VLC SANDBOX
(workshop 2020-09-17)
VLC
GOALS
https://news.ycombinator.com/item?id=14409123
VLC
- Ready-to-use pipeline
- Automatic configuration
- Designed for making players, and extending use case through plugins
- No «custom pipeline»
GStreamer
- Multimedia pipeline description framework
- Designed for generic application
- Pipeline is explicit (most of the time)
- But already different sandboxing history
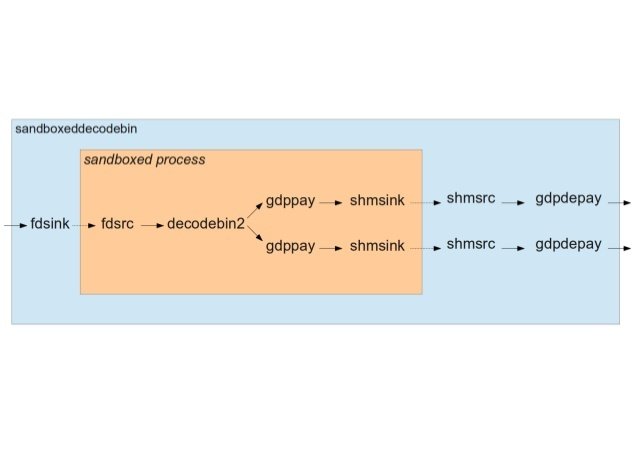
GStreamer sandbox bin
Pending work
- a «do your own security» framework
- designed for multimedia makers, not really final app makers
«Implement a generic sandboxing solution by implementing a GstElement / GstPad subclass that can be provide functionality of any GstElement in another process. »
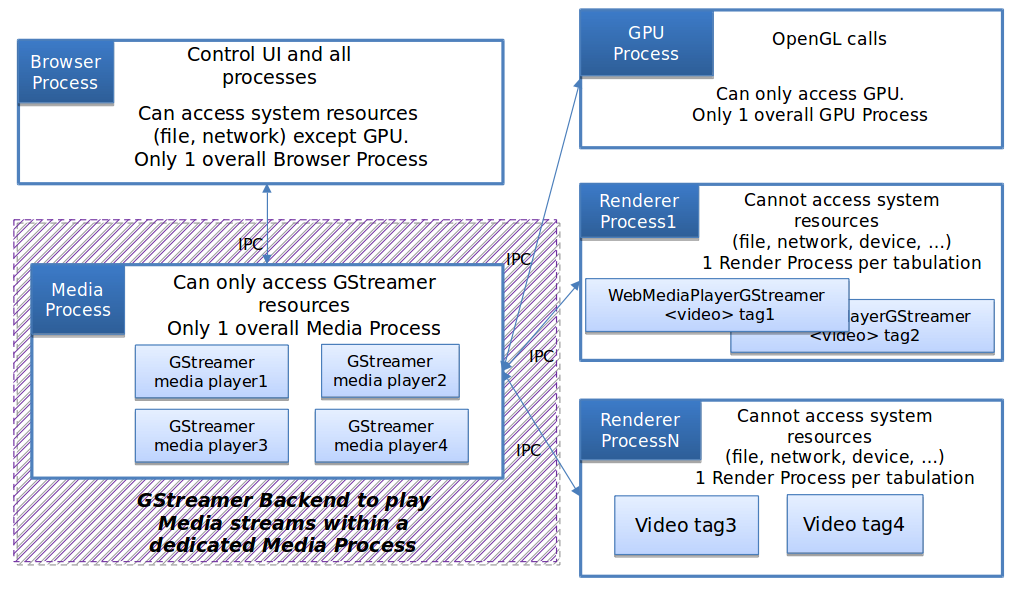
GStreamer in chromium
VLC
BUILDING
BLOCKS
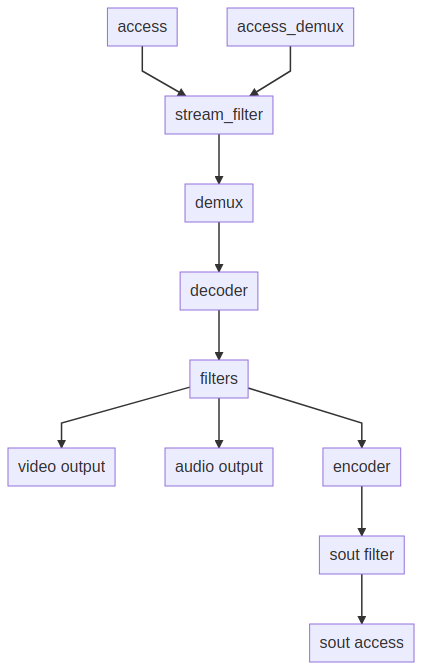
Pipeline
- src/video_output/video_output.c
- src/input/input.c
- src/input/decoder.c

Objects creation order
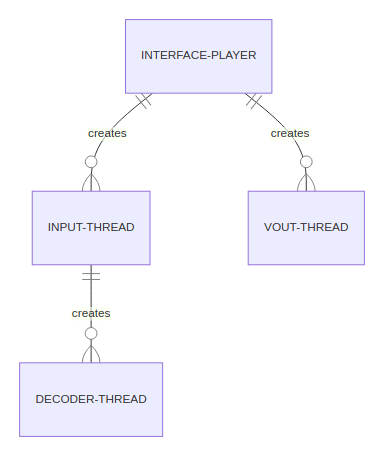
Main threads creation
VLC
PIPELINE
EVENTS
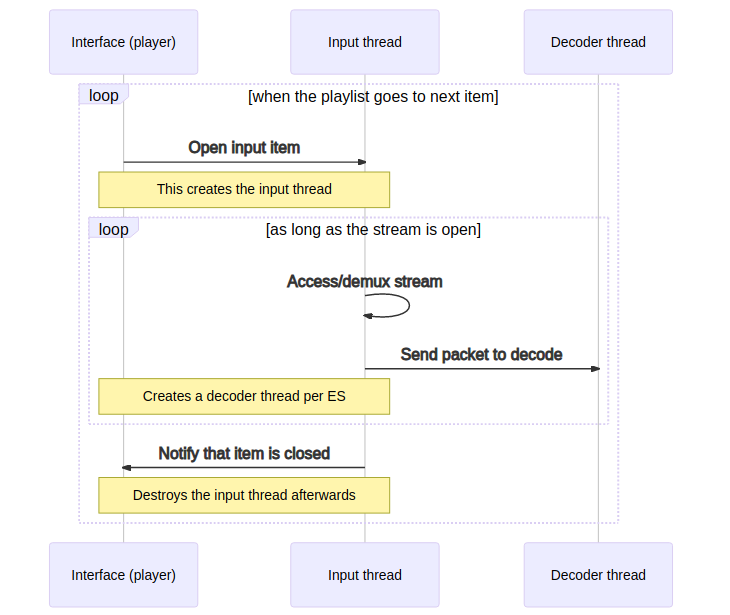
Focus on Input thread
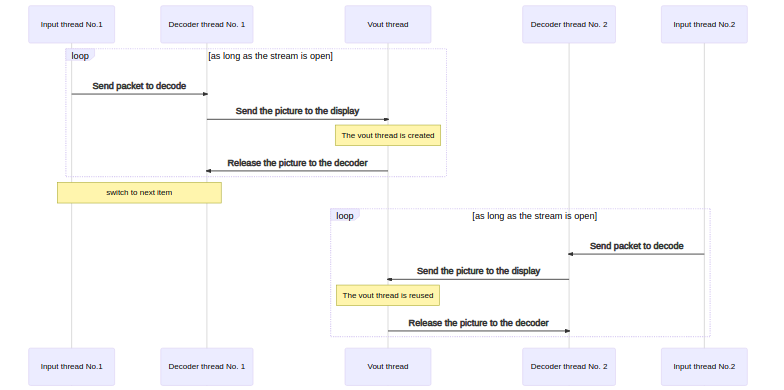
Focus on vout thread
"Sandbox"
prototype (Architecture)
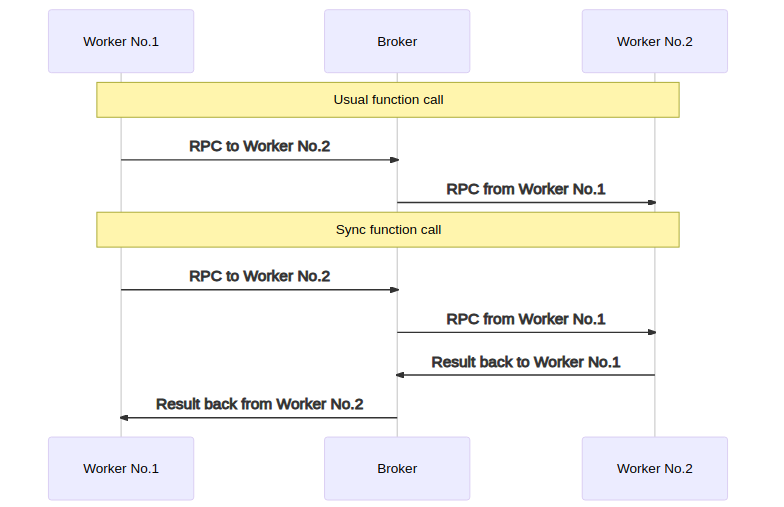
Broker IPC model
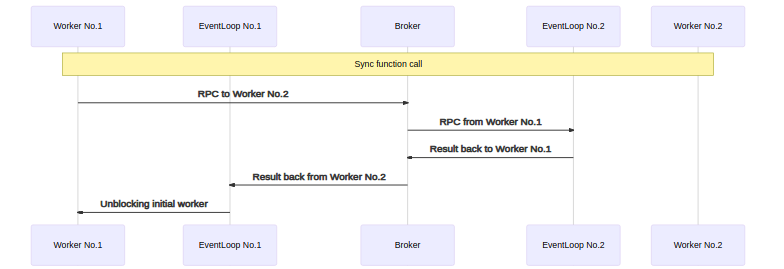
Broker in details
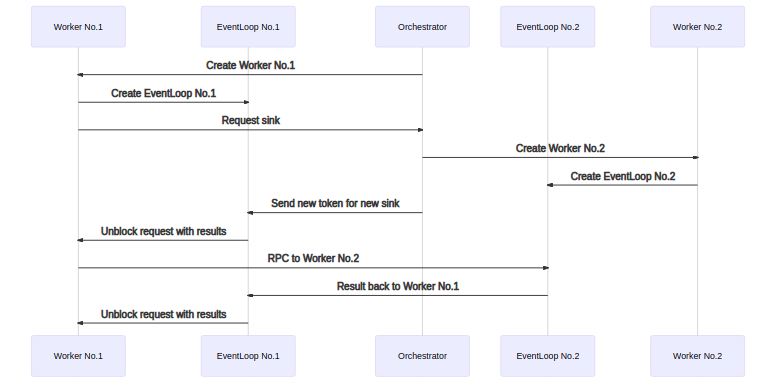
Orchestrator model
Capability
Handles and file descriptors can play the role of a capability token.
One pair of IPC per modules that are interacting.
Caveats
- More complexity
- Hard limit on fd number
- Can we always tranfer resources from one process to the other safely?
"Sandbox"
prototype (data transfer)
Windows
- DuplicateHandle
- ALPC / RPC Windows
- Process creation and setting up handles
- View on shared memory files
- Pipes
- D3d11 devices ?
- DXGI textures
Linux
- Unix socket and ancillary data
- Shared memory fd
- DMABuf fd
- Fork/Exec
Windows
- D3D11 devices
- DXGI resources
- COM objects (wasapi, some codec, some demux)
- File, network
Linux
- /dev/video0 (GBM, opengl, etc)
- wayland-0 / DISPLAY
- open(), network
"Sandbox"
prototype (Proxy system)
Proxy objects
- Bind two workers
- Allow request/response without knowing about the sandbox
- In theory, independent of the IPC implementation
- In practice... security must be accounted (available descriptors?)
- Need complex transparent object creation and object tracking
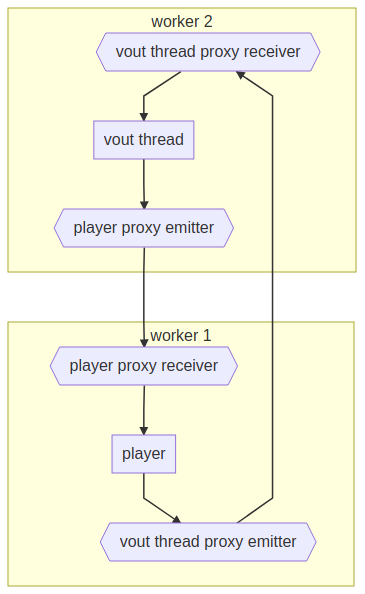

Transformed method call
Caveats
- Need to setup the different objects with the correct fd
- Need to have the same object virtually in multiple process
- Invisible capability hack?
- Platform limitations?
Benefit
- Transparent for VLC developers
- No intrusive sandbox design: sandbox concern
- Extension of RPC through plugins
- Independent of the underlying RPC framework
"Sandbox"
prototype (seccomp)
Main goals
- Split VLC into different priviledge area
- Classify syscalls into different categories
- Expose the limits
=> Guillaume Fournier's presentation
Main questions
Automatic testing ?
Creation of worker process?
Sharing/reuse of worker process with multiple components?
Tracing and mitigation?
Non-goals in the sandbox design?
Usual security flaws and how to handle them?
VLC Sandbox
By unidan
VLC Sandbox
- 77



