Traefik behind the Firewall
Kevin Wittek
Software Developer @ GDATA Advanced Analytics
Freelancer @ Styracosoft GbR
http://groovy-coder.com/
@Kiview
https://github.com/kiview




Constraints in an Enterprise
- Certificates signed by company CA
- No wildcard certificates (not even subdomain)
- Secrets need to be secure (private key)
- Internal services not reachable via Internet

Infrastructure as Code

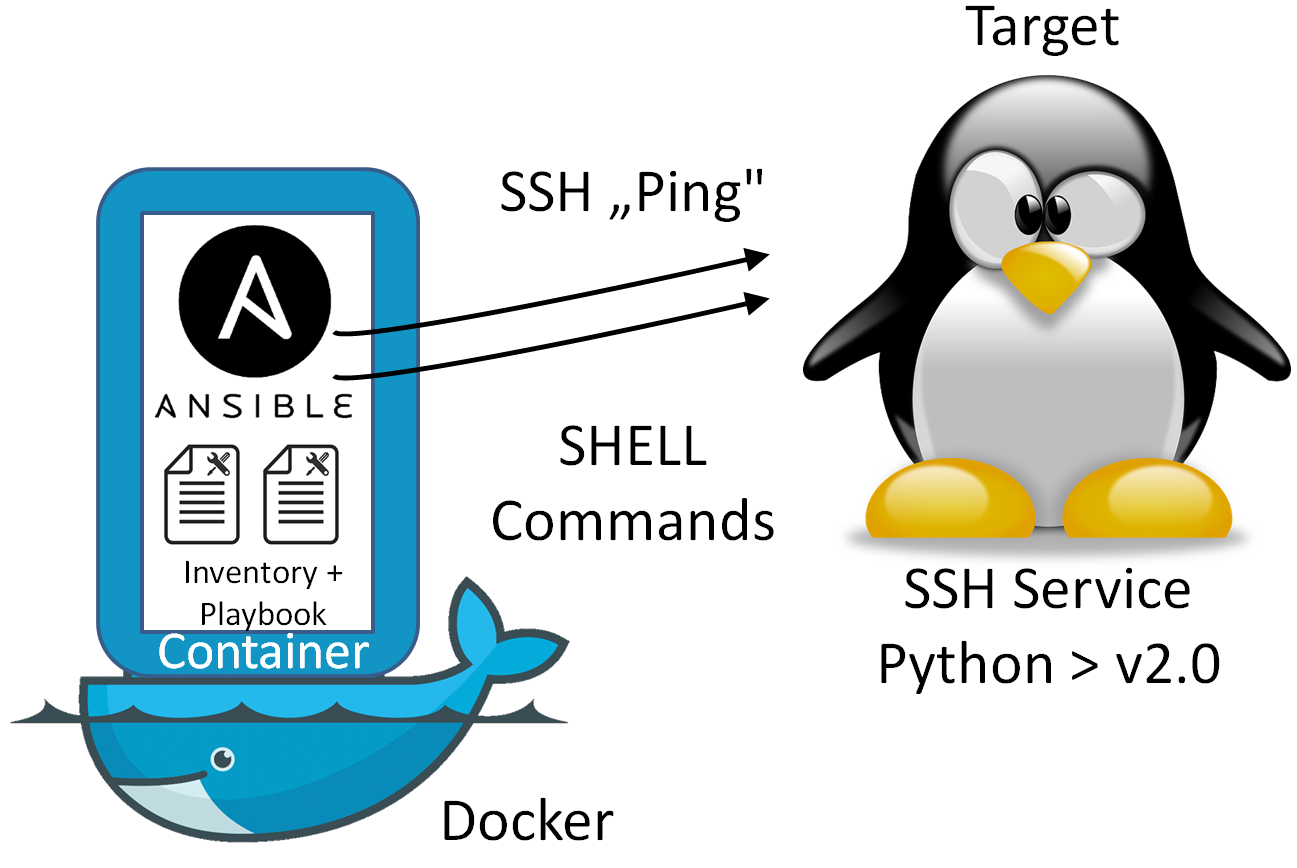
Text
source: https://oliverveits.wordpress.com/2015/11/09/it-automation-a-hello-world-example-using-ansible-on-docker/
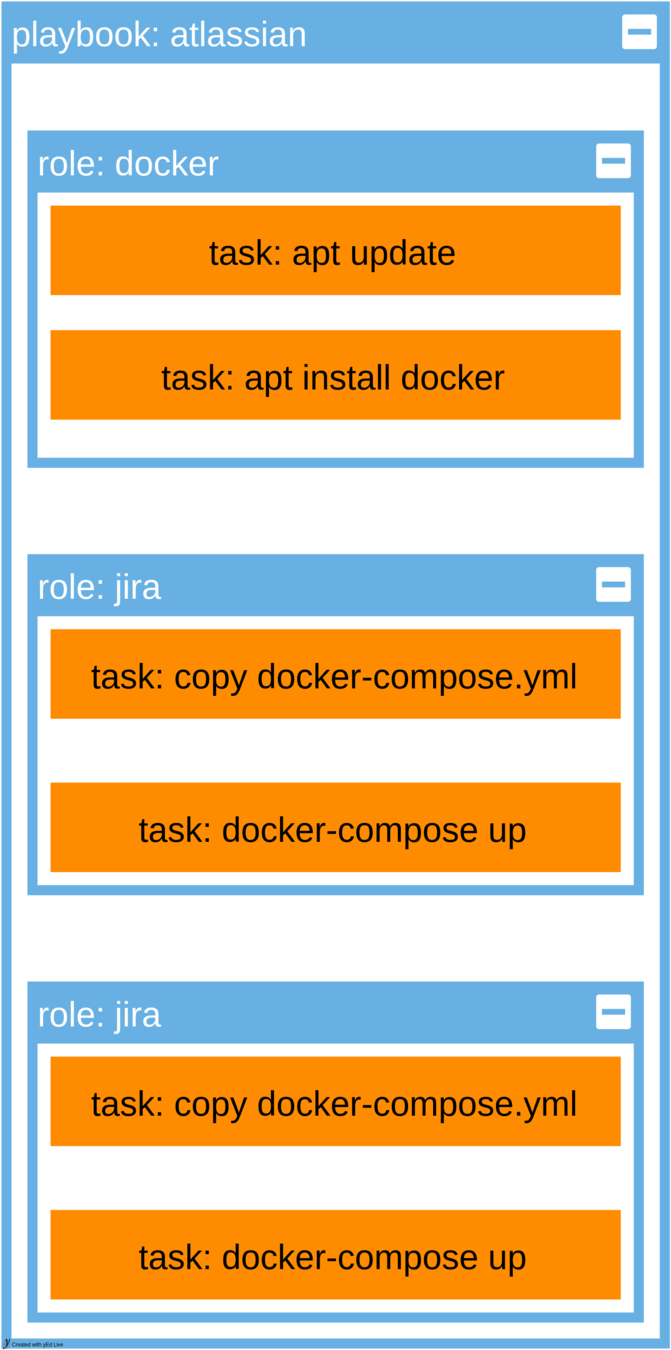
Traefik compose
version: '2'
services:
traefik:
image: traefik:v1.0.3
restart: always
ports:
- "443:443"
- "8080:8080"
volumes:
- ./traefik.toml:/etc/traefik/traefik.toml
- ./certs:/etc/traefik/certs/
- /var/run/docker.sock:/var/run/docker.sockTraefik role (tasks)
---
# tasks file for traefik
- name: create project directory
file: path=/docker/traefik state=directory
- name: copy docker-compose to host
copy: src=docker-compose.yml dest=/docker/traefik
- name: copy toml template
template: src=traefik.toml.j2 dest=/docker/traefik/traefik.toml
- name: create cert directory
file: path=/docker/traefik/certs state=directory
- name: Copy certs
copy: src={{ item }} dest=/docker/traefik/certs
with_fileglob:
- "{{ playbook_dir }}/*.crt"
- name: Write SSL keys
copy: content={{ item.ssl_key }} dest="/docker/traefik/certs/{{ item.name }}.key"
no_log: True
with_items: "{{ domains }}"
- name: start traefik
docker_service:
project_src: /docker/traefik
state: present
restarted: yesTraefik config (SSL SNI)
# To redirect an http entrypoint to an https entrypoint (with SNI support):
[entryPoints]
[entryPoints.http]
address = ":80"
[entryPoints.http.redirect]
entryPoint = "https"
[entryPoints.https]
address = ":443"
[entryPoints.https.tls]
[[entryPoints.https.tls.certificates]]
CertFile = "integration/fixtures/https/snitest.com.cert"
KeyFile = "integration/fixtures/https/snitest.com.key"
[[entryPoints.https.tls.certificates]]
CertFile = "integration/fixtures/https/snitest.org.cert"
KeyFile = "integration/fixtures/https/snitest.org.key"Traefik role (template)
[entryPoints]
[entryPoints.https]
address = ":443"
[entryPoints.https.tls]
{% for domain in domains %}
[[entryPoints.https.tls.certificates]]
certFile = "/etc/traefik/certs/{{domain.name}}.crt"
keyFile = "/etc/traefik/certs/{{domain.name}}.key"
{% endfor %}
Playbook
---
- hosts: ubuntu.hyperv.de
become: true
pre_tasks:
- include_vars: ssl_keys.yml
roles:
- role: traefik
domain_name: "{{ ansible_host }}"
tags:
- traefik
domains:
- {name: confluence.ubuntu.hyperv.de, ssl_key: "{{confluence_key}}"}
- {name: jira.ubuntu.hyperv.de, ssl_key: "{{jira_key}}"}
- role: jira
domain_name: "{{ ansible_host }}"
- role: confluence
domain_name: "{{ ansible_host }}"
tags:
- confluenceSecrets
- Ansible Vault
- Hashicorp Vault
- Square KeyWhiz

ansible-vault encrypt ssl_keys.yml
ansible-playbook site.yml --ask-vault-passDemo?
Traefik behind the Firewall
By Kevin Wittek
Traefik behind the Firewall
- 3,696



