Mutual of Omaha discussions
Matt Hale
Assistant Professor of Cybersecurity
Nebraska University Center for Information Assurance

Slides available at http://slides.mlhale.com/moo18/
Who is This Guy?

Dog Father, Husband, Software Engineer, Researcher, Teacher, Web Developer, Board Gamer, Philosopher, Artist
(roughly in that order)


Tweet @mlhale_
Two Main Research Areas:
Internet of Things Security and Phishing Prevention
Two Main Research Areas:
Internet of Things Security and Phishing Prevention
Today's Focus
STOP.
Look Around at Your Neighbors
What IF I told you...
...the most sophisticated phishing websites would dupe about half (45%) of the people around you. Even average, less sophisticated, sites manage to convince more than 1 in 10 (13.7%).
More Numbers
60 billion
6 billion
3 billion
28 million
164 million
16.5 Million
8.2 Million
100,000
http://services.google.com/fh/files/blogs/google_hijacking_study_2014.pdf https://www.getcybersafe.gc.ca/cnt/rsrcs/nfgrphcs/nfgrphcs-2012-10-11-en.aspx
Enter the CyberTrust Platform
Cybertrust Project
(Preventing Phishing Victimization using Bio-behavioral Markers of Cyber Trust)
Investigating what trust factors influence decision making with suspicious content
Some of this material is based on research sponsored in part by the Air Force Office of Scientific Research (AFOSR), under award number FA9550-12-1-0457. The U.S. Government is authorized to reproduce and distribute reprints for Governmental purposes notwithstanding any copyright notation thereon. The views expressed in this talk are those of the author and do not reflect the official policy or position of the Department of Defense or U.S. Government.

PRior Work Acknowledgement
Identify root causes of victimization
Identify user awareness gaps
Train participants to recognize suspicious content
Prevent victimization
Basic Idea
Instrumentation and Tooling
The Platform
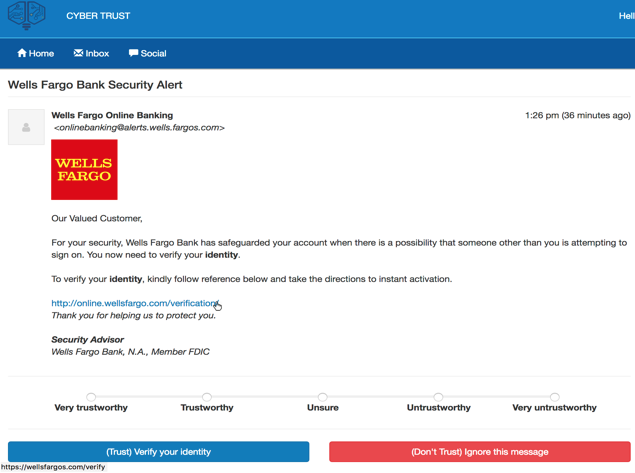
The Platform
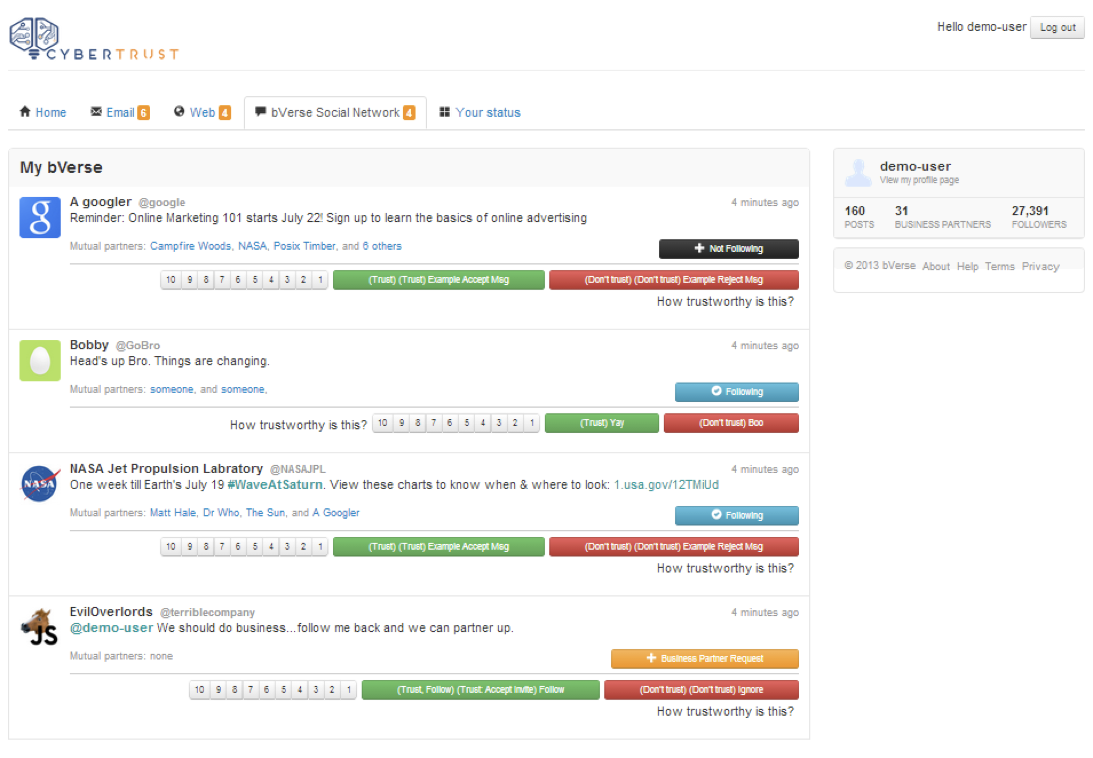
Previous Results:
predictor vs actual victimization
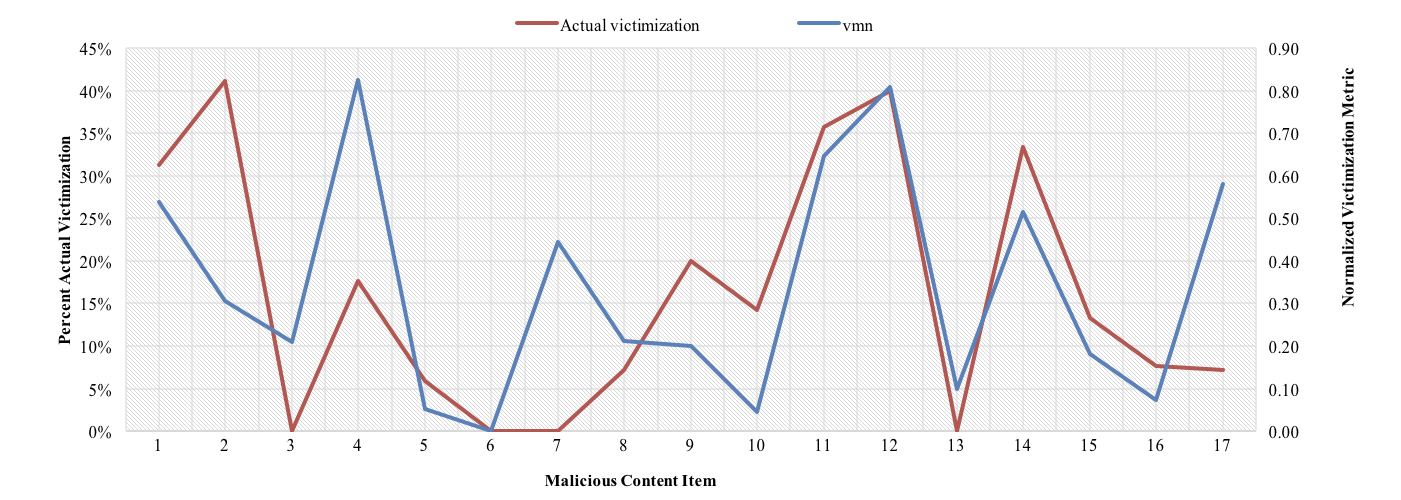
R=0.523, df=61, p=0.01
What Data is collected?
(eye movement data)
-
Behavior analysis tooling - What is wrong and how can we correct it?
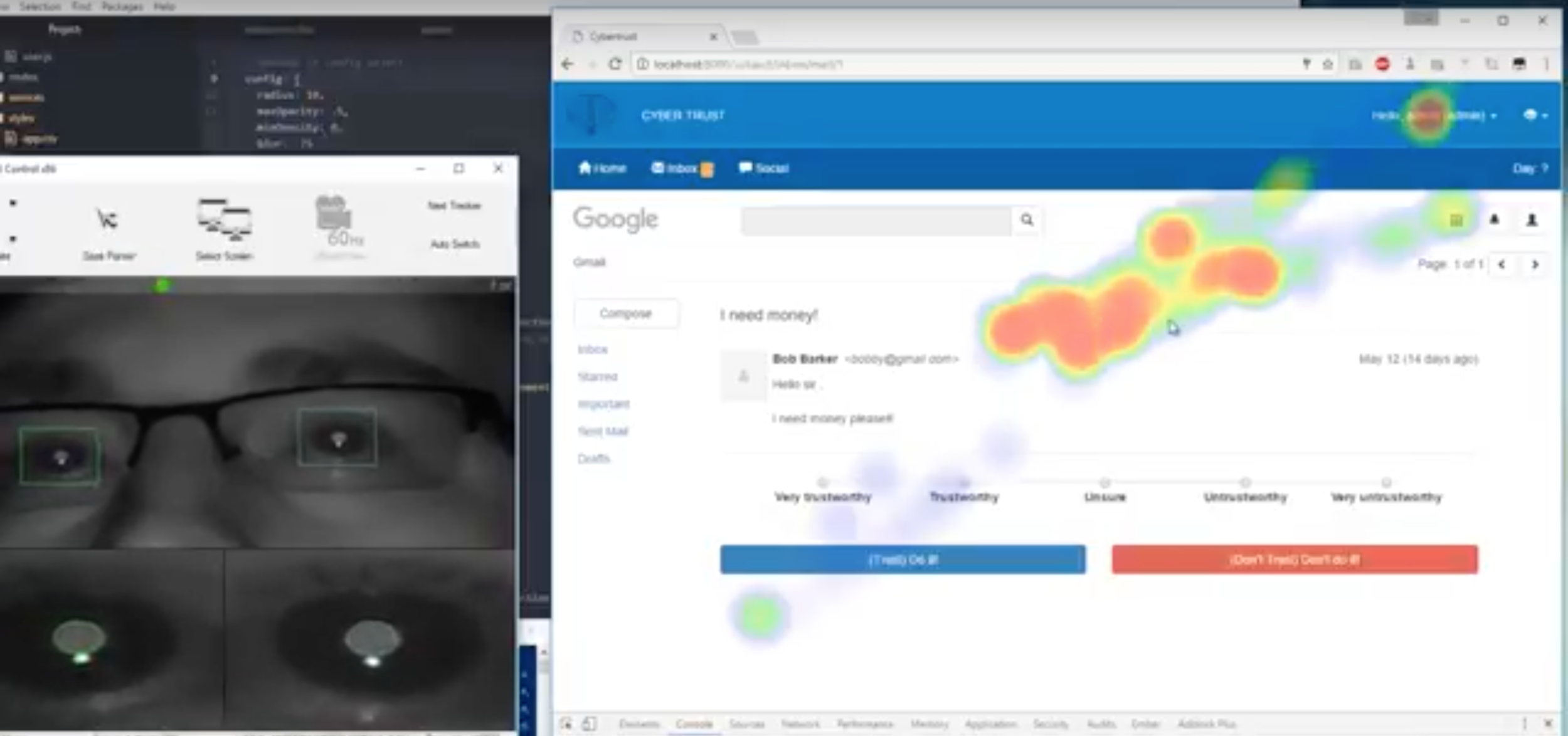
Example
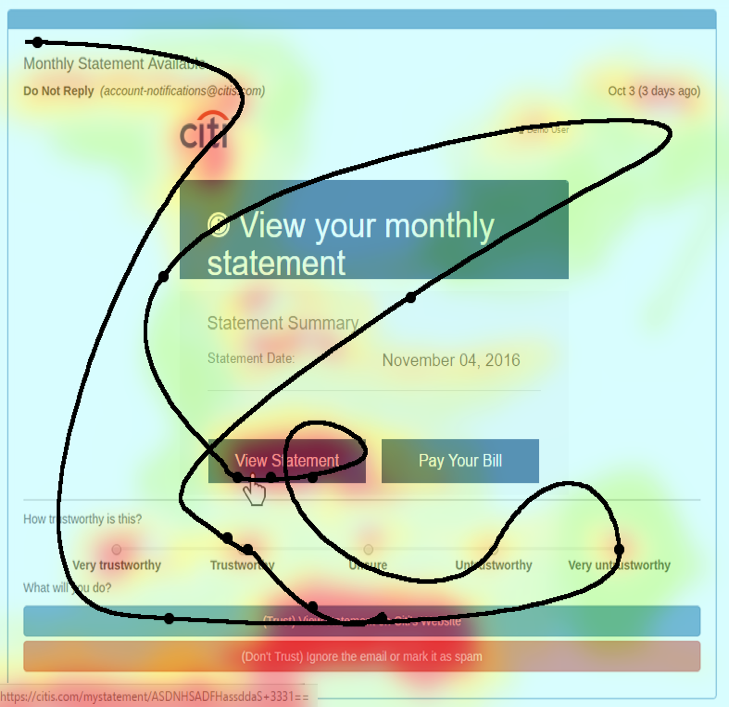
Heatmap and event tracing component output allows researchers to reconstruct subject sessions.
(black line = mousing events)
What's else is going on at UNO?
CyberSecurity @ UNO
NSA/DHS Designated Center of Academic Excellence
in Cyber Operations and Cyber Defense
NSF Scholarship for Service Program
6 Core Cybersecurity Faculty, 3 Affiliated Faculty, 1 Instructor
190 Undergrad students, 40 Grad students
Also offer a minor and concentration in Cybersecurity
Nebraska University Center for Information Assurance
Research Focus Areas
Secure Software Development: Web, Mobile, Wearables, Forensics-ready Software
Secure Embedded and Industrial Control Systems: ICS, DCS, SCADA
Secure Networking and Distributed Computing: Mobile, Cloud, Quantum Crypto.
Risk Management for Software Security Engineering
Behavioral Underpinnings of Trust
Questions?
©2018 Matthew L. Hale


Matt Hale, PHD
University of Nebraska at Omaha
Assistant Professor, Cybersecurity
mlhale@unomaha.edu
twitter: @mlhale_
Mutual of Omaha
By Matt Hale
Mutual of Omaha
HICSS 2018 Slidedeck
- 141



