Behind the curtain: Oblivious Transfer
Lyubomir Filipov @FilipovG

Who am I
Lyubomir Filipov
Team Lead
Enthusiast

Oblivious transfer
cryptographic primitive
1-out-of-2 OT: Alice chooses as input two bits b0 and b1. Bob chooses a selection bit c and gets as output the bit bc.
Bananas in Pyjamas

Oblivious transfer
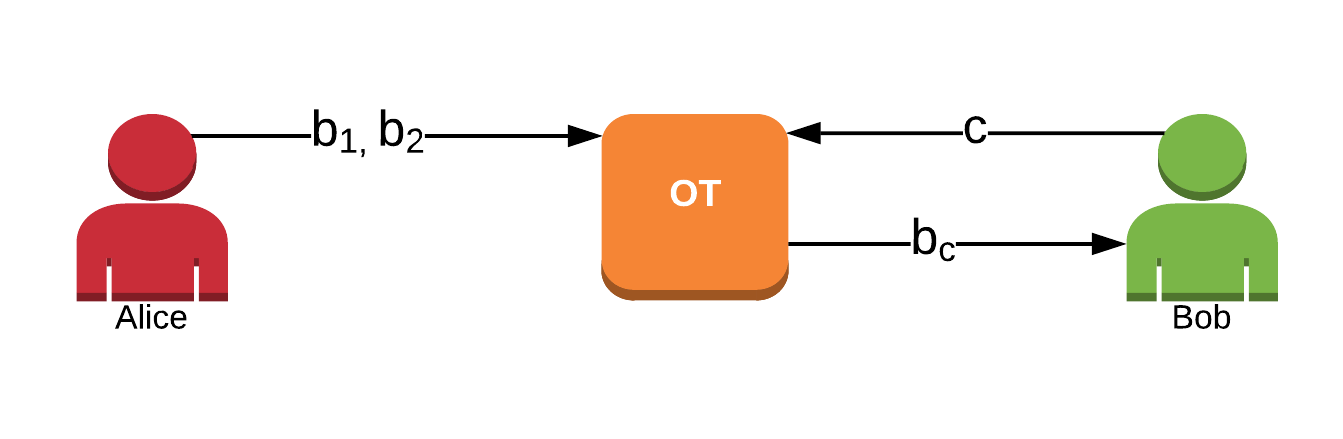
Alice should not learn c
Bob should not learn b1-c
Alice

Bob

Oblivious transfer

Only one item is returned to Bob.
Alice won't know what Bob has in his mind!
Oblivious transfer

Biometric data
personal data resulting from specific technical processing relating to the physical, physiological or behavioural characteristics of a natural person, which allow or confirm the unique identification of that natural person.
Biometric data

Fingerprint scanning

Iris recognition

Biometric data
Not 100% perfect
Every scan will return different results

Data representation

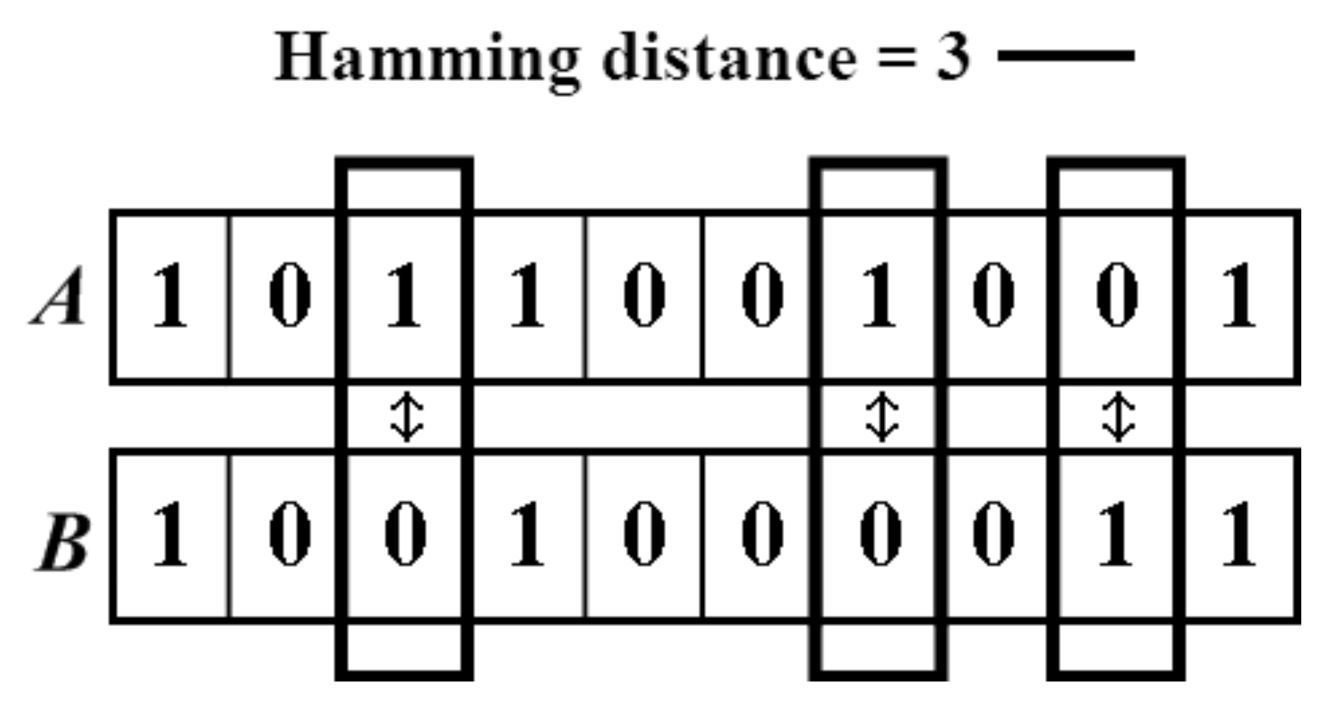
Hamming distance
Privacy-preserving biometric identification
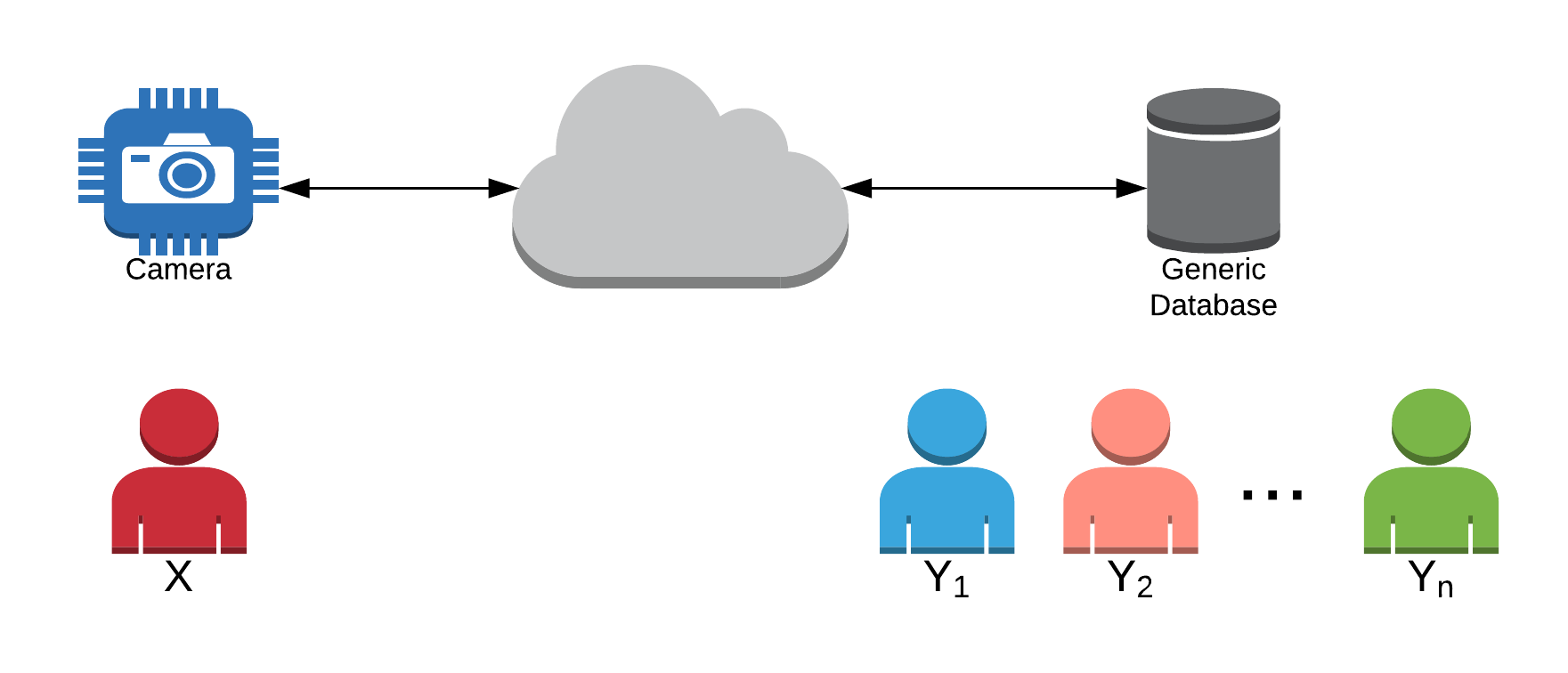

- Anonymous Biometric access Control
- Biometric Anonymous Credentials
- Secure Biometric Database Intersection
Biometric identification

SHADE protocol

SHADE protocol
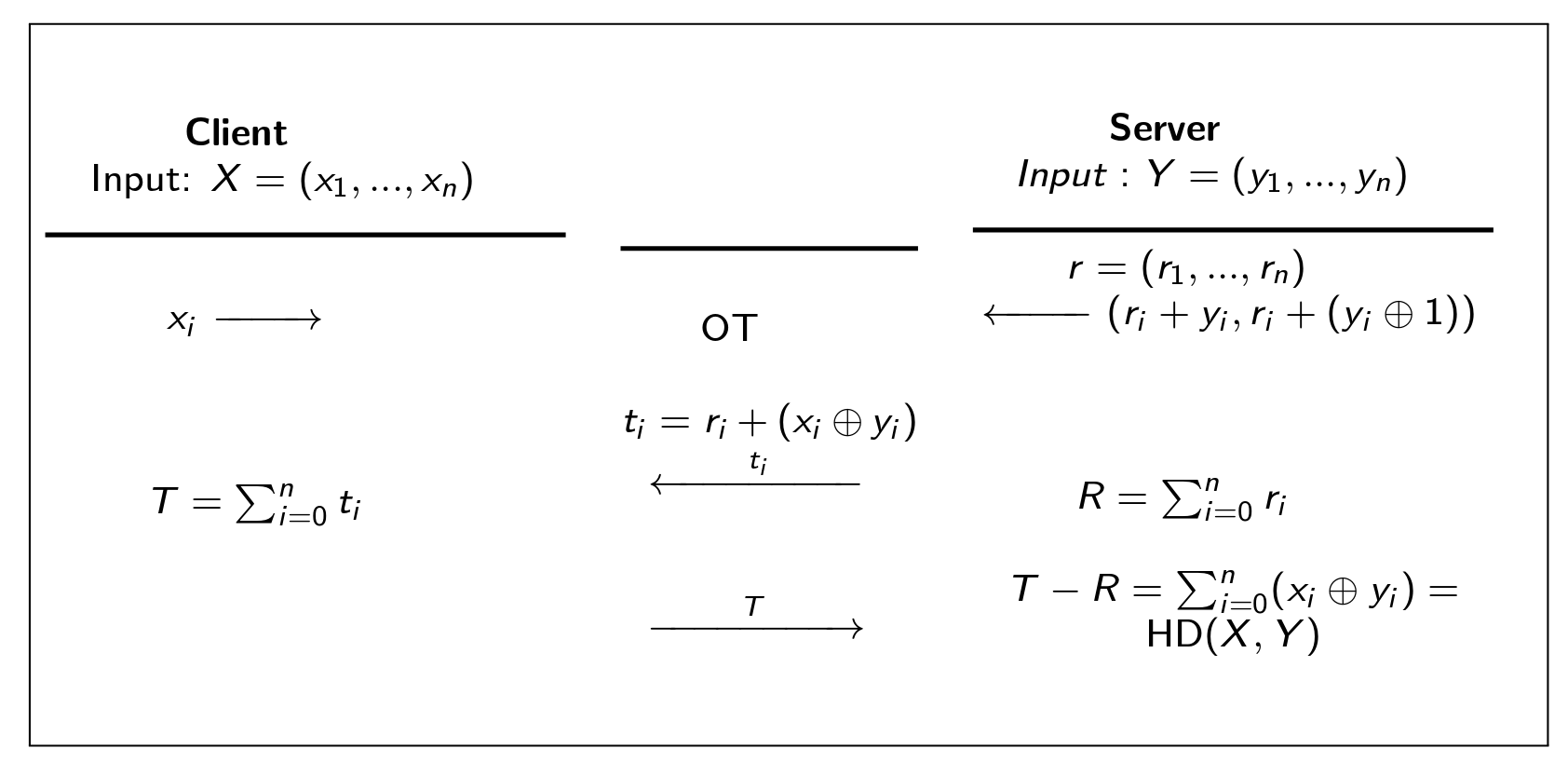
SHADE protocol
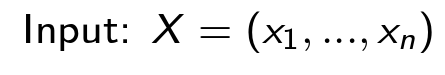
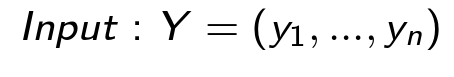


SHADE protocol

| X | Y | X XOR Y |
|---|---|---|
| 0 | 0 | 0 |
| 1 | 0 | 1 |
| 0 | 1 | 1 |
| 1 | 1 | 0 |

SHADE protocol

SHADE protocol
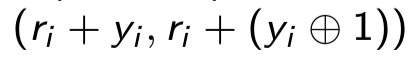

SHADE protocol

SHADE protocol
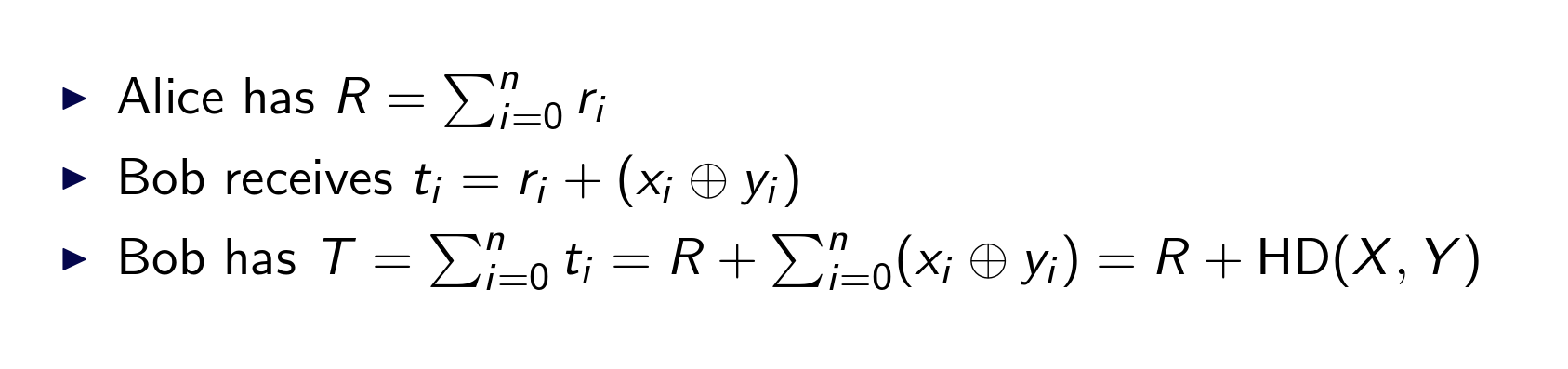

SHADE protocol

Where it could be applied
- Dating app where you only want to receive messages from one user.
- IoT devices that send sensitive data.
But, wait

To be aware of
- All this comes as extra traffic
- It could not be extended easily
Questions?

Behind the curtain: Oblivious Transfer
By Lyubomir Filipov
Behind the curtain: Oblivious Transfer
- 1,635



