Grab 'n Run
Ofek Wittenberg
Introduction
- The Android Market is huge
- This promotes competition
- Which leads to the use of DCL (Dynamic Code Loading)
What is DCL?
- Similar to shared libraries.
- Allows applications to load code that is not part of the initial code base.
- Library is loaded at runtime.
Why use DCL?
- Promote code reuse
- Self upgrade functionality
- Boost performance
- Extensibility

The drawbacks of DCL?
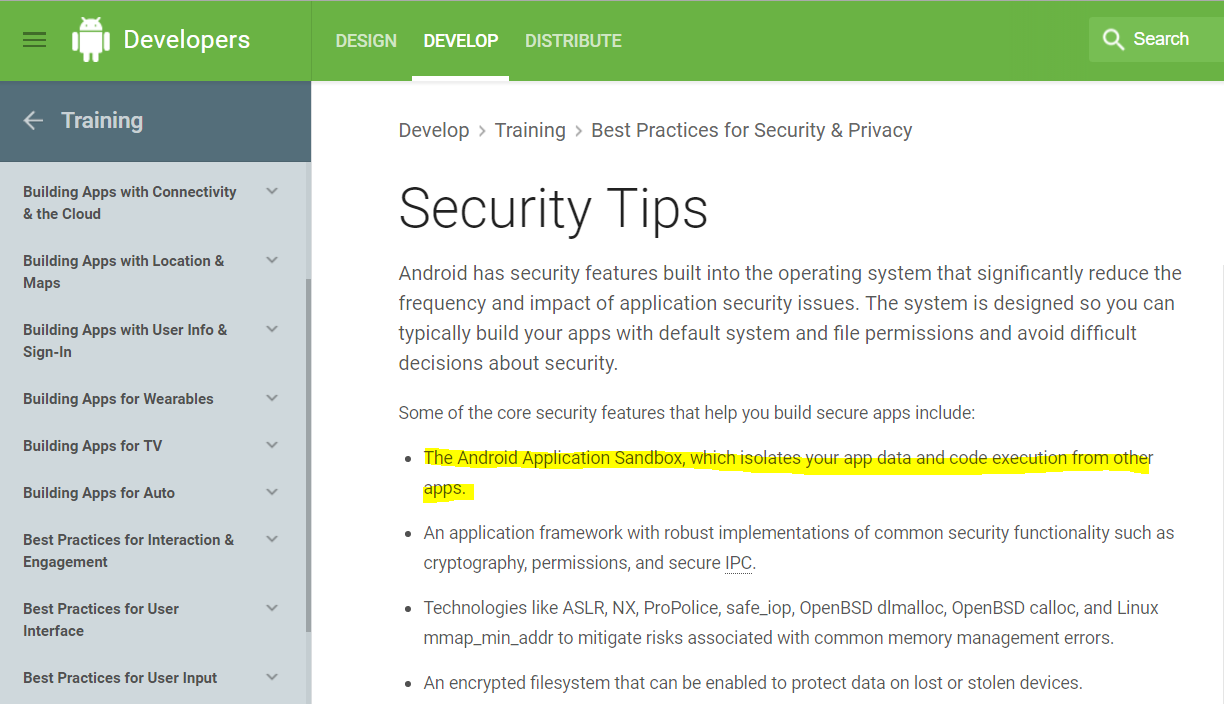
- Hard to make secure
- Can lead to code injection attacks (Man in the middle attacks)
- Evades static and dynamic analysis systems (Google Bouncer)
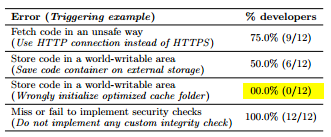
- 16% of the top 50 apps are affected

How is DCL Exploited?
- Code Retrieval
- Vulnerabilities: Plain text
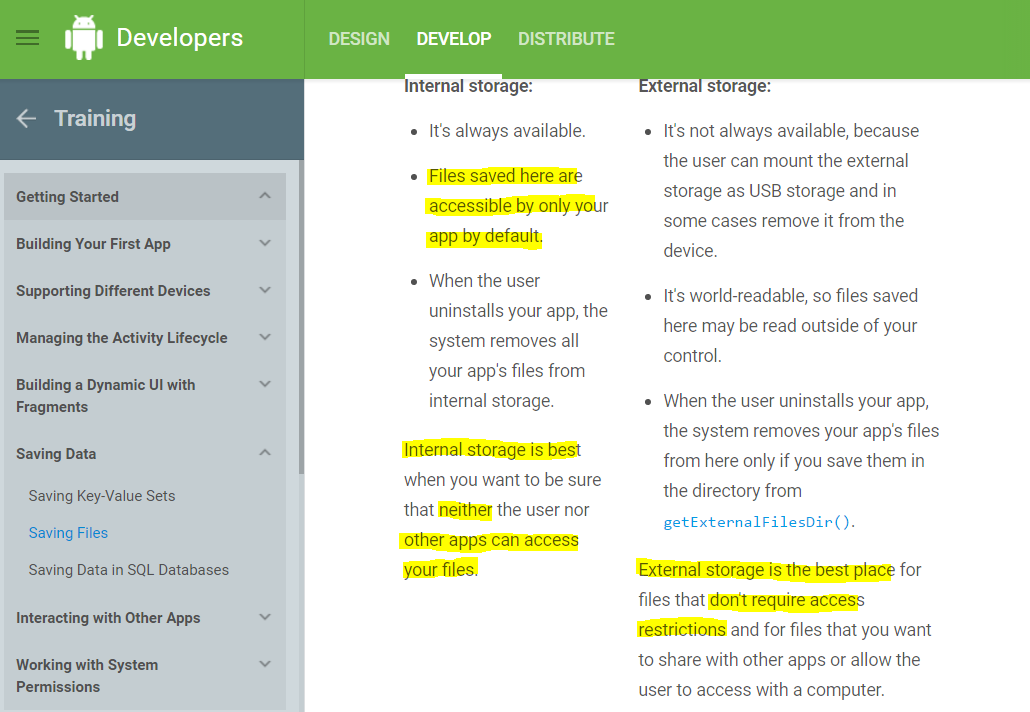
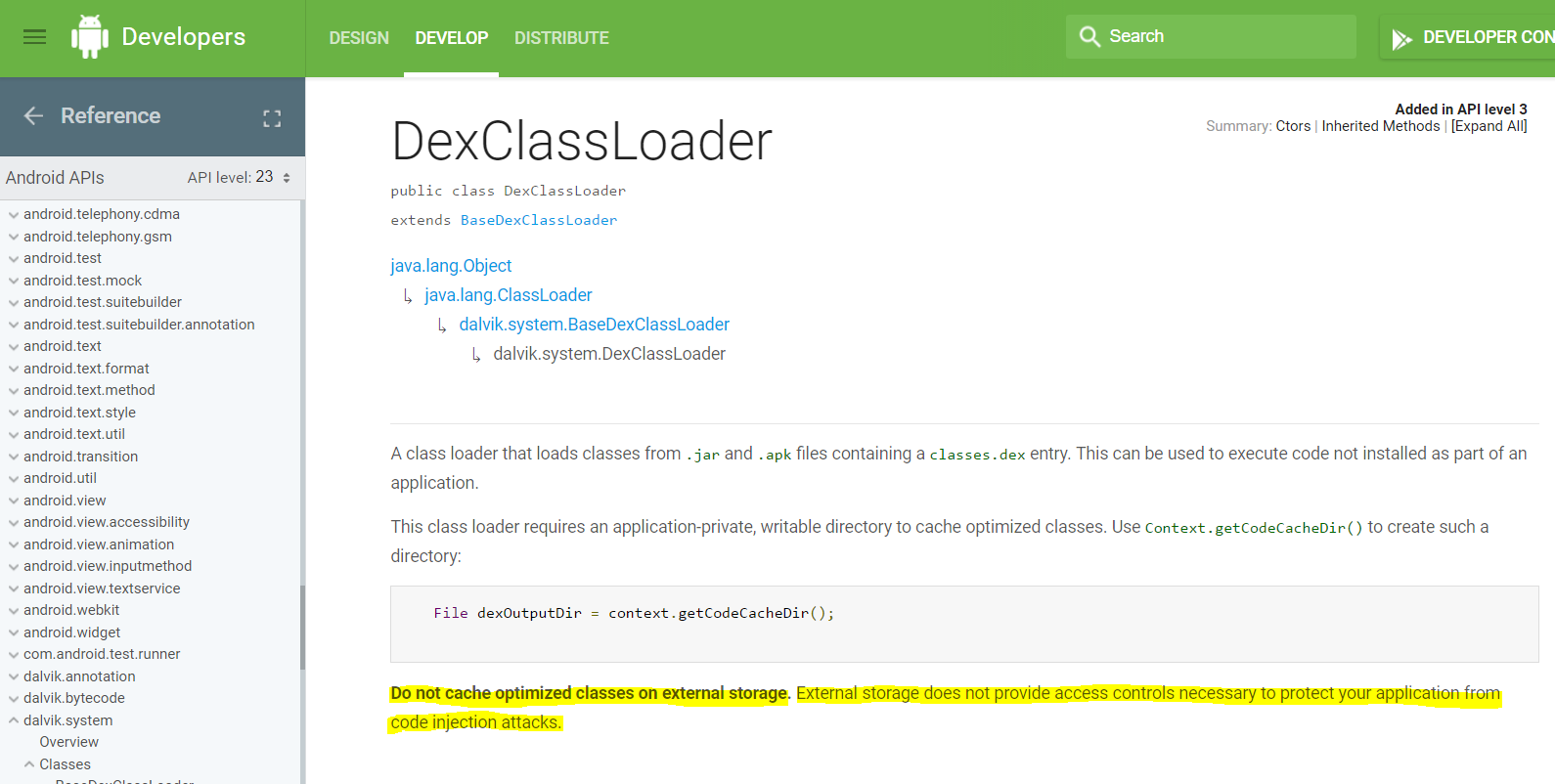
- Code Storage - needed due to framework restrictions
- Vulnerabilities: Vulnerable storage location such as in a world writable location - Enable malicious code to obtain rights of host app
-
Code Loading & Verification - Initialize the Android Framework responsible for handling the loading operation
- Vulnerabilities - Ensuring end to end code integrity.

Threat Model
The scope this solution aims to meet?
- Device - Execute malicious code
- Network Communication - Exploitation of unencrypted connections (MITM).
- Remote Server(s) - attacker cannot compromise a remote server

Grab n Run Goals
- Create a new library for DCL
- The library must be practical
- Make this library usable also when DCL functionality are implemented within third-party libraries.

Code Verification Protocol
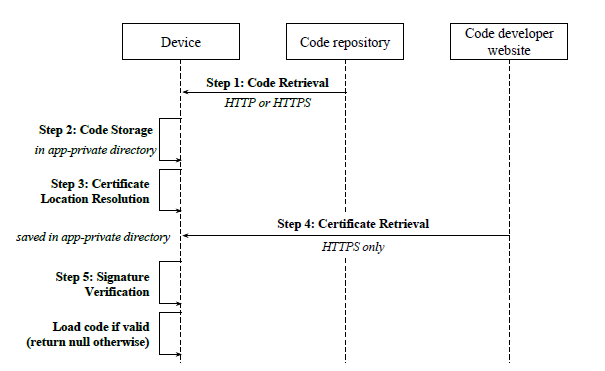
The SecureDexClassLoader API
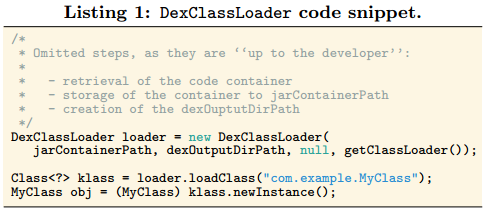
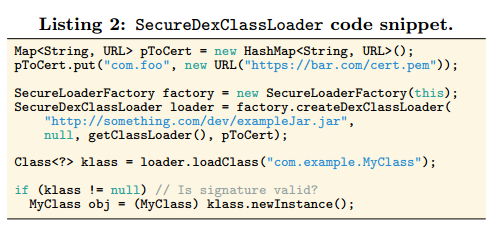
Repackaging Tool
- Unpacking
- Manifest Update
- Call Site Identification
- Patching
- Reassembly


Evaluation
- 12 developers
- Skeleton app provided
- Devs tasked with:
- Obtaining remote code
- Dynamically loading the code
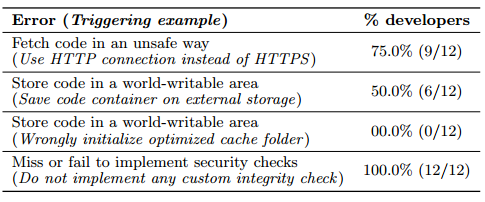
Feedback
- 12/12 Excellent rating for the Overall evaluation of Grab'n'Run API
- 12/12 Excellent rating for perceived security of SecureDexClassLoader
- 11/12 Easier to implement Grab'n'Run API over DexClassLoader
- 10/12 Grab'n'Run resulted in better code maintainability over DexClassLoader
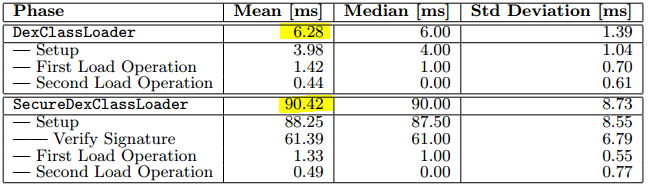
Performance
Criticisms
Weak evaluation
Setting up secure remote endpoints is not trivial


Single point of failure

Non trivial overhead
Limited to DexLoader
Improvements
- Reduce overhead
- if code retrieved via trusted HTTPS source no need to verify?
- Configurable automation tool
- Allow for any methods of DCL
- Remove single point of failure -
- Ensure, that code and certificates are stored in different domains
- Google services integration
- Utilize a Public Key Infrastracture (PKI)
- More comprehensive evaluation
Summary
- Dynamic Code Loading (DCL) is a useful feature of Android, but is supported and implemented insecurely.
- Grab ‘N Run aims to ensure DCL is done securely and easily, including third party applications.
- Grab ‘N Run does this by implementing:
- Secure storage of dynamically loaded code.
- Guaranteed code verification via certificates
- Grab ‘N Run automated patcher
- Several significant limitations
702 Seminar - Grab 'n Run
By Ofek Wittenberg
702 Seminar - Grab 'n Run
- 701



