Abhinav Sejpal
Fell in love with the power of software at age 17, and I am still in love. I'm the one your mom warned you about, So be careful and Follow me.

Null - Humla Session
^ I hope - You gotcha ^
 for Social Media
for Social MediaTwitter handle
Hashtag for this session





* We won't talk about Injection & XSS *
Client Side language : HTML & Javascript
Server side Language: PHP
DB : MYSQL
Why PHP ? - Any answer Here?
Why MySQL? MySQL is Girlfriend of PHP <3
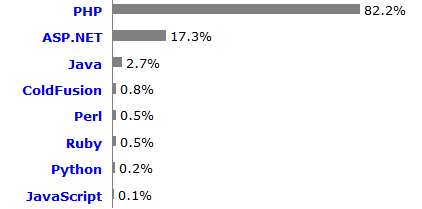
http://w3techs.com/technologies/overview/programming_language/all


Login ID - admin
password - adminpass
HTTP GET Request
http://127.0.0.1/xampp/mutillidae/index.php?do=logout
<html>
<title> CSRF Demo 1 </title>
Click me </a>
</html>
Yes it's not dangerous but annoying
ssh, No!!
Would you like to write CSRF exploit without click ??
<img style="display:none;" src="your Request">
Image tag does not require clicking the link compared Tag-A requires clicking on the link to activate the HTTP request
Can we try Demo 1 with Image tag ?
CSRF GET Request with Image Tag
<html>
<title> CSRF Demo 1 </title>
</html>
Iframe tag
<iframe
src="your Request"></iframe>
Java
Script code
<iframe
src="http://127.0.0.1/xampp/mutillidae/index.php?do=logout"></iframe>
<script> var X= new Image();
X.src= "http://127.0.0.1/xampp/mutillidae/index.php?do=logout";
</script>
<html>
<title> CSRF Demo 1 </title>
<a href =http://127.0.0.1/xampp/mutillidae/index.php?page=user-poll.php&csrf-token=&choice=nmap&initials=n&user-poll-php-submit-button=Submit+Vote>
Click me </a>
</html>
{ Post HTTP Request }
http://127.0.0.1/xampp/CSRF Attack/Add New Blog Entry - CSRF POST.html
No - you should try out
~ CSRF Finder Firefox add-on ~
* One Click POC *
* Hybrid automation *
Thank you - Piyush Pattanayak
CSRF & XSRF
Update the user info. without their knowledge
http://testphp.vulnweb.com/userinfo.php
You've been CSRF'd with static token!
Can we exploit this with Level #2 ?
Facebook CSRF worth USD 5000 by Amol
Google Account display pic deletion
Facebook Account deactivation
Advance Leanings - CSRF Token Validation Fail
http://haiderm.com/csrf-token-protection-bypass-methods/
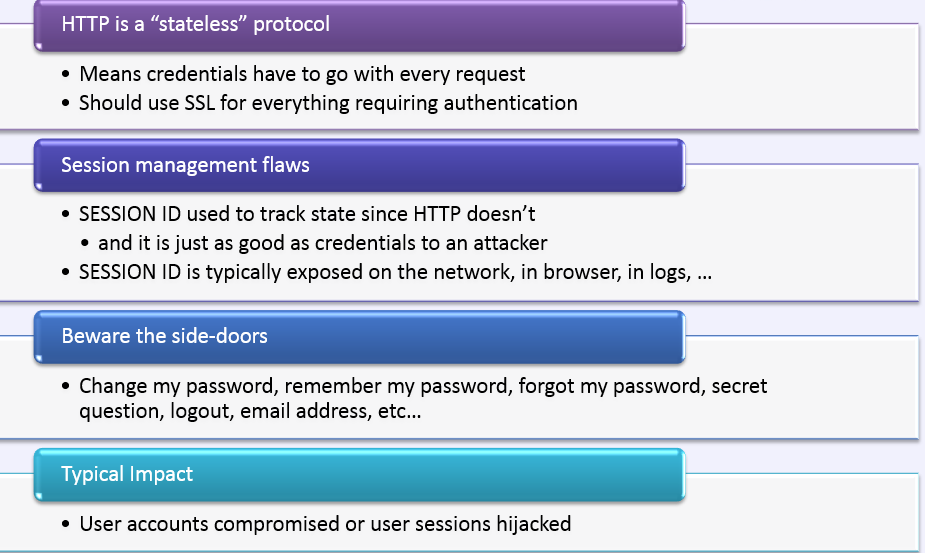
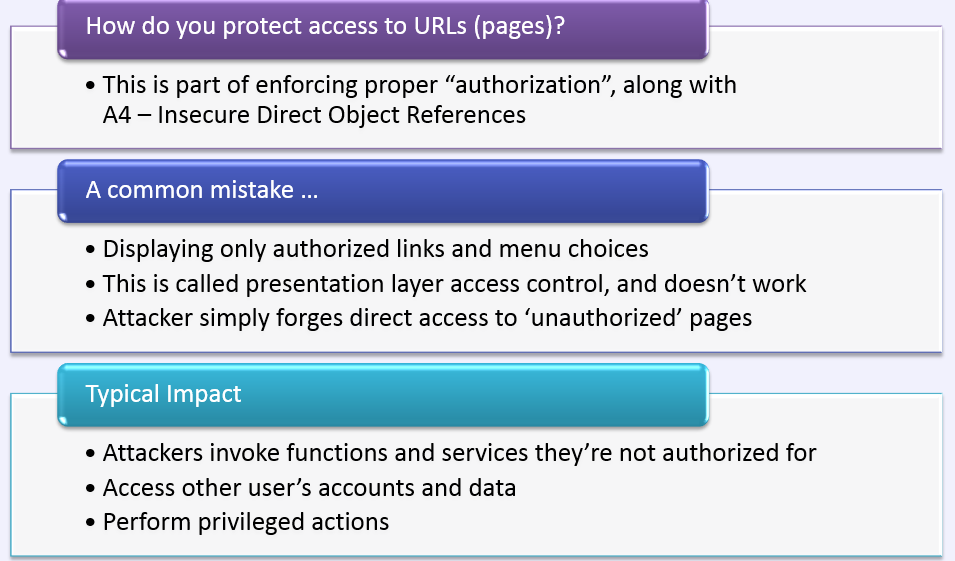
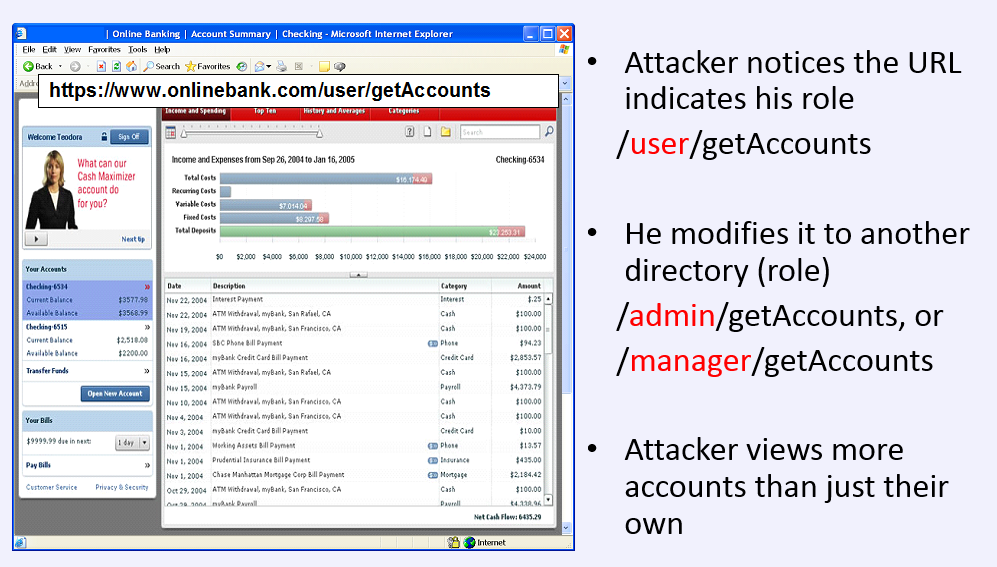
Am I Vulnerable To 'Broken Authentication &
Session Management'?
A2 - OWASP TOP 10

Can we do it ?
Part -1 Learning with SQL Injection
/xampp/mutillidae/index.php?page=login.php
Account Lock Policy & Captcha missing :P
PHPSESSID=0ebmp37g8v8stqsjpf1ln40c20
JSESSIONID
ASP Session.SessionID
Let's Try out Part 1 learning and exploit the session
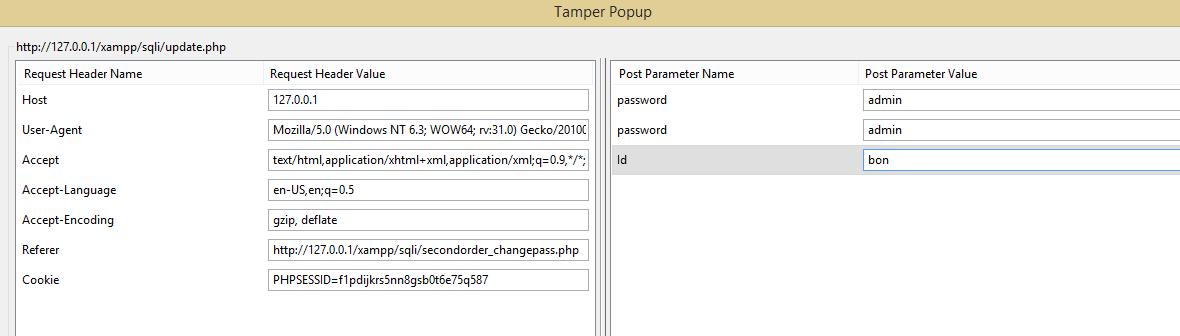
So, Let's Learn about Web App DB structure
Passwords are stored in plain text.
oh really -- ':(
OWASP #A6
Password is protected, when stored using encryption algorithm. Are you sure?
http://www.md5online.org/

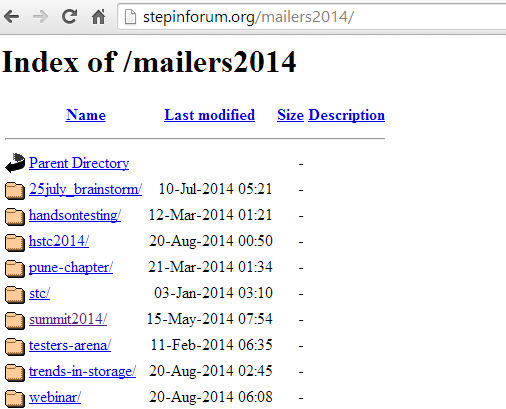
Robots.txt
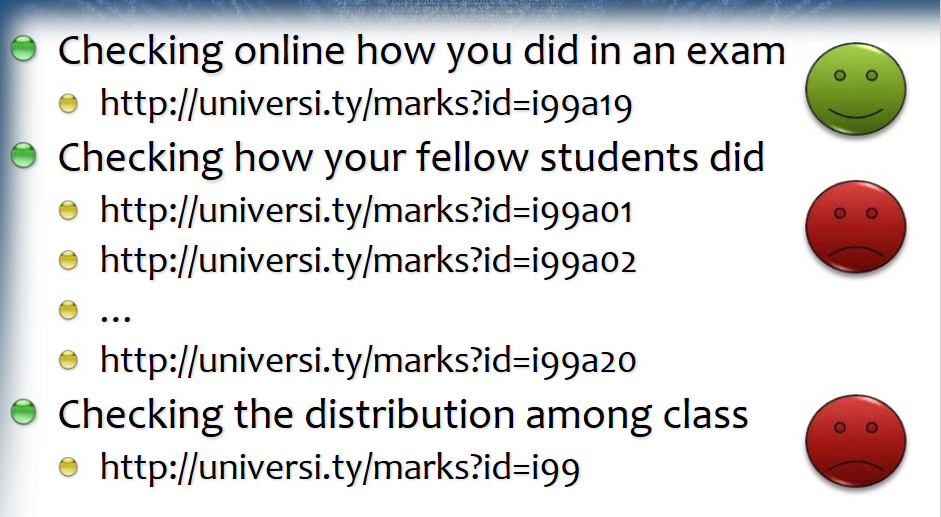
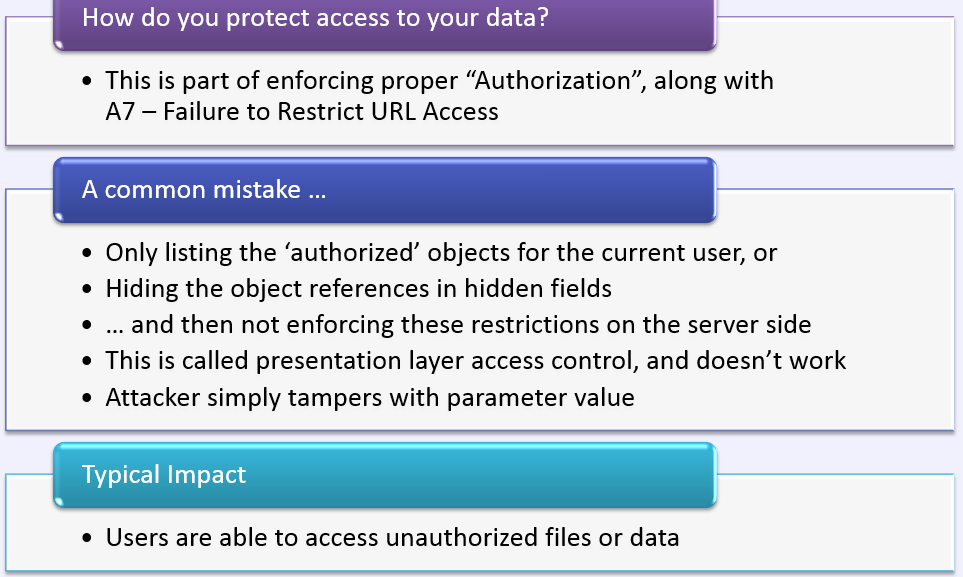
All Sensitive data expose

Secret PHP Server Configuration Page
http://127.0.0.1/xampp/mutillidae/index.php?page=phpinfo.php
OWASP #A9
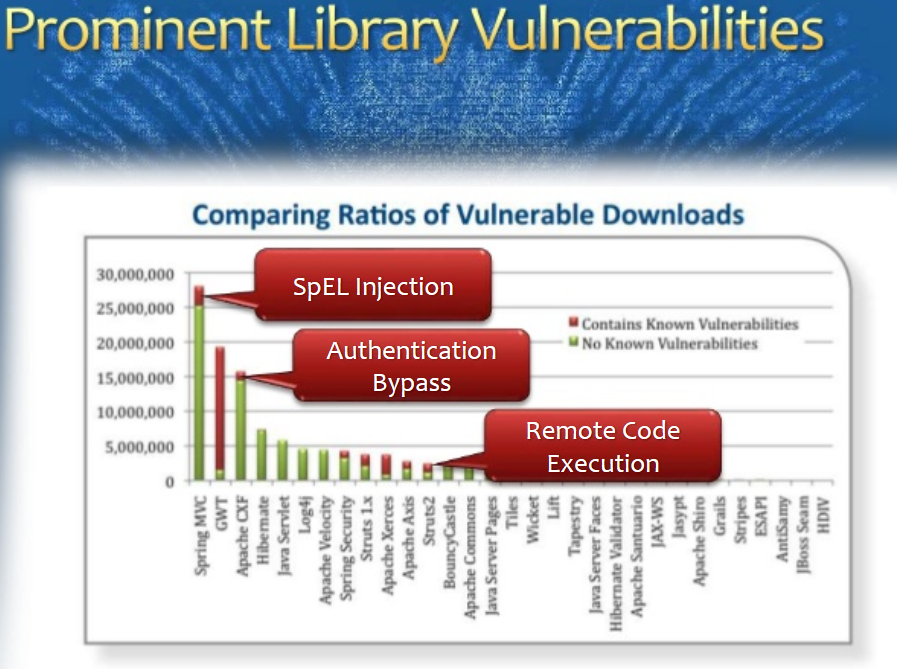
Latest buzzing known vulnerabilities


Code: – <iframe src= http://www.testingcircus.com> </iframe>
Live Demo: – http://goo.gl/6gEq2I
Click jacking Testing tool: – http://goo.gl/27VgQb
https://www.owasp.org/index.php/Top_10_2013-A10-Unvalidated_Redirects_and_Forwards
Vulnerable Redirection
http://127.0.0.1/xampp/mutillidae/index.php?page=redirectandlog.php&forwardurl=http://www.owasp.org
I don't think so, i need to explain you what you can do here :D

Feel free to write me at bug.wrangler at outlook.com
Say 'Hello' @null0x00

Thank-you http://garage4hackers.com/ community
Copyrights 2013-2014 Abhinav Sejpal
-----
Attribution-NonCommercial-NoDerivs 3.0 Unported
Dedicated to my lovely daddy
By Abhinav Sejpal
Mission :- Understand / Learn / Practice OWASP Web Security Vulnerabilities https://www.owasp.org/index.php/Top102013-Top_10 In this session, Attendees will perform hands-on exercises to get a better understanding of the OWASP top ten security threats.
Fell in love with the power of software at age 17, and I am still in love. I'm the one your mom warned you about, So be careful and Follow me.