Left Shift
Cybersecurity


Kevin Wittek
Technical Lead @ GDATA Advanced Analytics
Freelancer @ Styracosoft GbR
https://groovy-coder.com/
@Kiview
https://github.com/kiview




Karsten Tellmann



Classic Development Pipeline

Excursion: Pentesting
- Usually part of a quality gateway
- Often missplaced in the classical development process:
- Too early => Nothing productiv to test
- Too late => Critical findings threaten release date
- What is the motivation for a pentest?
Motivation
- Integrate security into fast DevOps cycles
- Find low hanging fruits by automated tools
- Use pentests for more complex issues
- Security awareness in developer context
Modern build pipeline

| Stage | Available Artifacts |
|---|---|
| Build | Source Code Byte Code Dependencies |
| Docker build | Container Image |
| Staging / Production | Container Image Configured Environment |
Modern build pipeline

Dependency Check


Demo
Exkurs: CVE, CPE, GAV
- CVE: Common Vulnerabilities and Exposures
- CPE: Common Platform Enumeration
- GAV: Maven Group:Artifact:Version
Exkurs: CVE, CPE, GAV
<entry id="CVE-2012-5055">
...
<vuln:vulnerable-software-list>
<vuln:product>cpe:/a:vmware:springsource_spring_security:3.1.2</vuln:product>
<vuln:product>cpe:/a:vmware:springsource_spring_security:2.0.4</vuln:product>
<vuln:product>cpe:/a:vmware:springsource_spring_security:3.0.1</vuln:product>
</vuln:vulnerable-software-list>
...
</entry>cpe:/[Entry Type]:[Vendor]:[Product]:[Version]:[Revision]:…
<!-- org.springframework.security:spring-security-core:3.0.1.RELEASE -->
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-core</artifactId>
<version>3.0.1.RELEASE</version>
</dependency>
Patton
https://github.com/BBVA/patton-server

POST /api/v1/check-dependencies/ HTTP/1.1
Host: patton.owaspmadrid.org
Content-Type: application/json
{
"method": "auto",
"source": "auto",
"libraries" : [
{
"library": "django",
"version": "1.2"
},
{
"library": "postgres",
"version": "8"
}
]
}HTTP/1.1 200 OK
Vary: Accept
Content-Type: application/json
{
"django:1.2": {
"cpes": [
"cpe:/a:djangoproject:django:1.2.1",
"cpe:/a:djangoproject:django:1.2.4",
"cpe:/a:djangoproject:django:1.2.3",
"cpe:/a:djangoproject:django:1.2",
"cpe:/a:djangoproject:django:1.2.2",
"cpe:/a:djangoproject:django:1.2.6",
"cpe:/a:djangoproject:django:1.2.2",
"cpe:/a:djangoproject:django:1.2.3",
"cpe:/a:djangoproject:django:1.2.4",
"cpe:/a:djangoproject:django:1.2.4"
],
"cves": [
{
"cve": "CVE-2011-0698",
"score": 7.5
},
{
"cve": "CVE-2011-0698",
"score": 7.5
},
{
"cve": "CVE-2011-0698",
"score": 7.5
},
{
"cve": "CVE-2011-0698",
"score": 7.5
}
]
},
"postgres:8": {
"cpes": [
"cpe:/a:postgresql:postgresql:8.4.15",
"cpe:/a:postgresql:postgresql:8.3.12",
"cpe:/a:postgresql:postgresql:8.4.13",
"cpe:/a:postgresql:postgresql:8.3",
"cpe:/a:postgresql:postgresql:8.3.4",
"cpe:/a:postgresql:postgresql:8.3",
"cpe:/a:postgresql:postgresql:8.3.4",
"cpe:/a:postgresql:postgresql:8.4.3"
],
"cves": [
{
"cve": "CVE-2013-1902",
"score": 10
},
{
"cve": "CVE-2013-1903",
"score": 10
},
{
"cve": "CVE-2013-1903",
"score": 10
}
]
}
}Static Code Analyis



https://www.veracode.com/
https://www.checkmarx.com/
https://find-sec-bugs.github.io/

Demo

Image scanning

http://layeredinsight.com/
https://github.com/coreos/clair/
https://docs.docker.com/docker-cloud/builds/image-scan/



Dynamic Scanner

http://www.zaproxy.org/
https://portswigger.net/burp
http://www.arachni-scanner.com/


ZAP + Docker/testcontainers

Excursion: OWASP Top 10
- A1:2017-Injection (SQLi, ...)
- A7:2017-Cross-Site Scripting (XSS)
- Persistent XSS
- (Reflected, DOM based, Mutation based)
https://www.owasp.org/index.php/Category:OWASP_Top_Ten_2017_Project
Demo
Gitlab-CI
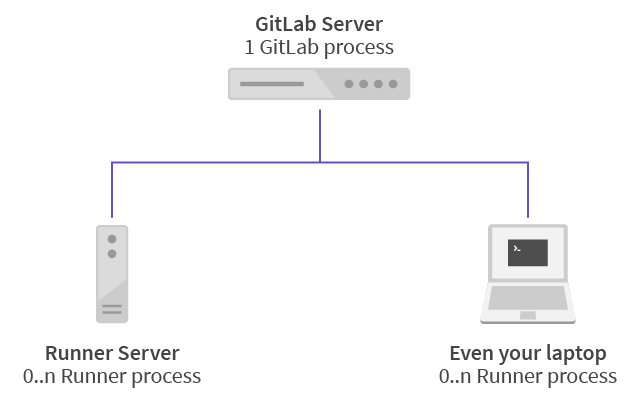
Security Features
- Container Scanning
- Dependency Scanning
- Static Application Security Testing
- Dynamic Application Security Testing
- OWASP ZAP
- Kubernetes Deployment
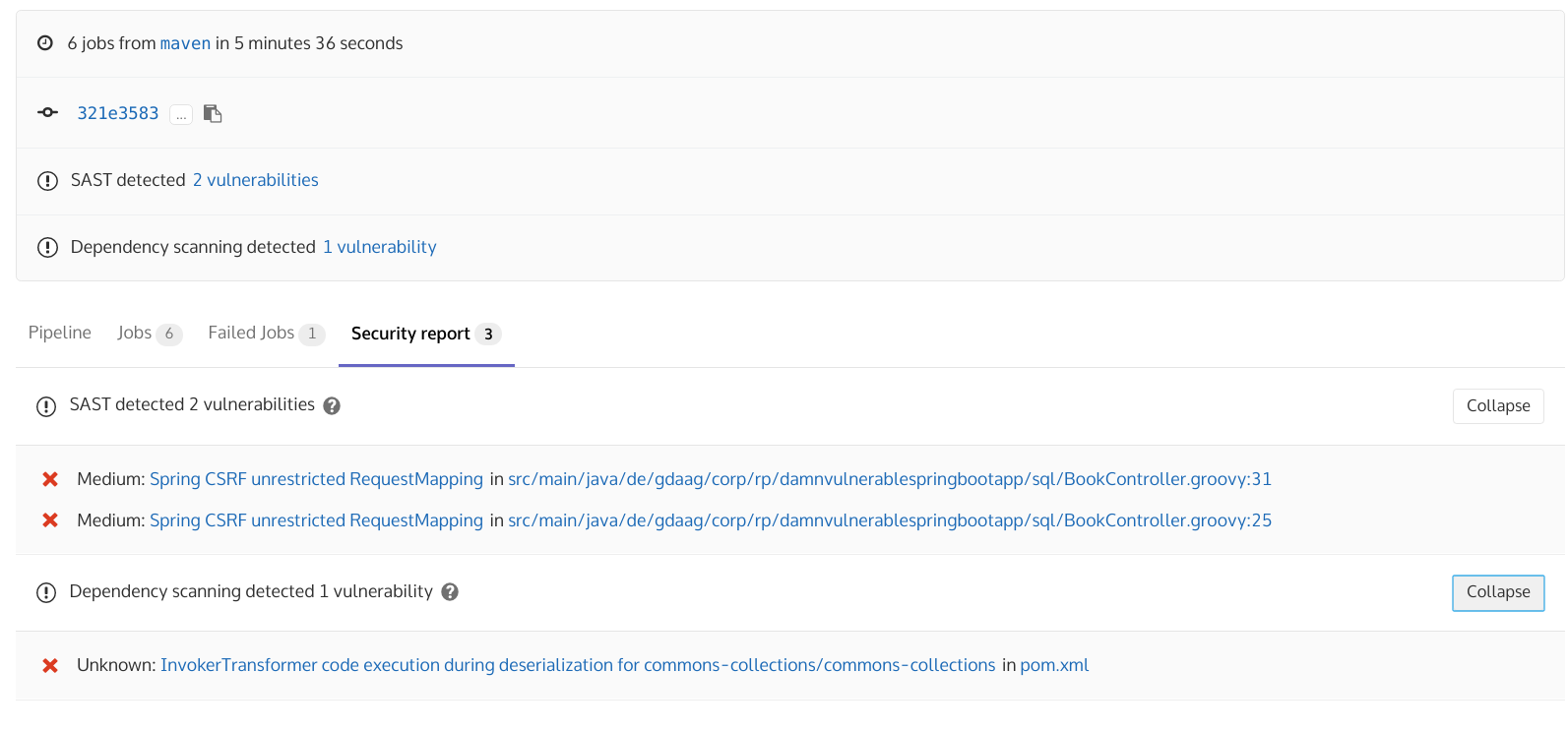
Code checks
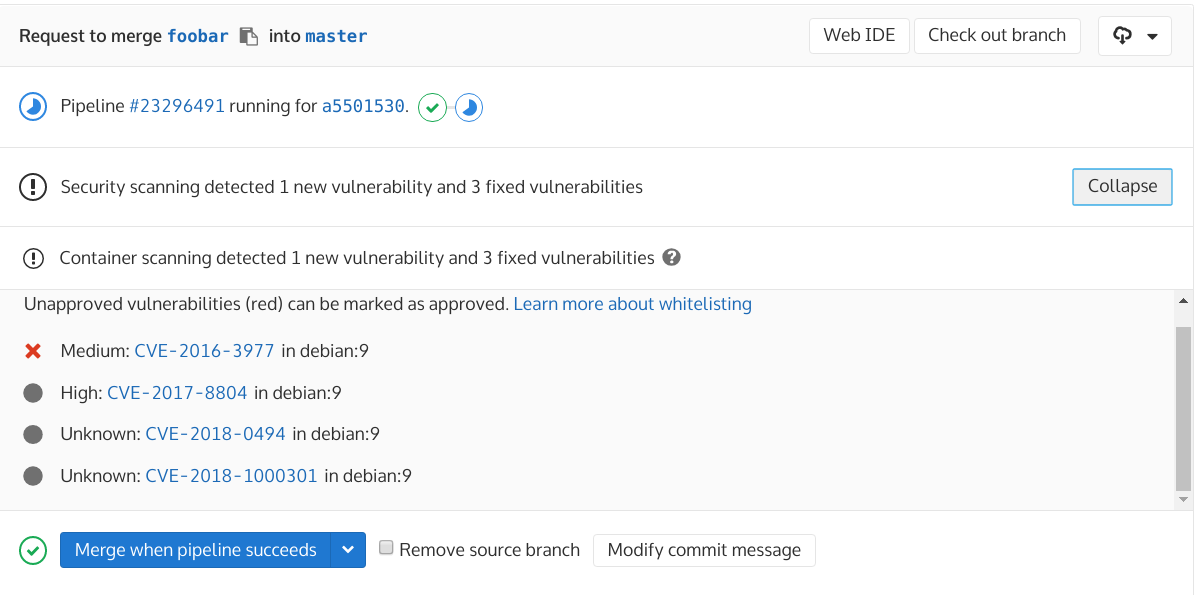
Container Scanning
Conclusion
- Integration into build chain possible
- Security insights for developers
- Possible without security experts
- Open Source tools can only provide a small security benefit
- Commercial products not evaluated
Outlook
- Increase security awareness inside developer community
- Security and developer communities need to work together:
- Shared goal: Better software
- Shared language would help
- CD Security is needed
Source: https://twitter.com/signalsciences/status/647533893617238016

Questions?
Left Shift Cybersecurity (v2)
By Kevin Wittek
Left Shift Cybersecurity (v2)
- 2,678



