Buffer Overflow

Speaker : Erica
2019 / 11 / 17
- Introduction of Buffer Overflow
- Lab - Simple buffer overflow
- How do attackers exploit buffer overflows?
- Conclusion
- Reference
Contents
Introduction of
Buffer Overflow

What is Buffer Overflow?
Buffer overflow is an anomaly that occurs when software writing data to a buffer overflows the buffer’s capacity, resulting in adjacent memory locations being overwritten.
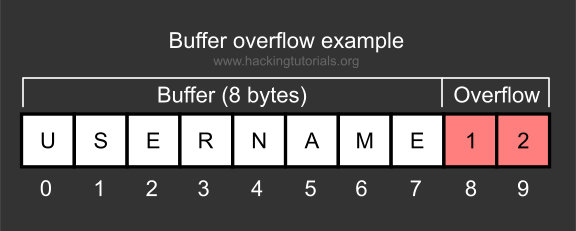
What is Buffer?
A buffer, or data buffer, is an area of physical memory storage used to temporarily store data while it is being moved from one place to another.

Who is vulnerable to buffer overflow attacks?
Certain coding languages are more susceptible to buffer overflow than others. C and C++ are two popular languages with high vulnerability.




Types of buffer overflow
- Stack overflow attack
- Heap overflow attack
- Integer overflow attack
- Unicode overflow
Lab
Simple buffer overflow

Step1 - Coding
#include <stdio.h>
void Name()
{
char name[10];
printf("What's your name?\n");
gets(name);
printf("Hey %s, how are you?\n", name);
}
int main()
{
Name();
return 0;
}Use C language :
void Name()
char name[10];It's a function can get the name.
Define a character array "name[10]"
with 10 character elements.
Ask users enter their name.
printf("What's your name?\n");
gets(name);
printf("Hey %s, how are you?\n", name);void Name(){Step2 - Install GCC via homebrew (Mac)
You can get homebrew form here .
And install GCC:
$ gcc --version
$ whereis gccIf you want to confirm the installation, you can execute the following command:
$ brew install gccStep2 - Install GCC via mingw (Windows)
You can get mingw form here .
And change the Environmental variables :
$ gcc --vIf you want to confirm the installation in Windows, you can execute the following command:
C:\MinGW\binStep3 - Use GCC
Open your command line and enter :
$ gcc overflow.c -o overflow -fno-stack-protectoroverflow.c is your file name.

$ gcc overflow.c -o overflow -fno-stack-protectorThis command means
"Do not enable stack protector".
-fno-stack-protector
This option can be used to set the name of the compiled product.
-o
$ gcc -o overflow overflow.c -fno-stack-protectorWhat is your name?
>>>Erica
Hey Erica, how are you?If your input less than 10:
Step4 - Run the code
If you use Windows, you can just enter the file name.
$ ./overflow //overflowWhat is your name?
>>>EricaOneAAAAAAAAAA
Hey EricaOneAAAAAAAAAA, how are you?
segmentation fault If your input more than 10:
It means we use "Buffer Overflow" to let this program broken.
segmentation fault
If you remove this command, recompile and execute, you should find a failure.
fno-stack-protector


If your input less than 10
▼ Stack
Why segmentation fault?
| name[1] ... name[10] |
| rdp |
| ret of Name |
If your input more than 10
▼ Stack
| name[1] ... name[10] |
| rdp |
| ret of Name |
Erica
OneAA
AAAAAAAA
How do attackers exploit buffer overflows?

An attacker can deliberately feed a carefully crafted input into a program that will cause the program to try and store that input in a buffer that isn’t large enough, overwriting portions of memory connected to the buffer space.

Conclusion

How to prevent buffer overflow attack?
2 common protections that help mitigate the risk of exploitation :
- Address space randomization
- Data execution prevention
Software developers can also take precautions against buffer overflow vulnerabilities by writing in languages that have built-in protections or using special security procedures in their code.
Reference

-
Buffer overflow From Wikipedia. Retrieved from: https://reurl.cc/b6N9Yo
-
緩衝區溢位攻擊之一(Buffer Overflow) 。Retrieved from: https://reurl.cc/9zb4vd
- Buffer Overflow. Retrieved from: https://reurl.cc/jdmDyp
- 在 Windows 10 中安裝 MinGW 及設定環境變數。Retrieved from: https://reurl.cc/jdmvvm
- GCC 下載安裝與基本使用教學。Retrieved from: https://reurl.cc/zyK660
Reference - 2

- strcpy溢出的攻击示例。Retrieved from: https://reurl.cc/8lbN04
-
攻擊行為-緩衝區溢位 Buffer Overflow。Retrieved from: https://reurl.cc/Ylk0VX
-
GCC,LLVM,CLANG 編譯器。Retrieved from: https://reurl.cc/XXamq3
Thanks for listening.

Buffer Overflow
By oneone
Buffer Overflow
11/17 present
- 177



