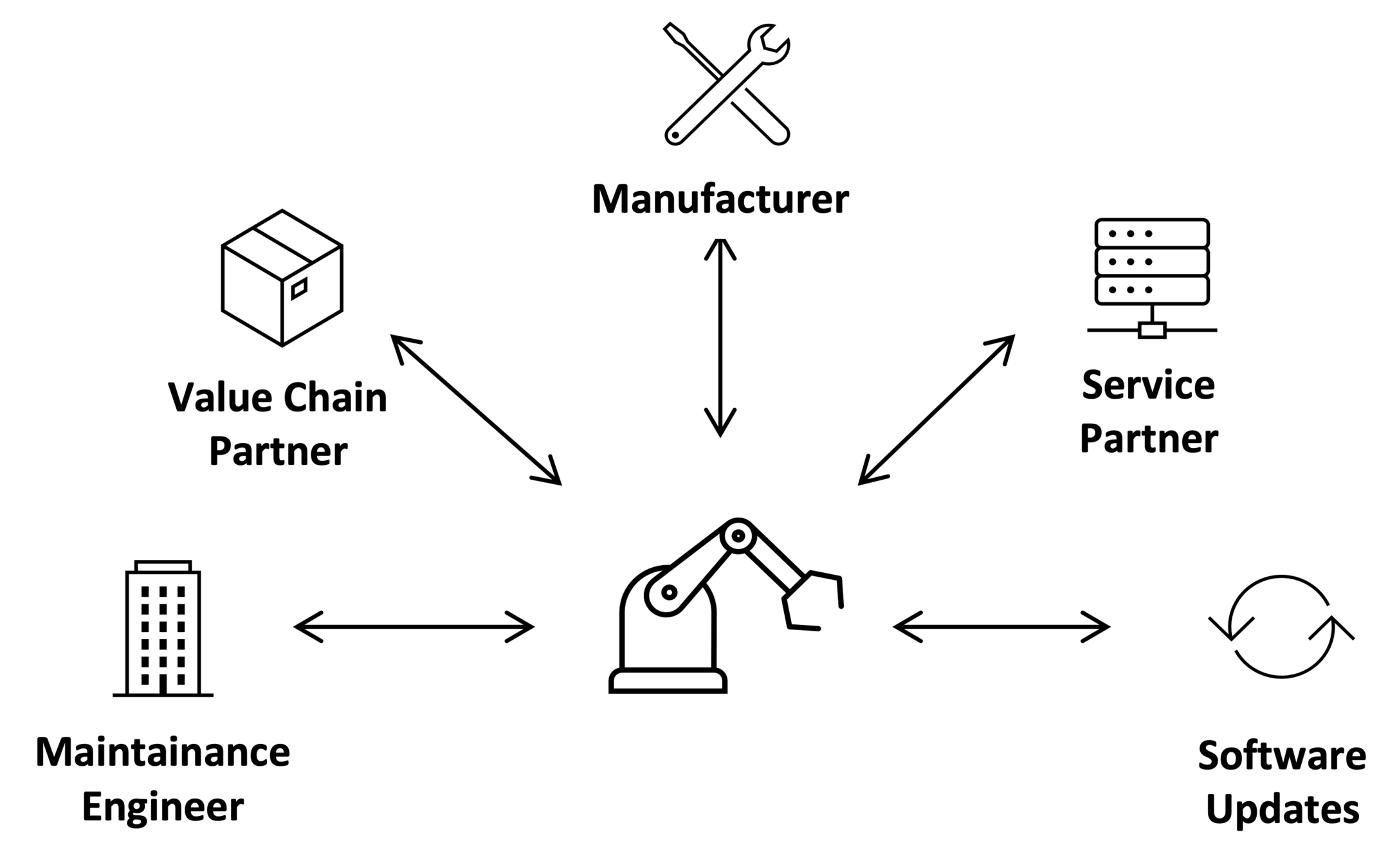
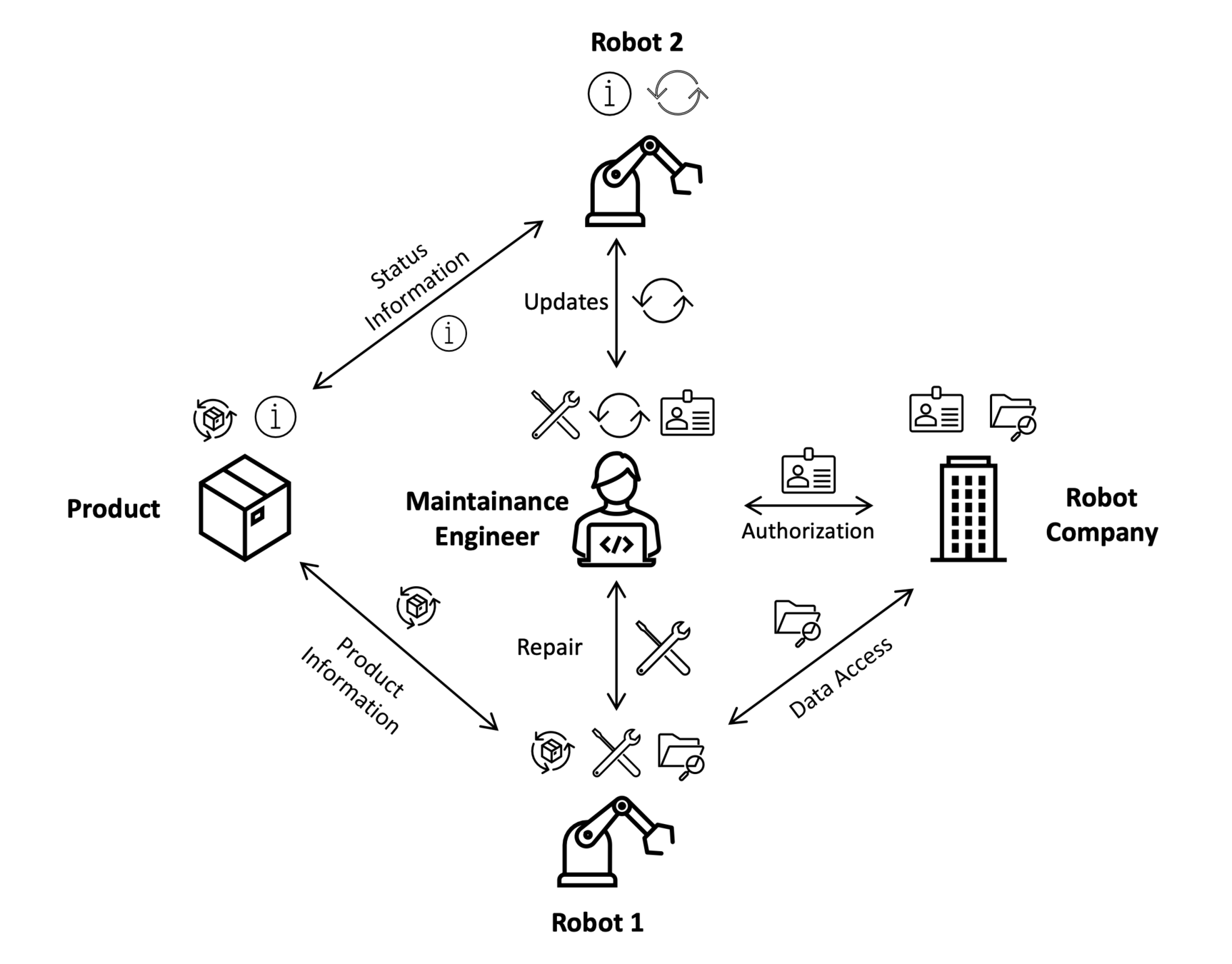
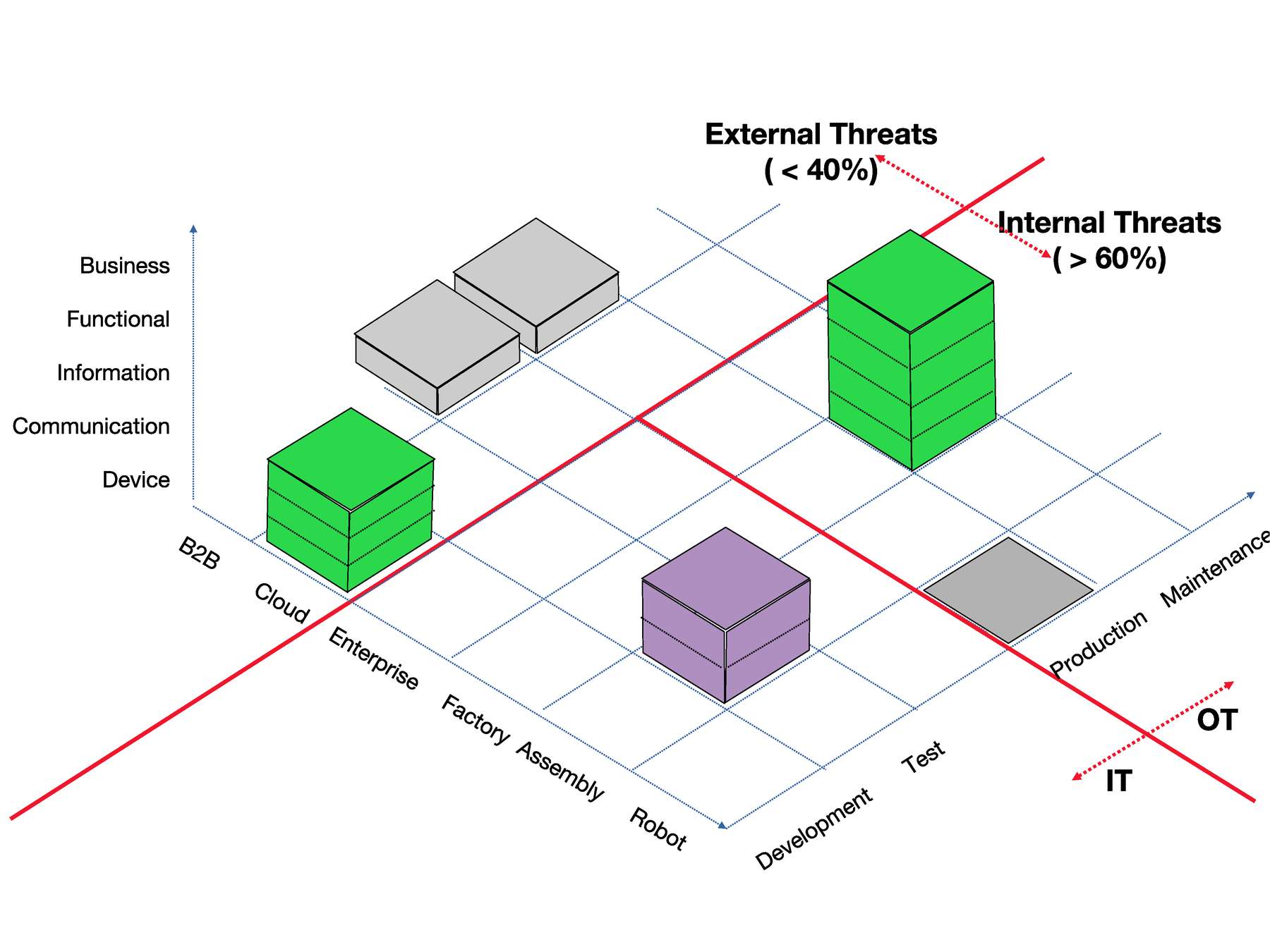
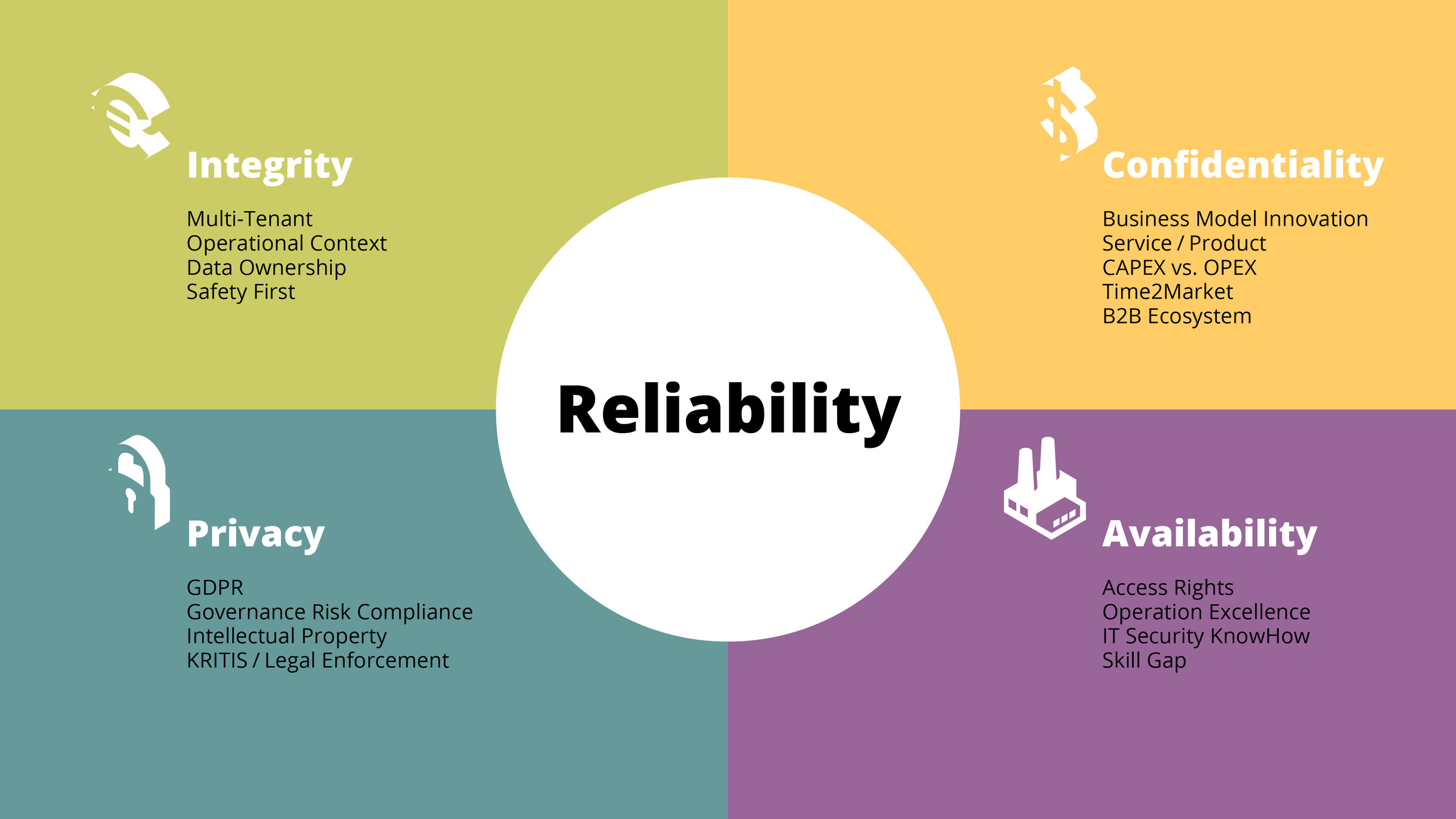
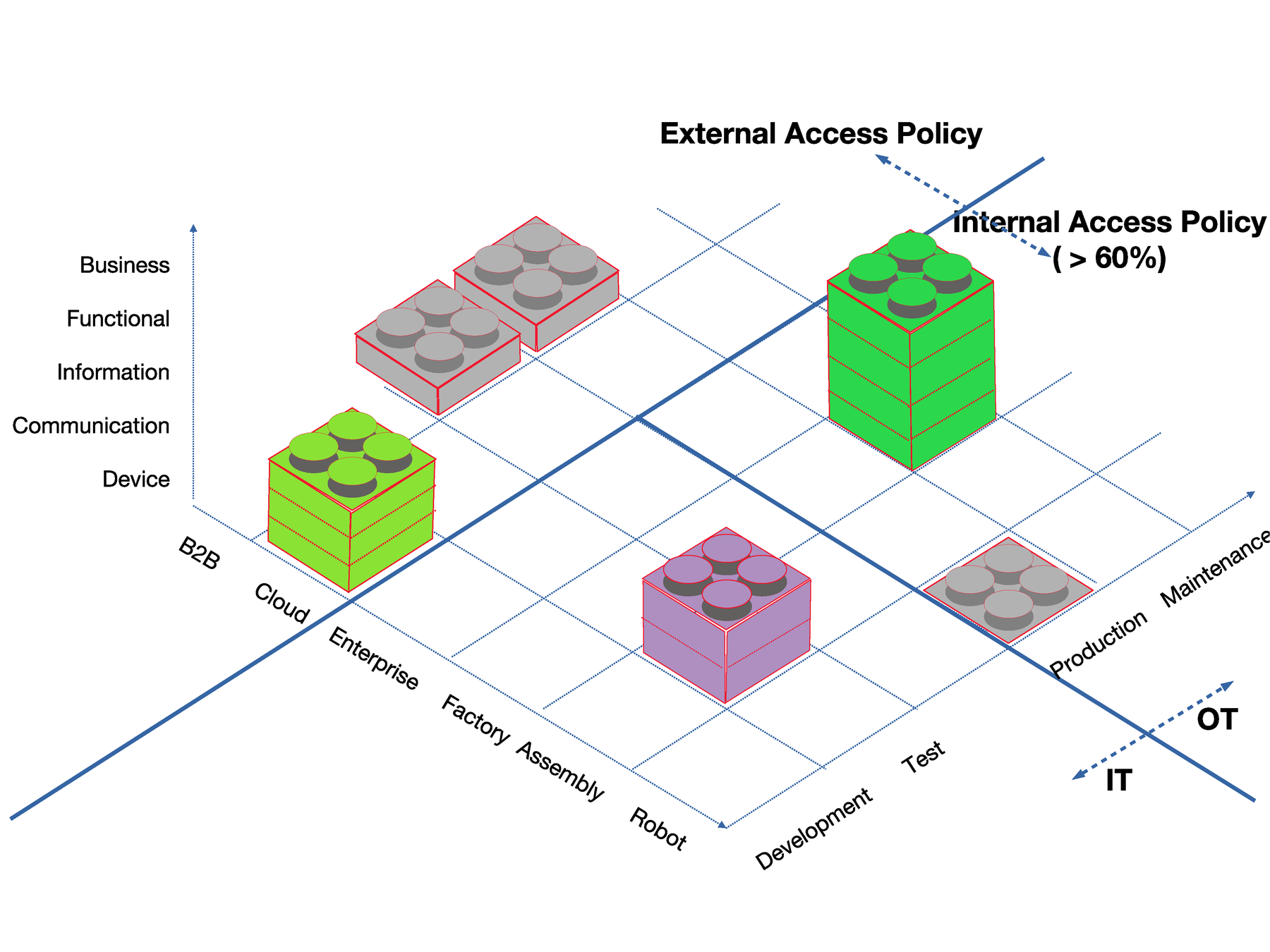
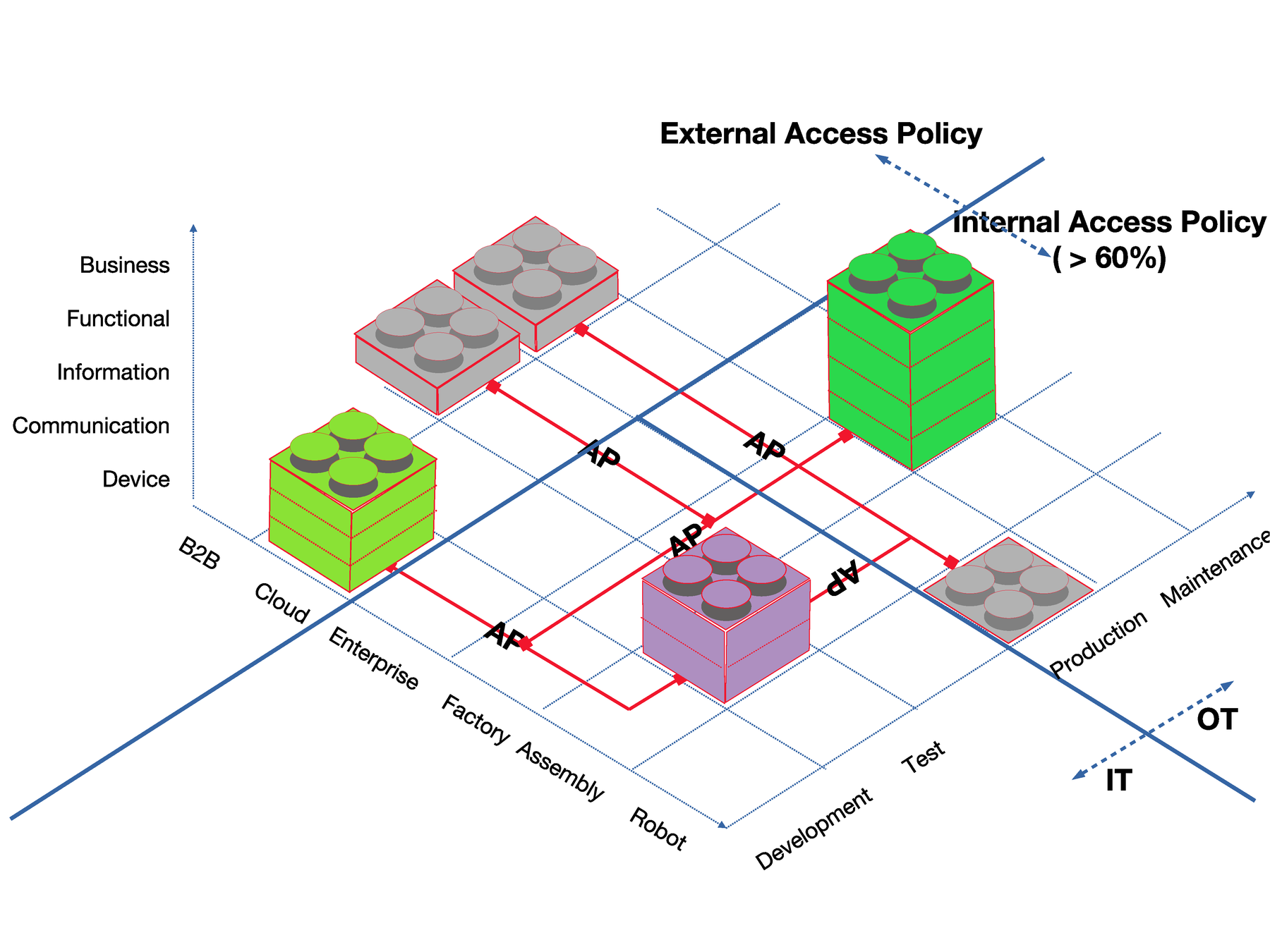
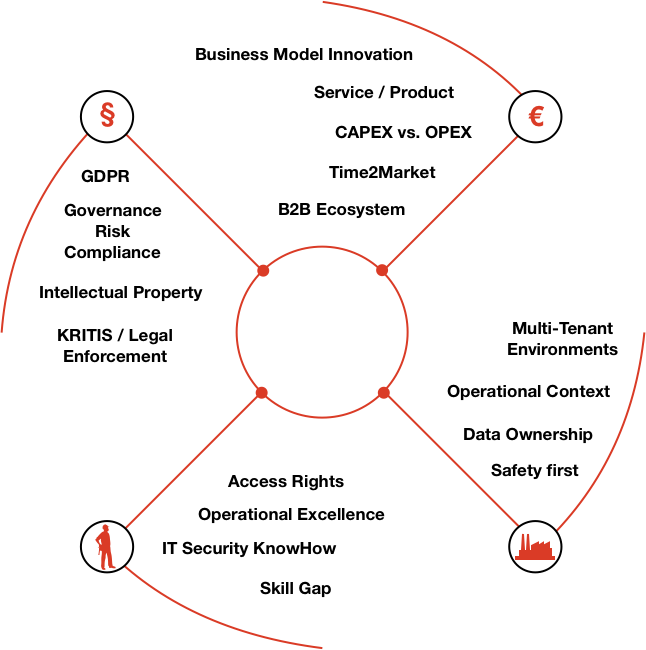
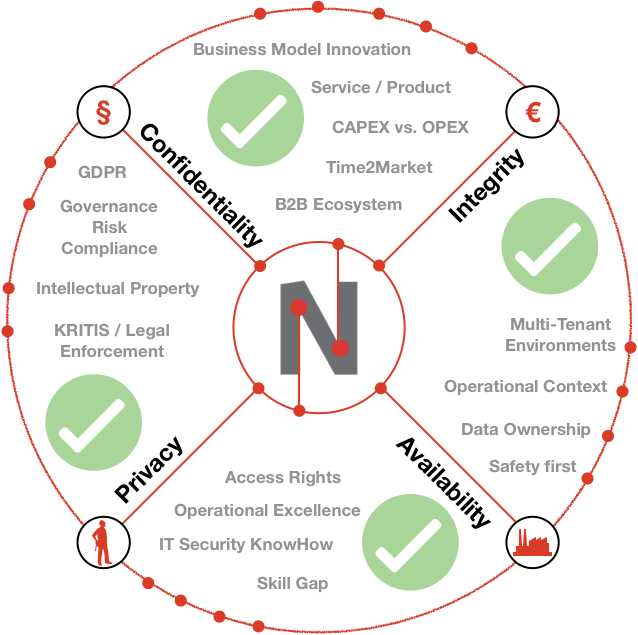
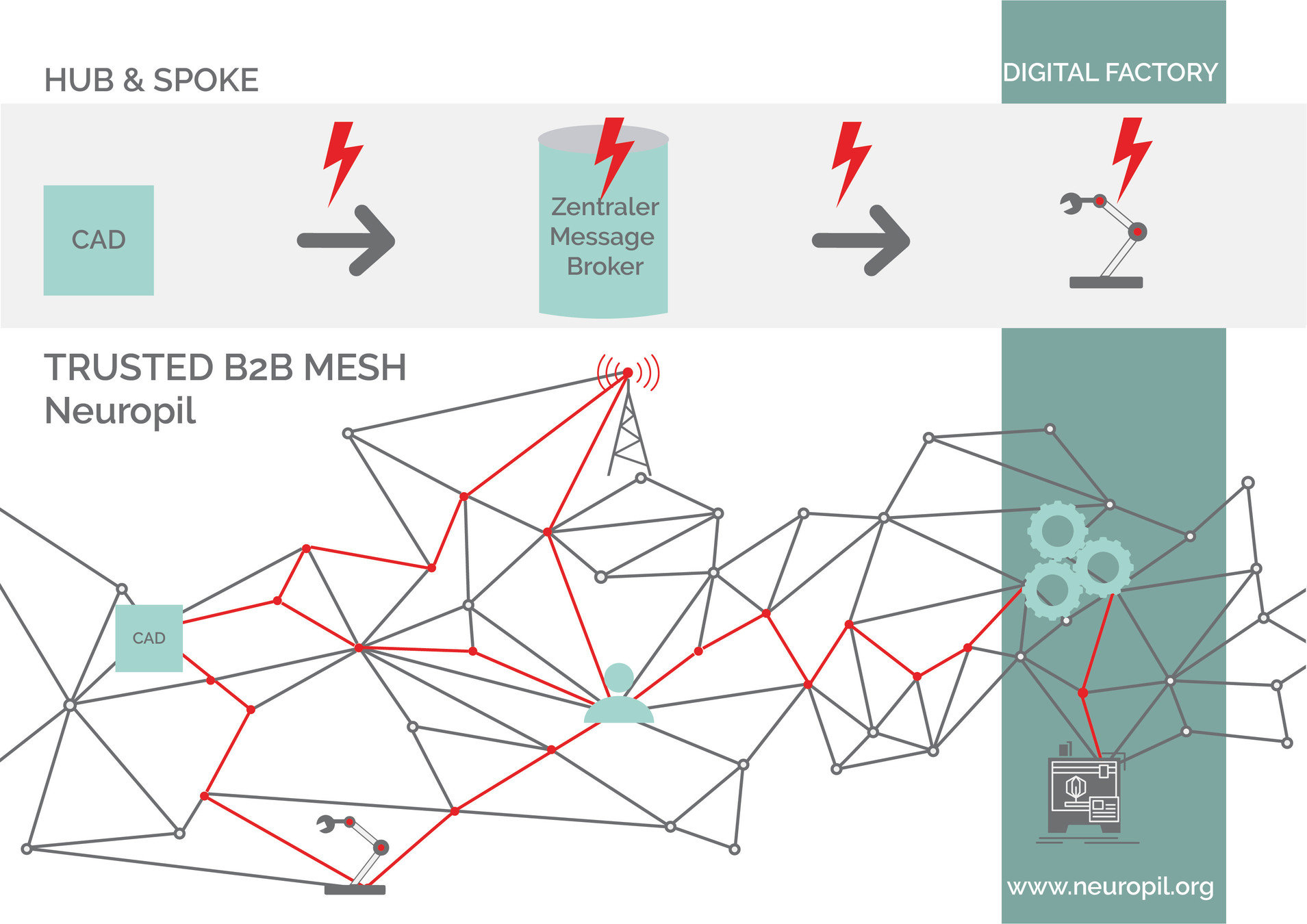
Neuropil is a project that wants to turn the tables on online search and discovery: instead of search solutions calling the shots, data owners decide what content is publicly searchable in the first place.
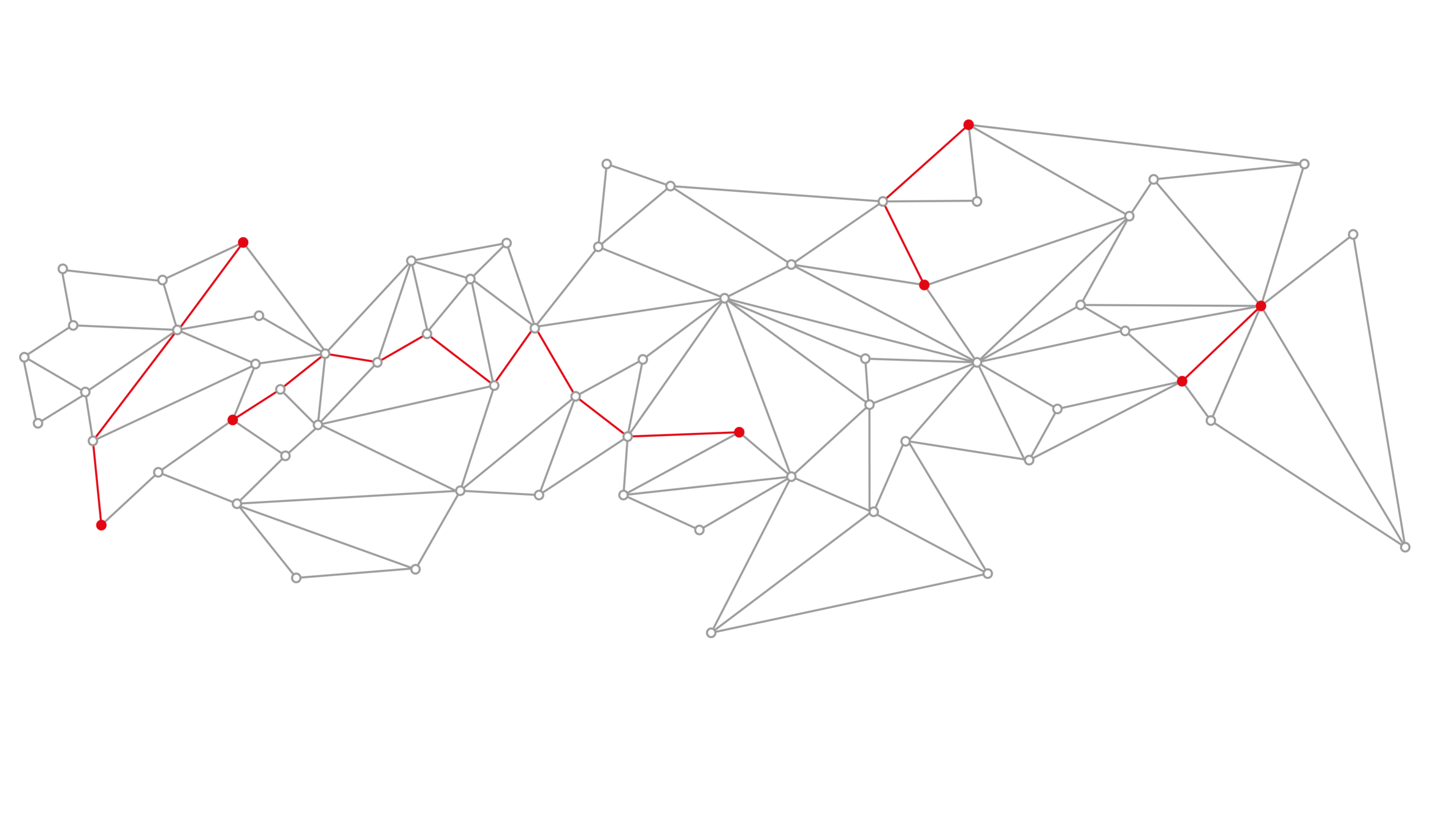
They can do this through their cybersecurity mesh that is private and secure by design. Data owners can send cryptographic and unique so-called intent messages that state what specific information can be found where.
The access to the actual information or content is also controlled by data owners, for instance to provide either paid or public free content.