Life behind the tinfoil curtain
A look at QubesOS and CopperheadOS
Konstantin Ryabitsev
The Linux Foundation
Linux Security Summit, 2018
Topics covered
- Why did you do this to yourself?
- Qubes OS
- Copperhead OS

- guiding principles
- device requirements
- installation
- daily use
- what you will like
- what will drive you mad
- convenience vs. security trade-offs
- future outlook
Including
Please interrupt at any time
for questions or clarifications
About me
-
Professional Russian Hacker
-
before it was popular
-
(you’ve probably never heard of me)
-
-
Linux on the desktop user since 1998
-
ask me about Corel Linux (or, actually, don't)
-
-
Member of the Linux Foundation IT team since 2011
-
Running Qubes OS since August 2016
-
Running Copperhead OS since September 2017
-
until June 2018
-
(but I hope to go back)
-
Caveat Auditor
- I am a systems administrator
- I am not a security researcher
- I am not a kernel developer
- I am a bit paranoid
- not nearly enough for some people

My goal is to share my experience using Linux-based tools aimed at significantly improving my security and privacy.

Qubes OS
Qubes OS: Guiding principles
- compartmentalization via virtualization
- using type-1 hypervisor (XEN)
- dom0 runs the graphical interface
- all applications run inside AppVMs
- hardware isolation
- I/O devices must be assigned to VMs
- convenient management tools
- network isolation
- full control over how appVMs get to the net
- (or not at all for vault VMs)
Qubes OS: Device requirements
- lots of RAM (16GB+)
- fast, large SSD disks (NVMe)
- multiple processors with many cores
- but works comfortably with 2x2
- CPU MUST have:
- Intel VT-x with EPT (or AMD-V with RVI)
- Intel VT-d (or AMD-Vi aka IOMMU)
- Intel graphics
Qubes OS: Installation
- modified Fedora installer
- post-installation requires knowledge
of what you're doing before you do it- sys-usb for your USB devices?
- which USB controller to assign to it?
- create regular AppVMs? (probably yes)
- work
- personal
- vault
- untrusted
- sys-usb for your USB devices?
Qubes OS: AppVMs
- think of them as isolated logical workspaces
- decide how they all get online
- does "work" need an employer VPN?
- does "personal" need a generic VPN?
- does "untrusted" need to go out via TOR?
- learn to love and use disposable VMs
- send them through TOR (maybe)
- learn how templates work
- everything not in /rw is lost
- you get Fedora, Debian, Whonix
- community templates available
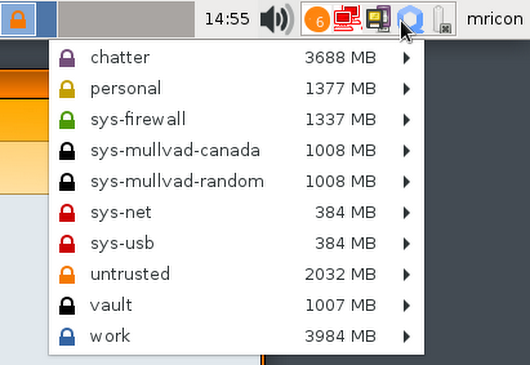
Qubes OS: Daily Use
- for the most part, everything works as you expect
- except:
- copying files
- you get used to it very quickly
- copy-pasting
- Ctrl-Shift-C/V to copy between AppVms
- (this will drive you crazy)
- installing software via dnf/apt
- must be done in TemplateVMs to persist
- changing global config values
- symlink things to /rw/config
- copying files
Qubes OS: what you will love
- feeling that your data is well protected
- opening mail attachments in disposable VMs
- at least in Thunderbird
- Sanitizing PDFs
- opens a DispVM and renders as images
- Fedora (or other template) upgrades
- don't like it, set it back to the previous template
- VaultVMs
- different endpoint egress per AppVM
Qubes OS: What will drive you mad
- copy-pasting
- not being able to screenshare
- you have to run a standalone windowed VM
- suspend/resume bugs
- launch lag when an AppVM is not running
- especially if it has to launch NetVMs first
- rare, but random weirdness
- occasionally, AppVMs won't start
- or your microphone stops working
- or the resolver in one of the VMs
- complicated backups
Qubes OS: Future Outlook
- Sponsored by Invisible Things Lab
- Under active development
- Partially user-supported via donations
- Uses XEN
- is written to be able to use other
virtualization platforms, if needed
- is written to be able to use other
- Has an active and diverse user base
Qubes OS: Who is it for?
- Systems administrators
- or similar gatekeepers with access to privileged data
- Journalists
- if they have a knowledgeable support department
- Anyone expecting direct precision attacks by well-funded and savvy adversaries
- Anyone working in environments where they are likely to be in trouble if caught by dragnet surveillance
Qubes OS: Who is it not for?
- Anyone not very familiar with Linux
- especially if they are doing it on their own
without a tech support department
- especially if they are doing it on their own
- Anyone who can't afford modern, powerful hardware
- CPUs capable of VT-x and VT-d, lots of RAM, large SSD come with a high price tag
- Anyone in danger of physical duress threats
- you probably just want Tails for deniability
Qubes OS: What can you use instead?
- You can reach some degree of feature parity with:
- Firejail for browser sandboxing
- Flatpak for other app isolation
- Whonix for persistent anonymous surfing
- TailsOS for disposable web sessions
- QubesOS offers all of the above plus convenience
- at the cost of a very steep learning curve

COpperhead OS
So much has happened since May
Copperhead OS in its previous incarnation is dead.
Existing installs won't receive any updates.
Must migrate to newer images.

Copperhead: guiding principles
- Also in other "pure AOSP androids":
- Google-free android experience
- Fast security patching turnaround
- Unique to Copperhead:
- Hardened kernel (plus KSPP patches)
- Hardened compiler toolchain
- Stricter SELinux policies
- MAC address randomization
- Stricter defaults
- and more

Maybe I should be more like Alex...

I.Repin: Ivan the Terrible kills his only son

I've destroyed
the firmware
signing keys
LOL U WOT MATE?
Copperhead: device requirements
- Only available on a very small set of devices
- Google Nexus
- Google Pixel (+XL)
- Google Pixel 2 (+XL)
- HiKey dev boards
Copperhead: Installation
- Downloadable and installable
- no OTA updates if you do this!
- a pretty involved process
- Buy a Pixel from CopperheadOS
- with ~80% markup
- Send in your own Pixel
- pay quite a lot of money
Copperhead: Daily use
- For the most part, just like any other "pure AOSP" device
- Some apps are available from F-Droid
- K-9 mail
- Some messengers (Telegram, Riot, Silence)
- Some others can be side-loaded:
- YALP
- APK Mirror
- Amazon Appstore
- Many apps may not work right, or at all
- (no, MicroG didn't work)
- Excellent for secure communication and browsing
- Excellent remote attestation feature
- Some apps are available from F-Droid
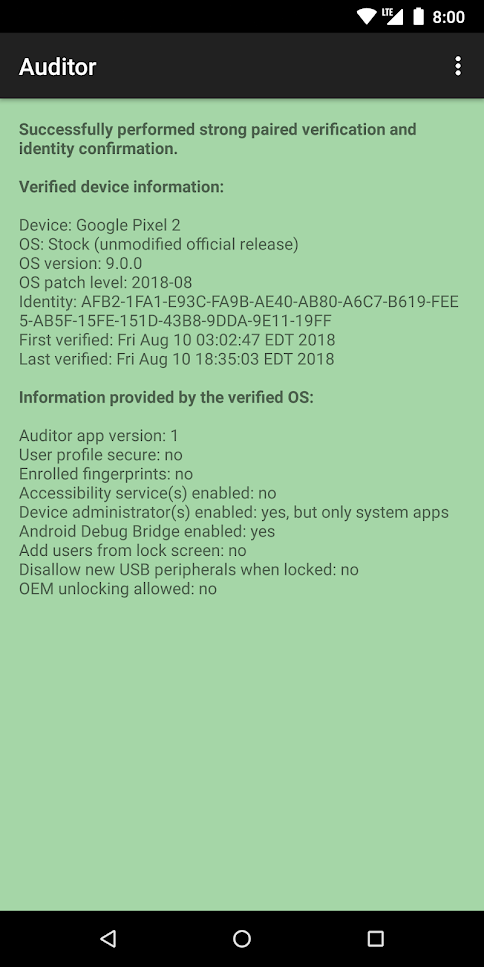
Copperhead: Auditor
The Auditor app uses hardware security features on supported devices to validate the integrity of the operating system from another Android device. It will verify that the device is running the stock operating system with the bootloader locked and that no tampering with the operating system has occurred. It will also detect downgrades to a previous version.
Pure AOSP: what you'll lOVE
- Battery life
- Knowledge that you're not being tracked
- ... as much
- depends on which apps you install and use
- your mobile service provider still tracks you
- Fast security patches
- depends on which Pure AOSP build you're using
- LineageOS is pretty good
- Knowledge that you're using free software
- F-Droid supports reproducible builds
- (some features may be source-available)
Pure AOSP: what you'll Hate
Pure AOSP: what you'll Hate
- Huge loss of convenient perks we've come to associate with owning a mobile device
- Side-loaded apps may or may not work
- they probably won't deliver notifications
- they may stop working at any time
- app authors don't care about your weird setup
- Side-loaded apps may or may not work
- True, you can communicate securely
- but only with people using the same 3 messaging apps
- your team members are probably on Slack
- your friends are probably on Facebook Messenger
- which actually works great
- but then what's the point?
Owning a pure-AOSP device comes with All the social perks of being a gluten-intolerant vegan with a peanut allergy

Also, you can't play Pokemon Go

Copperhead: Future Outlook

Copperhead: who is it for?
- Anyone really worried about dragnet private data collection by governments or large corporations
- true for most Pure-AOSP builds
- Anyone expecting direct precision attacks by well-funded and savvy adversaries
- Government employees
- Journalists
- Activists
Copperhead: who is it NOT for?
- Anyone who needs to use their device for more than secure communication
- or is dependent on apps that do not work well in a pure-aosp environment
Copperhead: what am I using now?
- I am back to stock Google Pie
- with some privacy tweaks
- I try to limit which apps I use
- use the mobile web version, if available
- the Hermit app makes this easier
- I don't intend to switch to LineageOS
- Not getting notifications was impacting my work
- Security improvements in stock Google Pie are impressive and are probably sufficient for my needs
- I will probably go back to CopperheadOS when I need a newer phone, if all goes well with the company

Does that make me a sheep?
Maybe, for now...
But at least I have an option to evolve.

EOF
LSSNA18: Life Behind The Tinfoil
By Konstantin Ryabitsev
LSSNA18: Life Behind The Tinfoil
Personal experiences using QubesOS and CopperheadOS.
- 4,151



