
-
FightBack program sends information of attacks to the responsible ISP for better anticipation and mitigation of attacks.
Thank You
References:
Australian Cyber Security Center 2015, 2015 Cyber Security Survey: Major Australian Business,
Australian Cyber Security Center, Barton, viewed 26 March 2016,
<https://www.cert.gov.au/system/files/614/691/2015-ACSC-Cyber-Security-Survey-MajorAustralian-Businesses.pdf>.
Bulk IP lookup locator - Enter IP Addresses to find their IP Location 2016, Ipligence.com , viewed 27 March 2016, <http://www.ipligence.com/iplocation>.
Distributed Intrusion Detection Systems: An Introduction and Review 2002, SANS Institute, viewed 26 March 2016, <https://www.sans.org/readingroom/whitepapers/detection/distributed-intrusion-detection-systems-introductionreview-897>.
FightBack Program 2016, SANS Institute, viewed 27 March 2016, <https://www.dshield.org/fightback.html>.
Infocon Internet Security 2016, SANS Institute, viewed 27 March 2016, <https://www.dshield.org/infocon.html>.
Internet Storm Center 2016, SANS Institute, viewed 27 March 2016, <https://isc.sans.edu/>.
SANS Institute: About 2016, SANS Institute, viewed 26 March 2016, <https://www.sans.org/about>. Scarfone, K & Mell, P 2010, ‘Intrusion Detection and Prevention Systems’, in P Stavroulakis, & M Stamp (ed.), Handbook of Information and Communication Security, Springer, Leipzig.
Service Name and Transport Protocol Port Number Registry 2016, Internet Assigned Number Authority, viewed 27 March 2016, <http://www.iana.org/assignments/service-names-port-numbers/service-names-portnumbers.xhtml>.
Stamp, M 2011, Information Security, Wiley, Hoboken.
TCP/UDP Port Activity - SANS Internet Storm Center 2016, SANS Internet Storm Center, viewed 27 March 2016, <https://isc.sans.edu/port.html?port=51413>.
Whitman, M & Mattord, H 2013, Management of information security, Cengage Learning, Stamford.
Distributed IDS by Arief Karfianto
By Arief Karfianto
Distributed IDS by Arief Karfianto
Presentation by Arief Karfianto
- 1,586



