This class, web app basics, and Github
Secure Web Application Development
Dr. Hale
University of Nebraska at Omaha
CYBR 8470 - Lecture 1
Welcome to CYBR8470
What is this class?
We will be making stuff. Its not for the faint of heart, but trust me it will be awesome and you will feel great when you create something new.
Why should you trust me?
I've made a lot of web apps - its kind of my thing. Also the previous three years student cohorts enjoyed the class.
Ok great, what will we cover?




Ok, So what will we cover?
- Web Services, RESTful APIs, and SOA
- Software Engineering: Architecting and design
- Software project management and Team dynamics
- Client-side application development
- Server-side API Creation
- Application Pen Testing
- Hardening and secure coding in the SDLC
Syllabus Time


Today: Not Just the Syllabus
Icebreaker
Part 1: Class Overview
Part 2: Web Apps 101
Part 3: HTTP Review and RESTful APIs
Icebreaker
The Cup-stack Challenge


Ok, so what did we learn here?
- Stacking cups is hard
- Teamwork is a give and take
- Collective vision is essential for success
- Building software in a team isn't all that different - each of you have different visions and try to make those visions a reality. It only works when everyone learns what their pull is.
- Pull requests puns are a real thing.
- Dr. Hale loves puns and will continue to use them unashamedly
Part1: Class Overview
GITHUB - Learn it and Love it
Class Repo: https://github.com/mlhale/CYBR8470
Slick version: mlhale.github.io/CYBR8470
We Will be using it a lot
Canvas - For Grades
Slack
Part2: Web Apps 101

(nearly) All companies have a web app
You probably use them, daily.
As a user, you expect web apps to be:
fast, responsive, always available, and secure
Despite your expectations:
96% of web apps have vulnerabilities*
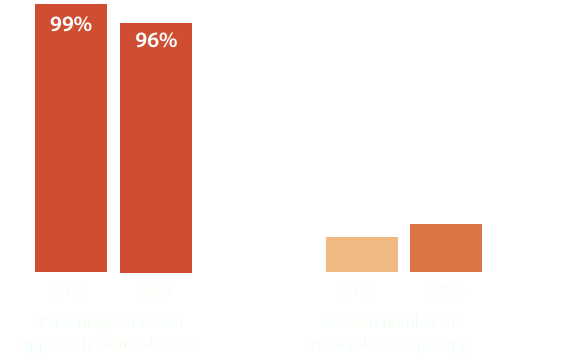
Cenzic Application Vulnerability Trends report, 2014
*...at the application Level!
* Cenzic Application Vulnerability Trends report, 2014
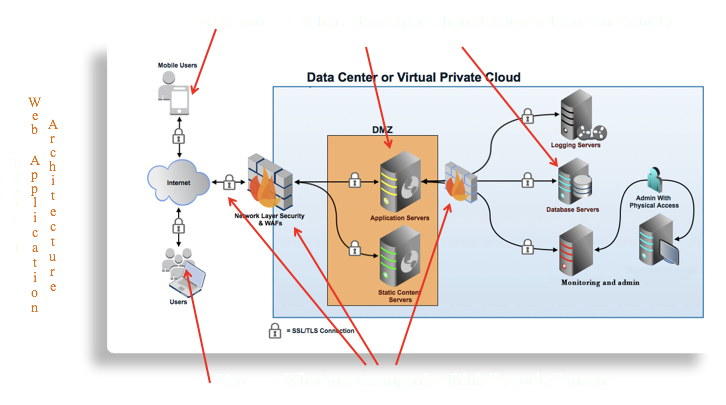
Basic Web App attack Principle
...make the web application do something it was never intended to do.
aka...user input is evil.
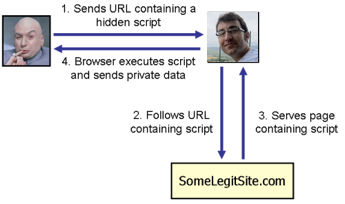
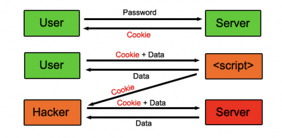
EX: XSS
Allows attackers to inject malicious scripts into web pages and have it executed in another user’s browser. Usually to capture some user information.
EX: XSS Defense
- Filter and validate all user input before accepting it.
- Encode and escape special characters as HTML.
- Never trust user input or display raw submissions.
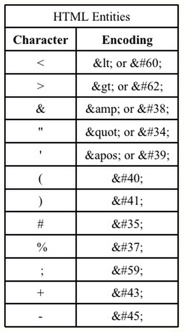
Problematic Characters
We will REturn to XSS
Part3: HTTP and REST Overview
Hands-on lesson: https://mlhale.github.io/CYBR8470/modules/restful-api/
Questions?
© 2014-2017 Matthew L. Hale or as listed


Matt Hale, PHD
University of Nebraska at Omaha
Assistant Professor, Cybersecurity
mlhale@unomaha.edu
twitter: @mlhale_
8470-Lecture-1
By Matt Hale
8470-Lecture-1
Secure Web Application Development - Class 1
- 127



