OAuth 2.0
FI MUNI, PA053, Michal Čížek
What is OAuth 2.0?
- industry-standard protocol for authorization
- authorization flow for web, mobile and desktop applications
- latest version is 2.0, which is most commonly used
OAuth example:
Abstract of OAuth 2.0
- enables third-party application to obtain limited access to an HTTP service
- access is granted on behalf of a resource owner or by allowing the third-party application to obtain it on its own behalf
Tokens
- OAuth access token is a string that the OAuth client uses to make requests to the resource server
- There is no restriction on the token format
- Access tokens may be either bearer tokens or sender-constrained tokens
Bearer token
- more common
- opaque string
- not intended to have any meaning to clients using it
- usable by itself
Sender-contrained token
- require OAuth client to prove possession of a private key in some way
- token by itself is not usable
Important rules for access tokens
- Access tokens must not be read or interpreted by OAuth client. The OAuth client is not the intended audiance
- Access tokens do not convey user identity or any other information about the user to the OAuth client
- Access tokens should only be used to make requests to the resource server. Additionally, ID tokens must not be used to make requests to the resource server
Refresh tokens
- Tokens expire after some time
- Short lifetimes for access tokens have security benefits
- OAuth clients can use a refresh token to get a new access token without the user's interaction
- A refresh token must not allow the client to gain any access beyond the scope of the original grant
JWT tokens
- Abbreviation for JSON Web tokens
- Commonly used for OAuth
- A standard method for representing claims securely between two parties
- Information in the token can be trusted since it is digitally signed
- JWT token consists of a header, payload, and signature
JWT token example
"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c"{
"alg": "HS256",
"typ": "JWT"
}token string:
{
"sub": "1234567890",
"name": "John Doe",
"iat": 1516239022
}header:
payload:
OAuth roles
- Resource owner: User that knows credentials to access a particular resource
- Client: Additional application that wants to access the user account in the authorization server (resource server does not talk directly with the authorization server - security reasons)
- Resource Server: hosts the application that the user wants to access.
- Authorization server: holds the user's accounts and credentials
OAuth flow
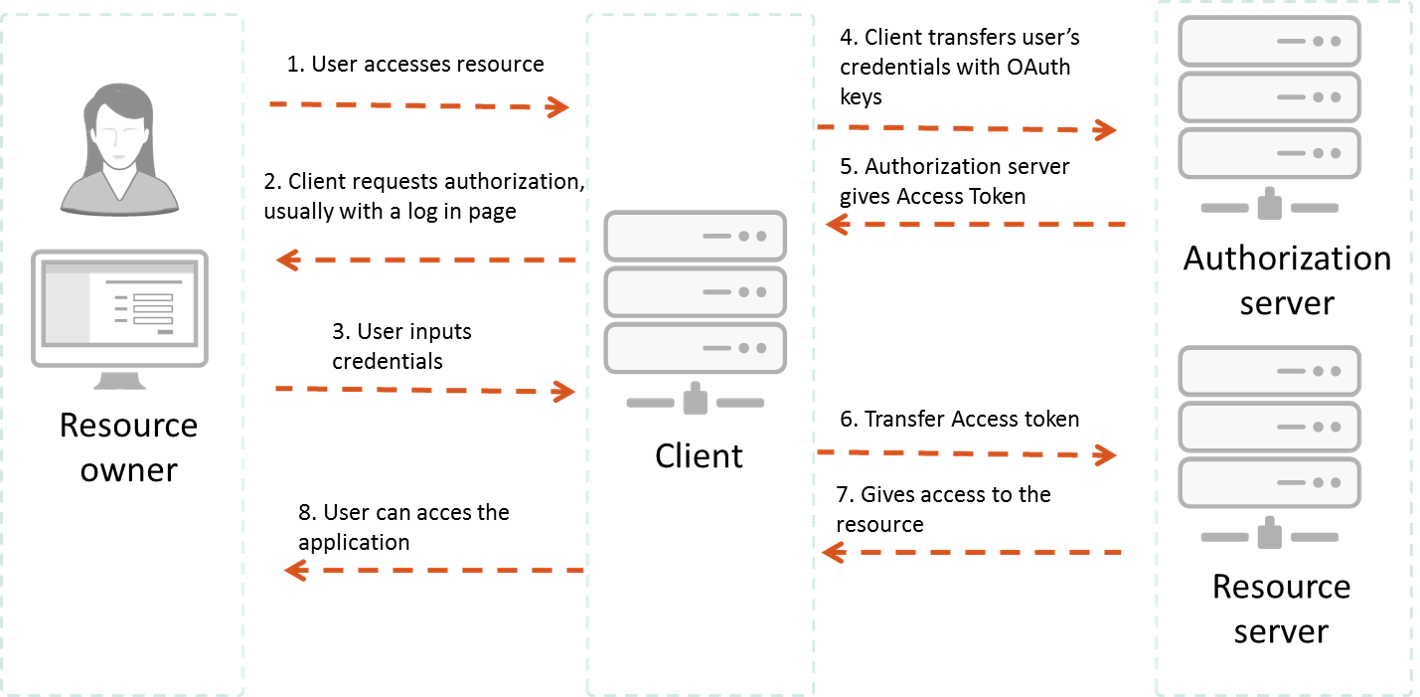
OAuth grant types
- OAuth specifies several grant types for different use cases
- The most common grant types are: Authorization code, PKCE, Client Credentials, Device Code, and Refresh Token
- Based on the grant type, the OAuth flow shown on the previous slide can be a bit different
OAuth scopes
- Applications usually need access to only a small subset of the resources from the resource server
- The user might not want to give the app permission for all the resources available
- Scopes are a mechanism in OAuth 2.0 to limit an application's access to a user's account
- An application can request multiple scopes
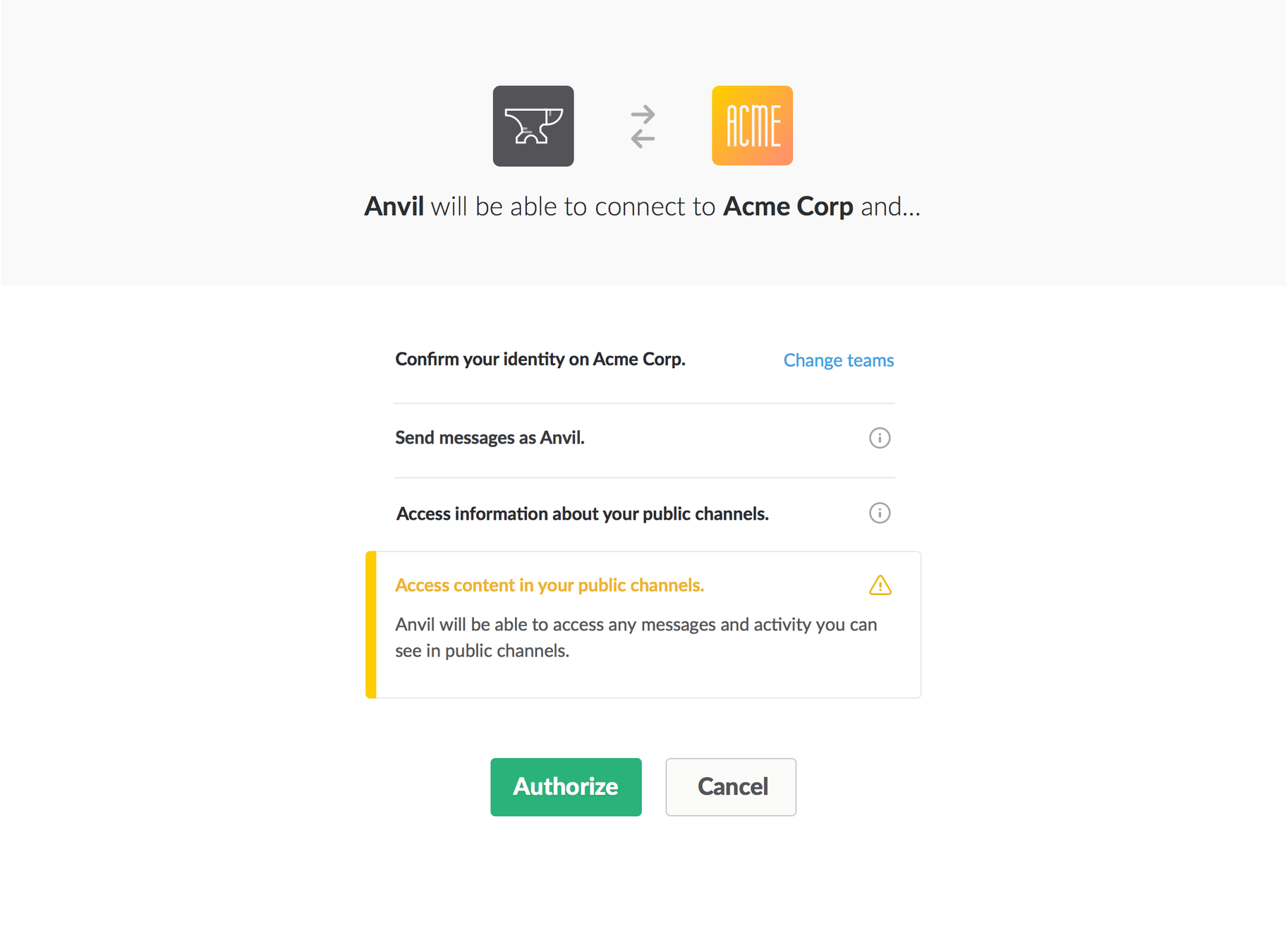
- Information for required scopes is presented in a consent screen
- Application will be limited to the scopes granted
OAuth scopes consent screen
Summary and takeaways
- OAuth is for authorization, not authentication
- OAuth allows authorization between multiple services/applications
- Access tokens are used to make requests to the resource server
- Refresh tokens are used to get a new access token
- Scopes limit the applications access to resources
OAuth
By Michal Čížek
OAuth
- 46


