Using PGP with GIT
(and why you should care)
Konstantin Ryabitsev
The Linux Foundation
kernel.org
LOL WAT, PGP?

Git is not a blockchain
- YES "Chain"
- NO: "Block"
- Also NO: proof
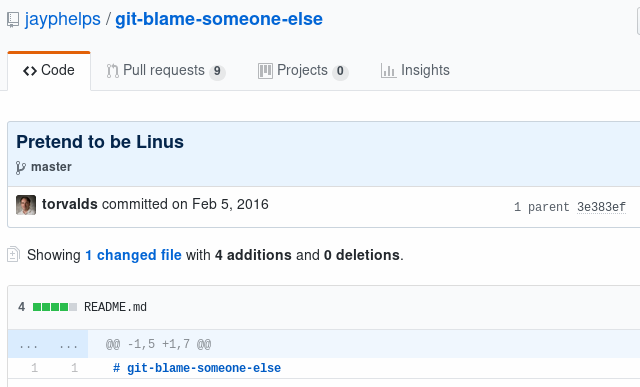
git blame-someone-else
How much do you trust:
- Your teammates?
- Your bosses?
- Other members of your FOSS project?
- Administrators of GitHub?
- ... of Microsoft?
Can push = can spoof
(certain conditions apply)
in 2011 kernel.org was breached
(but it's okay)
object 17b57b1883c1285f3d0dc2266e8f79286a7bef38
type commit
tag v4.19-rc6
tagger Greg Kroah-Hartman <gregkh@linuxfoundation.org> 1538318530 -0700
This is the 4.19-rc6 release
-----BEGIN PGP SIGNATURE-----
iQIzBAABCAAdFiEEZH8oZUiU471FcZm+ONu9yGCSaT4FAluw4MIACgkQONu9yGCS
[...]
=dMl4
-----END PGP SIGNATURE-----
git cat-file -p v4.19-rc6
what we've assured:
- object hash
- tag string
- tag message
tree 8985bd35269204c126b193d721cc260d740367fd
parent 9a10b063758c756a4d60d63acb890c27d03c9bef
author Greg Kroah-Hartman <gregkh@linuxfoundation.org> 1538316935 -0700
committer Greg Kroah-Hartman <gregkh@linuxfoundation.org> 1538316935 -0700
Linux 4.19-rc6
git cat-file -p 17b57b18
what we've assured:
- tree hash
- parent commit hash
- author info
- committer info
- commit message
[...]
100644 blob da4cb28febe66172a9fdf1a235525ae6c00cde1d COPYING
100644 blob 5befd2d714d0037548bed049a979dc4fcee1d300 CREDITS
040000 tree d573ed6502044d1cbc9860e3a34b7687652bfd9b Documentation
100644 blob 00530420548225a8b26a36f504d9aa00468ddb42 Kbuild
[...]git cat-file -p 8985bd35
what's in a tree hash?
what we've assured:
- contents of toplevel dir
- (perms, types, sums, names)
- hashes of subdirs
- (perms, types, sums, names)
Changing anything in a repository will result in a different tree hash
Changing anything about a commit (author, date, tree, etc) will result in a different
commit hash
Changing anything in the repository history (including adding/removing commits)
will result in a different
parent commit hash
signed git tags
When you sign a git tag, you create a cryptographic assurance that a cloned repository (and its entire history) are exactly, byte-for-byte, the same as on the developer's system.

git tag -s
Nature's immutable crypto chain
git commit -S
You can also sign commits:
- you can protect the entire tree by signing the tip commit
- useful when multiple people push into the same repository
- great for digital forensics
- also handy for people cherry-picking your commits
Protect your keys
You should treat your PGP keys as your developer's proof of identity:
- Store the master key offline
- Put the subkeys onto a hardware token
- Yubikey
- Nitrokey
- SmartCard

We have a handy doc!
https://github.com/lfit/itpol/
It covers all you need to know:
- PGP basics and best practices
- How to use PGP with Git
- How to protect your developer accounts
https://github.com/lfit/itpol/
Thank you!
https://github.com/lfit/itpol/
Using PGP with GIT
By Konstantin Ryabitsev
Using PGP with GIT
- 2,001



