Security for Transitioning Company
Michael Wittner
The Scenario
- JustWorks - SaaS startup transitioning to mid-sized
- Customers are primarily businesses
- Primarily focus on Human Resources
- Internal servers compromised
- Not sure where/how
- Primarily focused on production servers security prior


Assets And Threats
Assets
- Windows and Linux Servers
- Development
- Production
- Corporate Laptops for Employees
- About 100 employees
- Total Endpoints (about 125)
Threats
- Malware and Ransomware
- What the company experienced
- Phishing (potential entry vector)
- Denial of Service
- Potential for Advanced Persistent Threat, but unlikely
Issue At Hand
- Not enough quality logs
- Log Filtering
- Not enough real-time alerts
- Insecure firewall rules
- Out-of-date authentication and security model
- Lack of defense in depth

Security Model
- Chinese Wall Model as the primary model
- Allow employees to access the things that they need
- E.g. developers only ones able to access development servers
- Cost: (assuming cyber experts cost $100/hour)
- $146,400 in salary (6 months)
- $10,000 to $20,000 in other unforeseen expenses
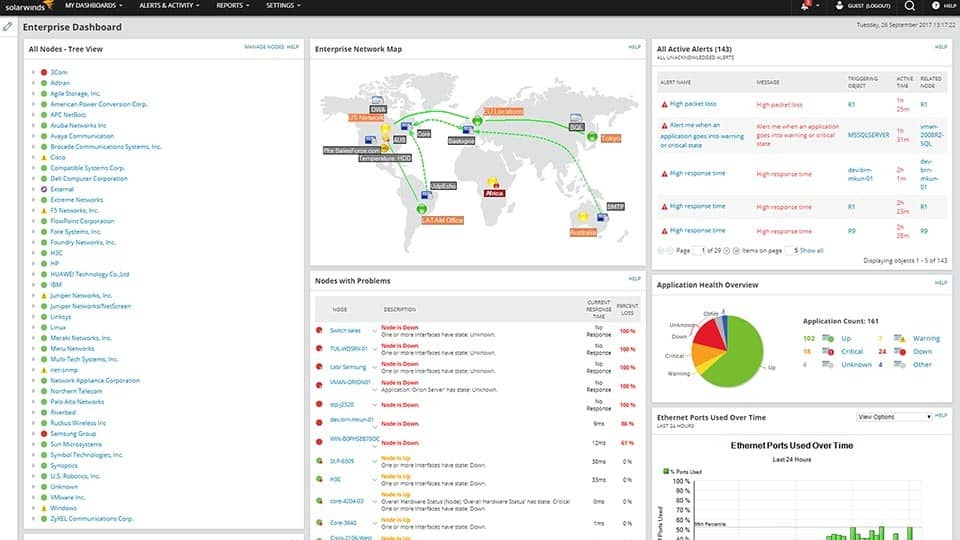
Network Monitoring
- Add Splunk and Snort
- Splunk can filter logs and generate reports
- Snort gives more detailed alerts and prevents intrusions
- Cost: $2500/year (hosting)
- Potentially use something more advanced like SolarWinds (if it's secure)
- Estimate, $15,000-$20,000
Enhanced Security
- Multi-Factor Authentication with Single Sign-on
- Encrypted communication on VPN
- Separate Networks as much as possible
- Internal servers only accessible through VPN or direct-access
- Separate VPN for Engineering and everything else
- Minimum: $7000/year (closer to $9000/year)
Endpoint Detection
- Honeypots (within both networks)
- Discover attack methods of adversaries (for all types of endpoints)
- Cost: Initially, $7,500 per five canaries/year minimum (no more than $15,000)
- FireEye/CrowdStrike endpoint protection
- Advanced endpoint detection
- $59.99/year per endpoint
- About $7500/year
Future Development
- Add developers to automate network analysis
- Can use machine learning to automate rule generation
- This should be innovative, cost is dependent on how much extra space is available

Summary
- Security Model is a need-based model
- Network and Endpoint protection/monitoring needs investment
- Dedicating time to improving Security can lead to long term savings
- Current total cost
- $196,000/minimum per year
Sources
- https://www.provendatarecovery.com/blog/cyber-security-cost-expenses-fees/
- https://www.solarwinds.com/onlinequotes/#/addLicense
- https://nordvpnteams.com/pricing/
- https://canary.tool
- https://www.business.com/reviews/fireeye-endpoint-security/#:~:text=Pricing%20starts%20at%20%2439%20per,or%20a%20downloadable%20virtual%20appliance.
Final Project Slides
By Ragnar Security
Final Project Slides
- 293



